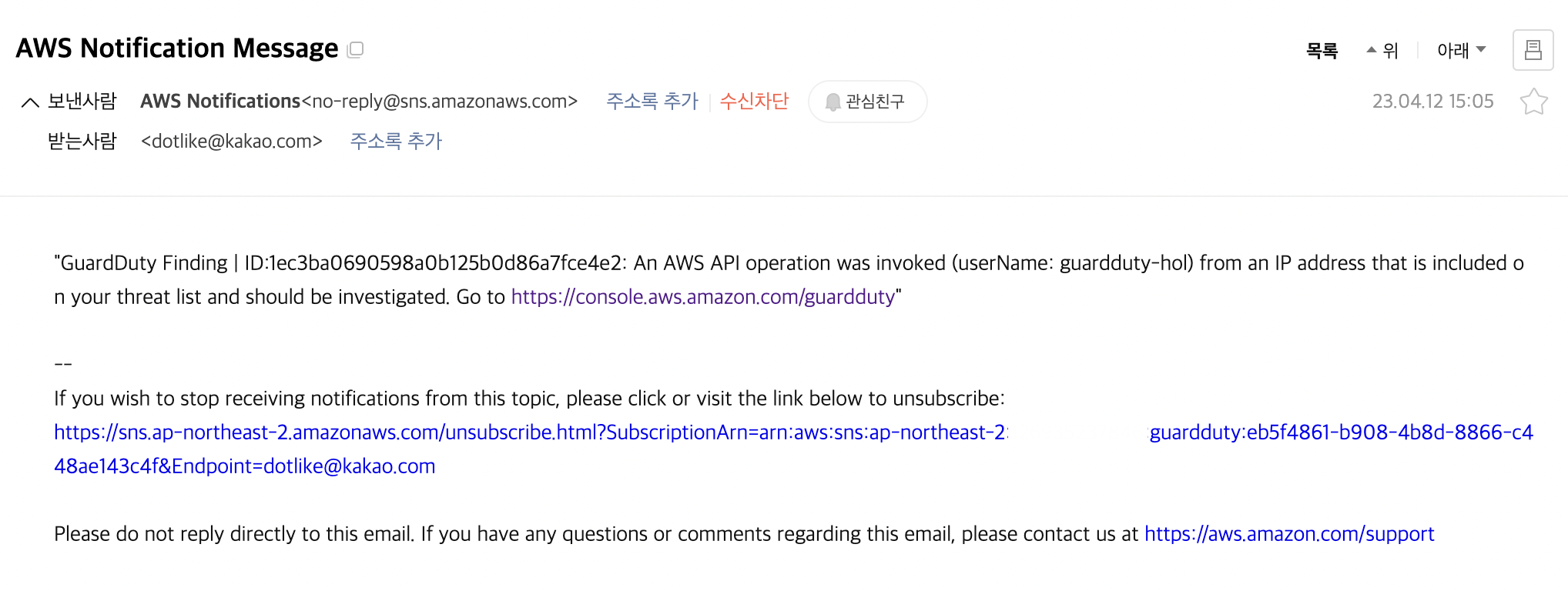
실습 구성도
- 알람을 위한 구독, 주제 설정
- 리소스들의 권한과 자격증명 탈취상황을 알아보기 위한 iam 생성
- 특정한 위협을 발생시키기 위해 ec2, eip를 guardduty에 등록
- eventbridge, lambda를 이용하여 특정 위협이 발생했을때 자동으로 격리 할수있도록 구성
Guardduty
- 활성화 한 이후 샘플결과 작성 누르면 결과 확인 가능
- 인스턴스 생성하지 않고 테스트해볼수있다.
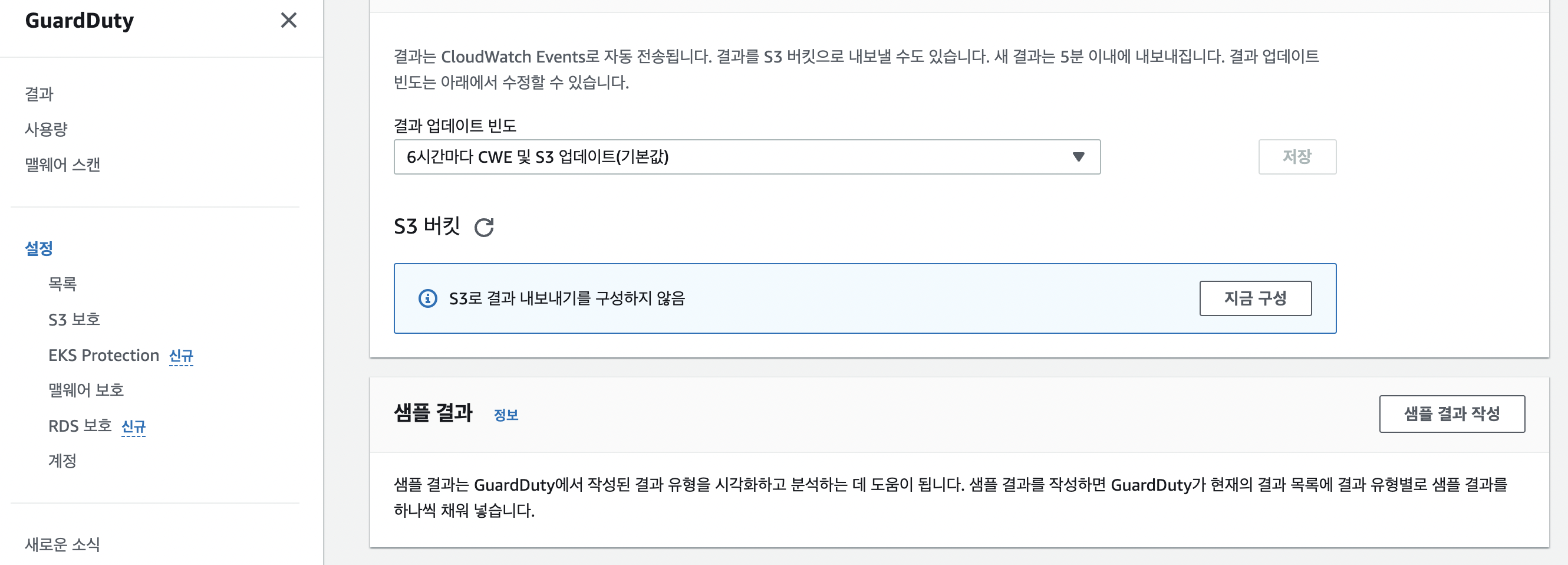
- 샘플결과
- 여러 취약점에 대해 중요도와 리소스 정보가 세분화 되어있음을 확인.
SNS
- 기본 세팅 값으로 생성
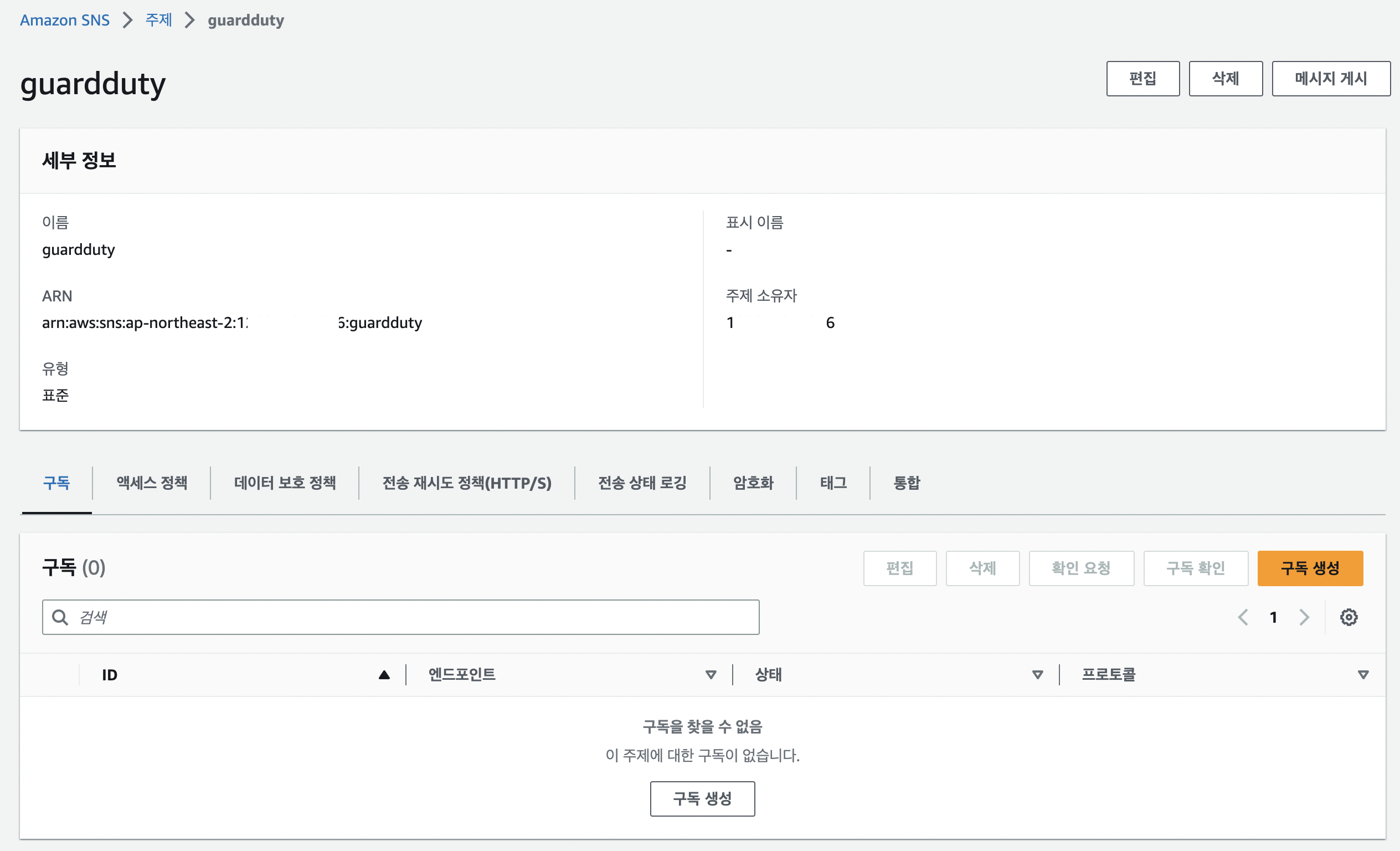
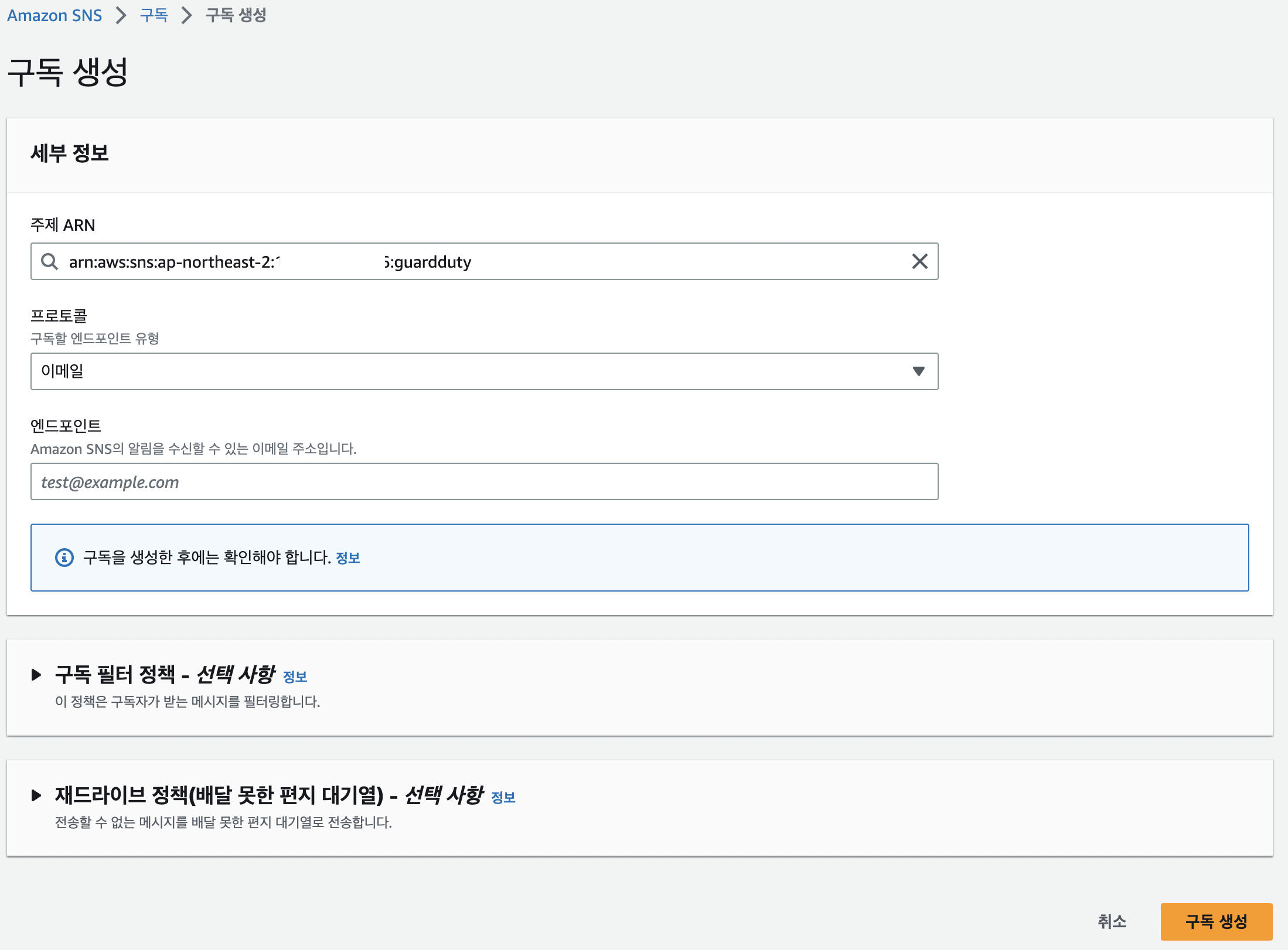
구독
- 앞서 만든 주제 arn 선택
- 프로토콜은 이메일 실제로 알람 받을 이메일 주소 입력
- 생성 이후 입력한 메일에서 “구독 확인” 눌러야함.
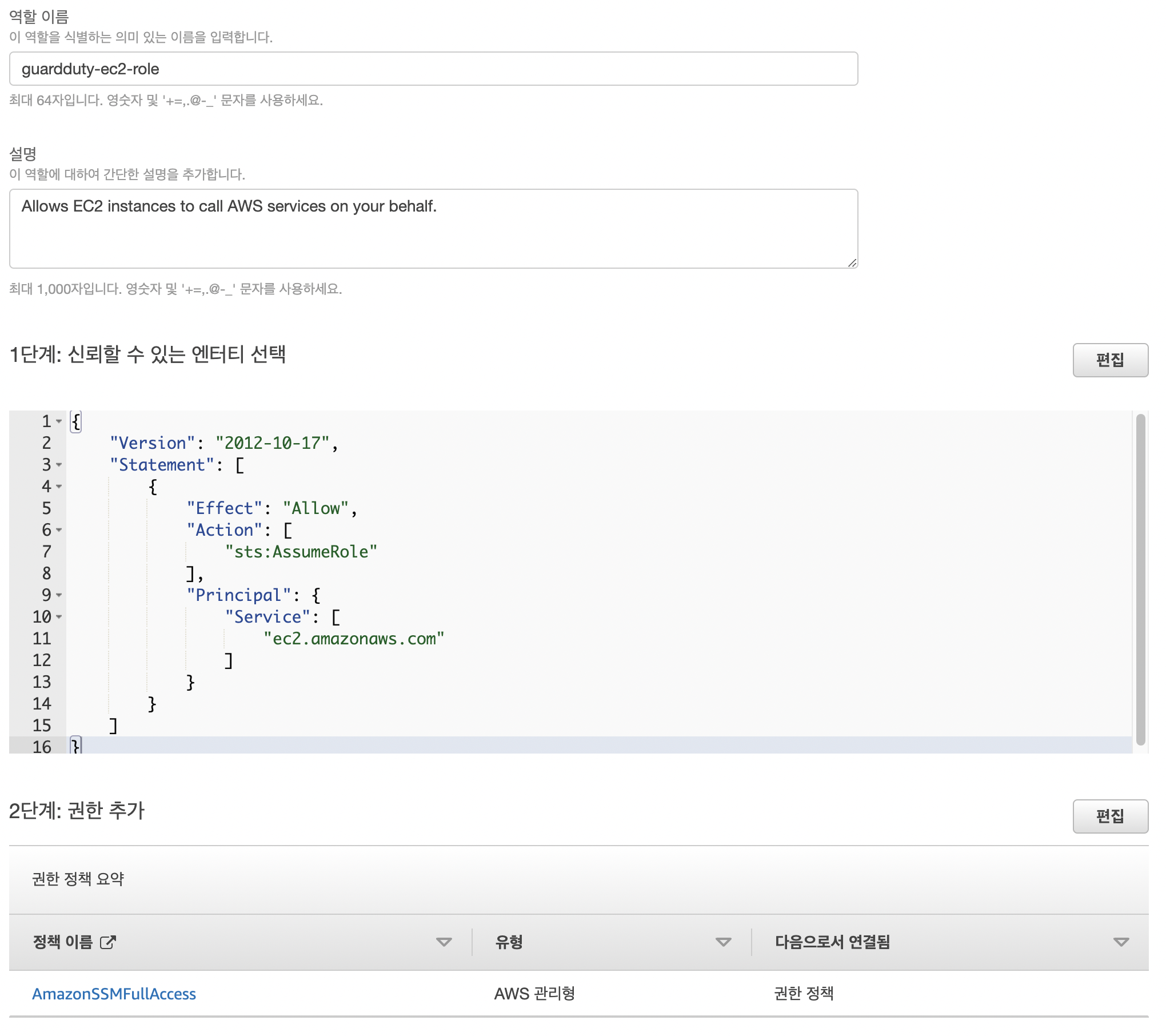
IAM
- 역할 생성
- ec2 > ssm full access로
