프로젝트 구현(ver.1)
🧸 프로젝트 구조
- 전체 참고 : Spring Boot JWT Tutorial
- 사용 정보
DB
MySQL : 15.1 Distrib 10.4.24-MariaDB, for Win64 (AMD64)
Redis : 3.0.504
Framework
SpringBoot 2.6.8
Program
IntelliJ IDEA Community Edition 2022.3.1
Xampp v3.3.0
Postman for Windows Version 10.9.2
-
메인
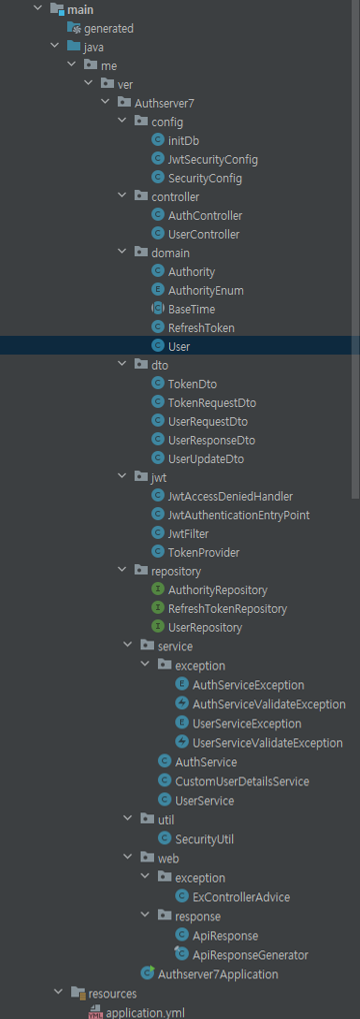
-
테스트
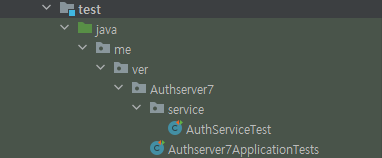
⚙️AuthService만 진행
- 이유? : 테스트 코드를 짜는 것 자체가 "처음"이어서, 기본적인 가입과 로그인 이외에는 어떤식으로 짜야할지 감이 안오기도 하고, 시간을 너무 많이 들이게 되어 다음 서버인 알림 서버를 개발하지 못할 가능성이 높아지기에 우선 (정보 조회, 수정, 탈퇴) 이 3가지는 테스트를 제외하기로 했다.
- 그 대신? : 프로젝트를 올릴때는 지우겠지만, POSTMAN을 이용해 테스트할 때 에러로그까지 뽑아내어 같이 확인하고 수정하는 과정을 거쳤다.
🧸 프로젝트 코드 설명
- 패키지 별로 설명 & import문 생략
- 프로젝트의 스펙에 대해서...
-> 이번 캠프를 통해 처음으로 스프링을 시작하게 되었고, 그렇기에 어떤 기술을 지향하고 지양하는 수준의 개발을 어려울 것이라 판단했으며 기본적인 튜토리얼로 배운 기술을 최대한 사용해보는 것을 목표로 했기에 기술 사용에 대해 비효율적인 부분이 있을 수 있습니다! 양해부탁드립니다😢
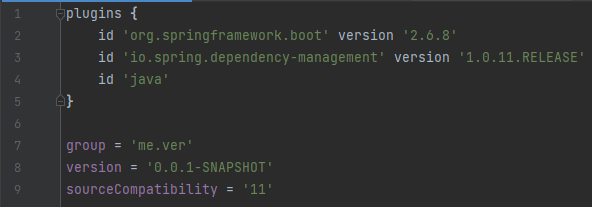
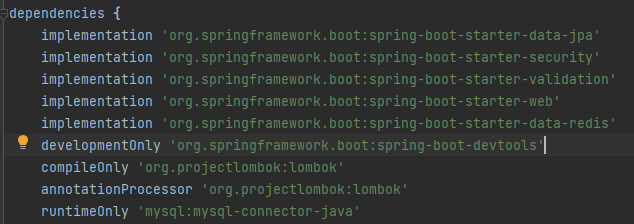
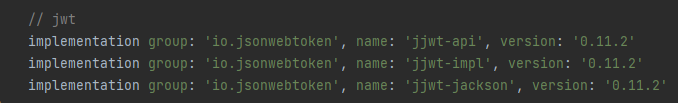
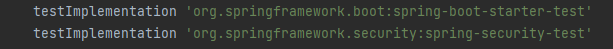
📌 build.gradle
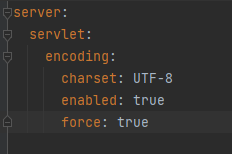
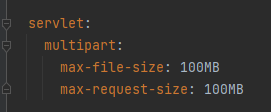
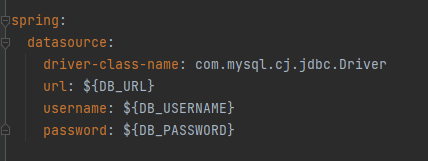
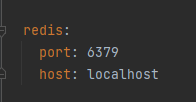
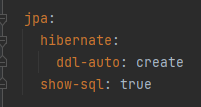
📌application.yml
🗂️ config
1. initDb
- 해당 스프링 프로젝트가 실행할 때, 호출되어 DB를 구성
@PostConstruct: spring web application server가 올라와서 bean이 생성, 그다음 호출
package me.ver.Authserver7.config;
import...
import javax.annotation.PostConstruct;
/**
* INSERT INTO authority (AUTHORITY_STATUS) values ('ROLE_USER');
* INSERT INTO authority (AUTHORITY_STATUS) values ('ROLE_ADMIN');
*/
@Component
@RequiredArgsConstructor
public class initDb {
private final InitService initService;
@PostConstruct
public void init() {
initService.dbInit();
}
@Component
@Transactional
@RequiredArgsConstructor
static class InitService {
private final AuthorityRepository authorityRepository;
public void dbInit() {
authorityRepository.save(new Authority(AuthorityEnum.ROLE_ADMIN));
authorityRepository.save(new Authority(AuthorityEnum.ROLE_USER));
}
}
}2. JwtSecurityConfig
@RequiredArgsConstructor: 직접 만든 TokenProvider와 JwtFilter를 SecurityConfig에 적용하기 위해서 사용함.SecurityConfigurerAdapter<DefaultSecurityFilterChain, HttpSecurity> {: 직접 만든 JwtFilter를 Security Filter 앞에 추가함.
package me.ver.Authserver7.config;
import...
@RequiredArgsConstructor
public class JwtSecurityConfig extends SecurityConfigurerAdapter<DefaultSecurityFilterChain, HttpSecurity> {
private final TokenProvider tokenProvider;
private final StringRedisTemplate redisTemplate;
@Override
public void configure(HttpSecurity http) {
JwtFilter customFilter = new JwtFilter(tokenProvider, redisTemplate);
http.addFilterBefore(customFilter, UsernamePasswordAuthenticationFilter.class);
}
}3. SecurityConfig
.sessionCreationPolicy(SessionCreationPolicy.STATELESS): 시큐리티는 기본적으로 세션을 사용하지만, 이 프로젝트에서 사용하지 않기 위해 stateless로 설정..exceptionHandling(): exception을 핸들링 할때 직접 만든 클래스를 추가함..apply(new JwtSecurityConfig(tokenProvider, redisTemplate));: JwtFilter를 addFilterBefore로 등록한 JwtSecurityConfig의 클래스를 적용함.
package me.ver.Authserver7.config;
import...
@EnableWebSecurity
@EnableGlobalMethodSecurity(prePostEnabled = true)
@RequiredArgsConstructor
public class SecurityConfig extends WebSecurityConfigurerAdapter {
private final TokenProvider tokenProvider;
private final JwtAuthenticationEntryPoint jwtAuthenticationEntryPoint;
private final JwtAccessDeniedHandler jwtAccessDeniedHandler;
private final StringRedisTemplate redisTemplate;
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.httpBasic().disable()
.csrf().disable()
.sessionManagement()
.sessionCreationPolicy(SessionCreationPolicy.STATELESS)
.and()
.exceptionHandling()
.authenticationEntryPoint(jwtAuthenticationEntryPoint)
.accessDeniedHandler(jwtAccessDeniedHandler)
.and()
.apply(new JwtSecurityConfig(tokenProvider, redisTemplate));
}
}
🗂️ controller
1. AuthController
- 회원가입, 로그인, 토큰 재발급을 처리하는 API
UserRequestDto: 사용자가 로그인을 시도한 email과 password String이 있음.TokenRequestDto: 토큰 재발급을 위해, AccessToken & RefreshToken String이 있음.
package me.ver.Authserver7.controller;
import...
