Internet Security Approach
Internet Security
- Web is now widely used by business, government, individuals
- But Internet & Web. are vulnerable
- Have a variety of threats
- Integrity
- Confidentiality
- Denial of service
- Authentication
- Need added security
TCP/IP
- Transmission Control Protocol/Internet Protocol
- Convention for communication on the Internet
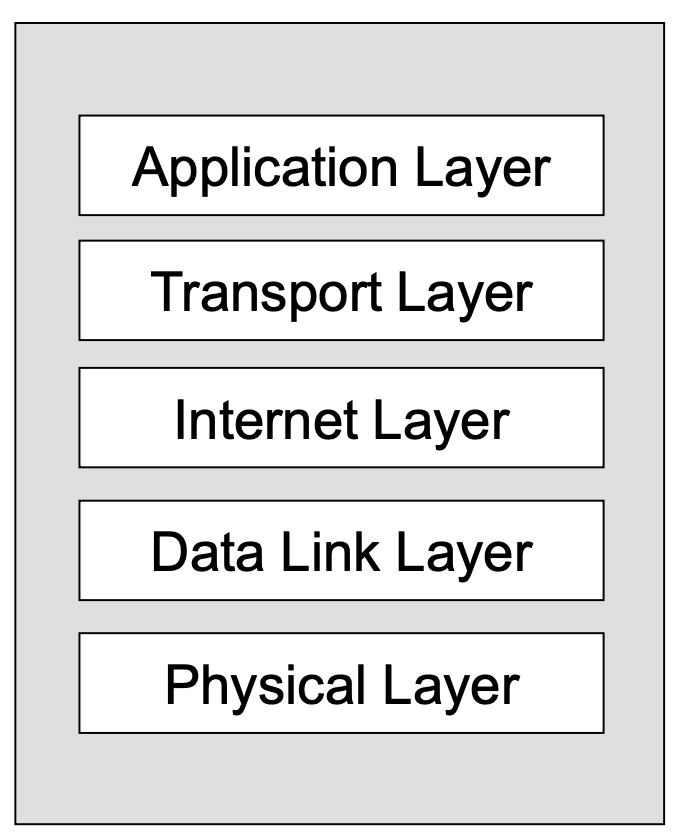
- Consists of five layers of software
- All layers except physical layer communicate with adjacent layers on the same computer
- Physical layer is the only layer where actual transmission between two computers happens
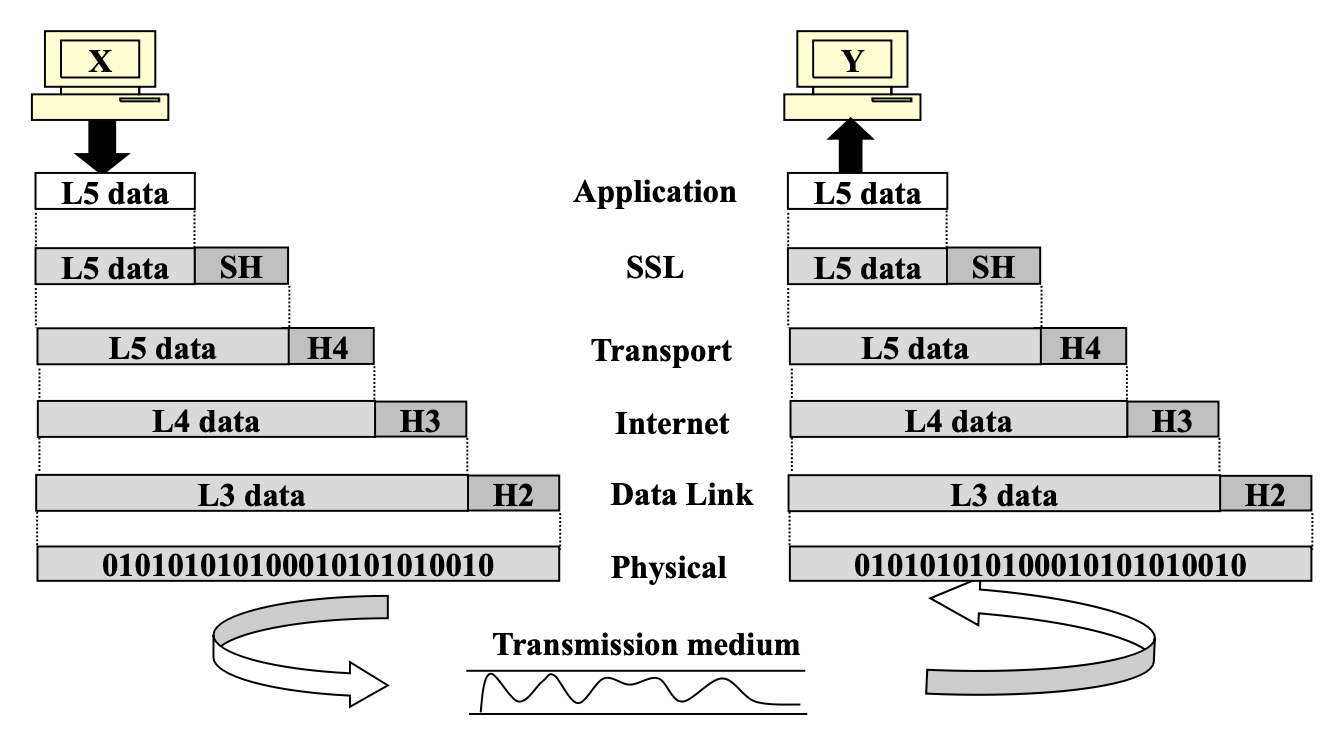
TCP/IP Communication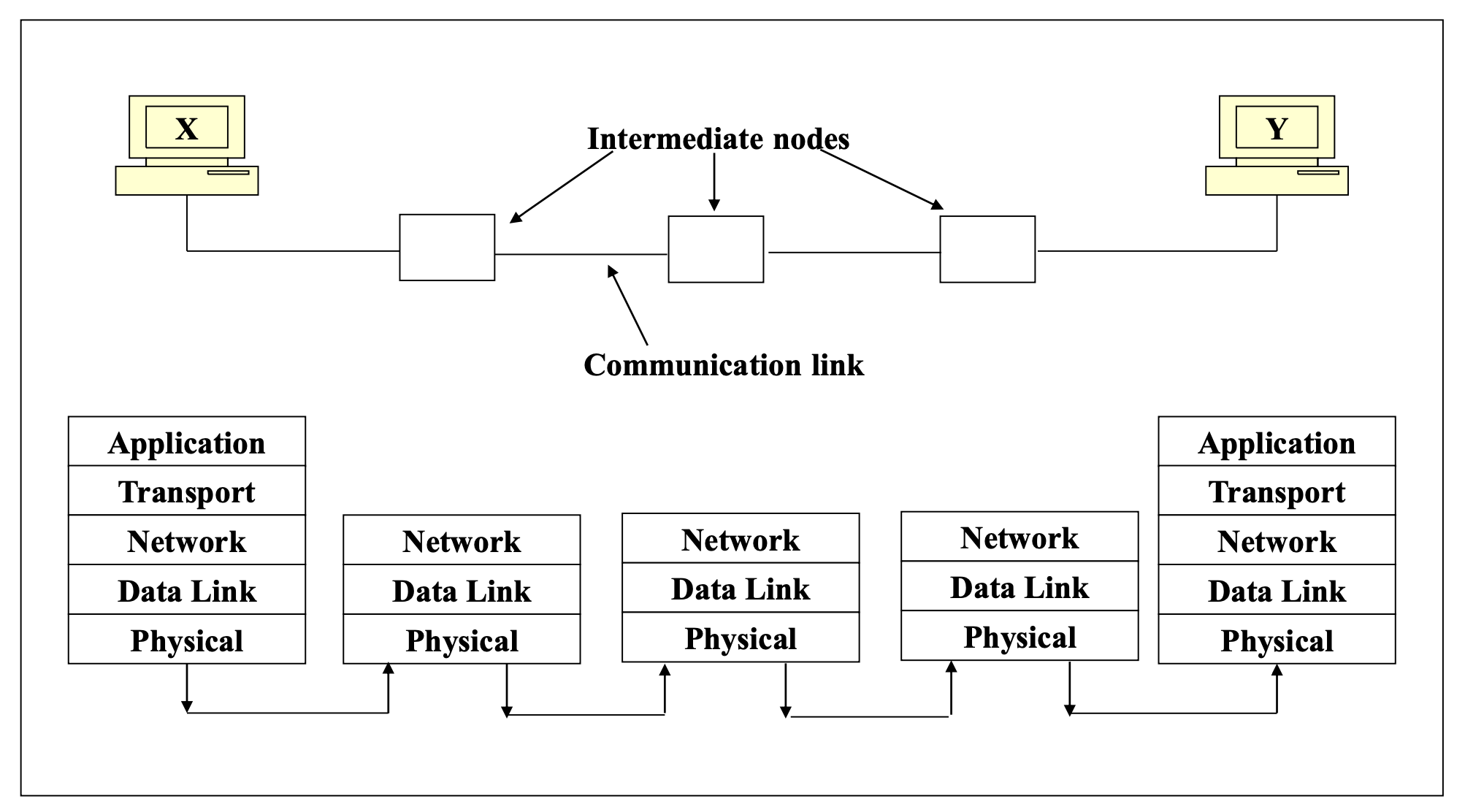
Data Exchange using TCP/IP Layers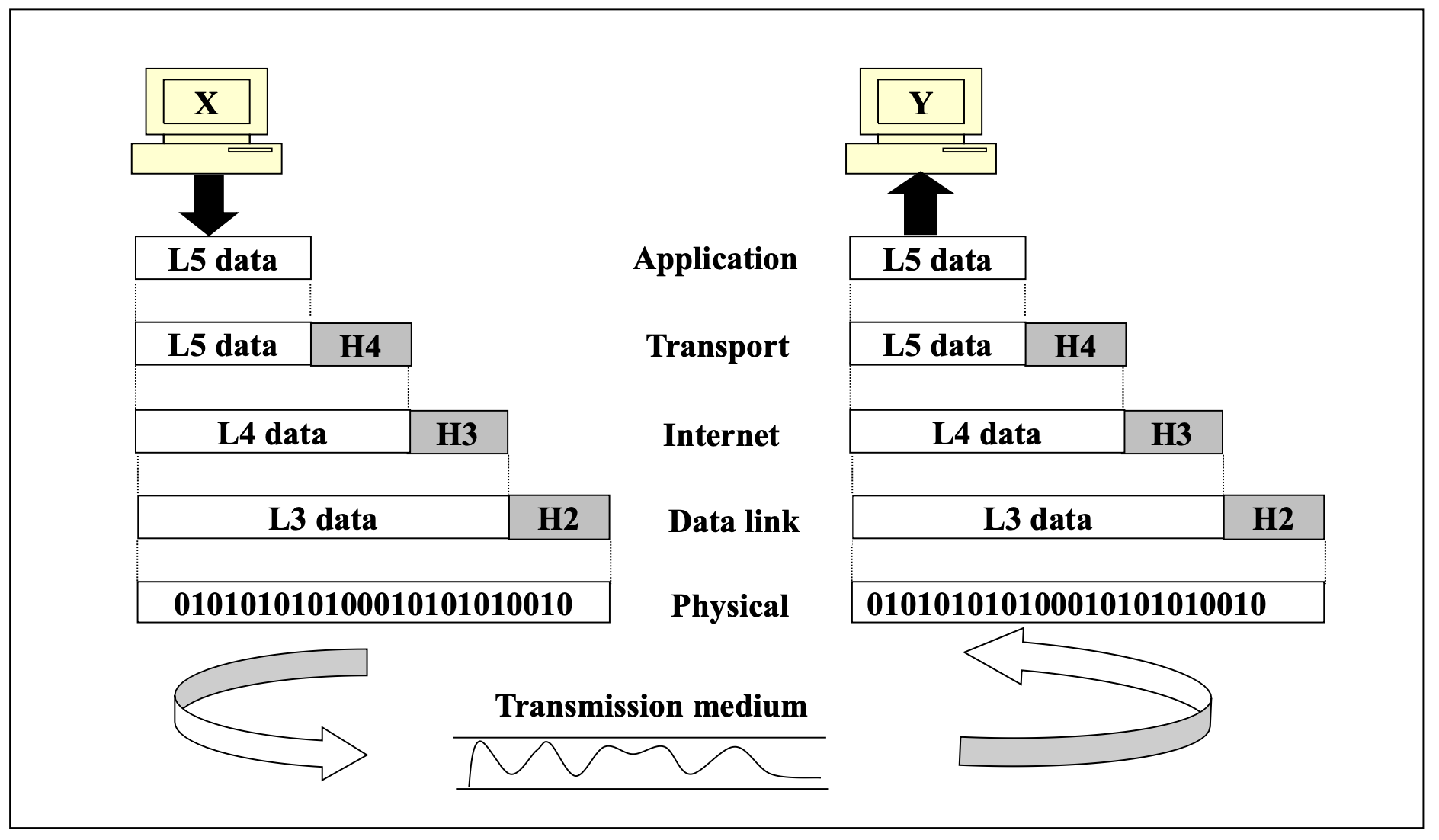
Web Traffic Security Approaches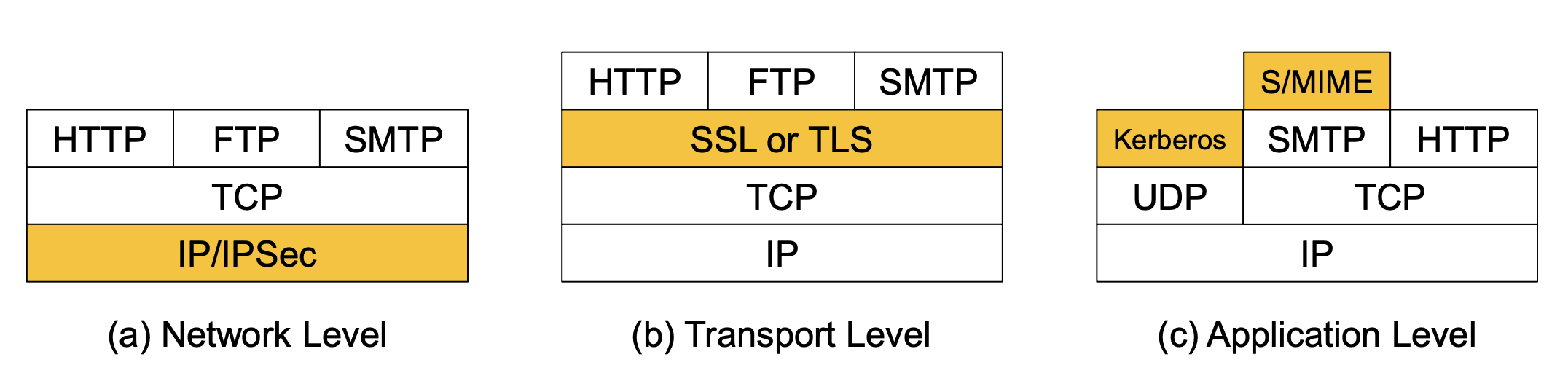
Basic of SSL
SSL (Secure Socket Layer)
-
Transport layer security service
-
Originally developed by Netscape
-
Version 3 designed with public input
-
Subsequently became Internet standard known as TLS (Transport Layer Security)
-
TLS (Transport Layer Security) is an IETF’s attempt to standardize SSL
-
SSL has two layers of protocols
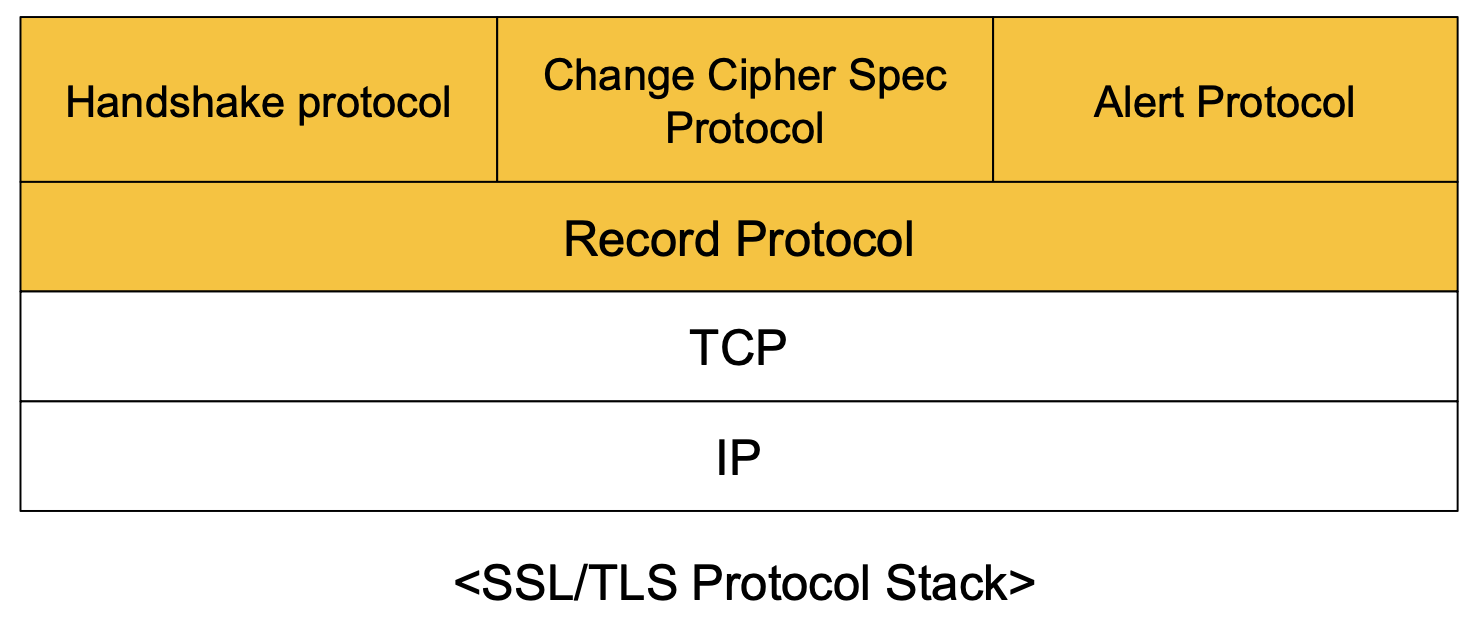
-
SSL layer at the sender’s end performs encryption on the data received from the application layer and also adds its own encryption information header (SH).
-
SSL layer at the receiver’s end removes SH, decrypts the encrypted data, and gives plain text to application layer
- Used by most websites for secure connections and for financial transactions to keep information safe.
- SSL not only encrypts the information, but also authenticates that the site you are connected to is really who you think it is.