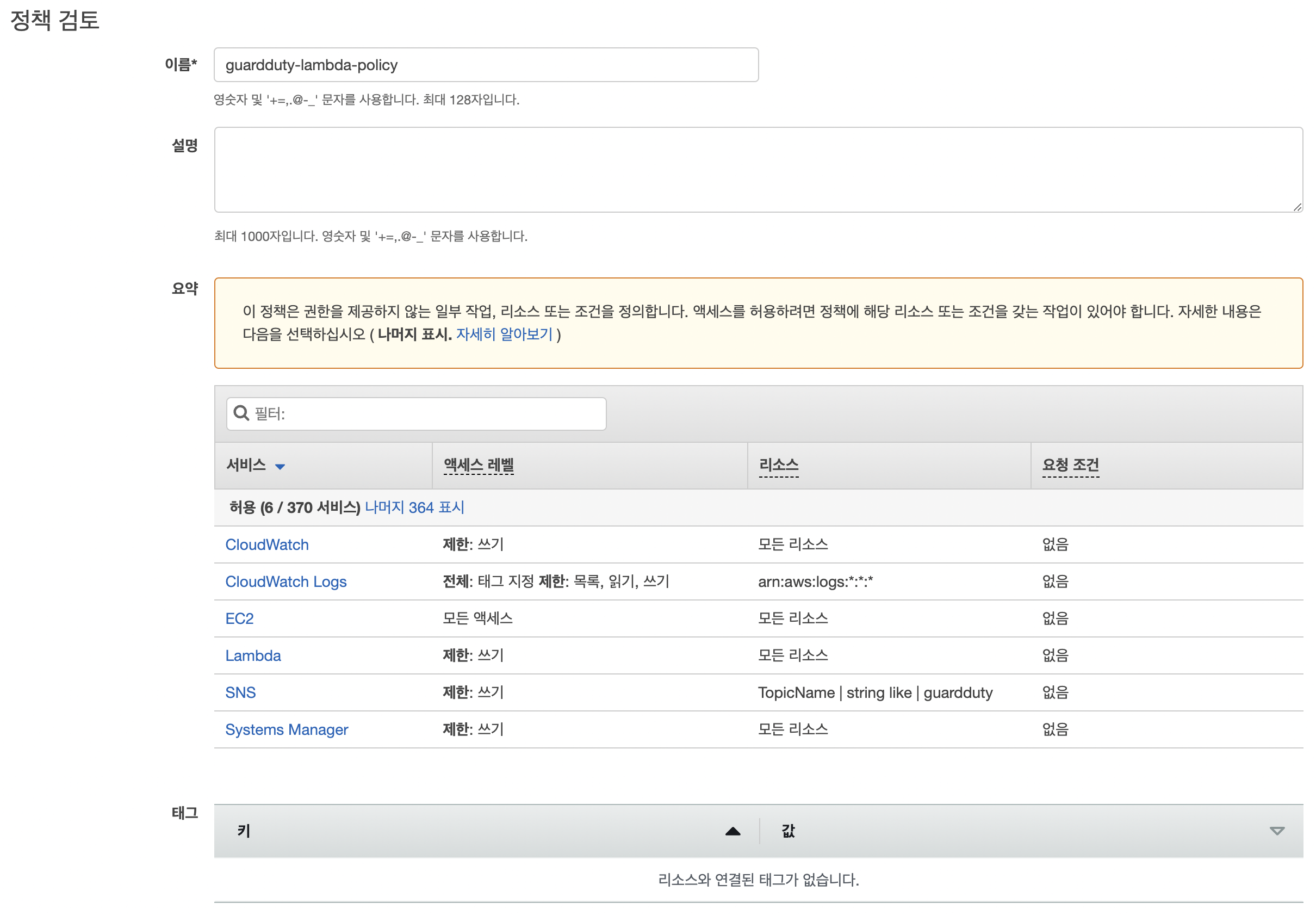
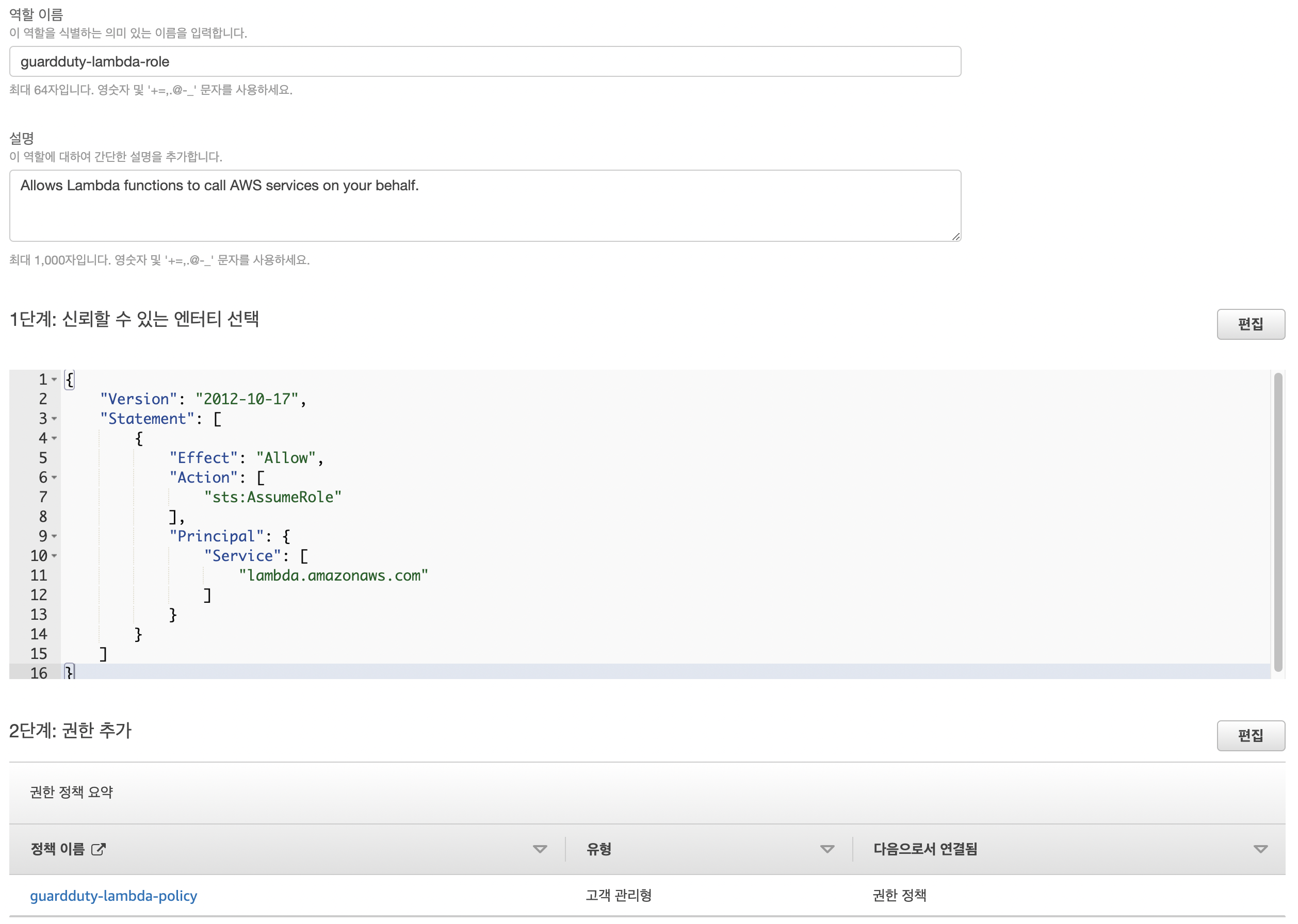
Lambda 역할
- 정책 신규 생성
- 정책
{ "Version": "2012-10-17", "Statement": [ { "Action":[ "ssm:PutParameter", "ec2:*", "lambda:InvokeFunction", "cloudwatch:PutMetricData" ], "Resource": "*", "Effect":"Allow" }, { "Action":[ "logs:*" ], "Resource": "arn:aws:logs:*:*:*", "Effect":"Allow" }, { "Action":[ "sns:Publish" ], "Resource": "arn:aws:sns:*:*:guardduty", "Effect":"Allow" } ] }
role
사용자 생성
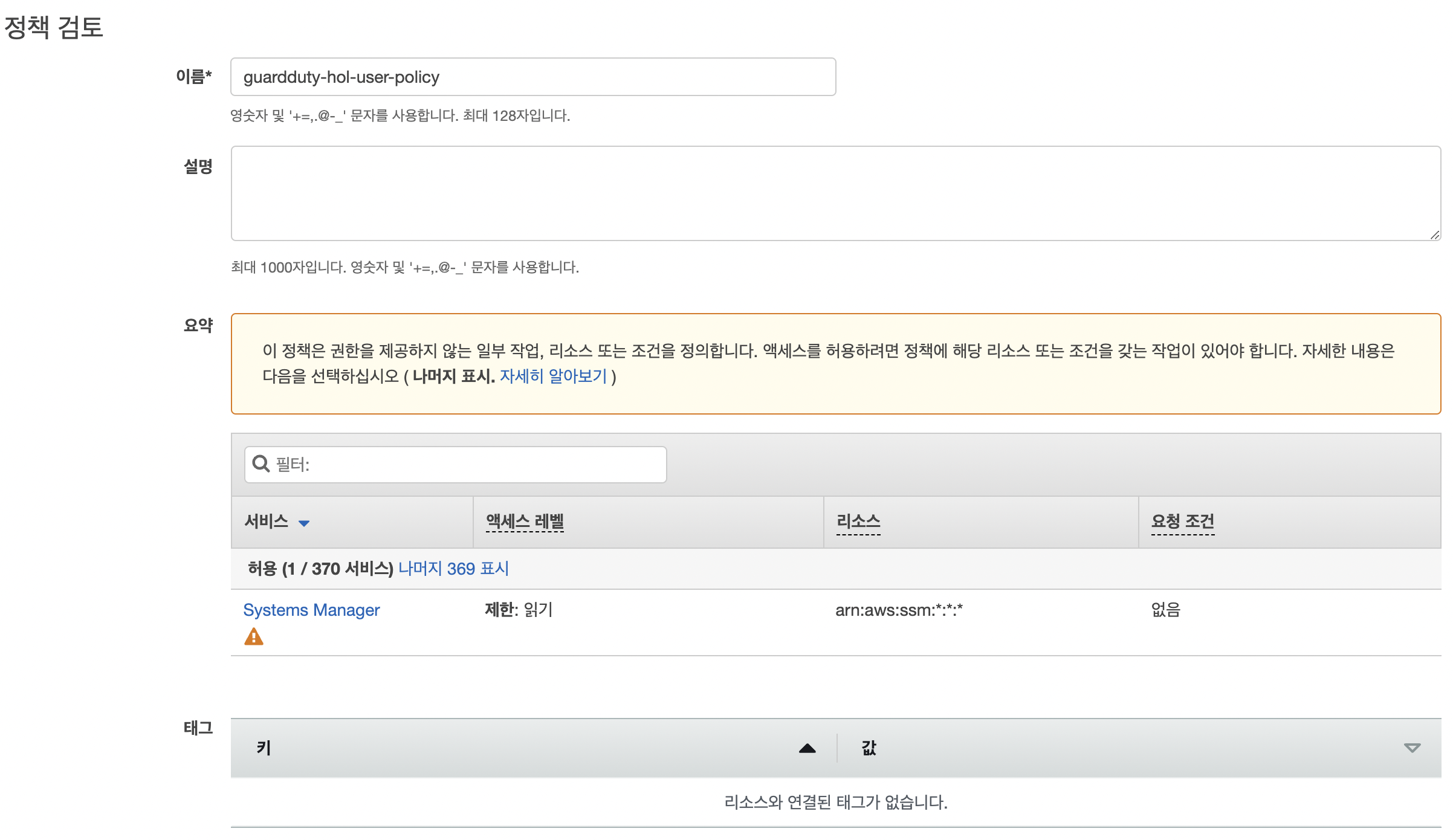
- 정책 신규 생성
- 정책 json