@RestController
@RequestMapping("/api/v1/auth")
@RequiredArgsConstructor
public class AuthController {
private final AuthService authService;
// 회원가입
@PostMapping("/signup")
public ResponseEntity<UserResponseDto> signup(@RequestBody UserRequestDto userRequestDto) {
return ResponseEntity.ok(authService.signup(userRequestDto));
}
// 로그인
@PostMapping("/login")
public ResponseEntity<TokenDto> login(@RequestBody UserRequestDto userRequestDto) {
return ResponseEntity.ok(authService.login(userRequestDto));
}
// 토큰 재발급
@PostMapping("/reissue")
public ResponseEntity<TokenDto> reissue(@RequestBody TokenRequestDto tokenRequestDto) {
return ResponseEntity.ok(authService.reissue(tokenRequestDto));
}
}
2. UserController
-
로그인을 한 상태에서 정보 조회, 정보 수정, 회원탈퇴, 로그아웃을 처리하는 API
-
API 요청이 들어오면 -> 필터에서 AccessToken을 복호화해 유저 정보를 꺼내
SecurityContext에 저장함. -
SecurityContext❓: Authentication 객체가 저장되는 보관소, 필요 시 언제든 이 객체를 꺼내 쓸 수 있도록 제동되는 클래스(TereadLocal에 저장되어 아무데서나 참조 가능), 인증 완료 시 HttpSession에 저장되어 어플리케이션 전반에 걸쳐 전역적 참조 가능 -
userService.getMyInfo(): 내 정보를 가져오기 위해 사용함. -
SecurityUtil 클래스: 유저 정보에서 UserID만 반환하는 메소드가 정의되어 있음.
➡️ 해당 클래스를 커스텀하면 토큰에 닉네임을 넣을 수 있을 것으로 보여, 많이 알아보았으나 CostomUserDetails, CostomUserDetailsSevice조차도 인자값이 정해져 있어 가능할지 모르겠음. -
참고링크
📍Spring Security UserDetails, UserDetailsService 란? - 삽질중인 개발자
📍UserDetails와 UserDetailsService 커스터마이징
📍커스터마이징1 - UserDetailsService, UserDetails
📍Spring Security Custom UserDetailsService 구현하기
📍Spring Security - 인증 절차 인터페이스 구현 (1) UserDetailsService, UserDetails
📍UserDetails에서 User 객체 가져오기
📍[Spring] 스프링 시큐리티 로그인 기능 구현해보기
package me.ver.Authserver7.controller;
import...
@RestController
@RequiredArgsConstructor
@RequestMapping("/api/v1/auth/user")
@PreAuthorize("isAuthenticated()")
public class UserController {
private final UserService userService;
// 정보 조회
@GetMapping("/me")
public ResponseEntity<UserResponseDto> getMyInfo() {
return ResponseEntity.ok(userService.getMyInfo());
}
// 정보 수정
@PutMapping("/update")
public ResponseEntity<UserResponseDto> updateMyInfo(@RequestBody UserUpdateDto dto) {
userService.updateMyInfo(dto);
return ResponseEntity.ok(userService.getMyInfo());
}
// 회원 탈퇴
@DeleteMapping("/me")
public ResponseEntity<String> deleteMember(HttpServletRequest request) {
userService.logout(request);
userService.deleteMember();
return new ResponseEntity<>("회원 탈퇴 성공", HttpStatus.OK);
}
// 로그아웃
@GetMapping("/logout")
public ResponseEntity<String> logout(HttpServletRequest request) {
userService.logout(request);
return new ResponseEntity<>("로그아웃 성공", HttpStatus.OK);
}
}🗂️ domain
1. Authority
@NoArgsConstructor(access = AccessLevel.PROTECTED): 파라미터가 없는 생성자의 생성 어노테이션으로 PROTECTED 사용(외부에서 생성자 생성 막기 위함)@Builder: builder 사용으로 생성자에 엔티티 객체 생성
package me.ver.Authserver7.domain;
import...
@Entity
@Getter
@NoArgsConstructor(access = AccessLevel.PROTECTED)
public class Authority {
@Id
@Column(name = "authority_status")
@Enumerated(EnumType.STRING)
private AuthorityEnum authorityStatus;
public String getAuthorityStatus() {
return this.authorityStatus.toString();
}
@Builder
public Authority(AuthorityEnum authorityStatus) {
this.authorityStatus = authorityStatus;
}
}
2. AuthorityEnum
- 권한 부여를 위해
Enum타입으로 관리
package me.ver.Authserver7.domain;
public enum AuthorityEnum {
ROLE_USER, ROLE_ADMIN
}3. BaseTime
@CreatedDate: 엔티티 생성 시에 그 시각을 자동으로 기입해줌@LastModifiedDate: 엔티티 수정 시에 그 시각을 자동으로 수정해줌
package me.ver.Authserver7.domain;
import...
@Getter
@MappedSuperclass
@EntityListeners(AuditingEntityListener.class)
public abstract class BaseTime {
@CreatedDate
@DateTimeFormat(pattern = "yyyy-MM-dd'T'HH:mm:ss")
private LocalDateTime created_at;
@LastModifiedDate
@DateTimeFormat(pattern = "yyyy-MM-dd'T'HH:mm:ss")
private LocalDateTime modified_at;
}
4. RefreshToken
key: User ID 값이 들어가게 됨value: refresh token String이 들어가게 됨저장은 어디에❓: 일반적으로 Redis를 많이 사용하지만, Redis 사용 경험이 없어 해당 token을 MySQL에 저장 & 로그아웃 기능에 Redis 사용(로그아웃은 RDB의 경우 배치 작업이 필요하나, 구현이 어려울 것으로 판단하여 Redis 사용함)
package me.ver.Authserver7.domain;
import...
@Getter
@NoArgsConstructor(access = AccessLevel.PROTECTED)
@Entity
public class RefreshToken {
@Id
@Column(name = "rt_key")
private String key;
@Column(name = "rt_value")
private String value;
@Builder
public RefreshToken(String key, String value) {
this.key = key;
this.value = value;
}
public RefreshToken updateValue(String token) {
this.value = token;
return this;
}
}5. User
-
회원 정보 :
Id(구분을 위함),email,password,nickname,created_at,modified_at -
@JoinTable: user_authority 테이블을 조인하여 가입한 사용자의 권한 저장 -
수정 가능 정보 :
password,username(실명),nickname
-> username의 경우 수정이 불가능하도록 할 수도 있음.
package me.ver.Authserver7.domain;
import...
@Getter
@NoArgsConstructor(access = AccessLevel.PROTECTED)
@Entity
@EntityListeners(AuditingEntityListener.class)
public class User {
@Id @GeneratedValue
@Column(name = "user_id")
private Long id;
@Column(unique = true)
private String email;
@Column
private String userName;
@Column
private String password;
@Column
private String nickName;
@Column
@CreatedDate
private LocalDateTime createdAt;
@Column
@LastModifiedDate
private LocalDateTime modifiedAt;
@ManyToMany
@Column
@JoinTable(
name = "user_authority",
joinColumns = {@JoinColumn(name="user_id",referencedColumnName = "user_id")},
inverseJoinColumns = {@JoinColumn(name = "authority_status",referencedColumnName = "authority_status")})
private Set<Authority> authorities = new HashSet<>();
@Builder
public User(String email, String userName, String password, String nickName, Set<Authority> authorities, LocalDateTime createdAt, LocalDateTime modifiedAt) {
this.email = email;
this.userName = userName;
this.password = password;
this.nickName = nickName;
this.authorities = authorities;
this.createdAt = createdAt;
this.modifiedAt = modifiedAt;
}
public void updateMember(UserUpdateDto dto, PasswordEncoder passwordEncoder) {
if(dto.getPassword() != null) this.password = passwordEncoder.encode(dto.getPassword());
if(dto.getUserName() != null) this.userName = dto.getUserName();
if(dto.getNickName()!= null) this.nickName = dto.getNickName();
}
}
🗂️ dto
1. TokenDto
로그인,토큰 재발급응답 dto
package me.ver.Authserver7.dto;
import...
