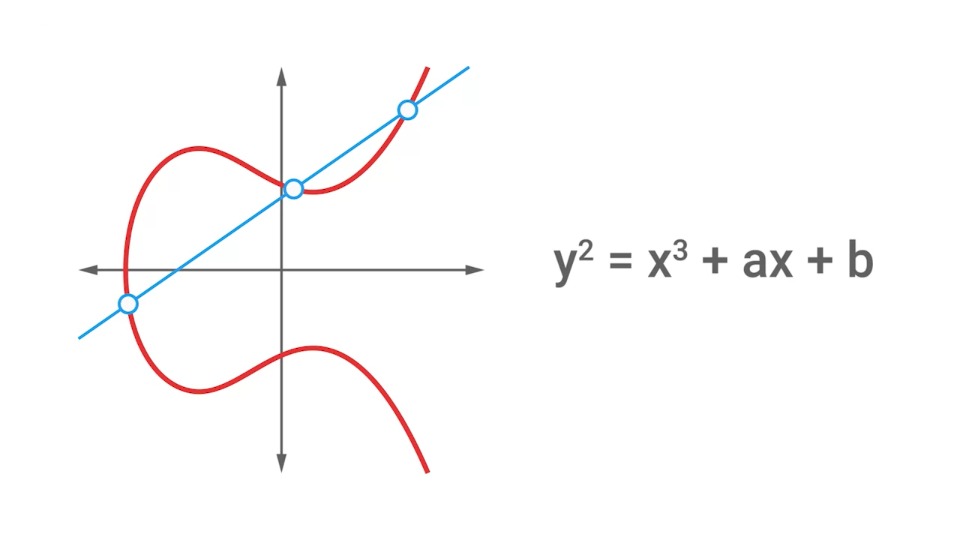Asymmetric Cryptography
Confidentiality
granted through the encryption-decryption mechanism
Authenticity
granted by the digital signature mechanism
Non-repudiation
the author of the message isn't able to dispute the origin of the message.
Message Authentication Code (MACs)
A MAC is a bit of information that allows authentication of a received message, ensuring that the message came from the alleged sender and not a third party masquerading as them.
-
Keyed-Hash Message Authentication Code : HMAC uses a cryptographic hash function along with a secret key to generate a MAC.
-
Cipher-Based Message Authentication Codes : The process is similar to HMAC, but instead of using a hashing function to produce a digest, a symmetric cipher with a shared keys used to encrypt the message and the resulting output is used as the MAC.
-
Cipher Block Chaining Message Authentication Codes : CBC-MAC is a mechanism for building MACs using block ciphers.
This works by taking a message and encrypting it using a block cipher operating in CBC mode.
CBC mode : CBC mode is an operating mode for block ciphers that incorporates a previously encrypted block cipher text into the next block's plain text.
This chain of interdependently encrypted blocks means that any modification to the plain text will result in a different final output at the end of the chain, ensuring message integrity.
Asymmetric Algorithm
RSA
one of the first practical asymmetric cryptography systems
Digital Signature Algorithm (DSA)
It's important to call out that the security of this system is dependent on choosing a random seed value that's incorporated into the signing process.
Diffie-Hellman (DH)
Elliptic curve cryptography (ECC)
A public key encryption system that uses the algebraic structure of elliptic curves over finite fields to generate secure keys.