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "ssm:GetParameter", "ssm:GetParameters", "ssm:DescribeParameter" ], "Resource": "arn:aws:ssm:*:*:*", "Effect": "Allow" } ] }
- 사용자
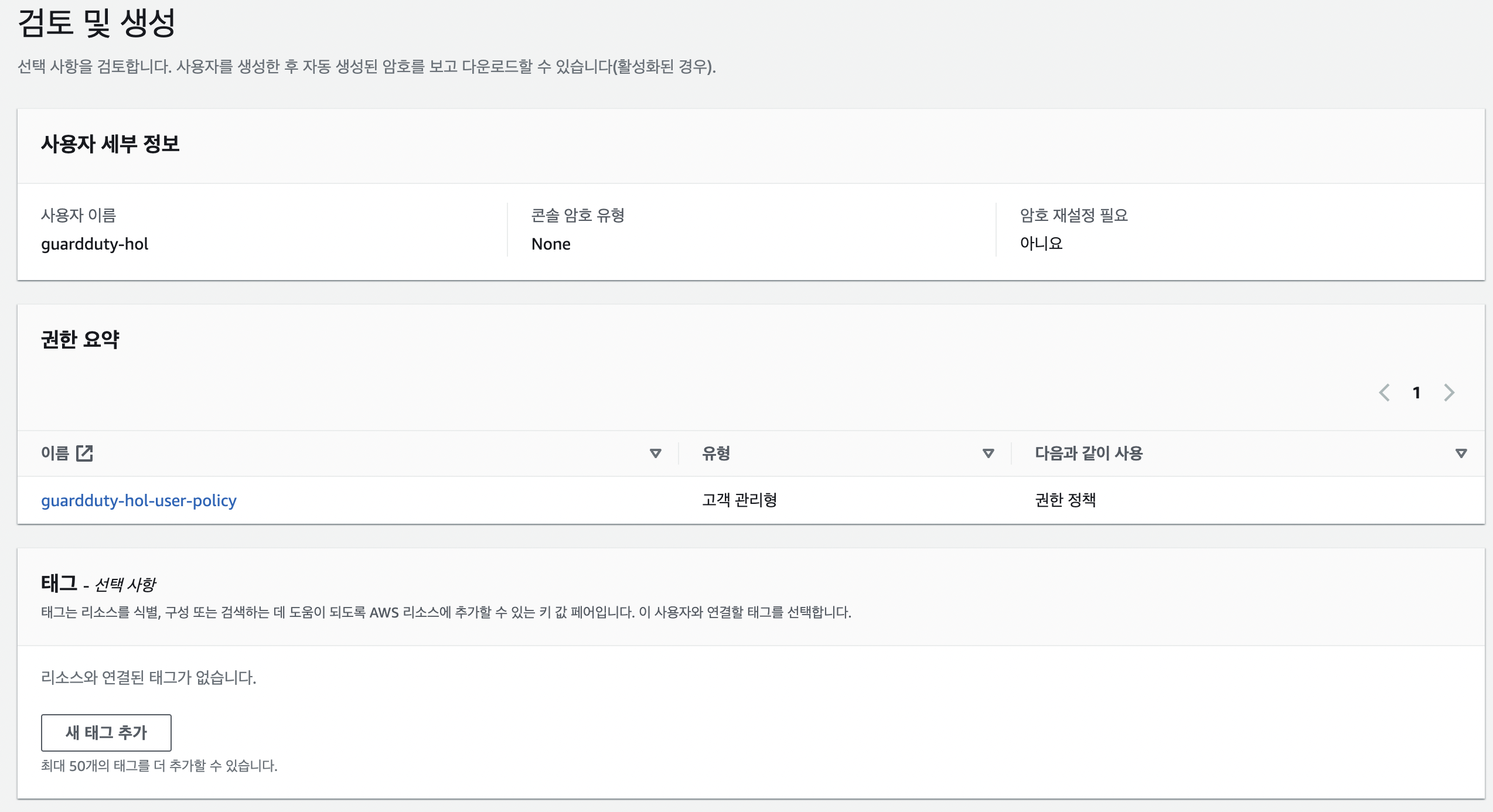
- 엑세스키는 별도로 생성
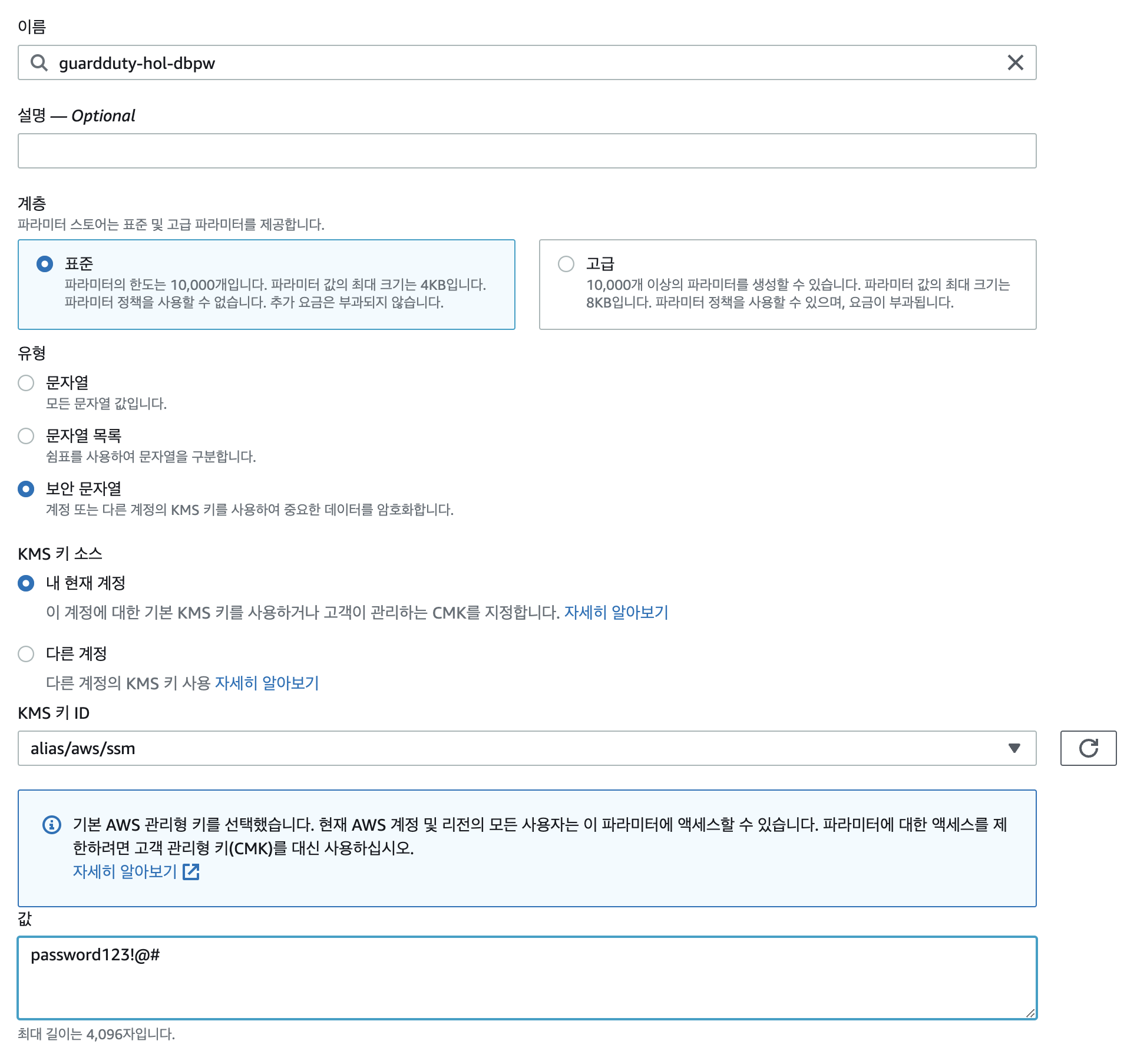
system manager
- aws cli로 system manager에 접근하는 공격을 해보기 위해 생성
ec2
- default vpc 사용
- 기본 amazon 이미지
- t2 micro
- 인스턴스 2개
- 키페어 새로 생성
- Security Group ip4 올오픈
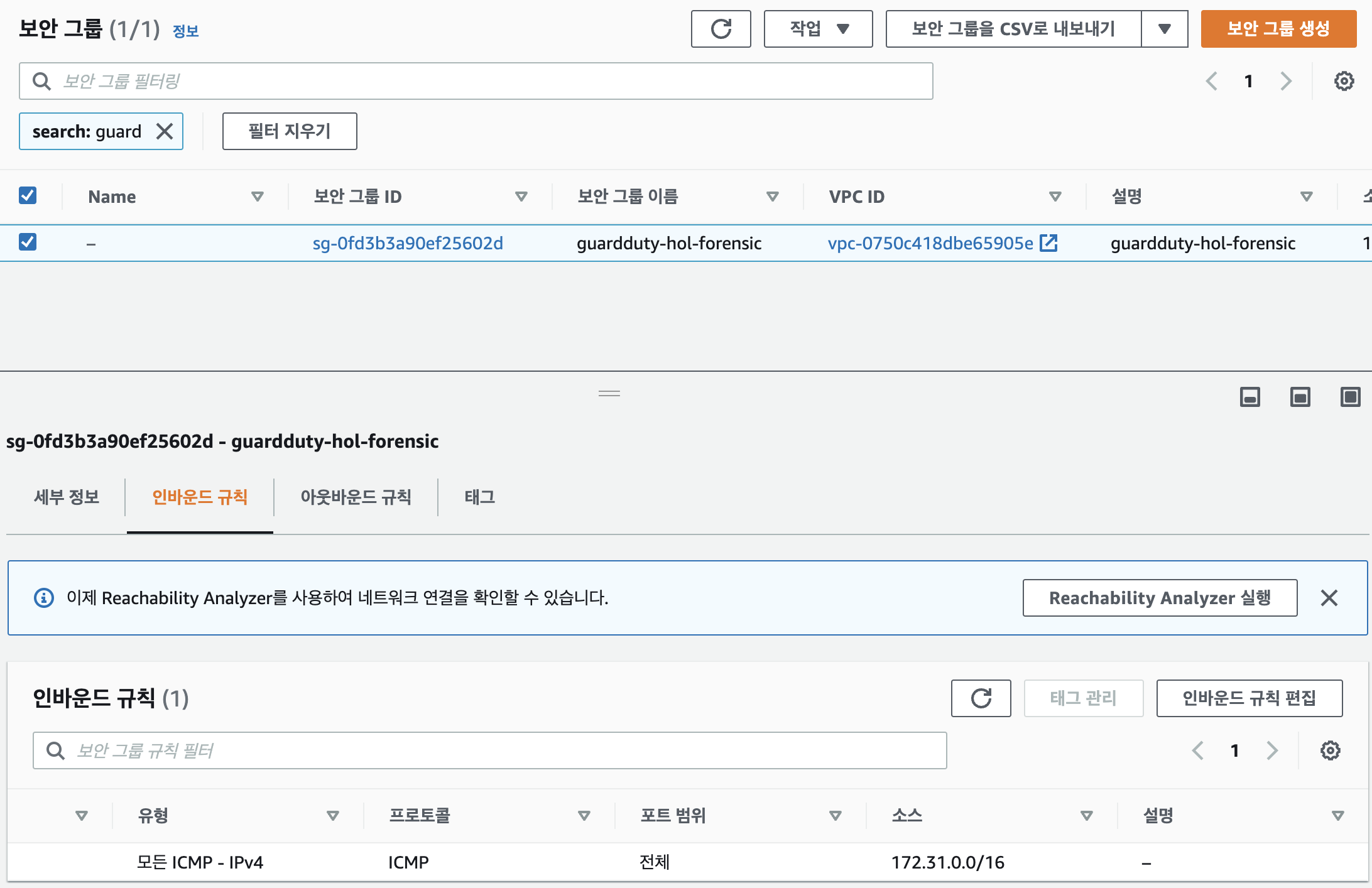
Security Group
- 인바운드 default vpc 설정
- 인스턴스를 격리시키기 위함
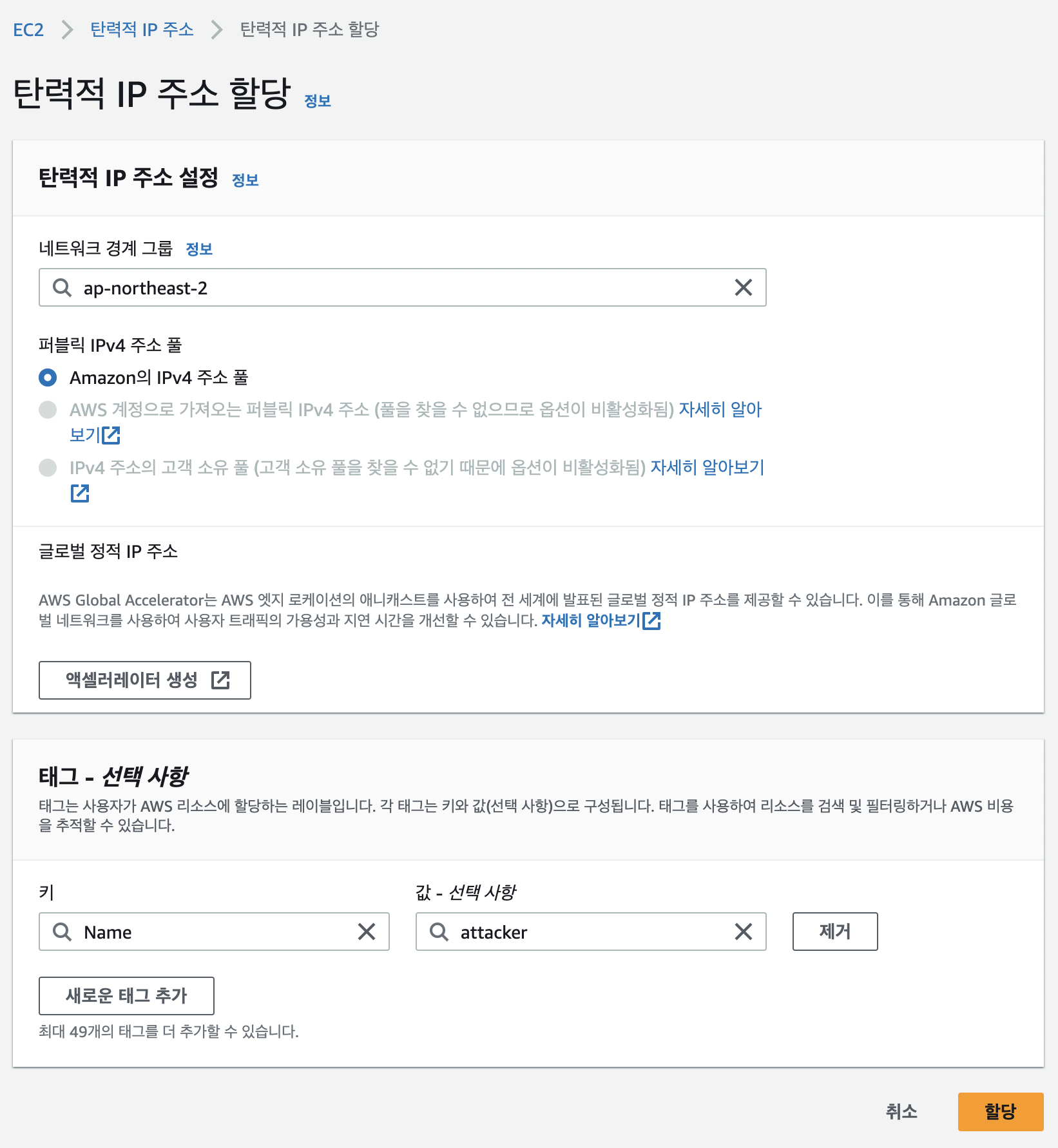
EIP
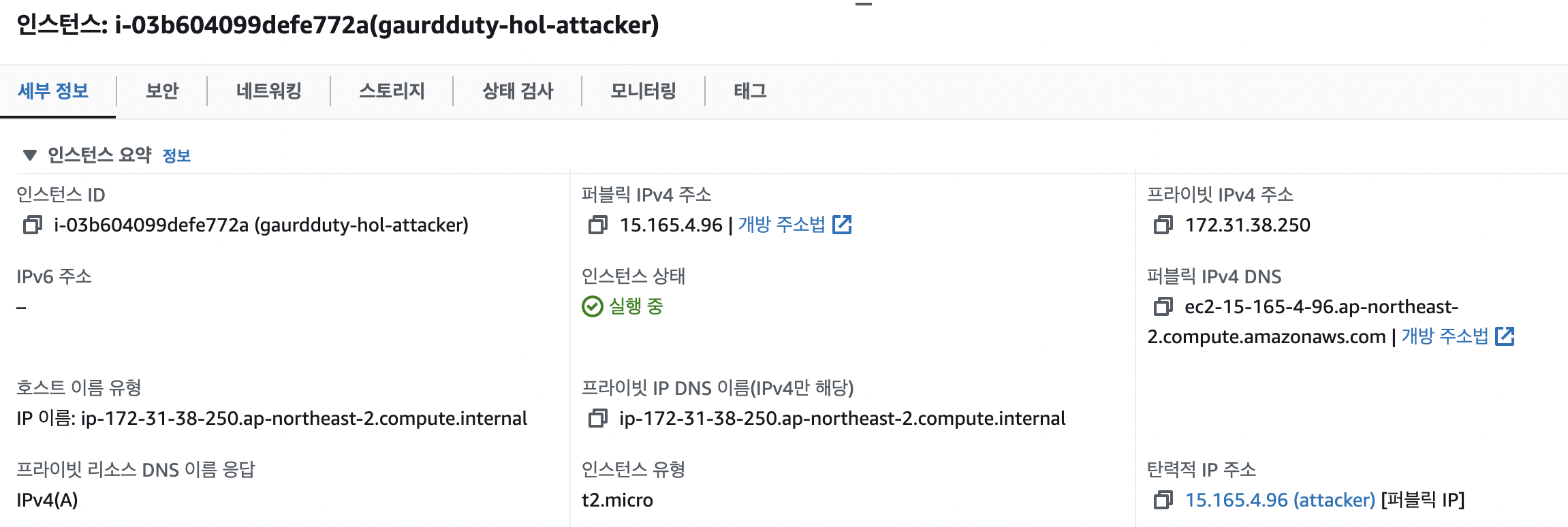
- 생성하고 attacker에 연결
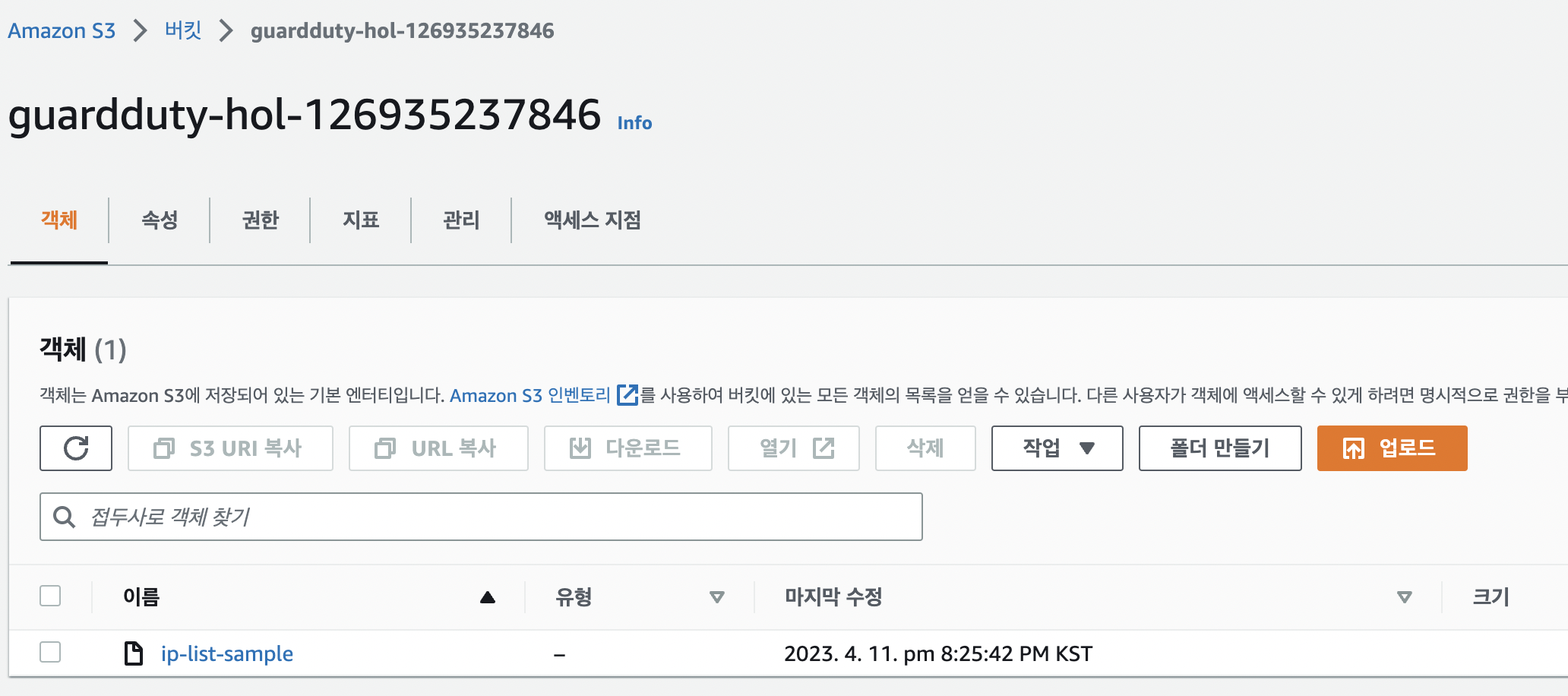
s3