- SSL uses symmetric cryptography, asymmetric cryptography, and digital signatures
How does SSL Work? (1)
- Go to a website for a financial transaction.
- It sends you a ‘certificate’ claiming to be some organization and claiming to have some public key.
- Your browser uses a chain of trust until it finds a site you trust. It will “vouch” for the accuracy of the certificate the website sent you.
- Now, you know that the Amazon.com site you are looking at is really authentic.
- Now you can send stuff to Amazon securely using asymmetric public/private key cryptography. But this is a bit slow.
- What do you send them? SHARED SECRET KEY.
- If you both have this shared secret key, you can now use symmetric cryptography to do the rest of the transaction and send info in both directions. Symmetric crypto is a lot faster than asymmetric.
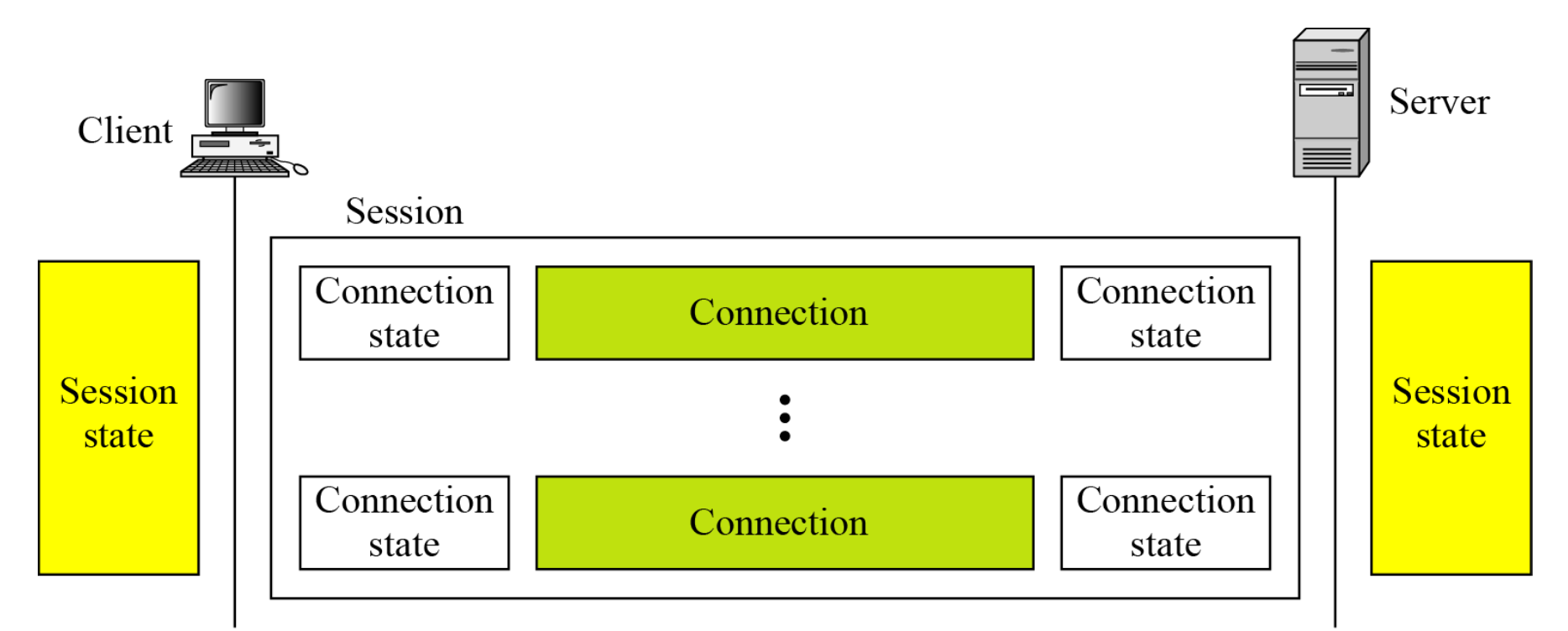
SSL Session & Connections
- SSL connection
- A transient, peer-to-peer, communications link
- Associated with 1 SSL session
- SSL session
- An association between client & server
- Created by the handshake protocol
- Define a set of cryptographic parameters
- May be shared by multiple SSL connections
- In a session, one party has the role of a client and the other the role of a server; in a connection, both parties have equal roles, they are peers.
Four SSL protocols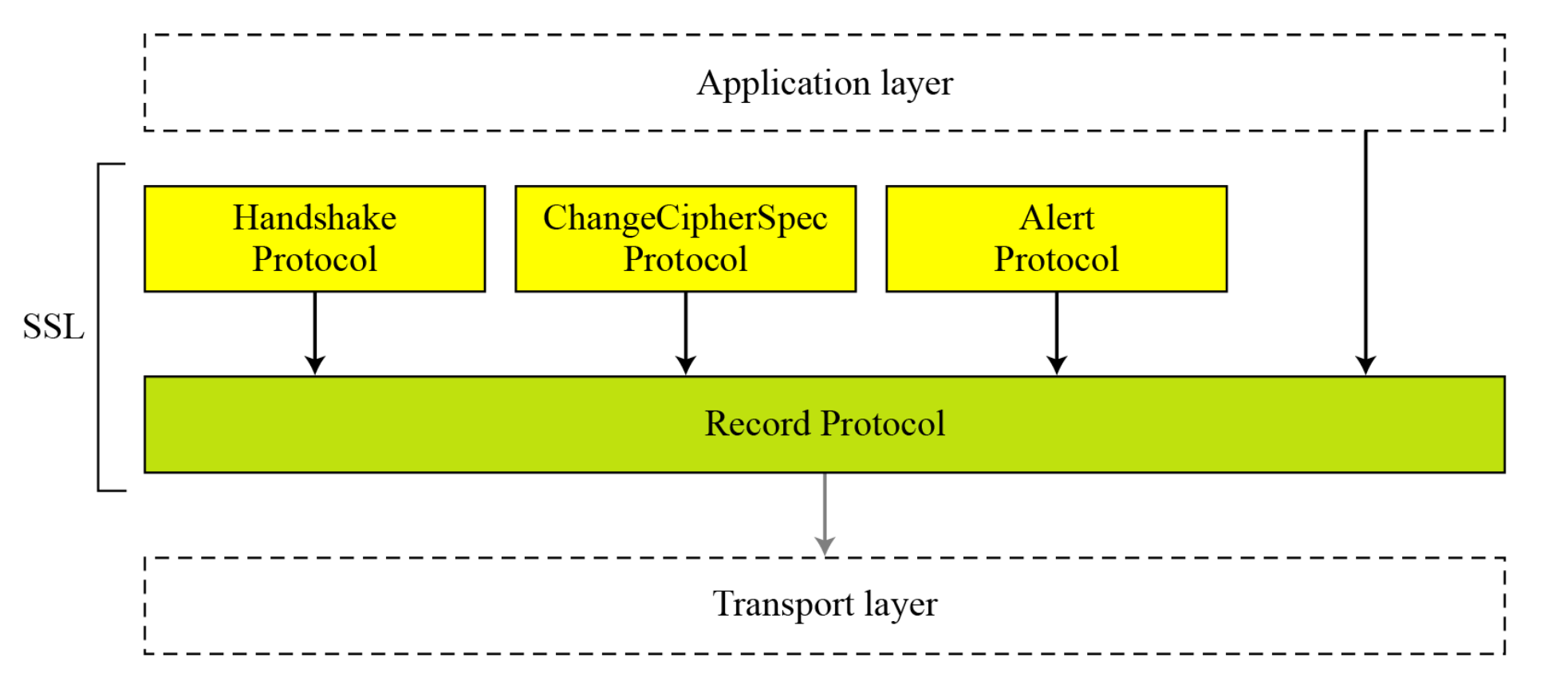
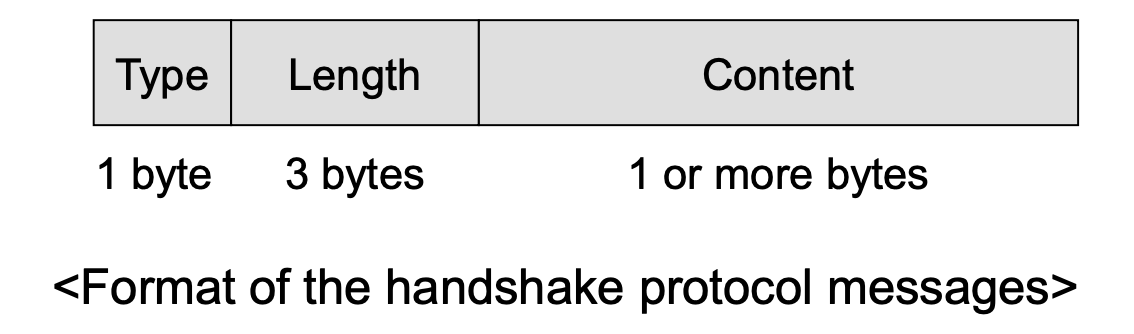
SSL Handshake Protocol
- The most complex part of SSL
- Allows the server and client to authenticate each other
- Negotiate encryption, MAC algorithms and determine cryptographic keys to be used
- Used before any application data are transmitted.