@Getter
@NoArgsConstructor
@AllArgsConstructor
@Builder
public class TokenDto {
private String grantType;
private String accessToken;
private String refreshToken;
private Long accessTokenExpiresIn;
}2. TokenRequestDto
토큰 재발급관련 요청 dto
package me.ver.Authserver7.dto;
import lombok.Getter;
import lombok.NoArgsConstructor;
@Getter
@NoArgsConstructor
public class TokenRequestDto {
private String accessToken;
private String refreshToken;
}3. UserResponseDto
회원가입에 대한 응답 dto
package me.ver.Authserver7.dto;
import...
@Getter
@AllArgsConstructor
@NoArgsConstructor
public class UserResponseDto {
private String email;
private String userName;
private String nickName;
private Set<Authority> authorities;
public static UserResponseDto of(User user) {
return new UserResponseDto(
user.getEmail(), user.getUserName(), user.getNickName(), user.getAuthorities());
}
}4. UserRequestDto
회원가입,로그인요청에 사용되는 dto
package me.ver.Authserver7.dto;
import...
@Data
@AllArgsConstructor
@NoArgsConstructor
public class UserRequestDto {
private String email;
private String password;
private String userName;
private String nickName;
private LocalDateTime createdAt;
private LocalDateTime modifiedAt;
private Set<Authority> authorities;
public User toMember(PasswordEncoder passwordEncoder, Set<Authority> authorities) {
return User.builder()
.email(email)
.password(passwordEncoder.encode(password))
.userName(userName)
.nickName(nickName)
.createdAt(createdAt)
.modifiedAt(modifiedAt)
.authorities(authorities)
.build();
}
public UsernamePasswordAuthenticationToken toAuthentication() {
return new UsernamePasswordAuthenticationToken(email, password);
}
}5. UserUpdateDto
- 해당 사용자의
정보 수정요청에 대한 dto
package me.ver.Authserver7.dto;
import...
@Data
@AllArgsConstructor
@NoArgsConstructor
public class UserUpdateDto {
private String userName;
private String password;
private String nickName;
}🗂️ jwt
1. JwtAccessDeniedHandler
- 유저에 대한 정보는 있지만, 자원에 접근할 수 있는 권한이 없는 경우
SC_FORBIDDEN(403)응답
package me.ver.Authserver7.jwt;
import...
@Component
public class JwtAccessDeniedHandler implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest request, HttpServletResponse response, AccessDeniedException accessDeniedException) throws IOException, ServletException {
response.sendError(HttpServletResponse.SC_FORBIDDEN);
}
}2. JwtAuthenticationEntryPoint
- 유저 정보가 없는 상태로 접근하는 경우
SC_UNAUTHORIZED(401)응답
package me.ver.Authserver7.jwt;
import...
@Component
public class JwtAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException authException) throws IOException {
response.sendError(HttpServletResponse.SC_UNAUTHORIZED);
}
}3. JwtFilter
-
OncePerRequestFilter인터페이스 구현 -
doFilterInternal: filtering 로직이 수행됨. -
SecurityContext에 유저 정보 저장(요청이 Controller에 도착 = SecurityContext에 UserId 존재가 보증됨)순서
a.String jwt = resolveToken(request);: request header에서 토큰 꺼내기
b.if (StringUtils.hasText(jwt) && tokenProvider.validateToken(jwt)) {: 토큰 유효성 검사(validateToken)
-> 정상 토큰 O : Authentication 가져와 SecurityContext에 저장
c.if (redisTemplate.opsForValue().get(jwt) != null) {: 로그아웃 체크 -
public String resolveToken(HttpServletRequest request) {: request header에서 토큰 정보 꺼내기
package me.ver.Authserver7.jwt;
import...
@RequiredArgsConstructor
public class JwtFilter extends OncePerRequestFilter {
public static final String AUTHORIZATION_HEADER = "Authorization";
public static final String BEARER_PREFIX = "Bearer ";
private final TokenProvider tokenProvider;
private final StringRedisTemplate redisTemplate;
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws IOException, ServletException {
String jwt = resolveToken(request);
if (StringUtils.hasText(jwt) && tokenProvider.validateToken(jwt)) {
if (redisTemplate.opsForValue().get(jwt) != null) {
throw new RuntimeException("로그아웃 된 사용자 입니다.");
}
Authentication authentication = tokenProvider.getAuthentication(jwt);
SecurityContextHolder.getContext().setAuthentication(authentication);
}
filterChain.doFilter(request, response);
}
public String resolveToken(HttpServletRequest request) {
String bearerToken = request.getHeader(AUTHORIZATION_HEADER);
if (StringUtils.hasText(bearerToken) && bearerToken.startsWith(BEARER_PREFIX)) {
return bearerToken.substring(7);
}
return null;
}
}4. TokenProvider
- 토큰 관련 로직이 이곳을 기준으로 이루어짐.
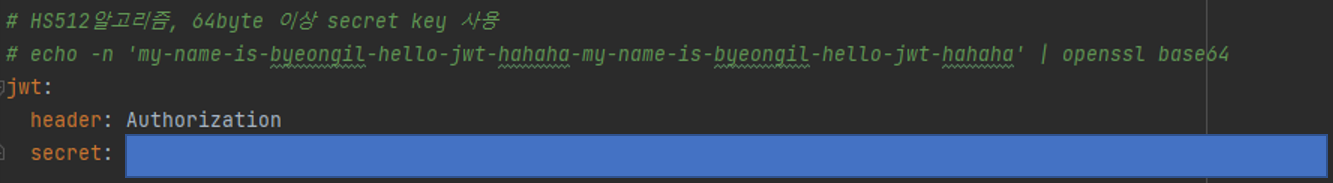
jwt.secret: application.yml에 정의되어 있음.generateTokenDto: 넘겨받은 유저 정보로 accessToken & refreshToken 생성uthentication.getName():id값을 가져옴.- 유저 & 권한 정보 : accessToken에만 넣는 것으로 구성함.
- refreshToken에는 만료날짜만 넣음.
getAuthentication: 토큰을 복호화해 accessToken에 있는 정보 꺼냄.validateToken: 토큰 정보 검증parseClaims: 토큰이 만료되었더라도, 정보를 꺼낼 수 있도록 함.
package me.ver.Authserver7.jwt;
import io.jsonwebtoken.*;
import io.jsonwebtoken.io.Decoders;
import io.jsonwebtoken.security.Keys;
import lombok.extern.slf4j.Slf4j;
import me.ver.Authserver7.dto.TokenDto;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.stereotype.Component;
import java.security.Key;
import java.util.*;
import java.util.stream.Collectors;
@Slf4j
@Component
public class TokenProvider {
private static final String AUTHORITIES_KEY = "auth";
private static final String BEARER_TYPE = "bearer";
private static final long ACCESS_TOKEN_EXPIRE_TIME = 1000 * 60 * 30; // 30분
private static final long REFRESH_TOKEN_EXPIRE_TIME = 1000 * 60 * 60 * 24 * 7; // 7일
private final Key key;
//private static final String NICKNAME = "nickName";
//private String nickName;
public TokenProvider(@Value("${jwt.secret}") String secretKey) {
byte[] keyBytes = Decoders.BASE64.decode(secretKey);
this.key = Keys.hmacShaKeyFor(keyBytes);
}
public TokenDto generateTokenDto(Authentication authentication) {
// 권한들 가져오기
String authorities = authentication.getAuthorities().stream()
.map(GrantedAuthority::getAuthority)
.collect(Collectors.joining(","));
//payload 부분 설정
//Map<String, Object> payloads = new HashMap<>();
//payloads.put("nickname", nickName);
long now = (new Date()).getTime();
Date accessTokenExpiresIn = new Date(now + ACCESS_TOKEN_EXPIRE_TIME);
String accessToken = Jwts.builder()
.setSubject(authentication.getName()) // payload "sub": "name"
//.claim(NICKNAME, User.getNickname())
//.setClaims(payloads)
.claim(AUTHORITIES_KEY, authorities) // payload "auth": "ROLE_USER"
.setExpiration(accessTokenExpiresIn) // payload "exp": 1516239022 (예시)
.signWith(key, SignatureAlgorithm.HS512) // header "alg": "HS512"
.compact();
String refreshToken = Jwts.builder()
.setExpiration(new Date(now + REFRESH_TOKEN_EXPIRE_TIME))
.signWith(key, SignatureAlgorithm.HS512)
.compact();
return TokenDto.builder()
.grantType(BEARER_TYPE)
.accessToken(accessToken)
.accessTokenExpiresIn(accessTokenExpiresIn.getTime())
.refreshToken(refreshToken)
.build();
}
public Authentication getAuthentication(String accessToken) {
Claims claims = parseClaims(accessToken);
if (claims.get(AUTHORITIES_KEY) == null) {
throw new RuntimeException("권한 정보가 없는 토큰입니다.");
}
Collection<? extends GrantedAuthority> authorities =
Arrays.stream(claims.get(AUTHORITIES_KEY).toString().split(","))
.map(SimpleGrantedAuthority::new)
.collect(Collectors.toList());
UserDetails principal = new User(claims.getSubject(), "", authorities);
return new UsernamePasswordAuthenticationToken(principal, "", authorities);
}
public boolean validateToken(String token) {
try {
Jwts.parserBuilder().setSigningKey(key).build().parseClaimsJws(token);
return true;
} catch (io.jsonwebtoken.security.SecurityException | MalformedJwtException e) {
log.info("잘못된 JWT 서명입니다.");
} catch (ExpiredJwtException e) {
log.info("만료된 JWT 토큰입니다.");
} catch (UnsupportedJwtException e) {
log.info("지원되지 않는 JWT 토큰입니다.");
} catch (IllegalArgumentException e) {
log.info("JWT 토큰이 잘못되었습니다.");
}
return false;
}
private Claims parseClaims(String accessToken) {
try {
return Jwts.parserBuilder().setSigningKey(key).build().parseClaimsJws(accessToken)
.getBody();
} catch (ExpiredJwtException e) {
return e.getClaims();
}
}
}🗂️ repository
1. AuthorityRepository
package me.ver.Authserver7.repository;
import...
