
이번에 토이 프로젝트로 백신 예약 웹 애플리케이션을 제작 중에 있고 이미 인증 부분은 구현된 상태입니다. 세션을 이용하는 Stateful 상태로 구현되었습니다.
예약 애플리케이션의 경우 특정 날짜, 특정 시간에 사용자가 몰리는 경우가 많습니다. 때문에 scale-out이 용이해야 합니다. 하지만 세션방식을 사용하는 경우 확장에 전혀 용이하지 않습니다.
프로젝트 완성 후 탈세션(?)을 시도하기 위해 토큰방식 인증의 가장 대표적 표준인 JWT를 이용해 인증을 구현해보고자 합니다.
📌 프로젝트 설정
- Springboot 2.5.x
- Maven
- Spring-security
- Lombok
- jjwt (jsonwebtoken) 0.9.1
- jaxb-api 2.3.1
🔎 SeucirtyConfig 설정파일 작성
Spring Security의 설정을 커스텀하기 위한 설정파일을 작성합니다.
/auth 경로로 인증요청을 할 것이므로 접근을 허가하고 그 외 모든 요청은 인증이 필요하도록 했습니다.
sessionCreationPolicy STATELESS 로 설정해주므로 세션을 사용하지 않도록 설정
다음으로 인증객체를 만들어줄 UserDetailsService를 정의합니다.
@RequiredArgsConstructor
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
private final CustomUserDetailsService customUserDetailsService;
private final JwtAuthenticateFilter jwtAuthenticateFilter;
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(customUserDetailsService);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().disable()
.authorizeRequests().antMatchers("/auth").permitAll()
.anyRequest().authenticated();
// Stateless (세션사용X)
http.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
// UsernamePasswordAuthenticationFilter 에 도달하기 전에 커스텀한 필터를 먼저 동작시킴
http.addFilterBefore(jwtAuthenticateFilter, UsernamePasswordAuthenticationFilter.class);
}
@Bean
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
}🔎 UserDetailsService 작성
보통 이 부분에서는 DB에서 username으로 User를 조회해야 하는데 테스트로 간단하게 직접 User 객체를 만들었습니다.
여기서 User객체는 엔티티가 아닙니다 !!
import org.springframework.security.core.userdetails.User;userdetails의 User 클래스입니다.
@RequiredArgsConstructor
@Service
public class CustomUserDetailsService implements UserDetailsService {
private final PasswordEncoder encoder;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
return new User("kim", encoder.encode("1234"), AuthorityUtils.createAuthorityList());
}
}🚀 JwtUtil 작성 (very 중요)
구현한 기능은 아래 6개 입니다.
- 토큰 생성 (
generate-create) - 토큰 유효성 검사 (
isValidToken) - Claim 디코딩 (
getAllClaims) - Claim에서 특정 key값 가져오기 (username)
- 토큰 만료기한 가져오기
- 토큰 만료여부 확인
여기서 Claim은 JWT의 페이로드 부분에 해당합니다.
Map을 상속하고 있기 때문에 편하게 key-value로 넣어주면 됩니다.
현재는 username 만 Claim으로 설정했습니다.
Claim에 값이 들어갈 때 Base64로 인코딩 됩니다. Base64는 공개된 인코딩 기법이기 때문에 디코딩 또한 가능합니다. 때문에 Claim에는 critial한 정보는 담지 않도록 주의합니다.
JWT는 3개 부분으로 나눠집니다.