- Handshake protocol action
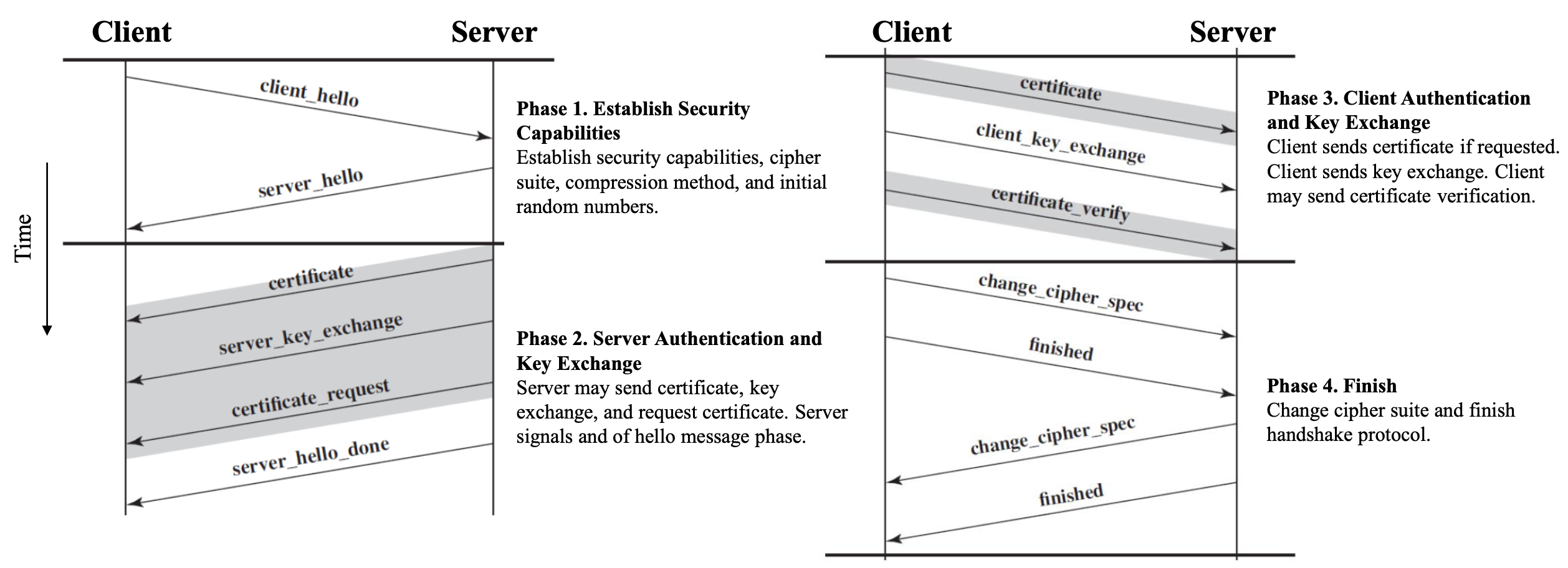
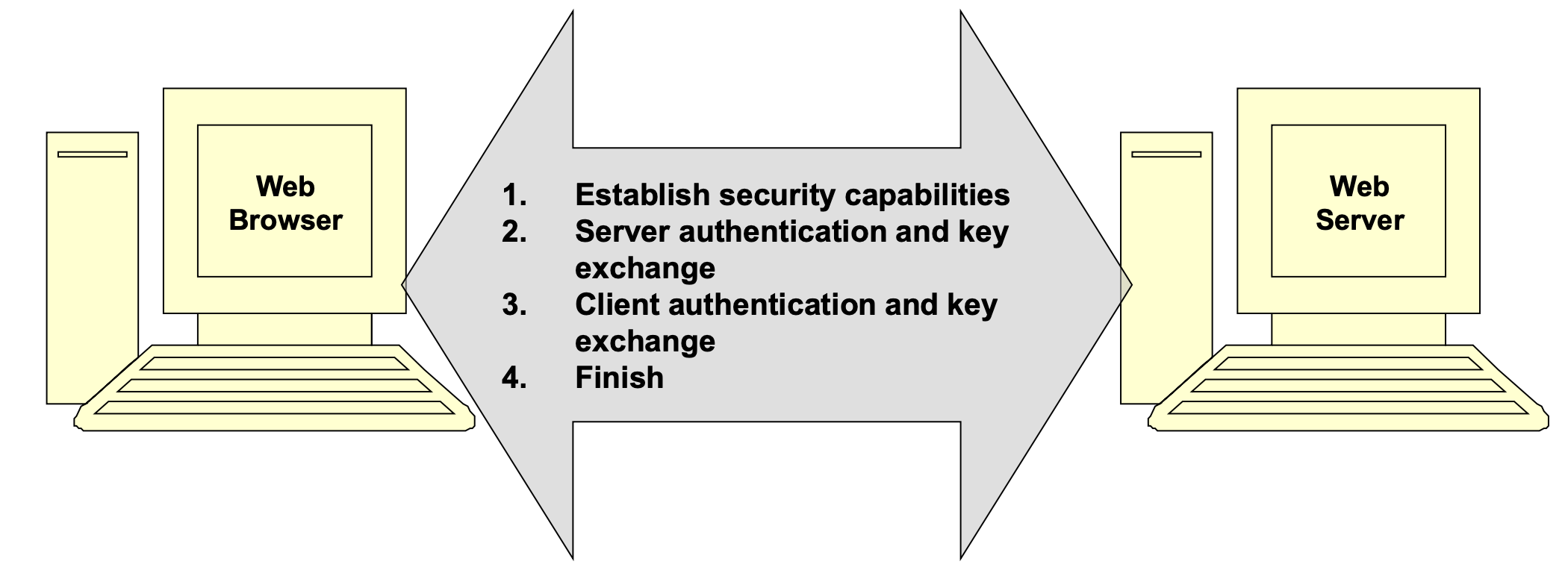
Phase 1: Establish security capabilities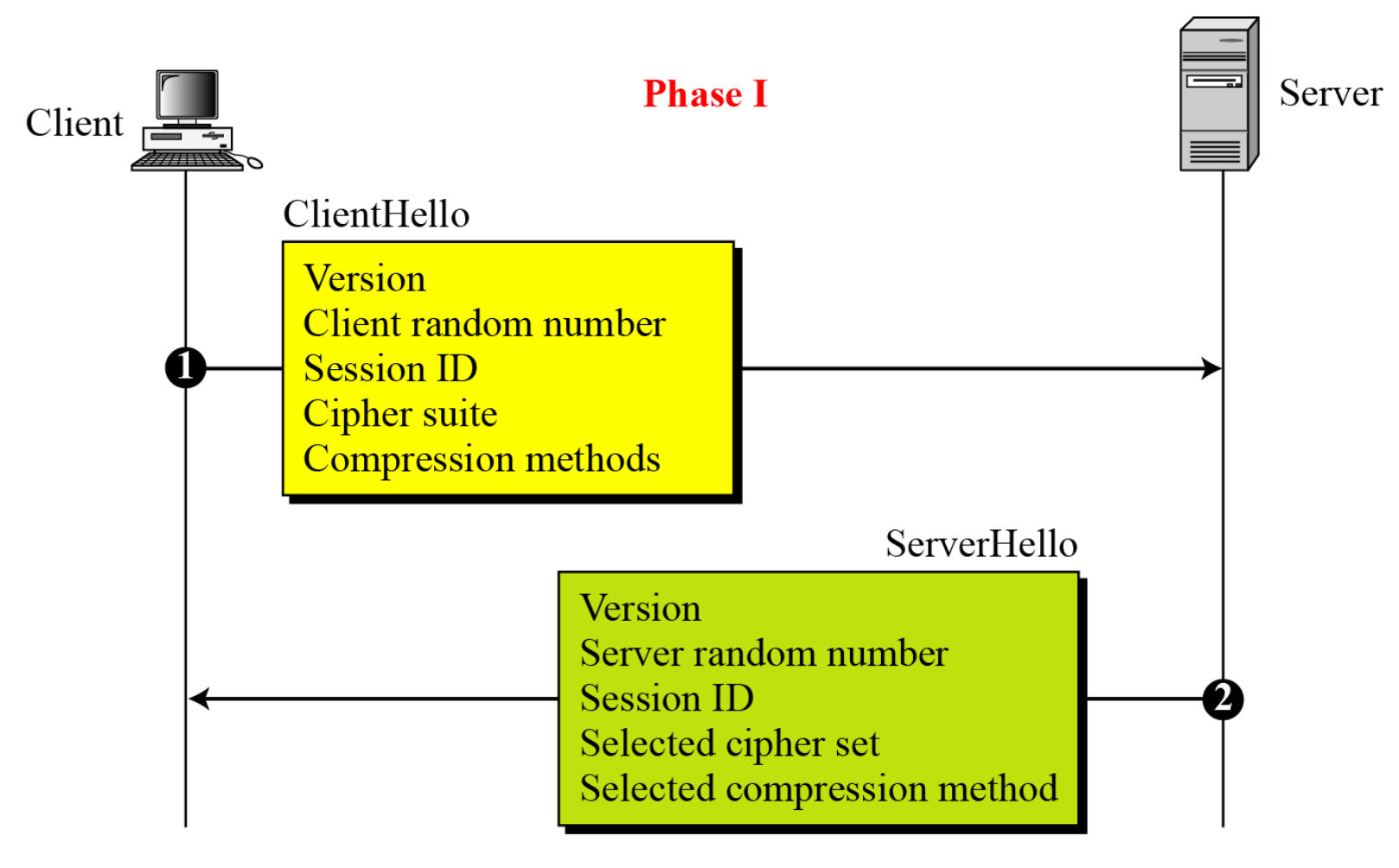
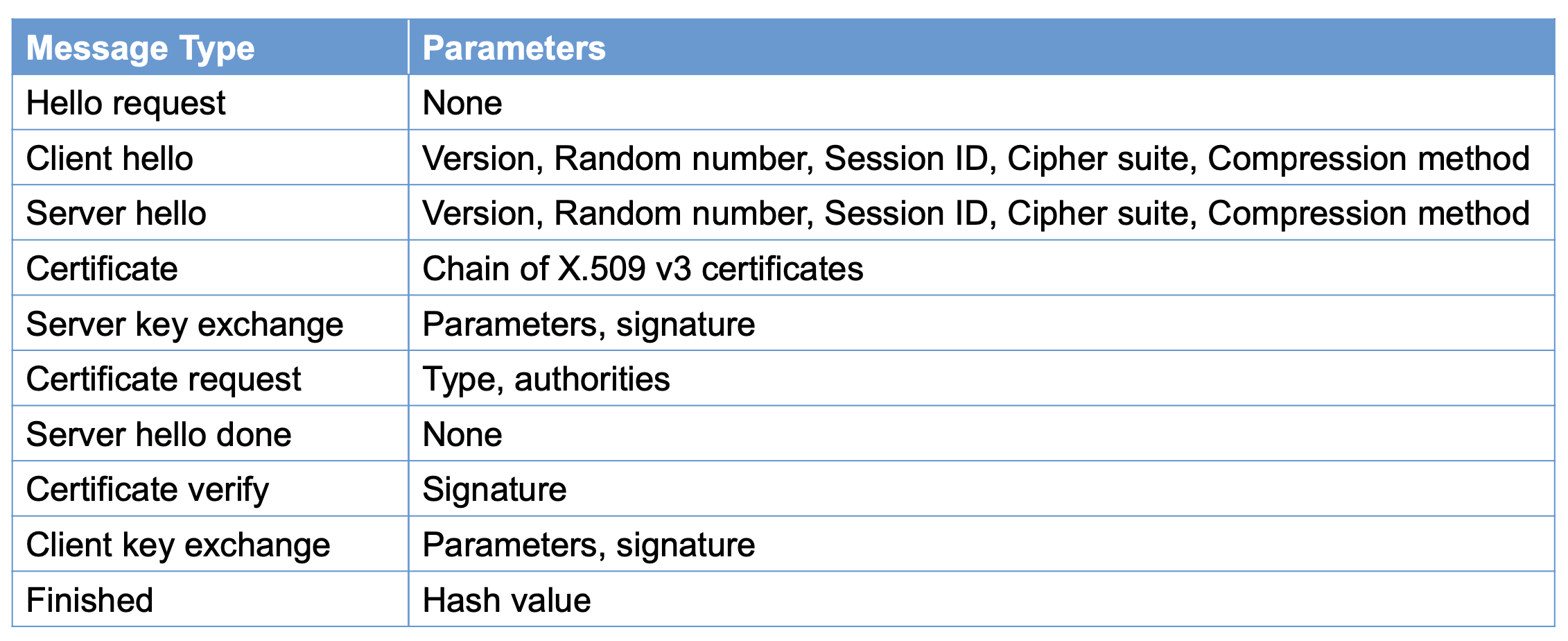
- Client_hello →
- Version: highest version of SSL understood by client
- Random: 32 bit time stamp + 28 random bytes (secure random number generator)
- SessionID: 0 → establish new connection on new session, non-zero means update parameters of an existing session
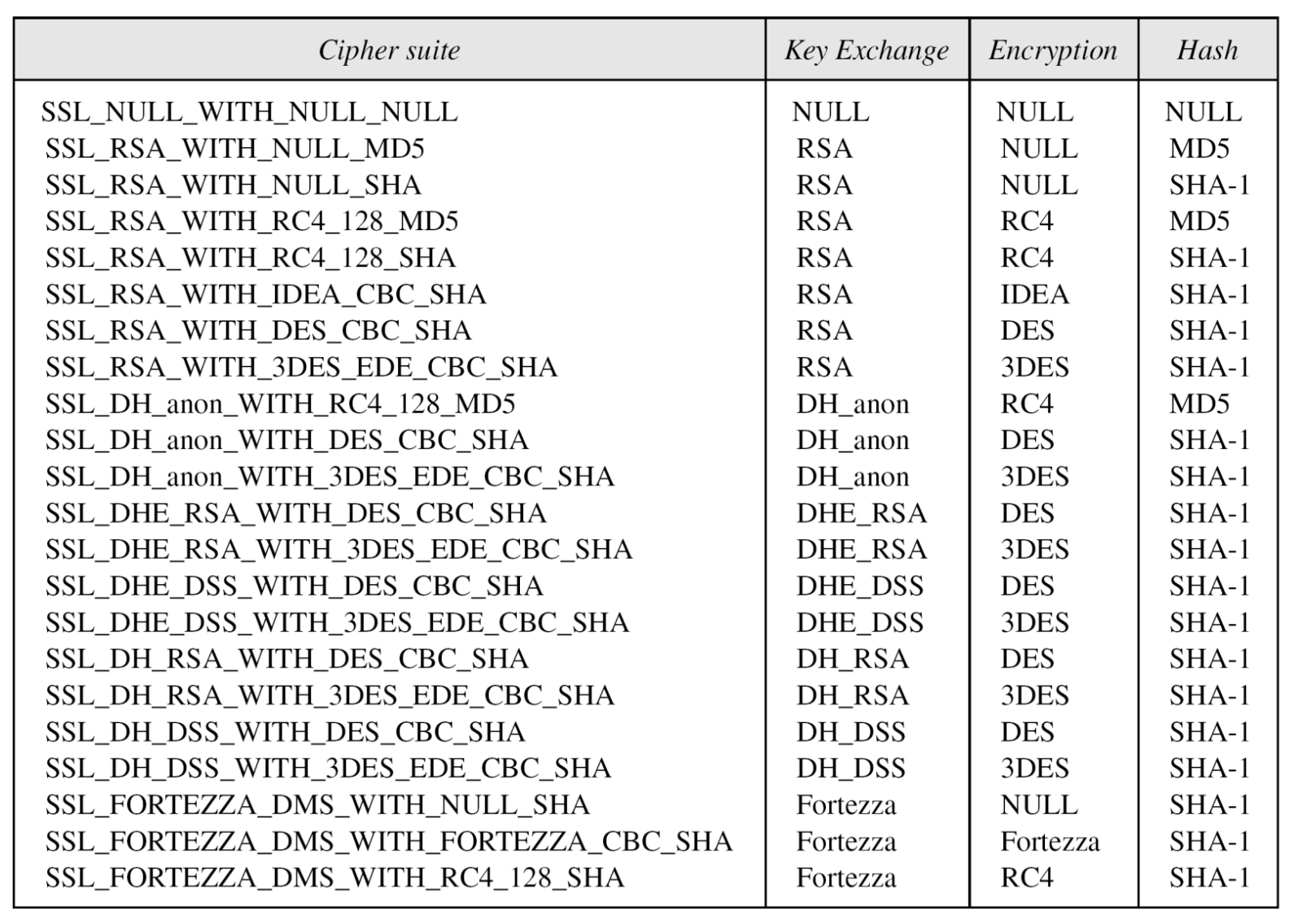
- Cipher suite: sequence of cryptographic algorithms in decreasing order of preference (key exchange + CipherSpec)
- Compression methods: sequence of compression methods
- Server_hello ← is sent back
- Same as above but confirmation
- Highest common version, new random field, same sessionID if nonzero, new sessionID otherwise, the selected cipher suite and the selected compression technique
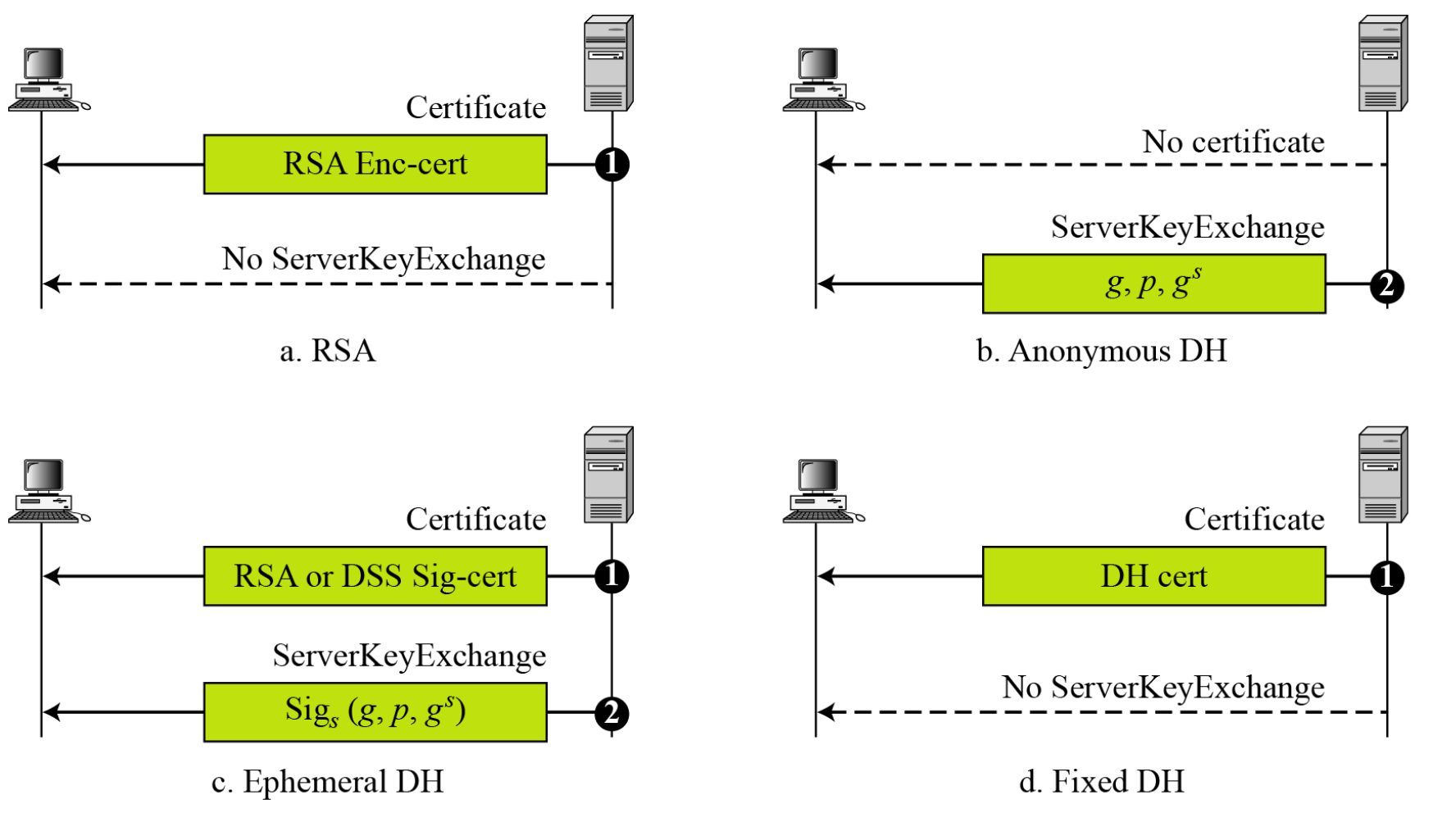
- Key Exchange methods
- RSA – secret key is encrypted with receiver’s RSA public key