import java.util.Optional;
public interface AuthorityRepository extends JpaRepository<Authority, AuthorityEnum> {
Optional<Authority> findByAuthorityStatus(AuthorityEnum authorityStatus);
}2. RefreshTokenRepository
package me.ver.Authserver7.repository;
import...
import java.util.Optional;
public interface RefreshTokenRepository extends JpaRepository<RefreshToken, String> {
Optional<RefreshToken> findByKey(String key);
Optional<RefreshToken> deleteByKey(String key);
}3. UserRepository
package me.ver.Authserver7.repository;
import...
import java.util.Optional;
public interface UserRepository extends JpaRepository<User, Long> {
Optional<User> findByEmail(String email);
boolean existsByEmail(String email);
}
🗂️ service
1. AuthService
회원가입 : 이메일 중복 여부 검증 -> authorityRepository에서 User 권한 찾아 User 객체 파라미터로 넘긴 후에 저장
로그인
- dto의 email, password를 받아
UsernamePasswordAuthenticationToken객체 생성 - authenticationManagerBuilder.getObject().authenticate 메서드가 실행될 때 CustomUserDetailsService 에서 만들었던 loadUserByUsername 메서드가 실행되고, Authentication 객체 생성
- tokenProvider.generateTokenDto()로 토큰 생성 -> TokenDto
key: authentication.getName(),value: tokenDto.getRefreshToken() -> refreshTokent 객체 생성 ->RefreshTokenRepository에 저장
토큰 재발급
- dto에서 accessToken & refreshToken 받음.
- refreshToken 검증
- accessToken 복호화 -> Authentication 객체 가져옴.
RefreshTokenRepository: Authentication객체를 통해 가져온 value와 dto의 refresh Token이 똑같은지 검사- ⭕ -> 새로운 토큰 생성해 RefreshTokenRepository에서 수정해줌.
package me.ver.Authserver7.service;
import...
@Service
@RequiredArgsConstructor
public class AuthService {
private final AuthenticationManagerBuilder authenticationManagerBuilder;
private final AuthorityRepository authorityRepository;
private final UserRepository userRepository;
private final PasswordEncoder passwordEncoder;
private final TokenProvider tokenProvider;
private final RefreshTokenRepository refreshTokenRepository;
/**
* 회원가입
*/
@Transactional
public UserResponseDto signup(UserRequestDto userRequestDto) {
if (userRepository.existsByEmail(userRequestDto.getEmail())) {
throw new RuntimeException("이미 가입되어 있는 이메일입니다.");
}
Authority authority = authorityRepository
.findByAuthorityStatus(AuthorityEnum.ROLE_USER).orElseThrow(()->new RuntimeException("권한 정보가 없습니다."));
Set<Authority> set = new HashSet<>();
set.add(authority);
User user = userRequestDto.toMember(passwordEncoder, set);
return UserResponseDto.of(userRepository.save(user));
}
/**
* 로그인
*/
@Transactional
public TokenDto login(UserRequestDto userRequestDto) {
UsernamePasswordAuthenticationToken authenticationToken = userRequestDto.toAuthentication();
Authentication authentication = authenticationManagerBuilder.getObject().authenticate(authenticationToken);
TokenDto tokenDto = tokenProvider.generateTokenDto(authentication);
RefreshToken refreshToken = RefreshToken.builder()
.key(authentication.getName())
.value(tokenDto.getRefreshToken())
.build();
refreshTokenRepository.save(refreshToken);
return tokenDto;
}
/**
* 재발급
*/
@Transactional
public TokenDto reissue(TokenRequestDto tokenRequestDto) {
if (!tokenProvider.validateToken(tokenRequestDto.getRefreshToken())) {
throw new RuntimeException("Refresh Token 이 유효하지 않습니다.");
}
Authentication authentication = tokenProvider.getAuthentication(tokenRequestDto.getAccessToken());
RefreshToken refreshToken = refreshTokenRepository.findByKey(authentication.getName())
.orElseThrow(() -> new RuntimeException("로그아웃 된 사용자입니다."));
if (!refreshToken.getValue().equals(tokenRequestDto.getRefreshToken())) {
throw new RuntimeException("토큰의 유저 정보가 일치하지 않습니다.");
}
TokenDto tokenDto = tokenProvider.generateTokenDto(authentication);
RefreshToken newRefreshToken = refreshToken.updateValue(tokenDto.getRefreshToken());
refreshTokenRepository.save(newRefreshToken);
return tokenDto;
}
}2. CustomUserDetailsService
- SpringSecurity의
UserDetailsService구현 클래스 - 로그인 시 DB에서 유저 정보 가져옴(UserReprsitory에서)
- 가져온 유저 정보를 기반으로
userdetails객체로 만들어 리턴
package me.ver.Authserver7.service;
import...
public class CustomUserDetails implements UserDetails {
private String email;
private String password;
private String AUTHORITY;
private boolean ENABLED;
private String nickName;
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
ArrayList<GrantedAuthority> auth = new ArrayList<GrantedAuthority>();
auth.add(new SimpleGrantedAuthority(AUTHORITY));
return auth;
}
@Override
public String getPassword() {
return password;
}
@Override
public String getUsername() {
return email;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return ENABLED;
}
public String getNickname() {
return nickName;
}
public void setNickname(String nickName) {
this.nickName = nickName;
}
}
- UserService
코드를 입력하세요🗂️ service > exception(수정 필요)
- (종준님 코드 사용 및 수정)
a. AuthServiceException
package me.ver.Authserver7.service.exception;
public enum AuthServiceException {
EXIST_AUTH("1101", "exist AUTH"),
NO_SUCH_AUTH("1102", "no such AUTH"),
ALREADY_GENERATE_PASSWORD("1103", "already generate password"),
NO_PASSWORD("1104", "no generated password"),
NO_MATCH_PASSWORD("1105", "no match password"),
;
private String message;
private String code;
AuthServiceException(String code, String message) {
this.code = code;
this.message = message;
}
public String getMessage() {
return message;
}
public String getCode() {
return code;
}
}
b. AuthServiceValidateException
package me.ver.Authserver7.service.exception;
import...
