What is a Firewall?
In reality, Firewall stands for a wall that protects us from "Fire".
Yet, in computer Networks, it stands for A HW/SW that accepts/declines/censors/declinces data across different networks.
What does Firewall do?
Firewalls basically serve to prevent the inflow of impure, unreliable data.
However, from these simple functions, as the level of hacking attacks and patterns increases, firewalls can also implement advanced functions that block data or restrict access by placing complex conditions.
Most firewalls are policy-based firewalls. A policy is a kind of law or rule that defines the function of a firewall. Starting with a general-level policy that simply blocks traffic, it allows more than 500 bytes of traffic with fake information, but leaves a log.' Even the same high-level policy can be implemented and used in various ways.
However, firewalls require a lot of management accordingly, and they primarily block them, and nothing more or less. As such, we need to filter secondarily with IDS/IPS and vaccines.
1st Generation Firewall: Packet filtering Firewall
The first generation is the packet filter firewall. A firewall that filters packets according to a preconfigured policy. Internal session of firewall is unmanaged, and is at the transport/network layer.
Basically, the packet filtering firewall has the following functions.
1. Foward: The ability to forward packets to their intended destination
2. Reject : Function to filter and recommend packets
3. Drop: Just go away
4. Log : Record information of accepted or rejected packets
5. NAT: NAT Features
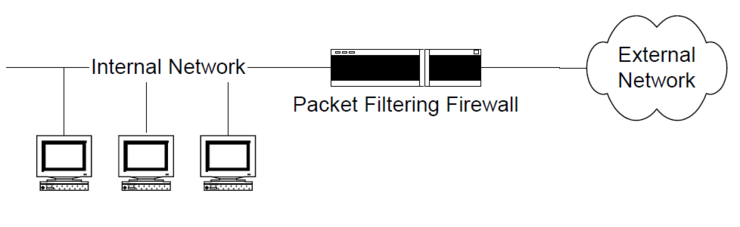
Because all packets are policy-based, this firewall is vulnerable to security because many policies are overloaded and bypassed packets are not filtered out, and there is no way to prevent attacks using session-creating protocols.
In addition, there are many problems with packet filtering firewalls.
1. Packet filtering settings are too difficult for end users to do.
2. Sometimes there are situations where it is difficult to perform filtering tests.
3. Degrades the performance of the router.
4. An attacker may tunnel to the permitted port and access it.
2nd Generation Firewall: Stateful Inspection Firewall
This firewall is much more secure than packet filters because it is a session-by-session firewall, not a packet-by-packet firewall, and it also has extensions to handle complex derived sessions such as FTP without adding additional policies.
It can be said that it is a firewall with more powerful functions than the first generation.
3rd Generation Firewall: Application Firewall
And as attack techniques were subdivided, diversified, and advanced, it was difficult to defend only with packet filter-based firewalls.
So what came up is the third generation application firewall. Network security solutions such as IPS, WAF, and UTM belong to the application firewall. It works at the application layer, and stands between the server and client as a proxy server.
Firewall Features
- Packet Filter
The packet filter is a firewall operating in a network layer, and is a firewall that does not allow packets to pass when violating an established policy. It has the advantage of having a large amount of traffic that is often performed at the kernel level and can be processed by performing limited inspections.
A packet filter has a stateful firewall that only inspects packets themselves, and a stateful firewall that manages sessions to which packets belong, so that all packets belonging to this session do the same.
A firewall such as iptables can perform packet filtering functions.
- Proxy
It is a function of terminating an existing session and forming a new session to check the harmfulness contained in the session, and checking when information is handed over from one session to another by forming two sessions, origin-destination session and origin-firewall, firewall-destination.
It takes a lot of inspection, but it is safer and can perform additional functions such as protocol changes.
- NAT (Network Address Translation)
It is a function that keeps the IP address used in the internal network different from the address exposed to the outside, and it provides a certain amount of security function because the exposed address and the actual address used are different. With NAT, there is a possibility of session conflicts when accessing the internal network outside, so there is also PAT, a way to avoid collisions by changing ports.
Types of Firewall
-
Screening Router
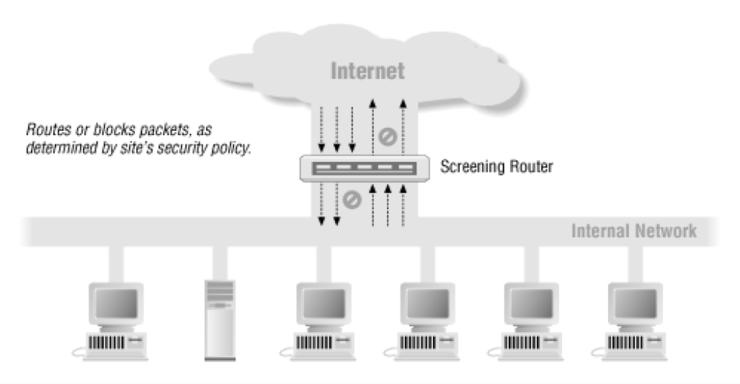 The first is to configure a basic firewall environment using a screen router with a packet filtering function.