- Header (서명 알고리즘, 토큰타입)
- Payload (의미있는 정보 key-value)
- Signature (서명 = Header+Payload+secret)
@Slf4j
@Component
public class JwtUtil {
// 설정파일로 빼서 환경변수로 사용하는 것을 권장
private final String SECRET = "secret";
/**
* 토큰 생성
*/
public String generateToken(UserDetails userDetails) {
Claims claims = Jwts.claims();
claims.put("username", userDetails.getUsername());
return createToken(claims, userDetails.getUsername()); // username을 subject로 해서 token 생성
}
private String createToken(Claims claims, String subject) {
return Jwts.builder()
.setClaims(claims)
.setIssuedAt(new Date(System.currentTimeMillis()))
.setExpiration(new Date(System.currentTimeMillis() + 1000 * 60 * 60 * 10)) // 1시간
.signWith(SignatureAlgorithm.HS256, SECRET)
.compact();
}
/**
* 토큰 유효여부 확인
*/
public Boolean isValidToken(String token, UserDetails userDetails) {
log.info("isValidToken token = {}", token);
String username = getUsernameFromToken(token);
return (username.equals(userDetails.getUsername()) && !isTokenExpired(token));
}
/**
* 토큰의 Claim 디코딩
*/
private Claims getAllClaims(String token) {
log.info("getAllClaims token = {}", token);
return Jwts.parser()
.setSigningKey(SECRET)
.parseClaimsJws(token)
.getBody();
}
/**
* Claim 에서 username 가져오기
*/
public String getUsernameFromToken(String token) {
String username = String.valueOf(getAllClaims(token).get("username"));
log.info("getUsernameFormToken subject = {}", username);
return username;
}
/**
* 토큰 만료기한 가져오기
*/
public Date getExpirationDate(String token) {
Claims claims = getAllClaims(token);
return claims.getExpiration();
}
/**
* 토큰이 만료되었는지
*/
private boolean isTokenExpired(String token) {
return getExpirationDate(token).before(new Date());
}
}🔎 토큰 발급 테스트
@Slf4j
@RequiredArgsConstructor
@RestController
public class HomeController {
private final CustomUserDetailsService userDetailsService;
private final JwtUtil jwtUtil;
private final AuthenticationManager authenticationManager; // authenticate 메서드 : username, password 기반 인증 수행
@GetMapping("/home")
public String home() {
return "home";
}
@PostMapping("/auth")
public ResponseEntity<LoginSuccessResponse> authenticateTest(@RequestBody LoginRequest loginRequest) {
log.info("/auth 호출");
try {
// username, password 인증 시도
authenticationManager.authenticate(
new UsernamePasswordAuthenticationToken(loginRequest.getUsername(), loginRequest.getPassword()));
} catch (BadCredentialsException e) {
throw new BadCredentialsException("로그인 실패");