@Getter
public class AuthServiceValidateException extends RuntimeException {
private final String code;
public AuthServiceValidateException(UserServiceException publisherServiceException) {
super(publisherServiceException.getMessage());
this.code = publisherServiceException.getCode();
}
}
c. UserServiceException
package me.ver.Authserver7.service.exception;
public enum UserServiceException {
EXIST_USER("1101", "exist user"),
NO_SUCH_USER("1102", "no such user"),
ALREADY_GENERATE_PASSWORD("1103", "already generate password"),
NO_PASSWORD("1104", "no generated password"),
NO_MATCH_PASSWORD("1105", "no match password"),
;
private String message;
private String code;
UserServiceException(String code, String message) {
this.code = code;
this.message = message;
}
public String getMessage() {
return message;
}
public String getCode() {
return code;
}
}
d. UserServiceValidateException
package me.ver.Authserver7.service.exception;
import...
@Getter
public class UserServiceValidateException extends RuntimeException {
private final String code;
public UserServiceValidateException(UserServiceException publisherServiceException) {
super(publisherServiceException.getMessage());
this.code = publisherServiceException.getCode();
}
}
🗂️ util
- SecurityUtil
JwtFilter에서SecurityContext에 세팅한 유저 정보 꺼냄id를 저장 -> Long 타입으로 파싱SecurityContext: ThreadLocal에 사용자 정보 저장
package me.ver.Authserver7.util;
import...
public class SecurityUtil {
private SecurityUtil() { }
public static Long getLoginMemberId() {
final Authentication authentication = SecurityContextHolder.getContext().getAuthentication();
if (authentication == null || authentication.getName() == null) {
throw new RuntimeException("로그인 유저 정보가 없습니다.");
}
Long LoginId = Long.parseLong(authentication.getName());
return LoginId;
}
}🗂️ web(수정 전 ver)
- 성공 코드와 실패 코드를 커스텀하는 것이 아직은 미숙해서 많이 알아보았으나 적용에 대한 고민이 깊어져 우선, 종준님의 web 부분을 가져와 내 부분에 맞게 살짝만 바꿔둔 상태.
1. web > exception
a. ExcontrollerAdvice
package me.ver.Authserver7.web.exception;
import...
@Slf4j
@RestControllerAdvice
public class ExControllerAdvice {
private static void logger(Exception exception) {
log.error(exception.getClass()
.getSimpleName() + " = [{}][{}]",
exception.getClass(), exception.getMessage());
}
@ResponseStatus(HttpStatus.BAD_REQUEST)
@ExceptionHandler({UserServiceValidateException.class})
public ApiResponse<ApiResponse.FailureBody> PublisherExHandler(UserServiceValidateException exception) {
logger(exception);
return ApiResponseGenerator.fail(HttpStatus.BAD_REQUEST, HttpStatus.BAD_REQUEST.value() + exception.getCode(),
exception.getClass()
.getSimpleName(), exception.getMessage());
}
@ResponseStatus(HttpStatus.BAD_REQUEST)
@ExceptionHandler({AuthServiceValidateException.class})
public ApiResponse<ApiResponse.FailureBody> RoomExHandler(AuthServiceValidateException exception) {
logger(exception);
return ApiResponseGenerator.fail(HttpStatus.BAD_REQUEST, HttpStatus.BAD_REQUEST.value() + exception.getCode(),
exception.getClass()
.getSimpleName(), exception.getMessage());
}
@ResponseStatus(HttpStatus.BAD_REQUEST)
@ExceptionHandler({IllegalStateException.class})
public ApiResponse<ApiResponse.FailureBody> illegalStateExHandler(IllegalStateException exception) {
logger(exception);
String defaultMessage = exception.getMessage();
return ApiResponseGenerator.fail(HttpStatus.BAD_REQUEST, HttpStatus.BAD_REQUEST.value() + "001",
exception.getClass()
.getSimpleName(), defaultMessage);
}
@ResponseStatus(HttpStatus.BAD_REQUEST)
@ExceptionHandler(BindException.class)
public List<ApiResponse<ApiResponse.FailureBody>> bindingExHandler(BindException exception) {
logger(exception);
List<ApiResponse<ApiResponse.FailureBody>> errorResults = new ArrayList<>();
exception.getAllErrors()
.forEach(error -> {
FieldError fieldError = (FieldError) error;
String field = fieldError.getField();
String defaultMessage = fieldError.getDefaultMessage();
ApiResponse<ApiResponse.FailureBody> bindingException = ApiResponseGenerator.fail(HttpStatus.BAD_REQUEST, HttpStatus.BAD_REQUEST.value() + "1001", exception.getClass()
.getSimpleName(), field + " 필드 입력이 필요합니다. " + defaultMessage);
errorResults.add(bindingException);
});
return errorResults;
}
@ResponseStatus(HttpStatus.BAD_REQUEST)
@ExceptionHandler
public ApiResponse<ApiResponse.FailureBody> exHandler(Exception exception) {
logger(exception);
String defaultMessage = exception.getMessage();
return ApiResponseGenerator.fail(HttpStatus.BAD_REQUEST, HttpStatus.BAD_REQUEST.value() + "1000",
exception.getClass()
.getSimpleName(), defaultMessage);
}
}
2. response
a. ApiResponse
package me.ver.Authserver7.web.response;
import...
@Getter
public class ApiResponse<T> extends ResponseEntity<T> {
public ApiResponse(T body, HttpStatus status) {
super(body, status);
}
@Getter
public static class FailureBody implements Serializable {
private Timestamp timestamp;
private String code;
private String error;
private String message;
public FailureBody(final String code, final String error, final String message) {
this.timestamp = new Timestamp(System.currentTimeMillis());
this.code = code;
this.error = error;
this.message = message;
}
}
@Getter
public static class withData<T> implements Serializable {
private Timestamp timestamp;
private String code;
private String message;
private T data;
public withData(T data, String code, String message) {
this.timestamp = new Timestamp(System.currentTimeMillis());
this.code = code;
this.message = message;
this.data = data;
}
}
@Getter
public static class withCodeAndMessage implements Serializable {
private Timestamp timestamp;
private String code;
private String message;
public withCodeAndMessage(String code, String message) {
this.timestamp = new Timestamp(System.currentTimeMillis());
this.code = code;
this.message = message;
}
}
}
b. ApiResponseGenerator
package me.ver.Authserver7.web.response;
import...
