Secure your app against DDoS, API Abuse, Hijacking, Fraud, etc.
Layered application defense: Cloud Armor, Apigee, reCAPTCHA
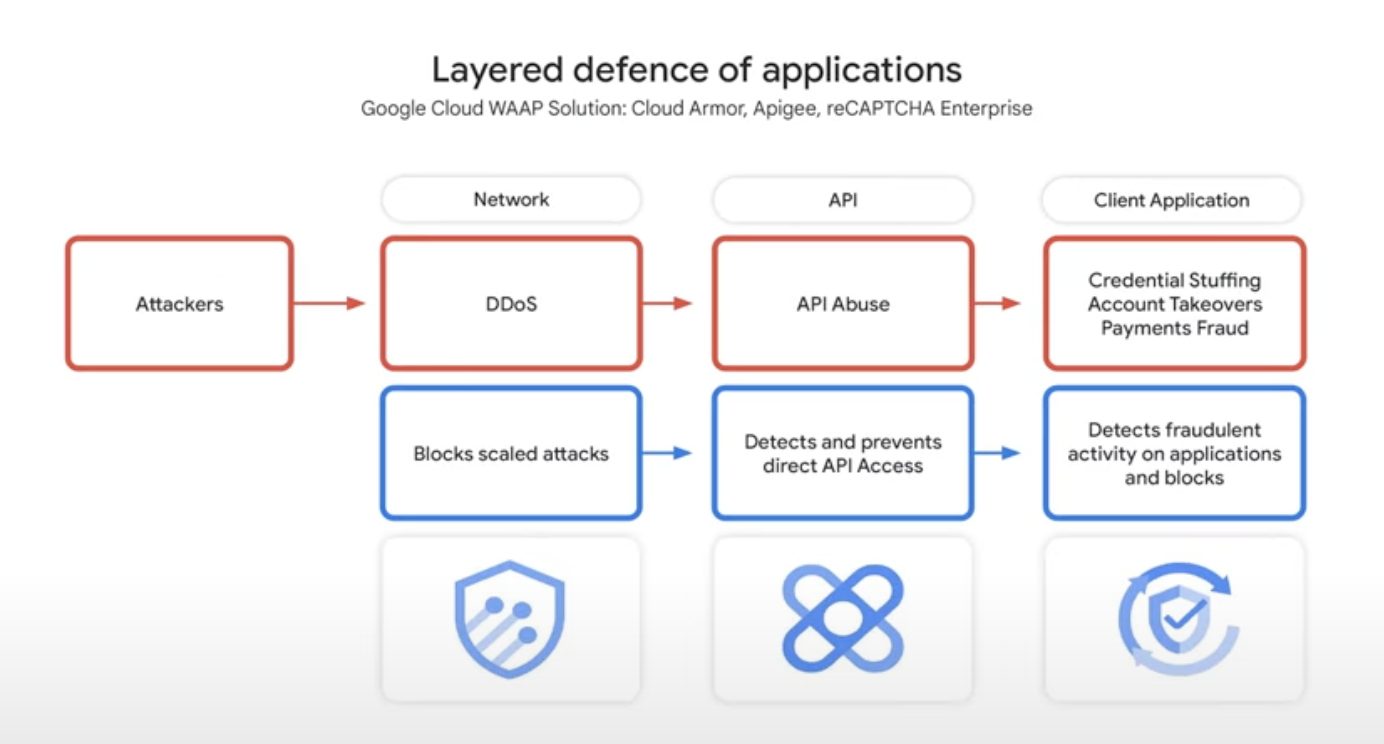
- Cloud Armor: defends against DDoS attacks at the networking layer
- Apigee: defends against API abuse
- reCAPTCHA: defends against sophisticated credential stuffing, ATOs, and payments fraud on the client
Cloud Armor
Cloud Armor
- provides global scale defense against volumetric protocol and application attacks.
- built w/ the same technology & infrastructure that Google uses to protect its user web apps
- provides WAF protection focused on OWASP Top 100 for apps (ex) SQL injection, cross-site scripting, etc.
- can be used for geofencing: define allowed/denied regions, countries, IPs
Geofencing: the use of GPS or RFID technology to create a virtual geographic boundary, enabling software to trigger a response when a mobile device enters or leaves a particular area
L3L4 DDoS protection
- always on for all projects using global load balancers
- detects & mitigates network DDoS attacks (ex) SYN floods, UDP amplification attacks
- can be deployed in front of any website/service to support hybrid/multi-cloud architectures
User functions: you create filtering policies to allow, deny, redirect, or rate limit connections
Bot management: Cloud Armor acts as an enforcement point determined by reCAPTCHA models for fraud & bot detection engines
ML based Layer 7 Adaptive protection
- designed to detect volumetric DDoS attacks
- ML models good traffic & notifies when highly suspicious patterns emerge
Apigee
- offers many policies & services to meet requirements for security visibility and control
- requirements: threat protection (abuse detection), governance (role-based access control, masking, compliance requiements), data security w/ TLS requirements or encrypting functionality
How to secure API in runtime
- detects any abuse on API logic or sensitive information
- provides in-product dashboards or integration w/ SIEM for further anaylsis/integration
SIEM (Security Information and Event Management): a security solution that helps organizations recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations
Google as part of Apigee control plane
Since Google runs on already existing analytic data, no additional data is required and hence new privacy concerns or approvals are not needed.
Effect: close to zero latency impact on API calls
New API abuse detection dashboards
- powered by ML models trained to detect abuse detection in real-time API traffic
- focus on scraping & anomaly detection
- clustering algorithm to help reduce noise & focus on the most sensitive/timely incidents
- detected APIs are grouped into clusters
ReCAPTCHA
New ReCAPTCHA
- frictionless
- installs on JavaScript
- hence provides users & developers a completely frictionless experience
- analyzes the behavior of users on the page
- enables developers to put reCAPTCHA everywhere on their site & mobile applications to keep users safe with no additional friction
- visibility into legitimate, adversarial, fraudulent traffic across majority of the Internet
- enables Google models to keep applications safe while not interrupting legitimate users
- analyzes data from all traffic types, web, mobile, and WAF
WAF (Web Application Firewall): a protocol layer 7 defense that helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet
Mobile native applications
ReCAPTCHA offers native, Android, and iOS SDKs to defend mobile applications from fraud.
Android can be installed as one line dependency to Google's Maven Repository. iOS can be installed via Cocoapods Swift Package Manager, or direct download.
- All device signals seen by an application into a fraud score
Account Defender
Account defender: complete account takeover defense
- expanded original reCAPTCHA to cover the entire hijacking/account takeover risk workflow
Process
- ReCAPTCHA observes users' registration behavior & subsequent login events for anomalies
- checks username & password combinations against Google's global leak database to ensure they are not compromised
- Provider can trigger two-factor authentication w/ email/SMS integration within the reCAPTCHA platform
- If you observe any abuse, reCAPTCHA will oferr related acocunts API to help find similar accounts to the ones you know are abusive
Fraud Prevention
Fraud prevention enables reCAPTCHA to combine transaction & behavior data on sites to leverage the in-class behavioral intelligence of reCAPTCHA with payments instrument data provided by traditional providers. This combination caputres and detects fraud and lowers friction on legitimate users.
https://www.youtube.com/watch?v=7ss6J_lnucM
https://www.ibm.com/topics/siem