- 이름은 모든 리전에 대해 유니크해야함
- 앞서 만든 eip를 텍스트로 저장하고 업로드
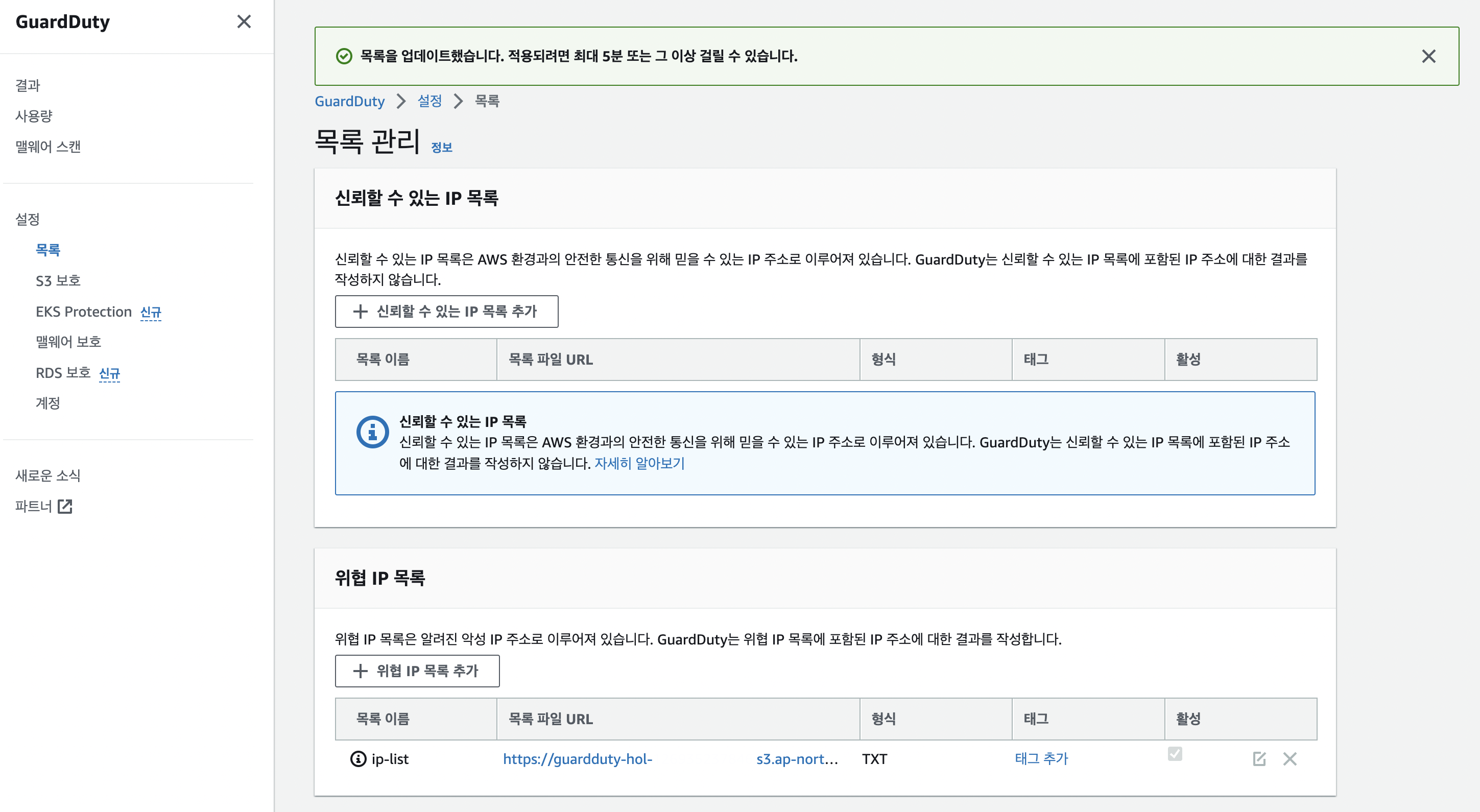
위협목록추가
- 앞서 가져온 iplist url을 Guardduty 위협 ip목록에 추가한다
lambda
-
Guardduty에서 탐지된 로그를 분석하여 보안 조치할 수 있도록 설정
- 인스턴스의 sg를 격리시키고, 메일발송
-
python 코드
from __future__ import print_function from botocore.exceptions import ClientError import boto3 import json import os def lambda_handler(event, context): # Log out event print("log -- Event: %s " % json.dumps(event)) # Create generic function response response = "Error auto-remediating the finding." try: ec2 = boto3.client('ec2') # Set Variables instanceID = event["detail"]["resource"]["instanceDetails"]["instanceId"] security_group_id = os.environ['FORENSIC_SG'] if instanceID == os.environ['INSTANCE_ID']: print("log -- Security Group Created %s : " % (security_group_id)) # Isolate Instance ec2 = boto3.resource('ec2') instance = ec2.Instance(instanceID) print("log -- %s, %s" % (instance.id, instance.instance_type)) instance.modify_attribute(Groups=[security_group_id]) # Send Response Email response = "GuardDuty Remediation | ID:%s: GuardDuty discovered an EC2 instance (Instance ID: %s) that is communicating outbound with an IP Address on a threat list that you uploaded. All security groups have been removed and it has been isolated. Please follow up with any additional remediation actions." % (event['detail']['id'], event['detail']['resource']['instanceDetails']['instanceId']) sns = boto3.client('sns') sns.publish( TopicArn=os.environ['TOPIC_ARN'], Message=response ) print("log -- Response: %s " % response) else: print("log -- Instance unrelated to GuardDuty-Hands-On environment.") except ClientError as e: print(e) print("log -- Response: %s " % response) return response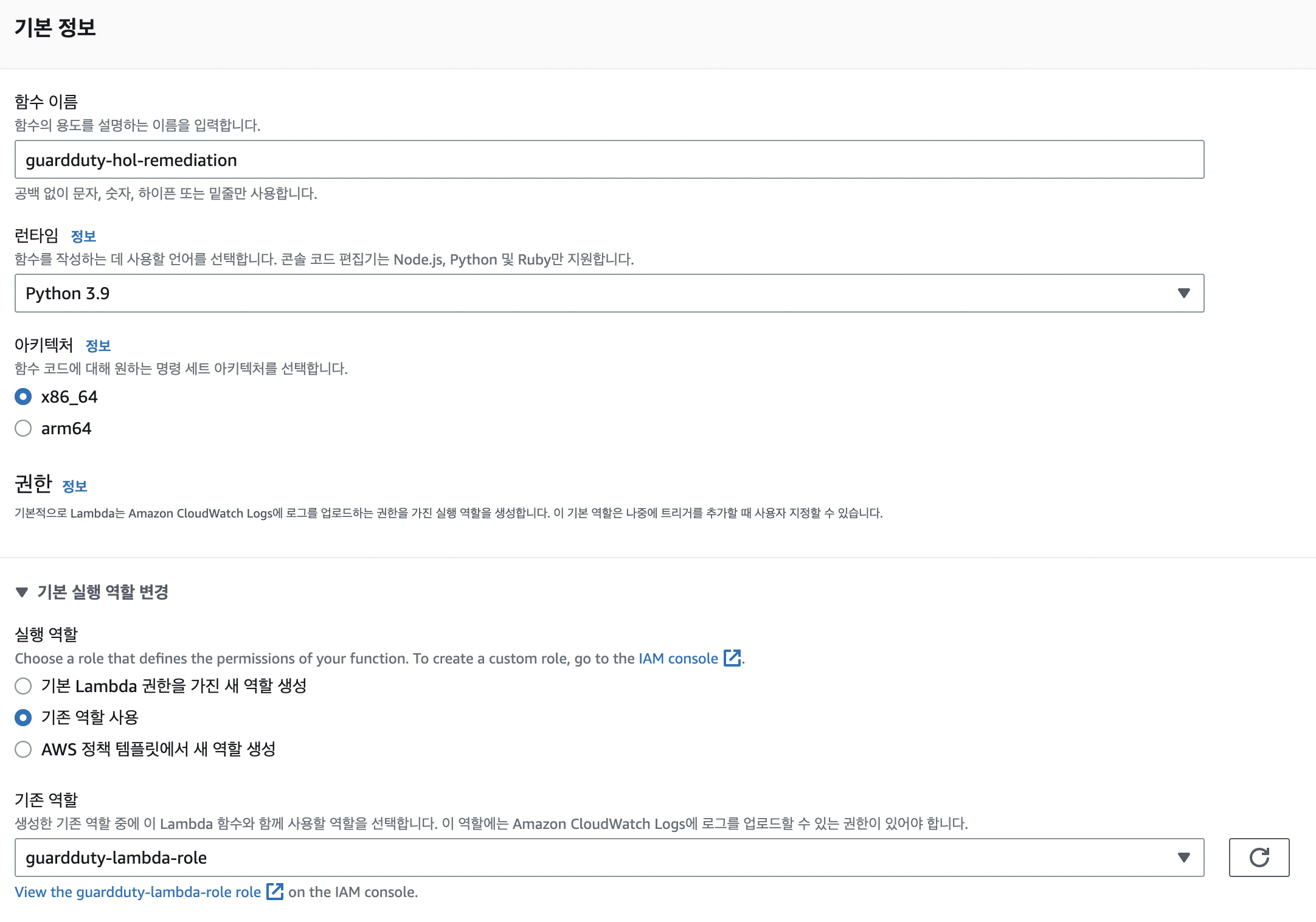
-
구성 > 시간 30초로 변경
-
환경변수
- python코드에서 사용하는 변수를 미리 세팅
- forensic_sg = security group 신규생성 했던걸로.