The first is to configure a basic firewall environment using a screen router with a packet filtering function. -
Dual-homed host
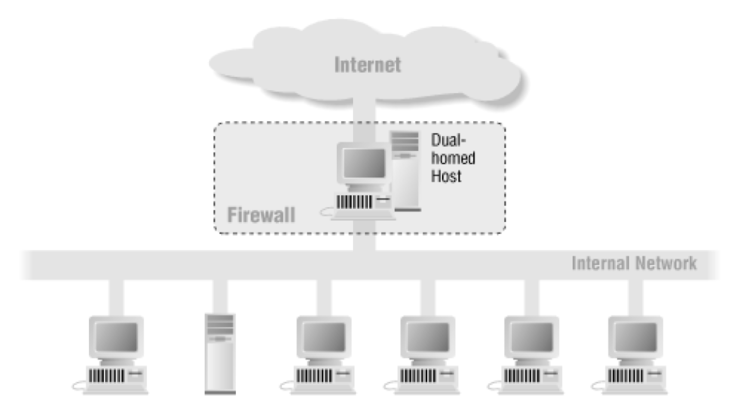 The dual home host structure is a structure in which a host uses two network interfaces (NICs). It is configured by connecting one to an external network and the other to an internal network.
The dual home host structure is a structure in which a host uses two network interfaces (NICs). It is configured by connecting one to an external network and the other to an internal network. -
Screened host
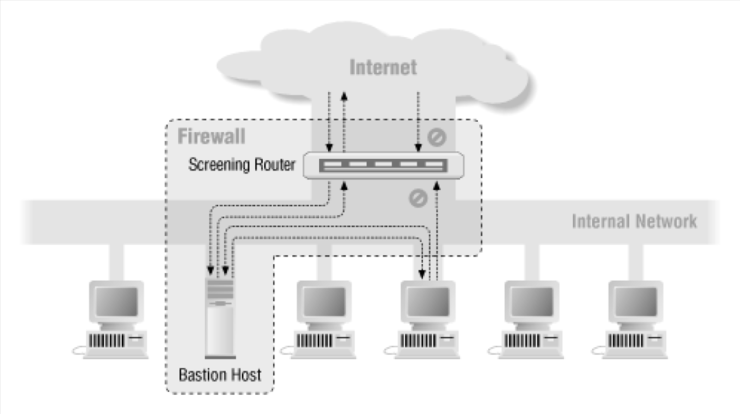 The screen host method is a method in which a Bastion Host is placed on the internal network and the screen routers are connected one by one.
The screen host method is a method in which a Bastion Host is placed on the internal network and the screen routers are connected one by one.
All communication is possible only through the Bastion Host. Direct access is not possible. [External -> Internal] Or [Internal -> External] All.
If the Bastion Host is broken, it will be a disaster. -
Screened Subnet
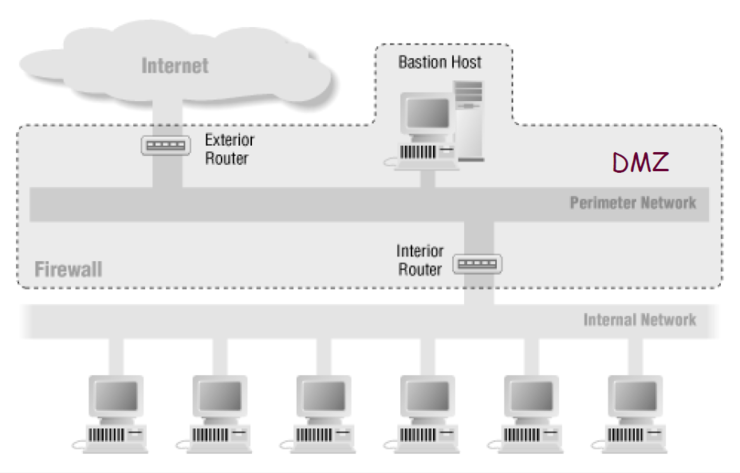 A screen subnet structure refers to a structure in which one or more boundary networks are placed between an external network and an internal network. In the figure, it is supposed to have a DMZ network.
A screen subnet structure refers to a structure in which one or more boundary networks are placed between an external network and an internal network. In the figure, it is supposed to have a DMZ network.
It uses two screen routers, one connecting the outside and the DMZ, and one connecting the DMZ and the inside.
The Bastion Host is placed on the DMZ, which separates the Bastion Host from the internal network, so the attacker has to penetrate the external router - Bastion Host - internal router, which is relatively secure
Source: https://plummmm.tistory.com/423 [Plummmm♪:티스토리]

who need help improving their coding skills baseball necklace , daily game solve cross