}
// 인증 성공 후 인증된 user의 정보를 갖고옴
UserDetails userDetails = userDetailsService.loadUserByUsername(loginRequest.username);
// subject, claim 모두 UserDetails를 사용하므로 객체를 그대로 전달
String token = jwtUtil.generateToken(userDetails);
// 생성된 토큰을 응답 (Test)
return ResponseEntity.ok(new LoginSuccessResponse(token));
}
// 인증요청 객체
@AllArgsConstructor
@Data
static class LoginRequest{
private String username;
private String password;
}
// 인증요청에 대한 응답 객체
@AllArgsConstructor
@Data
static class LoginSuccessResponse {
private String token;
}
}/auth 로 username=kim, password=1234 요청
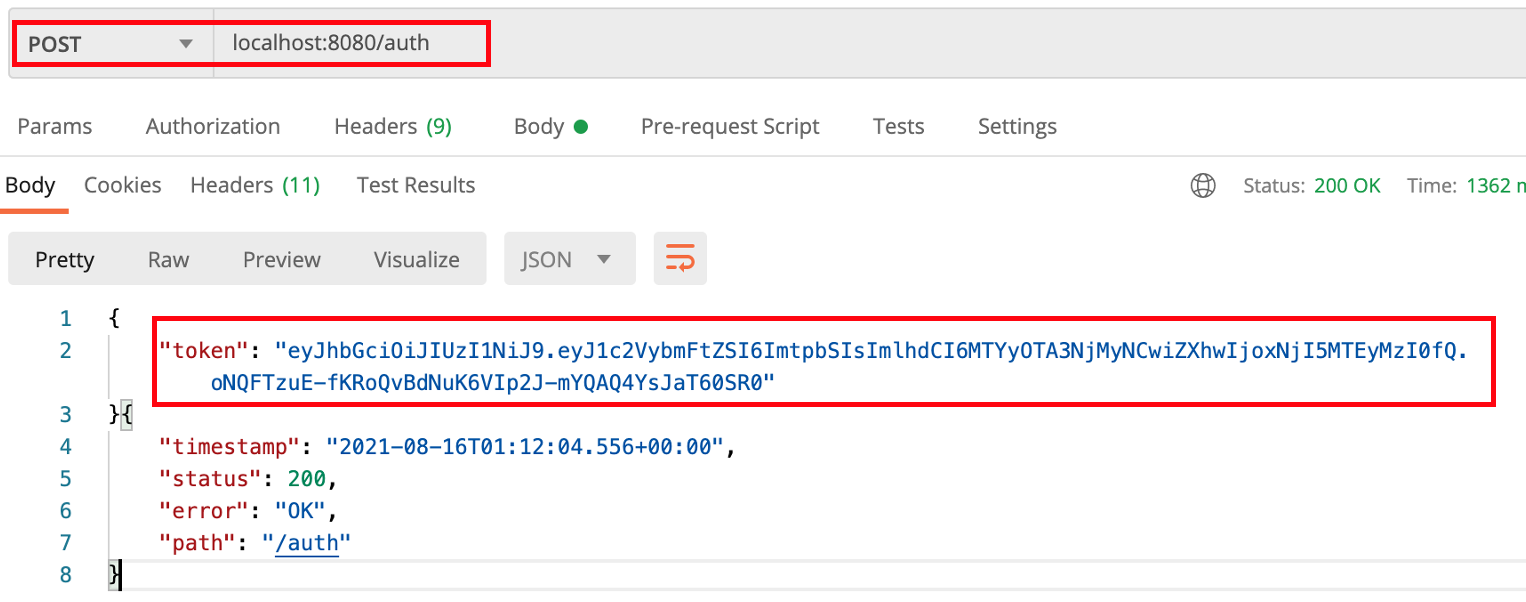
토큰이 정상적으로 발급되었습니다.
이제 클라이언트가 발급된 토큰을 들고 인증요청을 했을 때 서버측 처리를 구현해볼께요.
🔎 토큰 검증 (JwtFilter)
이제 인증을 필요로 하는 경로로 요청이 들어왔을 때 username, password를 기반으로 인증하는 방식이 아니고 클라이언트가 들고온 토큰의 유효여부로 판단해야 합니다.
Spring security는 여러 개 필터가 등록되어 있는데 그 중 하나인 UsernamePasswordAuthenticationFilter가 전달된 username과 password로 인증을 진행합니다.
그럼 우리는 UsernamePasswordAuthenticationFilter 앞쪽에 토큰을 검증하는 필터를 넣어주면 됩니다. 일단 필터부터 만들어볼께요.
@Slf4j
@RequiredArgsConstructor
@Component
public class JwtAuthenticateFilter extends OncePerRequestFilter {
private final CustomUserDetailsService userDetailsService;
private final JwtUtil jwtUtil;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {
String authorization = request.getHeader("Authorization"); // 헤더 파싱
String username = "", token = "";
if (authorization != null && authorization.startsWith("Bearer ")) { // Bearer 토큰 파싱
token = authorization.substring(7); // jwt token 파싱
username = jwtUtil.getUsernameFromToken(token); // username 얻어오기
} else {
filterChain.doFilter(request, response);
}
// 현재 SecurityContextHolder 에 인증객체가 있는지 확인
if (username != null && SecurityContextHolder.getContext().getAuthentication() == null) {
UserDetails userDetails = userDetailsService.loadUserByUsername(username);
// 토큰 유효여부 확인
log.info("JWT Filter token = {}", token);
log.info("JWT Filter userDetails = {}", userDetails.getUsername());
if (jwtUtil.isValidToken(token, userDetails)) {
UsernamePasswordAuthenticationToken usernamePasswordAuthenticationToken
= new UsernamePasswordAuthenticationToken(userDetails, null, userDetails.getAuthorities());
usernamePasswordAuthenticationToken
.setDetails(new WebAuthenticationDetailsSource().buildDetails(request));
SecurityContextHolder.getContext().setAuthentication(usernamePasswordAuthenticationToken);
}
}
filterChain.doFilter(request,response);
}
}필터 진행 흐름
1. 요청 헤더에 Authorization이 있는가 ?