- Fixed Diffie-Hellman
- Ephemeral Diffie Hellman
- Anonymous Diffie-Hellman
- Fortezza
- CipherSpec follows containing the fields
- Cipher algorithm
- MAC algorithm
- CipherType: block or stream
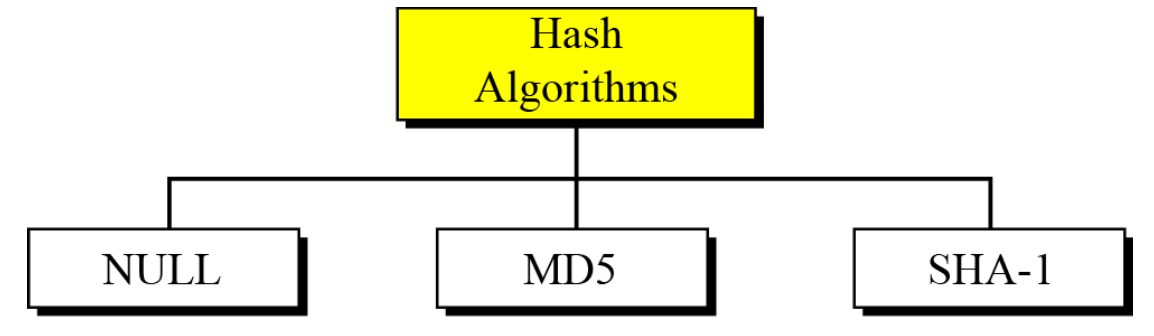
- Hash size: 0, 16 for MD5 or 20 for SHA-1 bytes
- Key material: sequence of bytes used to generate keys
- IV size: The size of Initial Value for Cipher Block Chaining (CBC)
- Encryption/decryption algorithms
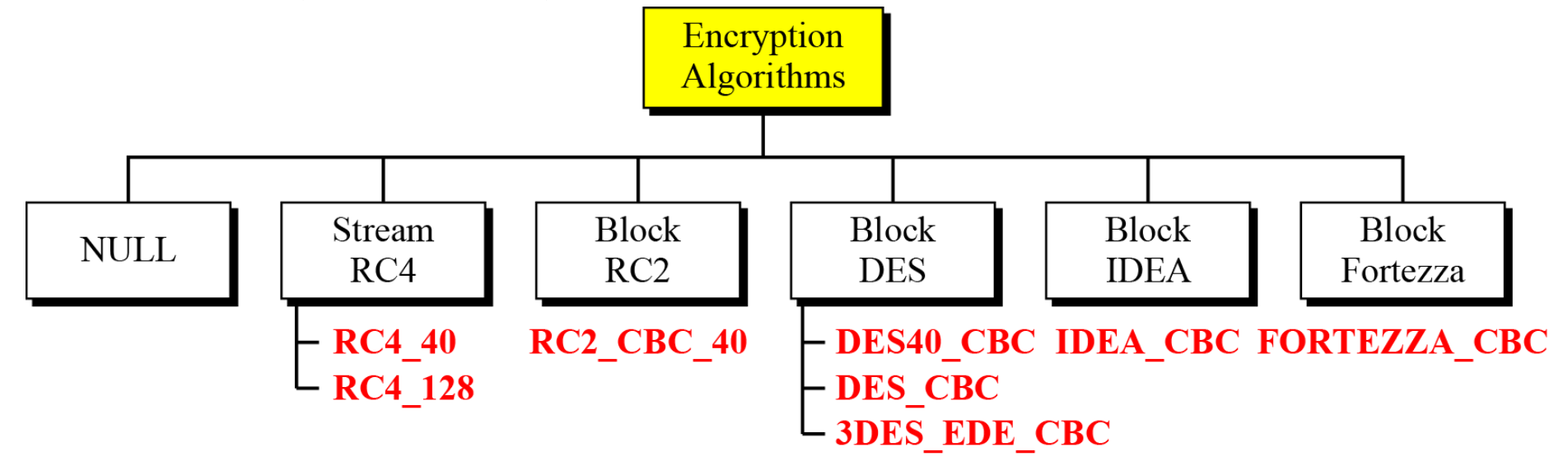
- Hash algorithms for message integrity
- After Phase I, the client and server know the following:
- The version of SSL
- The algorithms for key exchange, message authentication, and encryption
- The compression method
- The two random numbers for key generation
Phase 2: Server authentication and key exchange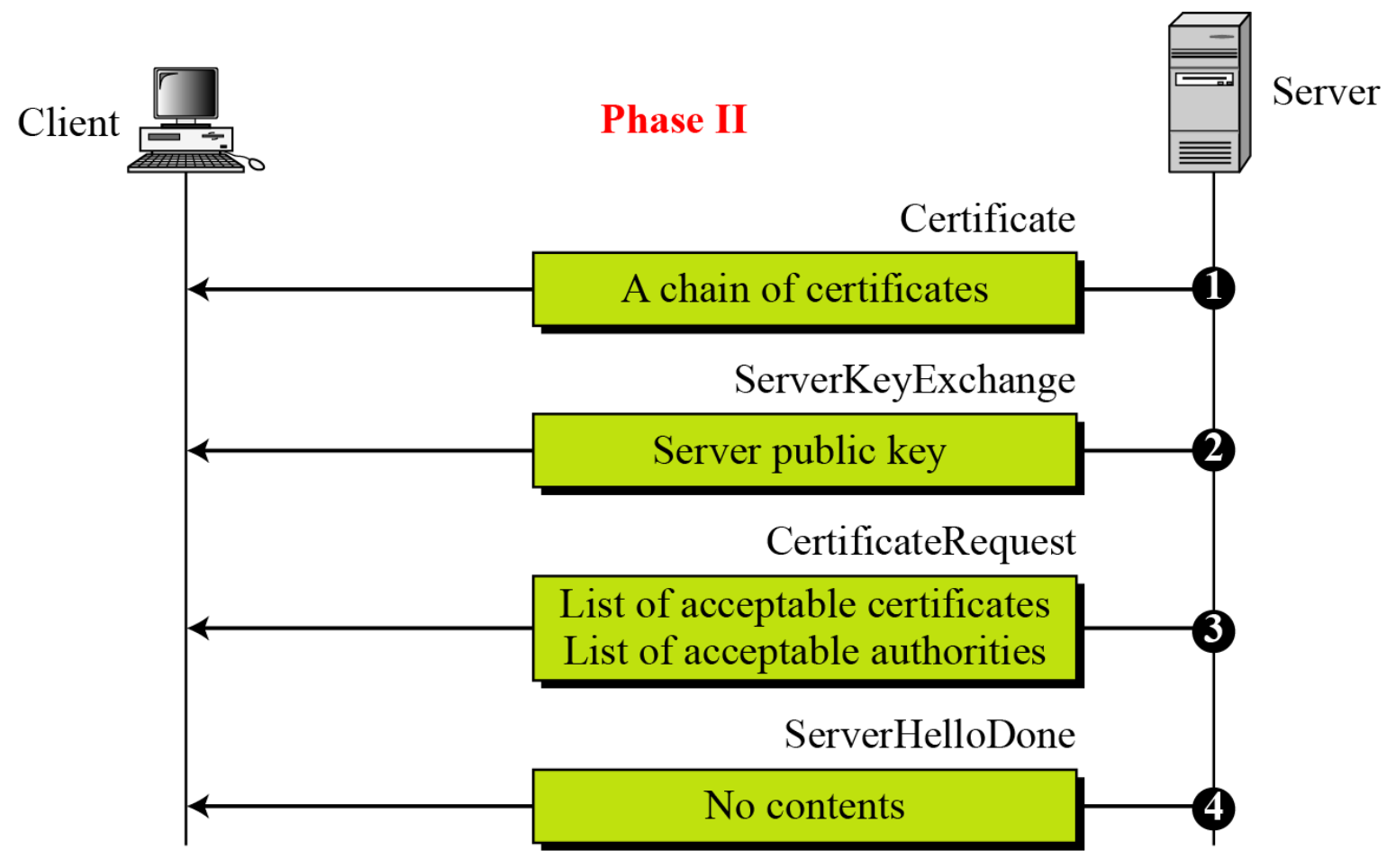
- Server Authentication and Key Exchange
- Server sends
- Certificate: X.509 certificate chain
- Not required for anonymous Diffie-Hellman
- Server_key_exchange
- Not required if the key exchange method is RSA or fixed DH