@UtilityClass
public class ApiResponseGenerator {
public static <D> ApiResponse<ApiResponse.withData> success(final D data,
final HttpStatus status,
final String code, final String message) {
return new ApiResponse<>(new ApiResponse.withData<>(data, code, message), status);
}
public static ApiResponse<ApiResponse.withCodeAndMessage> success(
final HttpStatus status,
final String code, final String message) {
return new ApiResponse<>(new ApiResponse.withCodeAndMessage(code, message), status);
}
public static ApiResponse<ApiResponse.FailureBody> fail(
final HttpStatus status,
final String code, final String error, final String message) {
return new ApiResponse<>(new ApiResponse.FailureBody(code, error, message), status);
}
}
🧸 현재까지의 결과
0. 프로젝트 실행
-
DB
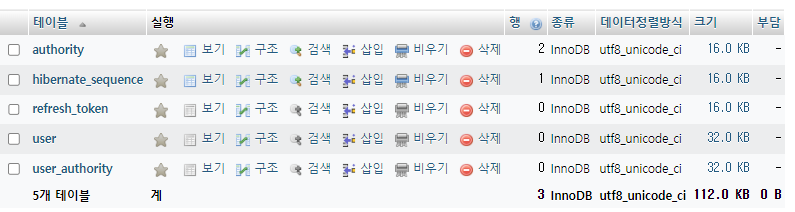
-
여러 처리 후
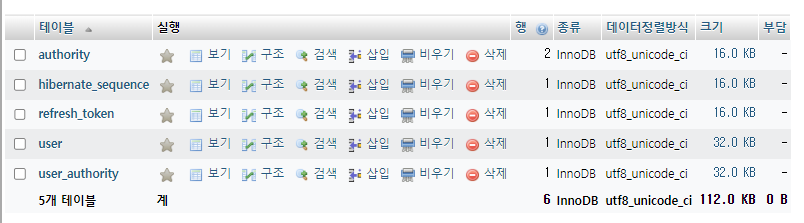
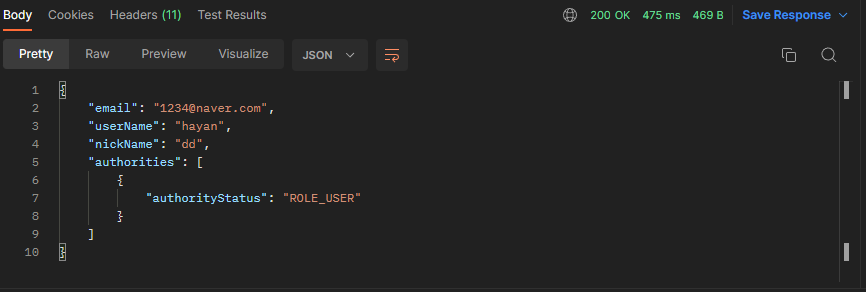
1. 회원가입
-
성공
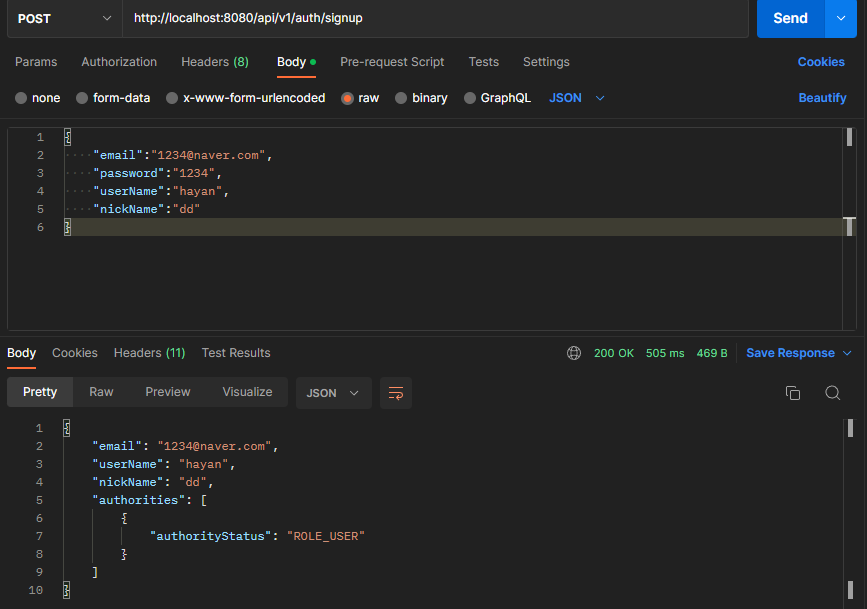
-
실패
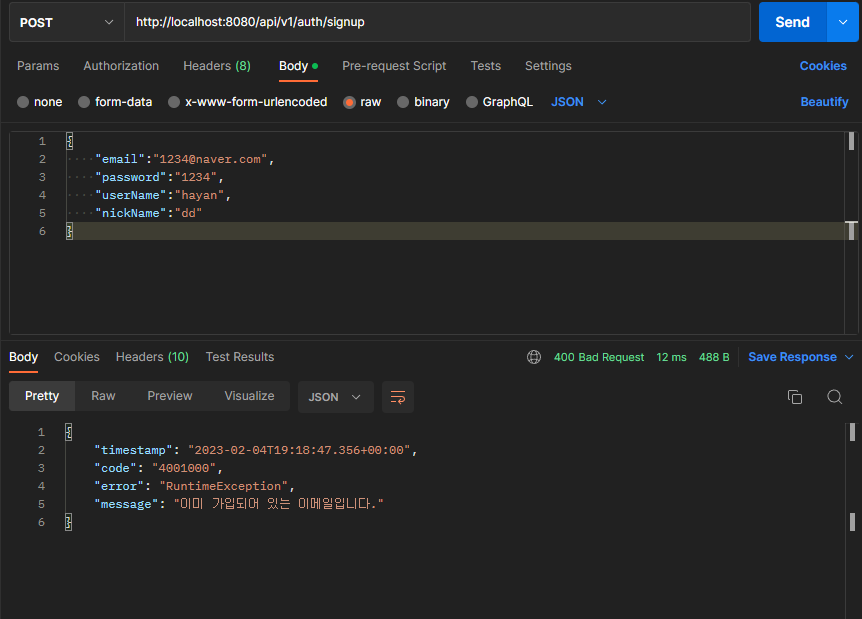
2. 로그인
-
성공
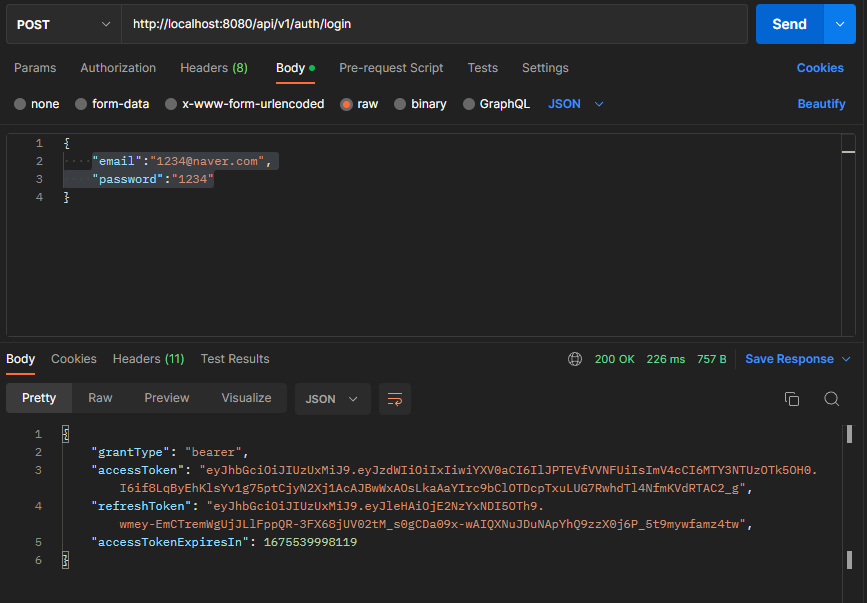
-
실패
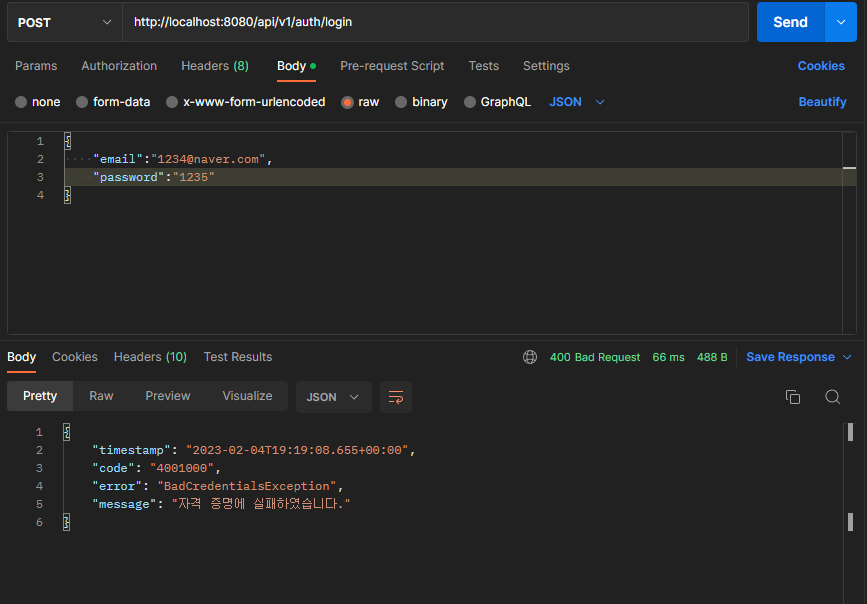
3. 로그아웃
-
성공
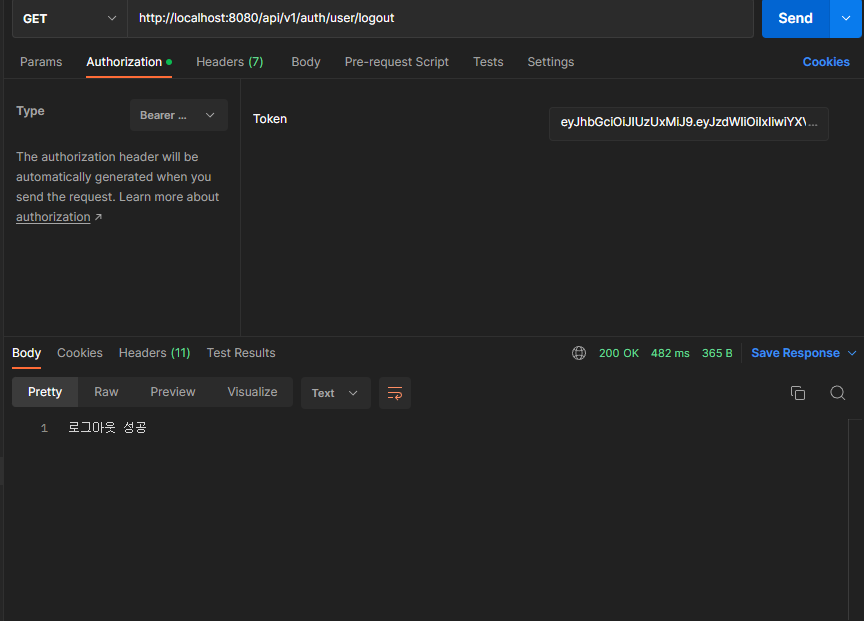
-
실패
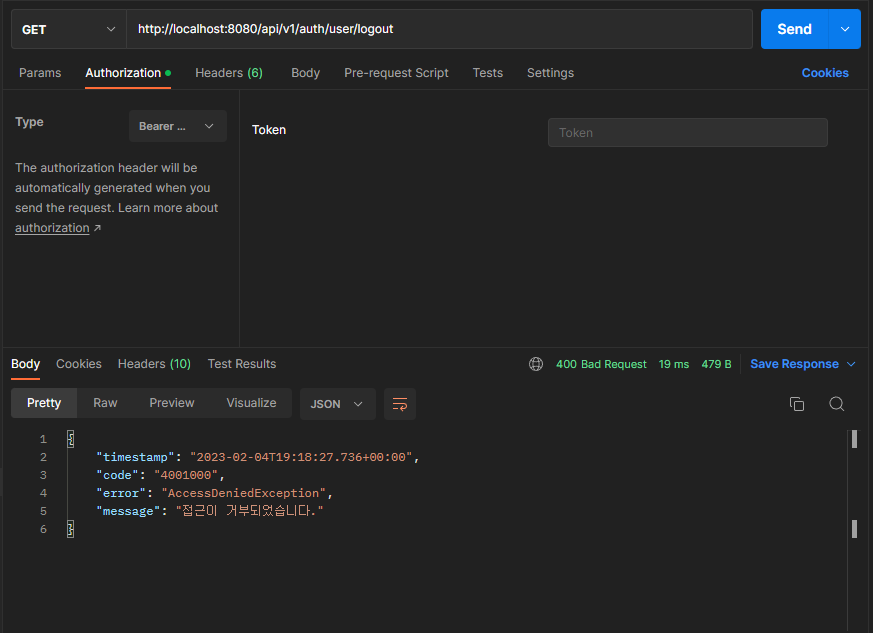
4. 정보 조회
-
성공
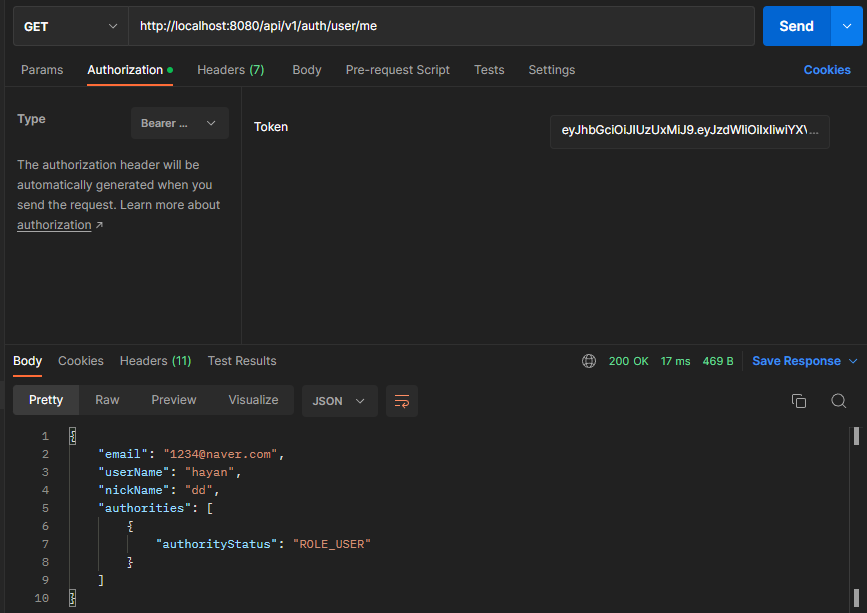
-
실패
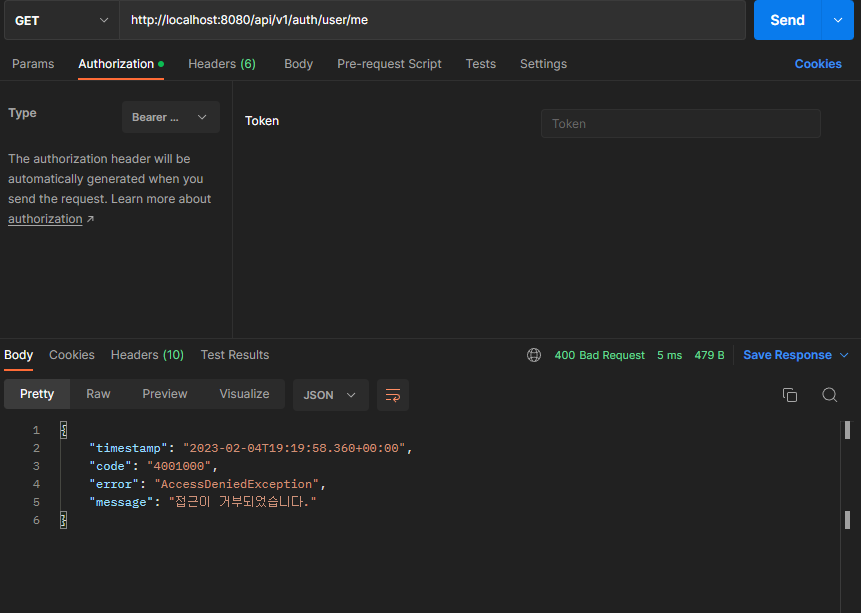
5. 정보 수정
-
성공

-
실패
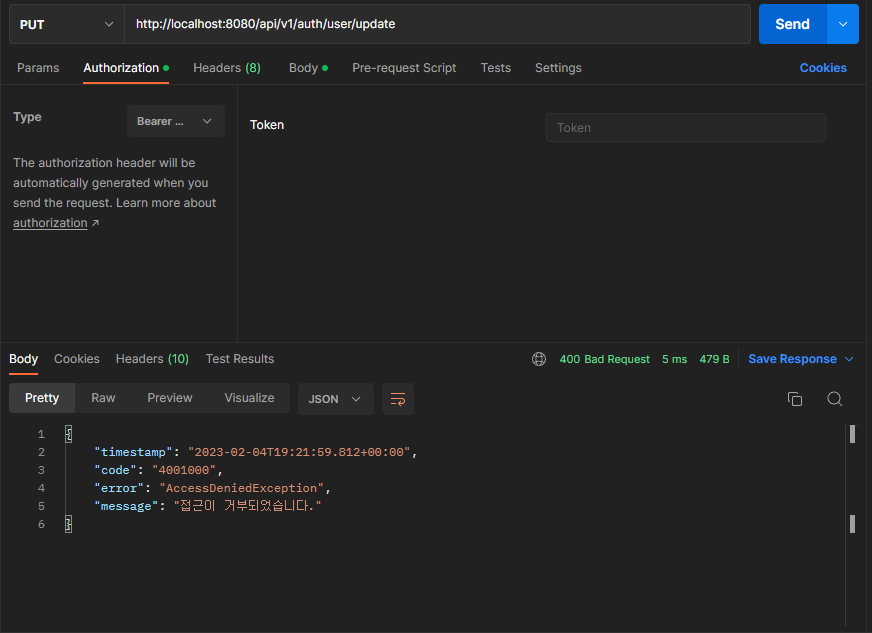
6. 회원 탈퇴
-
성공