2. Authorization의 값이 Bearer 토큰 타입인가?
3. (1,2) 만족시 전달된 토큰을 받아오고 subject를 파싱
4. 현재 SecurityContext에 인증된 객체가 없는가?
5. (4) 만족시 UserDetails get
6. 토큰이 유효한가 ?
7. 토큰이 유효하다면 인증객체를 생성하여 SecurityContext에 세팅
OncePerRequestFilter?
OncePerRequestFilter 는 이름 그대로 한 번의 요청 당 한 번만 실행을 보장하는 필터입니다.
"같은 request 객체를 사용하는 한 이 필터를 다시 타지 않는다" 라고 이해해도 될 것 같네요.
Bearer Token?
토큰의 타입 중 하나로 jwt, oauth2 에서 Access token으로 사용됩니다.
필터 적용
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().disable()
.authorizeRequests().antMatchers("/auth").permitAll()
.anyRequest().authenticated();
// Stateless (세션사용X)
http.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
// UsernamePasswordAuthenticationFilter 에 도달하기 전에 커스텀한 필터를 먼저 동작시킴
http.addFilterBefore(jwtAuthenticateFilter, UsernamePasswordAuthenticationFilter.class);
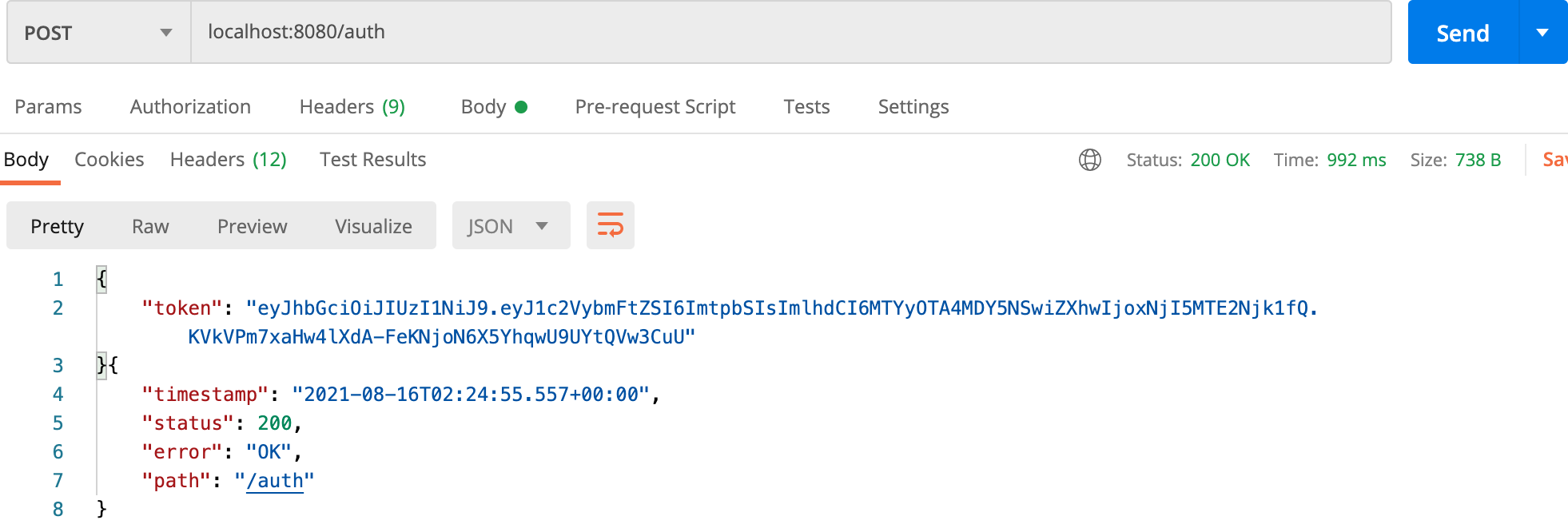
}🔎 토큰검증 테스트
토큰 발급
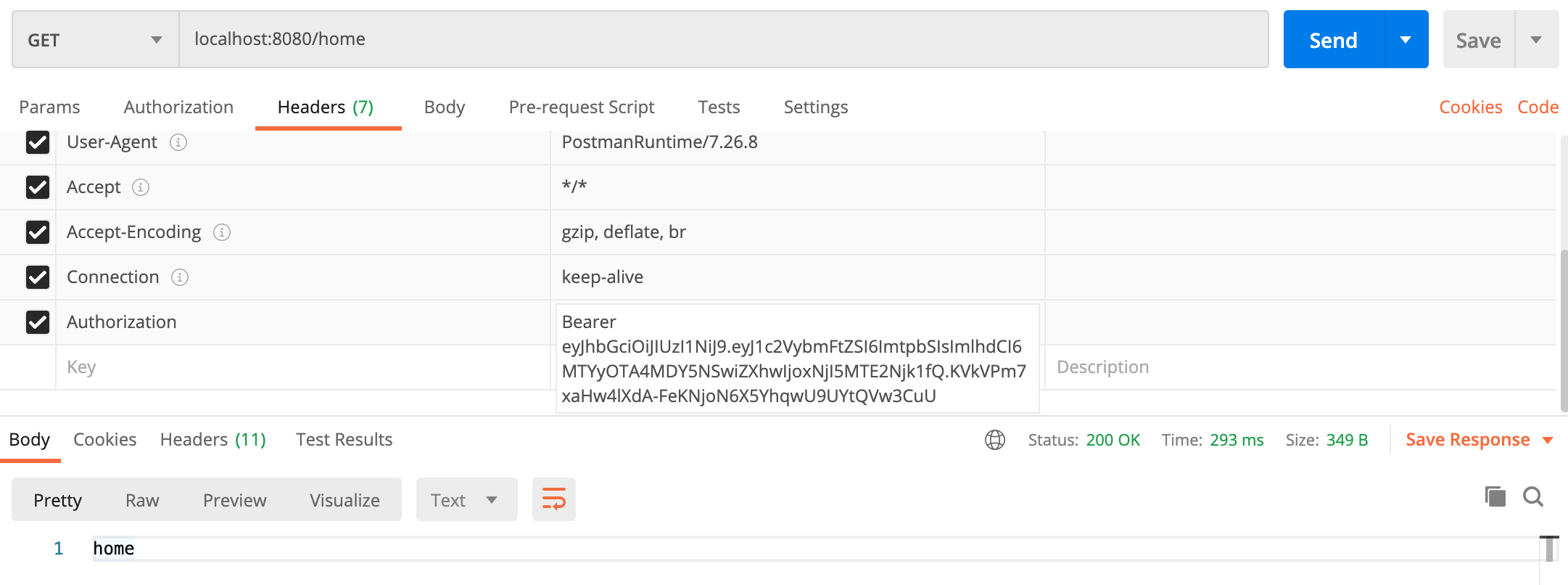
발급된 토큰으로 인증 요청 (/home 으로 요청)
아주 간단하게 JWT에 대해 알아보았습니다.
다음에는 DB, JPA, MVC 등을 추가해서 보다 실무적인 예제를 소개해보겠습니다.
감사합니다. 😄
좋은글 감사합니다!