- Server sends message that includes its contribution to the pre-master secret.
- Certificate_request: certificate type and certificate authorities
- Server_hello_done: I’m done and I’ll wait on response
- Four cases in Phase 2
Phase 3: Client authentication and key exchange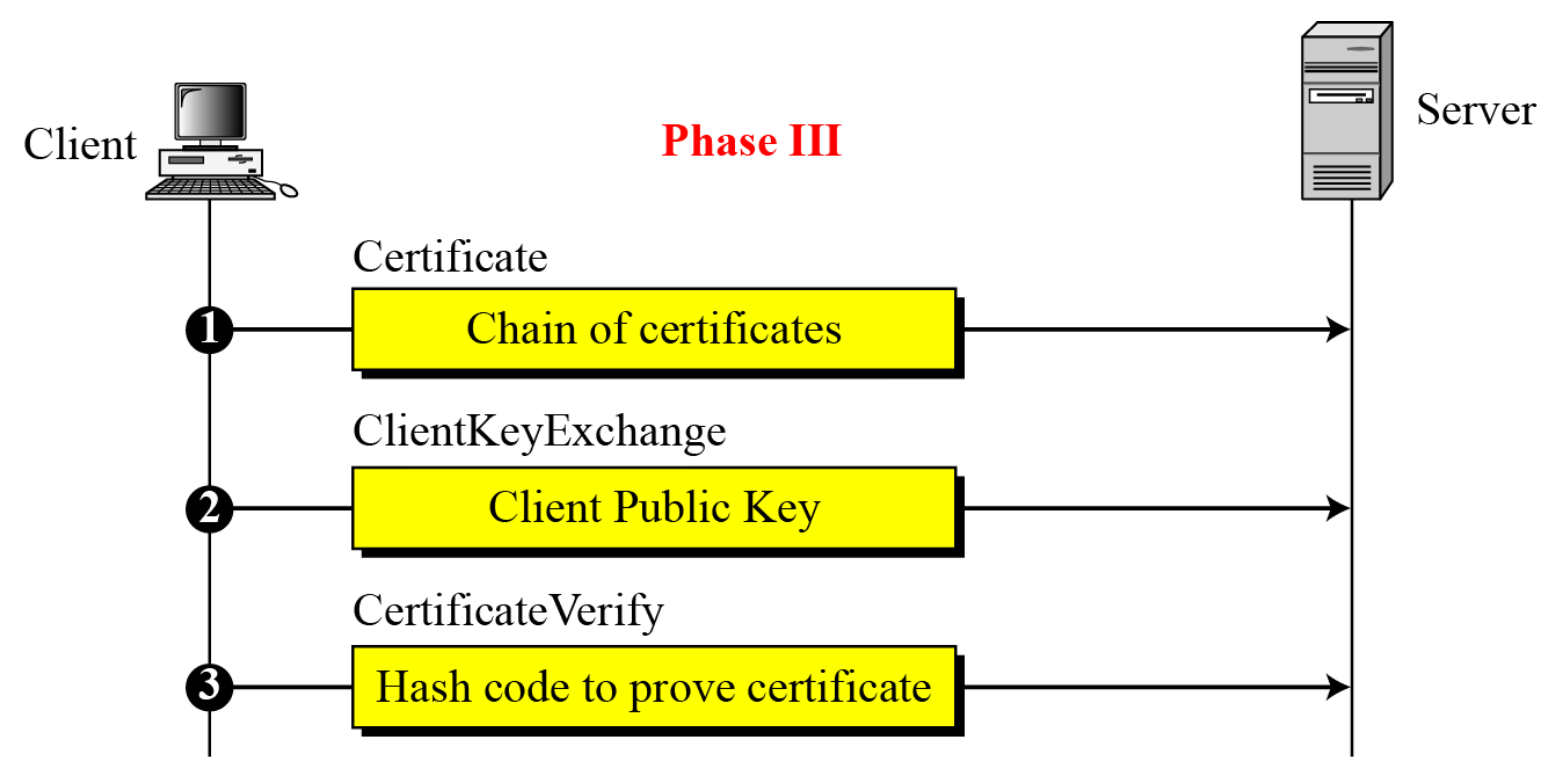
- Client verifies that server provided a valid certificate and checks that the server hello parameters are acceptable.
- Client sends
- Certificate(optional)
- If server demands, client sends its DC; if client does not have a DC, sends a No certificate message; server decides whether to continue or stop
- Client_key_exchange
- Client creates a 48-bytes pre-master secret, encrypts with server’s public key, and sends it to server (or its contribution to the pre-master secret)
- Certificate_verify
- Provide explicit verification of client certificate : “I’ve got the correct private key.”
- Four cases in Phase 3
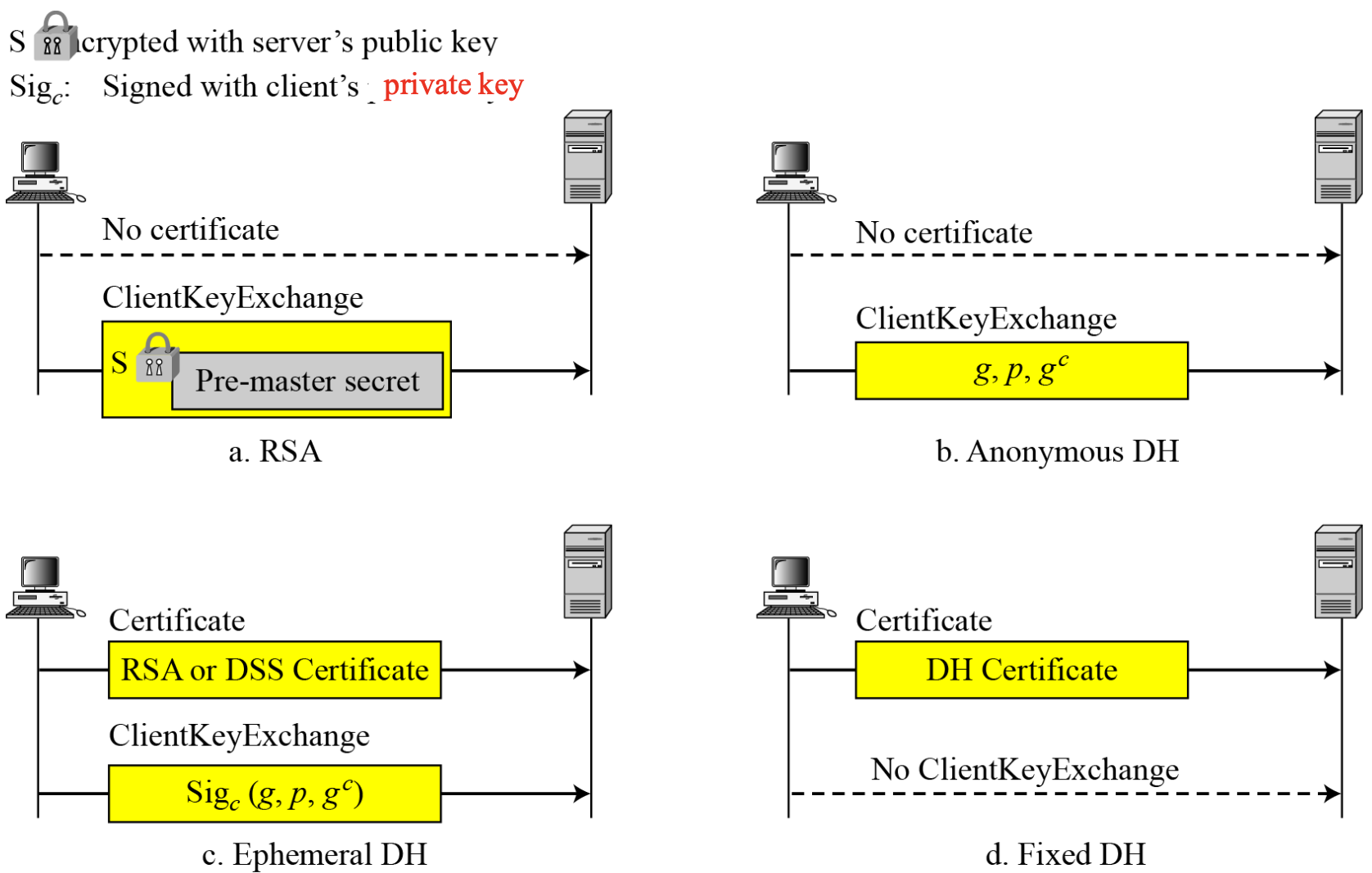
- After Phase 3,
- The client is authenticated for the server.