- instance_id= victim
- topic_arn = sns arn
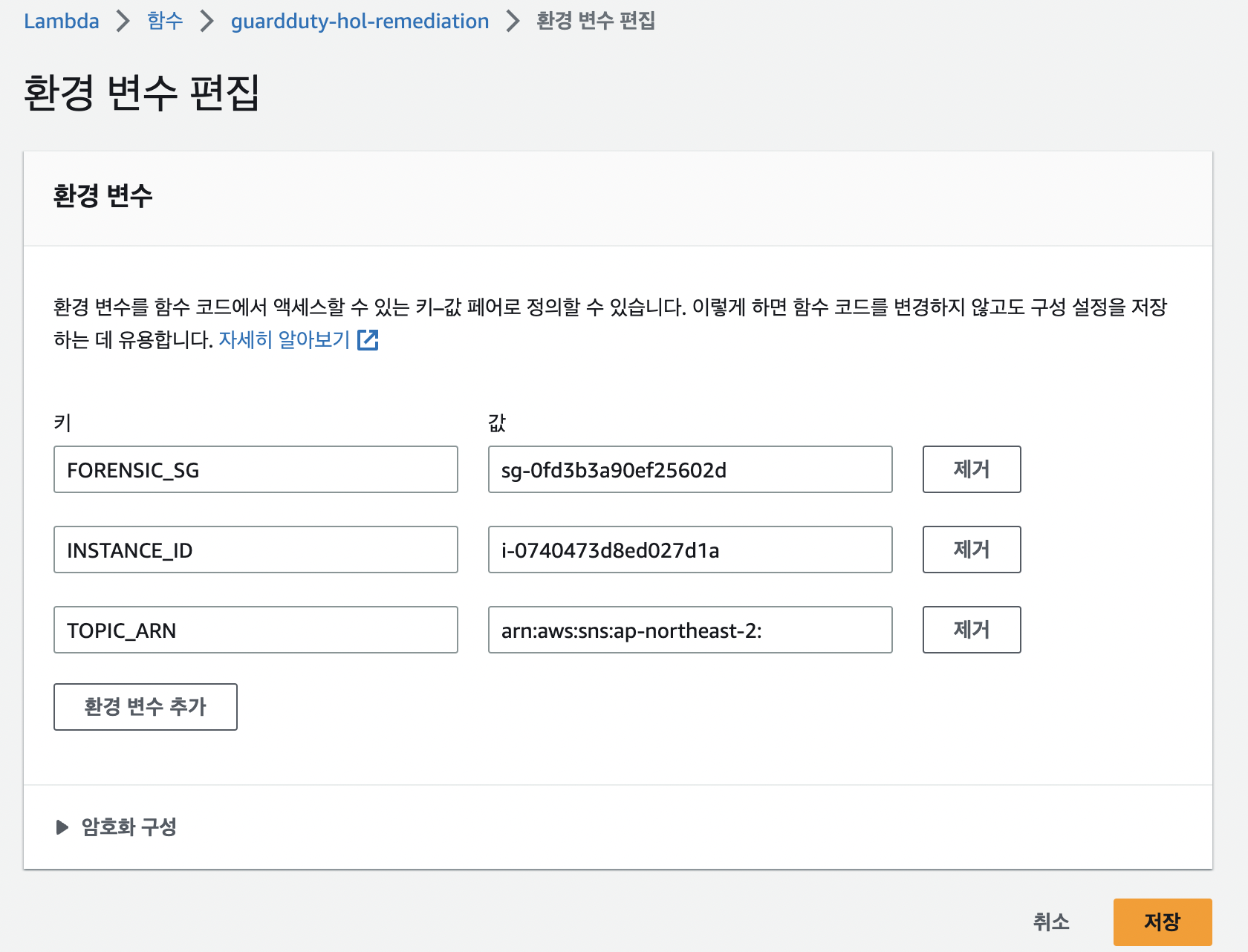
EventBridge
-
guardduty의 로그가 생성되었을때 lambda를 실행할수있도록 이벤트 규칙을 생성.
-
규칙 생성
- 인스턴스가 지정된 위협ip로 연결하는것을 탐지 했을때. lambda를 실행하고, 메일발송(**UnauthorizedAccess:EC2/MaliciousIPCaller.Custom)**
-
유형 참고
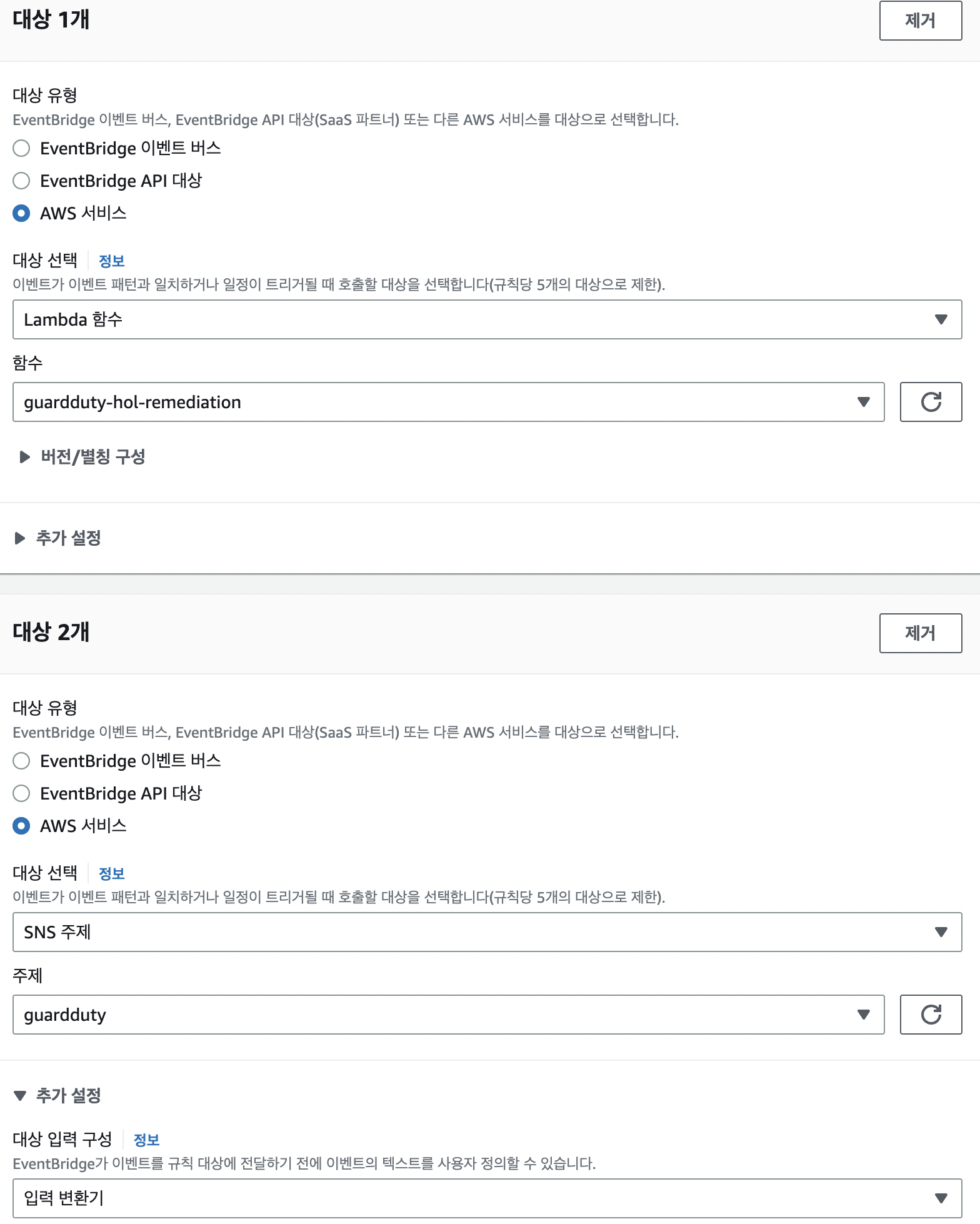
- 지정된 위협ip에 대해 iam api호출이 발생했을때, 메일 발송
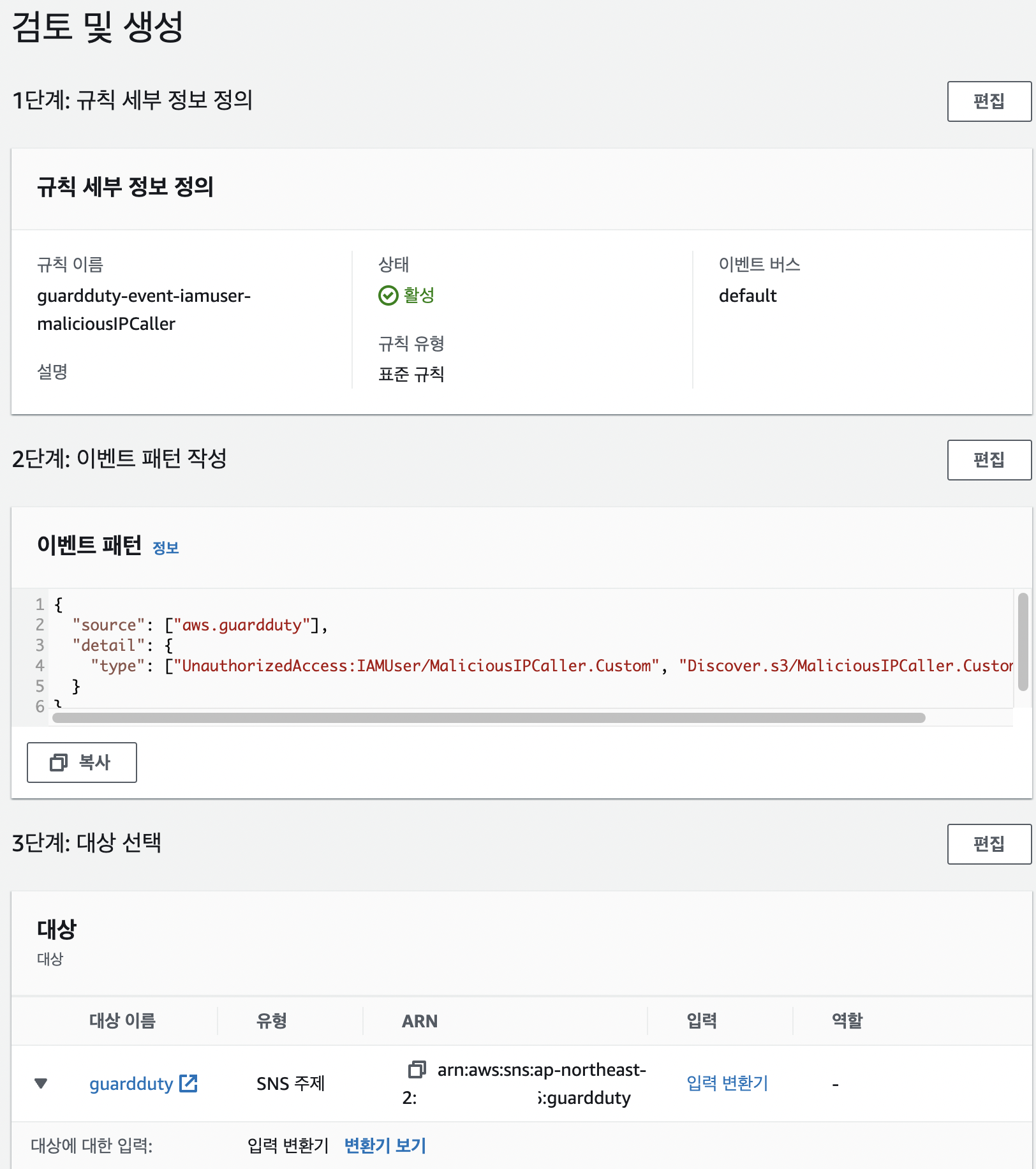
-
입력변환기
- 입력으로 들어온 텍스트를 변경해준다.
- 로그의 정보를 가지고 치환하여 메일로 전송할때 사용.
#****UnauthorizedAccess:EC2/MaliciousIPCaller.Custom**** #입력경로 {"gdid":"$.detail.id","instanceid":"$.detail.resource.instanceDetails.instanceId"} #템플릿 "GuardDuty Finding | ID:<gdid>: The EC2 instance <instanceid> may be compromised and should be investigated. Go to