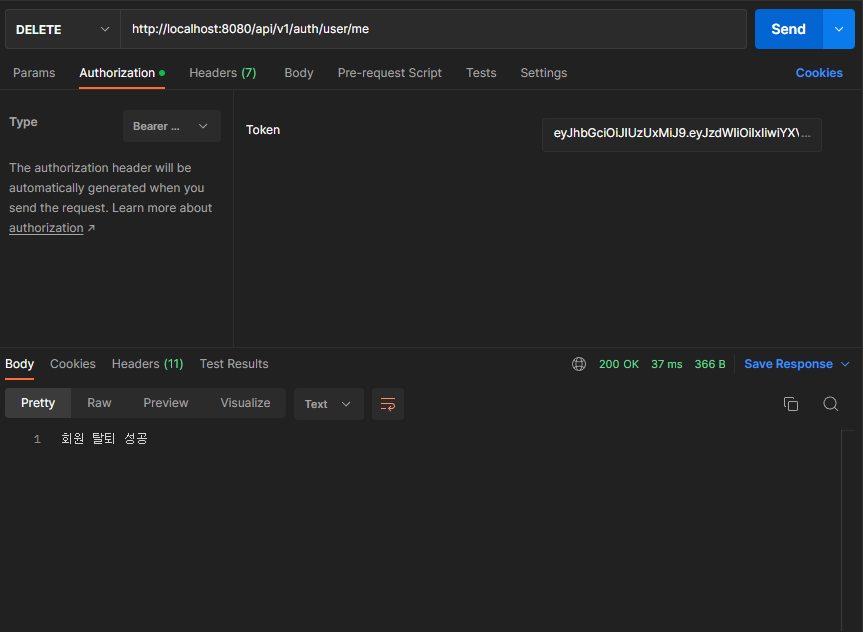
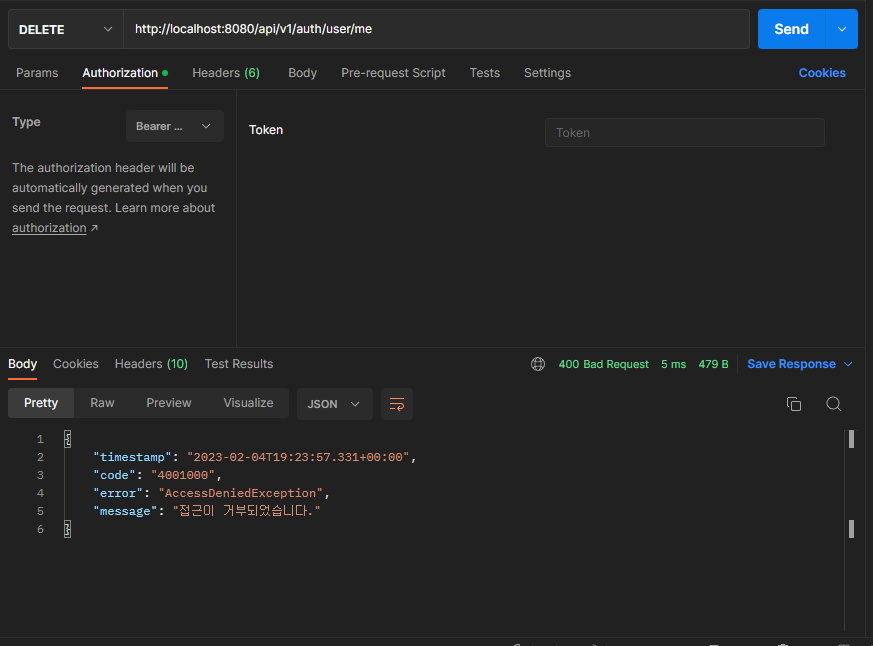
-
실패
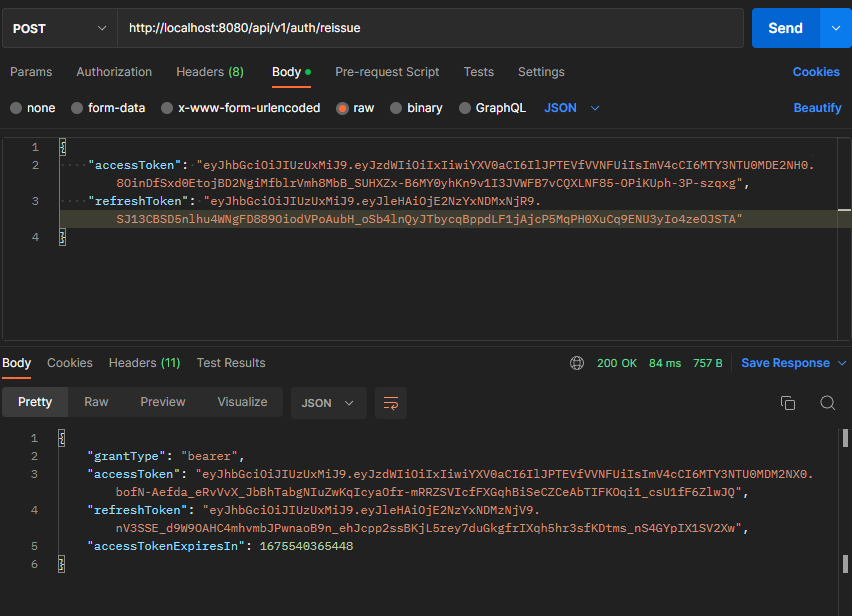
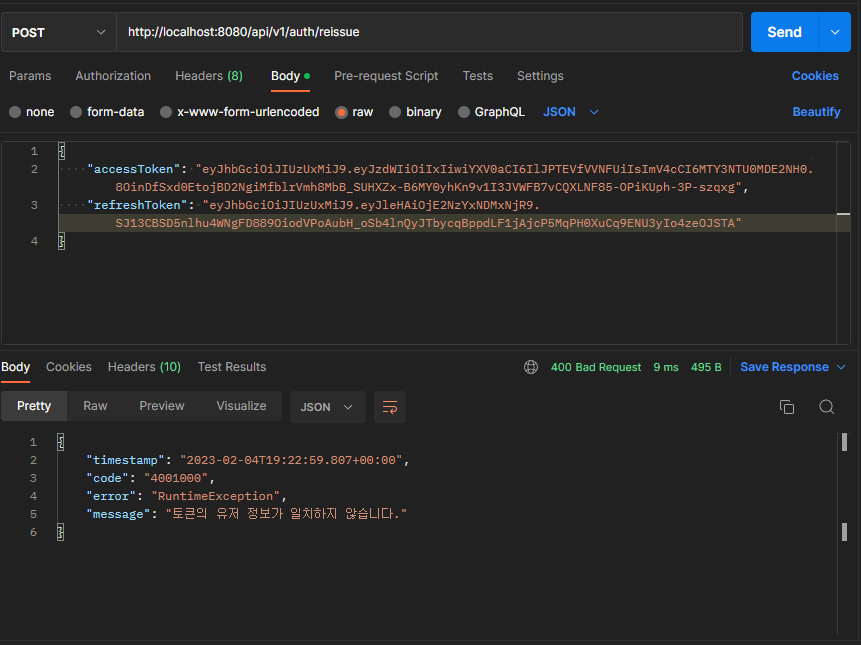
7. 토큰 재발급
-
성공
-
실패
🧸 해결이 어려운 것들
- 토큰에 닉네임 값을 추가하는 것 (payload 안)
- 현재까지 참고 링크
📍Spring boot jwt token 사용하기
📍[프로젝트 2]Jwt Token에 담길 사용자 정보에 대한 결정과 표준에 대한 이해
📍JWT(Json Web Token) 알아가기
📍[JWT/JSON Web Token] 로그인 / 인증에서 Token 사용하기
📍#2.3 비공개 (private) 클레임
📍spring boot REST API Web 프로젝트 (10) - Jwt AccessToken + RefreshToken으로 보안성과 사용자 편의성 고도화하기
📍🌱 Spring Security - 토큰방식 인증 (JWT)
- 실패 응답은 정해둔 규칙에 맞게 출력이 되는데, 성공 응답이 원하는대로 출력이 안되는 상태
- 바람직한 성공 응답
{
"result": "success"
"data": null // 보내줄 데이터가 없다면 null로 보내는 것.
}{
"result": "success"
"data" {
...
}
}