-4 Both the client and the server know the pre-master secret.
- The client is authenticated for the server.
Phase 4: Finish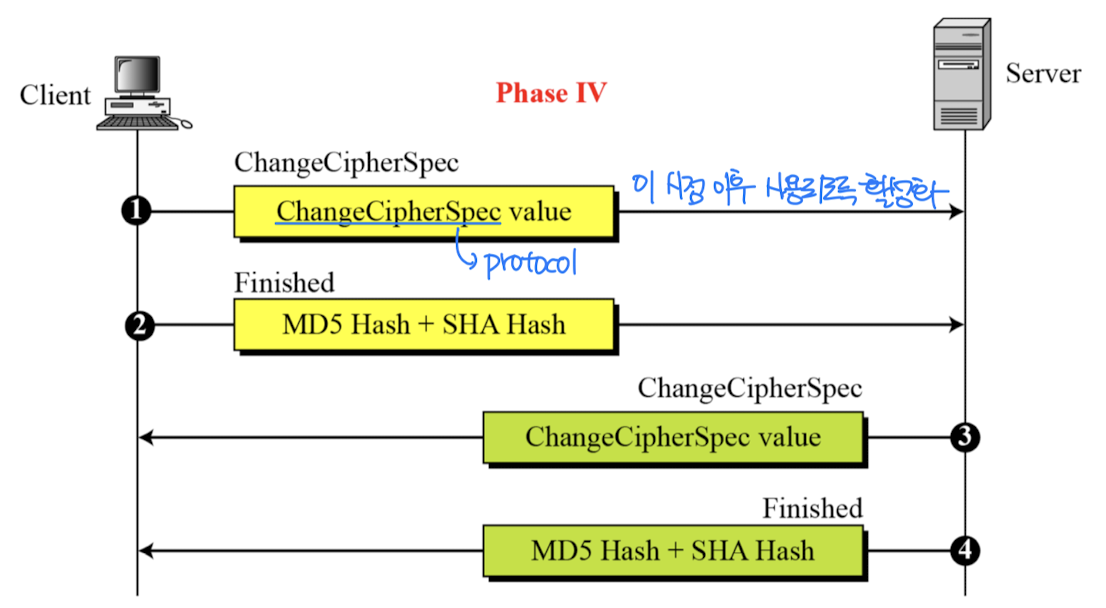
암호화되기 시작, 전에는 Plaintext
- Finish up: switch to next cipher_spec
- Client sends
- Change_cipher_spec message
- Finished message under new algorithms, keys (new cipher_spec)
- Server sends back
- Change_cipher_spec message
- Finished message under new algorithms, keys (new cipher_spec)
- After Phase 4, the client and server are ready to exchange data.
Cryptographic Computations
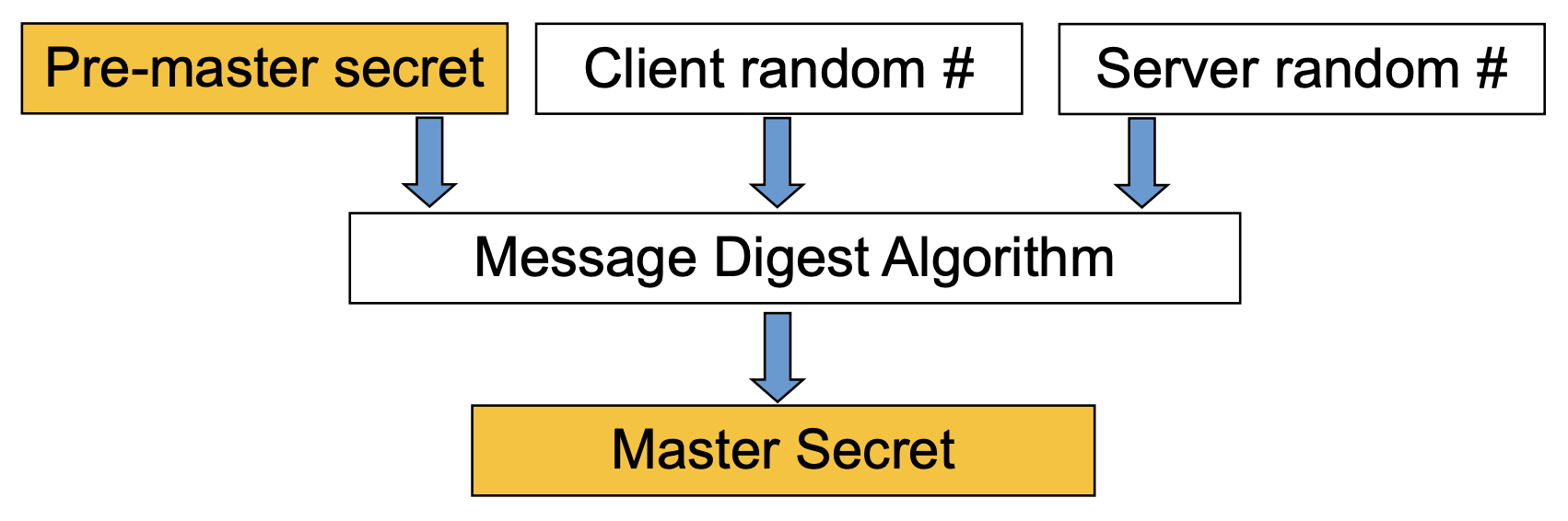
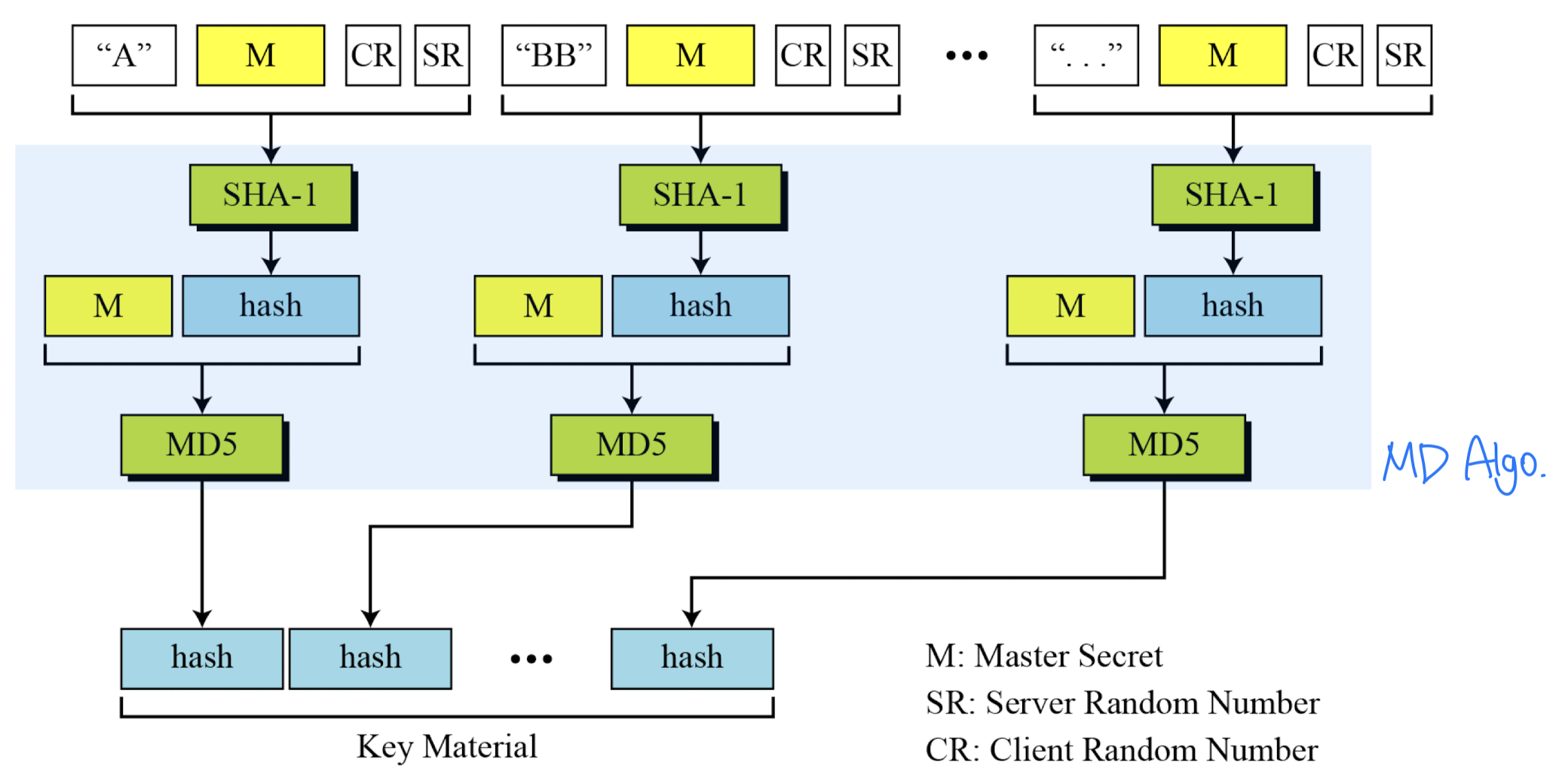
- Master secret creation
- a one-time 48-byte value
- generated using secure key exchange (RSA / Diffie-Hellman) and then hashing info
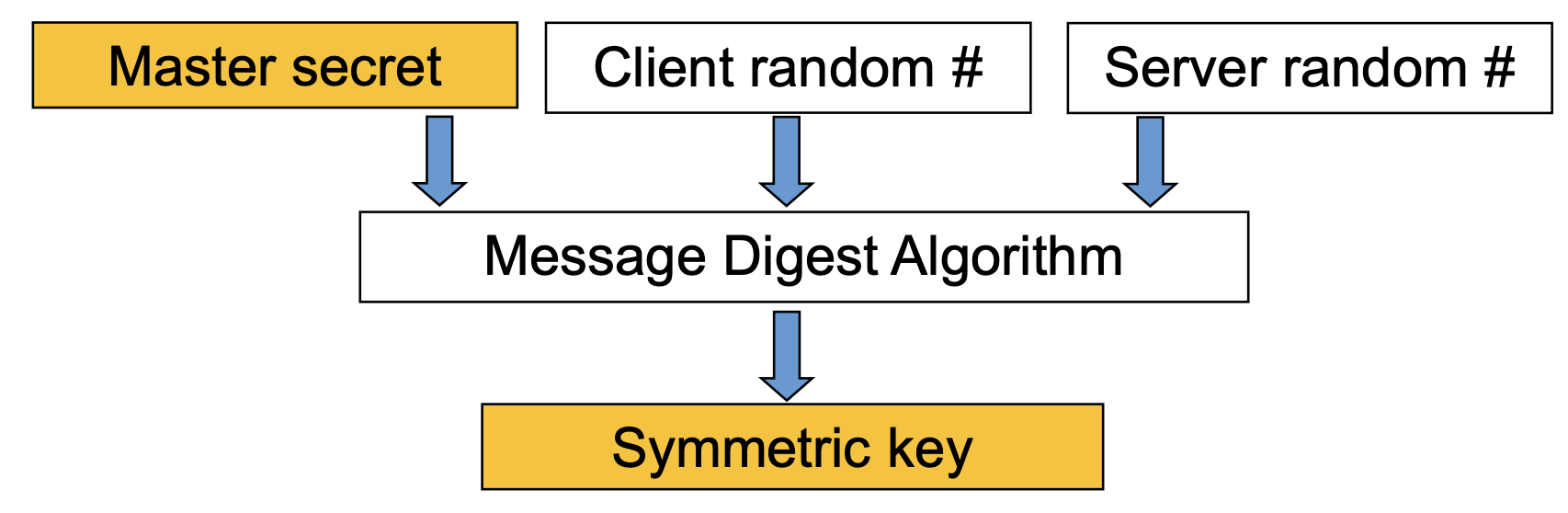
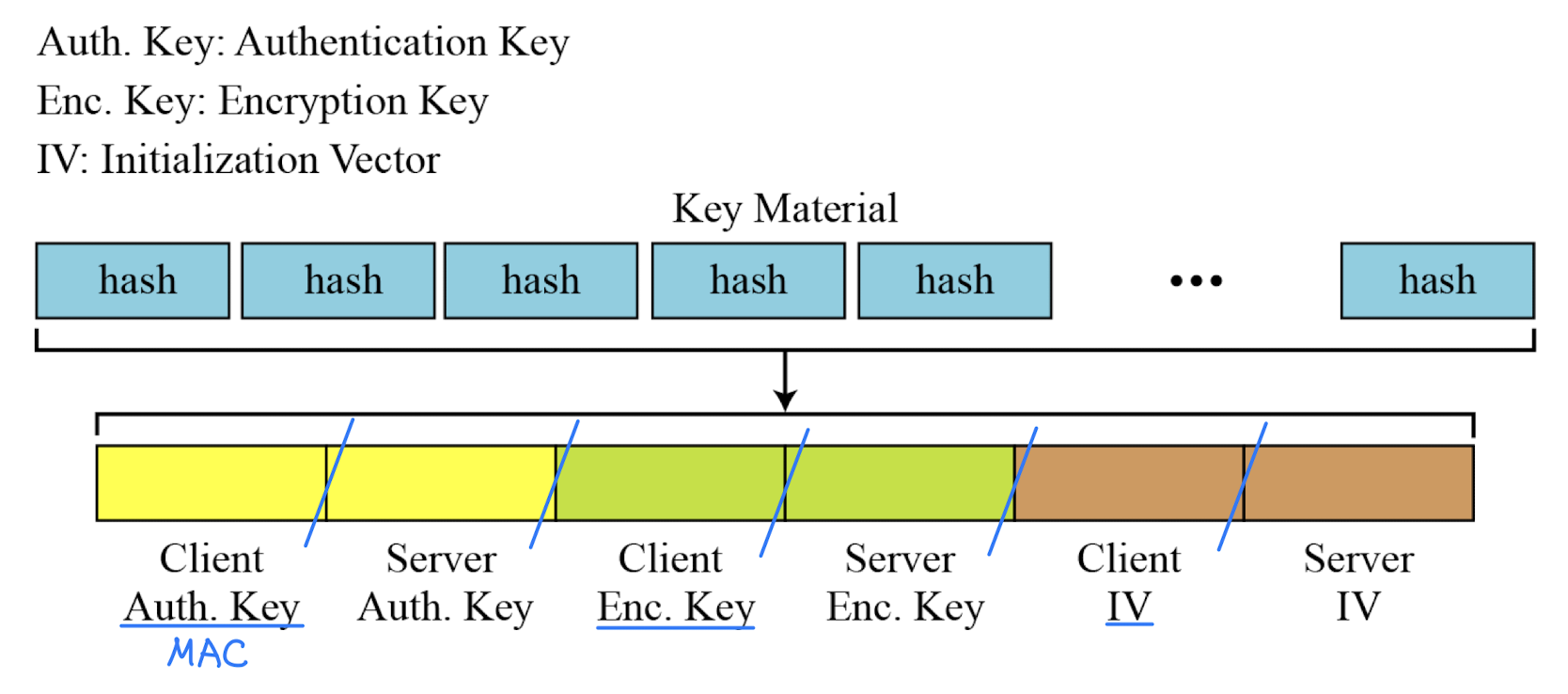
- Generation of cryptographic parameters
- client write MAC secret, a server write MAC secret, a client write key, a server write key, a client write IV, and a server write IV
- generated by hashing master secret
- Client generates a 48-byte pre-master-secret sp
- Master secret:
- Session key is generated in the same way, but use the master secret in place of pre-master-secret to generate byte stream
- Calculation of master secret from pre-master secret
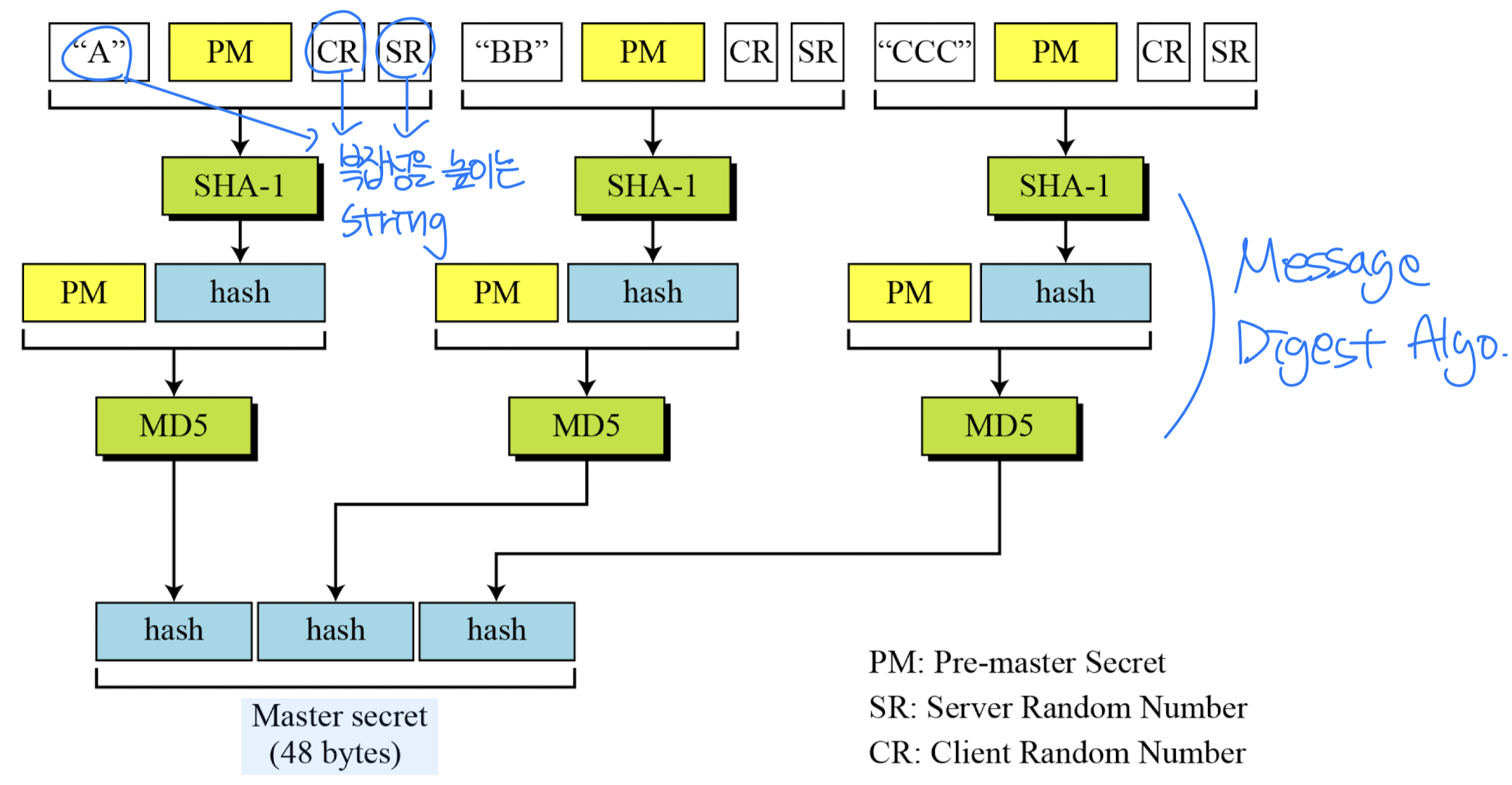
- Calculation of key material from master secret
SSL Record Protocol
SSL Record Protocol Services
- Confidentiality
- using symmetric encryption with a shared secret key defined by Handshake Protocol
- AES, IDEA, RC2-40, DES-40, DES, 3DES, Fortezza, RC4-40, RC4-128
- message is compressed before encryption
- Message integrity
- using a MAC with shared secret key
- similar to HMAC but with different padding
SSL Record Protocol Operation
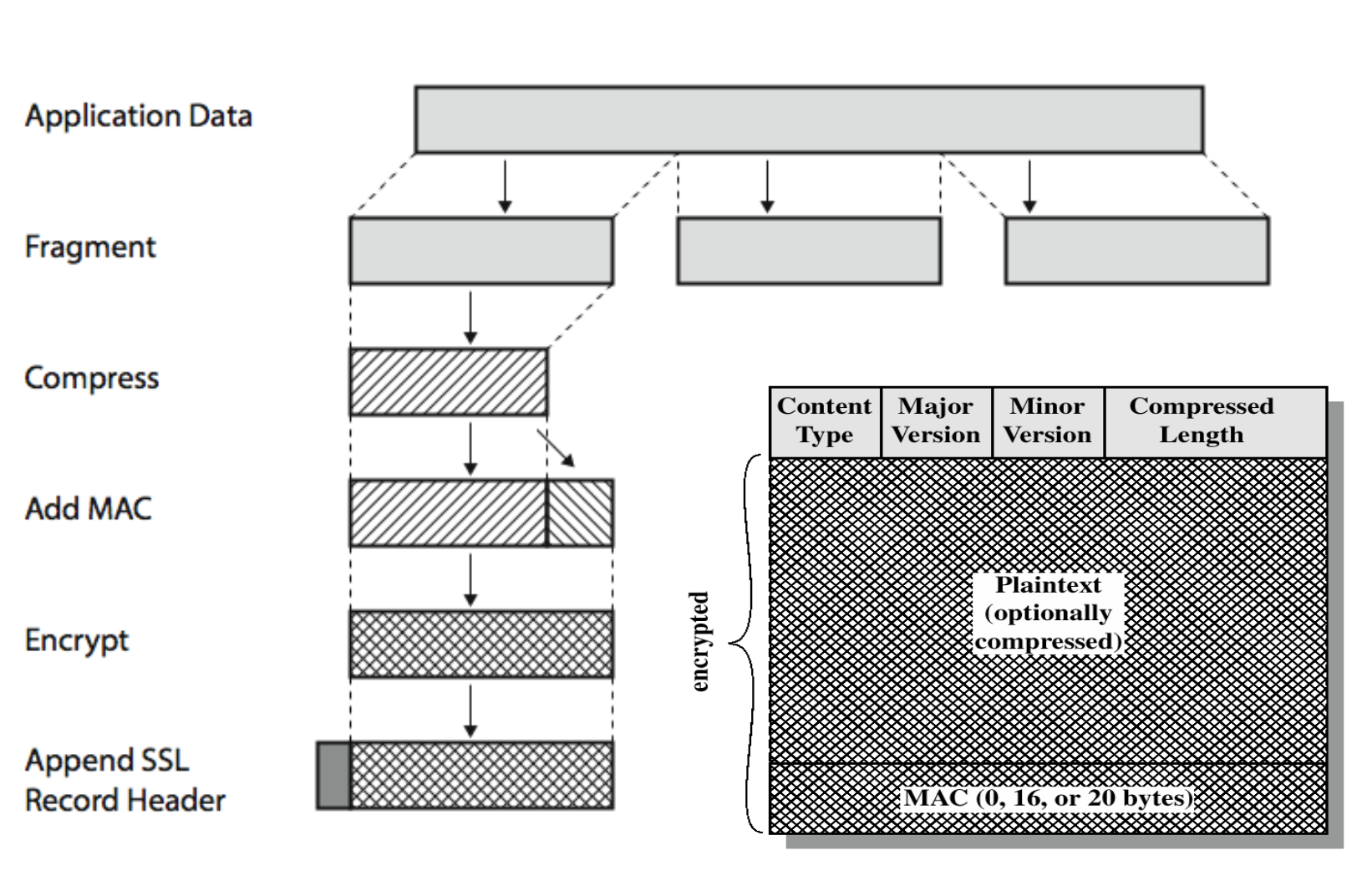
- Fragmentation
- Application message is broken into blocks
- Block size ≤ 214 bytes (16,384bytes)
- Compression
- Optional step
- Must be a lossless compression
- Addition of MAC
- Using the shared key, the MAC for each block is calculated
→ hash(MAC_write_secret, pads, seq_num, etc) - Similar to HMAC, but two pads are concatenated instead of being XORed.
- Using the shared key, the MAC for each block is calculated
- Encryption
- Symmetric encryption
- Encryption may not increase the size by more than 1024 bytes. (combined with the maximum expansion from the compression step)
- For block encryption, padding may be added after MAC prior to encryption.
The total amount of padding is the smallest amount such that the total size of the data to be encrypted is multiple of cipher’s block length.
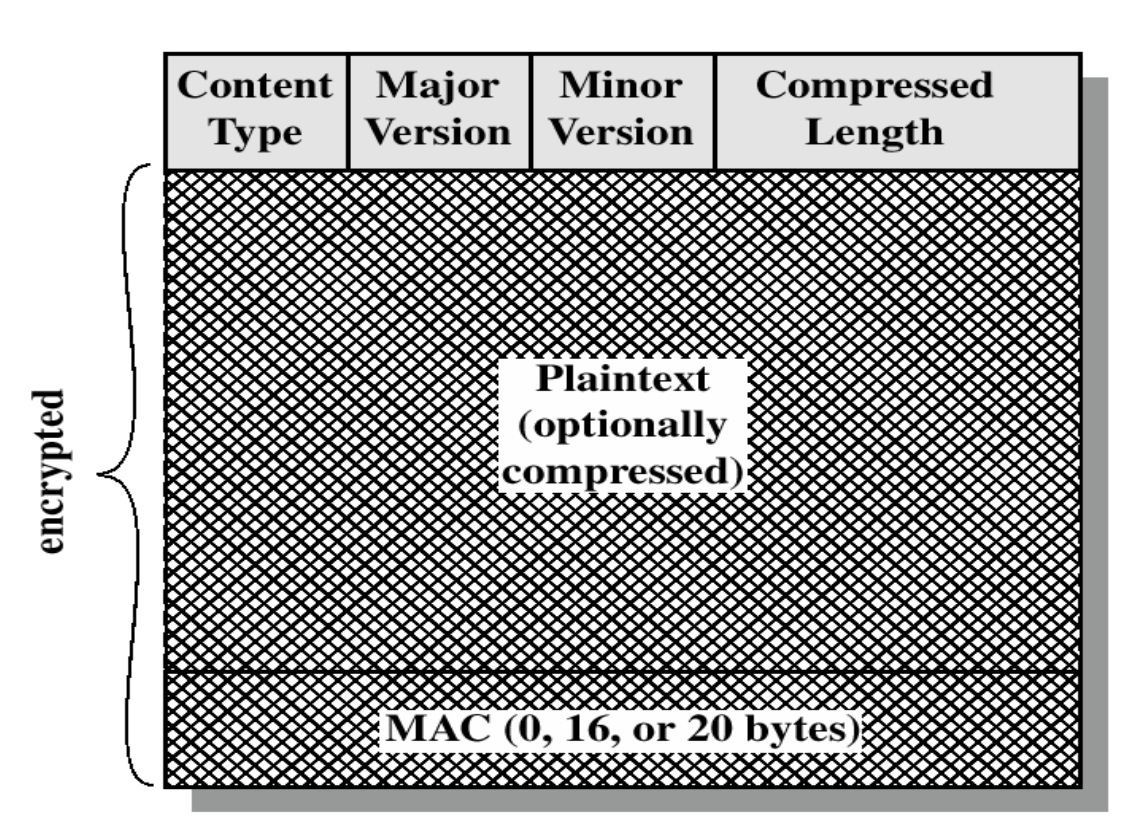
- Append header
- Content type: handshake, alert, or change cipher
- Major version: If version is 3.1, then 3
- Minor version: If version is 3.1, then 1
- Compression length
SSL Change Cipher Spec Protocol and Alert Protocol
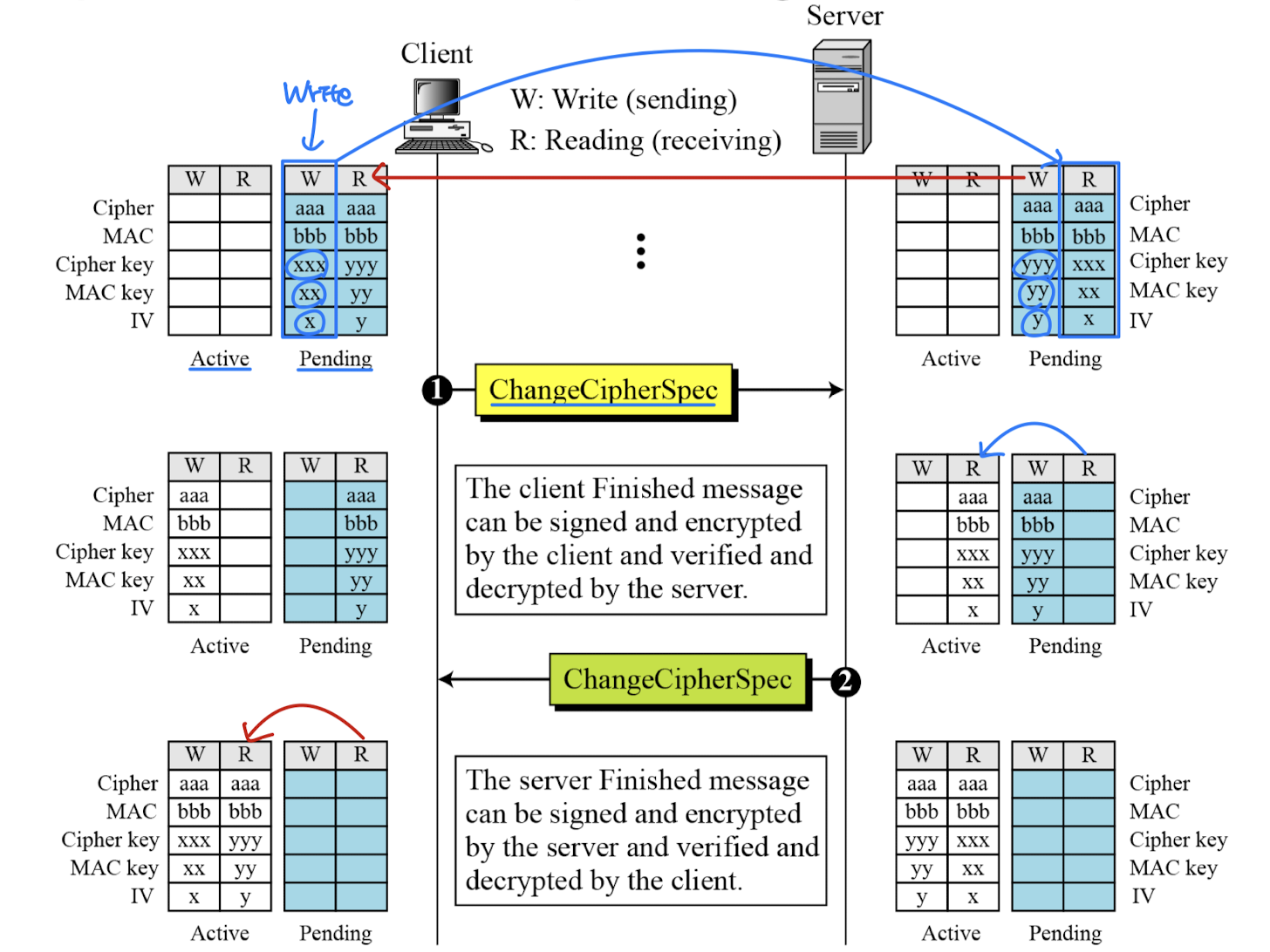
SSL Change Cipher Spec Protocol
- One of 3 SSL specific protocols which use the SSL Record protocol
- A single message
- Causes pending state to become current
- Hence updating the cipher suite in use

- We have seen that the negotiation of the cipher state and the generation of cryptographic secrets are formed gradually during the Handshake protocol.
- The question now is: When can the two parties use these parameters or secrets?
- SSL mandates that the parties cannot use these parameters or secrets until they have sent or received a special message, the ChangeCipherSpec message, which is exchanged during the Handshake protocol and defined in the ChangeCipherSpec Protocol.
- Movement of parameters from pending state to active state
SSL Alert Protocol
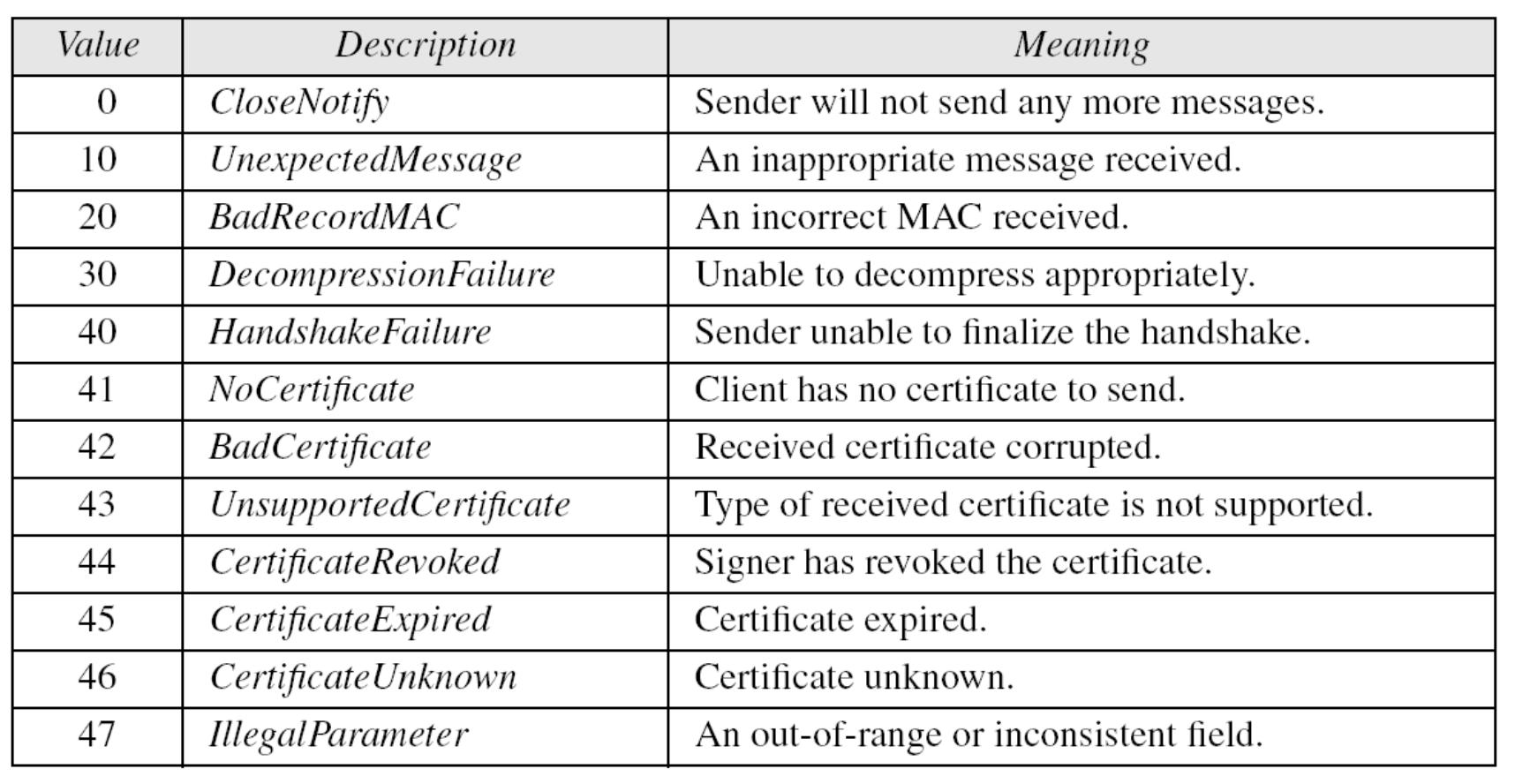
- Conveys SSL-related alerts to peer entity
- Severity
- warning or fatal
- Specific alert
- fatal: unexpected message, bad record mac, decompression failure, handshake failure, illegal parameter
- warning: close notify, no certificate, bad certificate, unsupported certificate, certificate revoked, certificate expired, certificate unknown
- Compressed & encrypted like all SSL data

HGU 전산전자공학부 고윤민 교수님의 24-2 컴퓨터 보안 수업을 듣고 작성한 포스트이며, 첨부한 모든 사진은 교수님 수업 PPT의 사진 원본에 필기를 한 수정본입니다.