https://console.aws.amazon.com/guardduty" #UnauthorizedAccess:IAMUser/MaliciousIPCaller.Custom, Discovery:S3/MaliciousIPCaller.Custom #입력경로 {"gdid":"$.detail.id","userName":"$.detail.resource.accessKeyDetails.userName"} #템플릿 "GuardDuty Finding | ID:<gdid>: An AWS API operation was invoked (userName: <userName>) from an IP address that is included on your threat list and should be investigated. Go to https://console.aws.amazon.com/guardduty"
# 첫번째 시나리오
- 서비스 중인 인스턴스가 손상
- 위협 ip로 등록된 서버로 통신이 되는중
- 본 실습에서는 icmp로 대체
- vpc flow log를 guardduty가 분석
- cloudwatch에 규칙을 생성 하고 탐색된 위협에 대해 알람
- 동시에 lambda를 통해 인스턴스를 격리시킴
- 외부와 통신을 할 수 없도록 생성된 sg을 적용시킴
step1. 취약한 ec2에서 공격자의 서버로 ping을 날린다
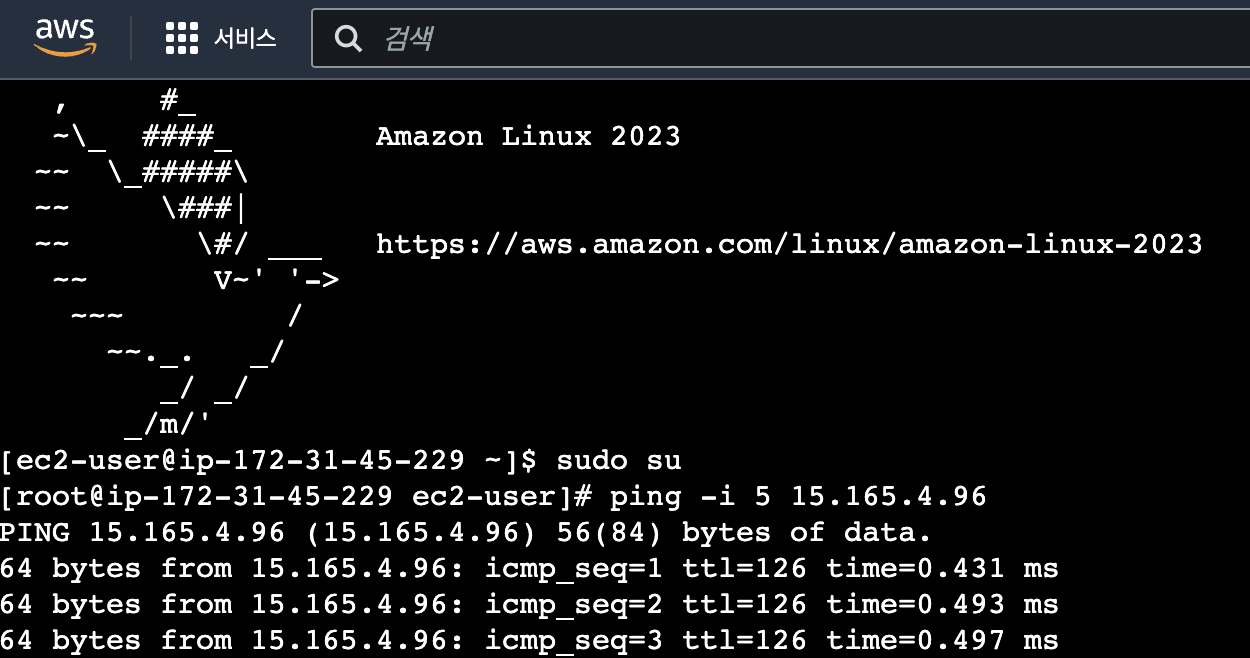
결과
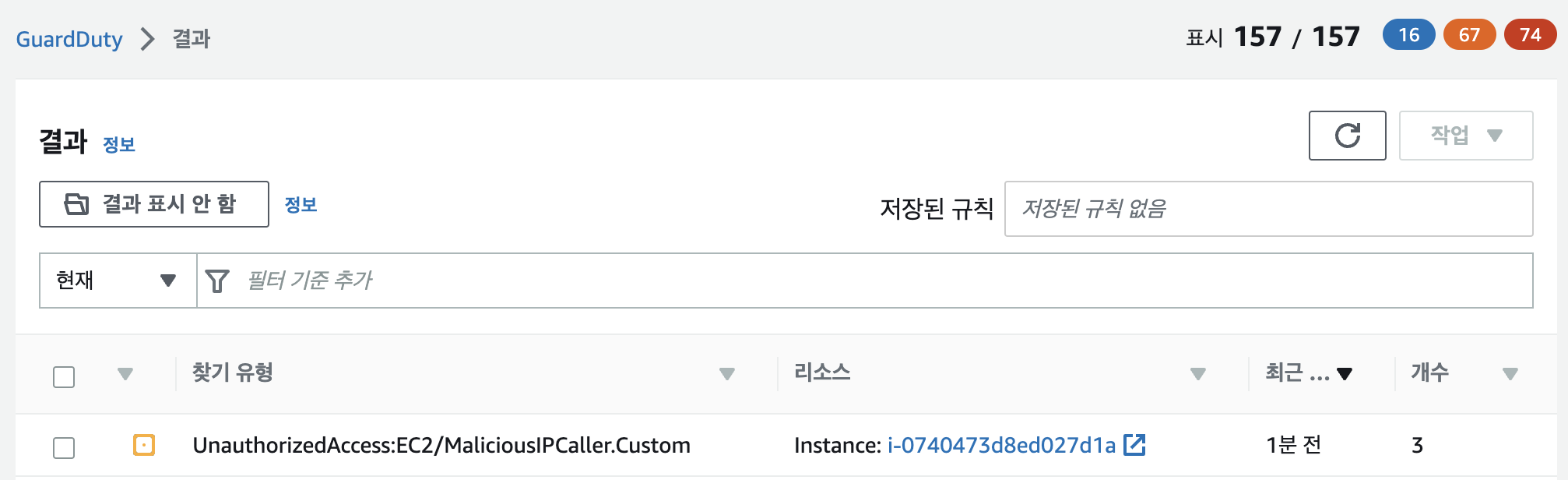
- Guardduty 로그 확인
- 앞서 만든 커스텀 룰에 대한 표시.
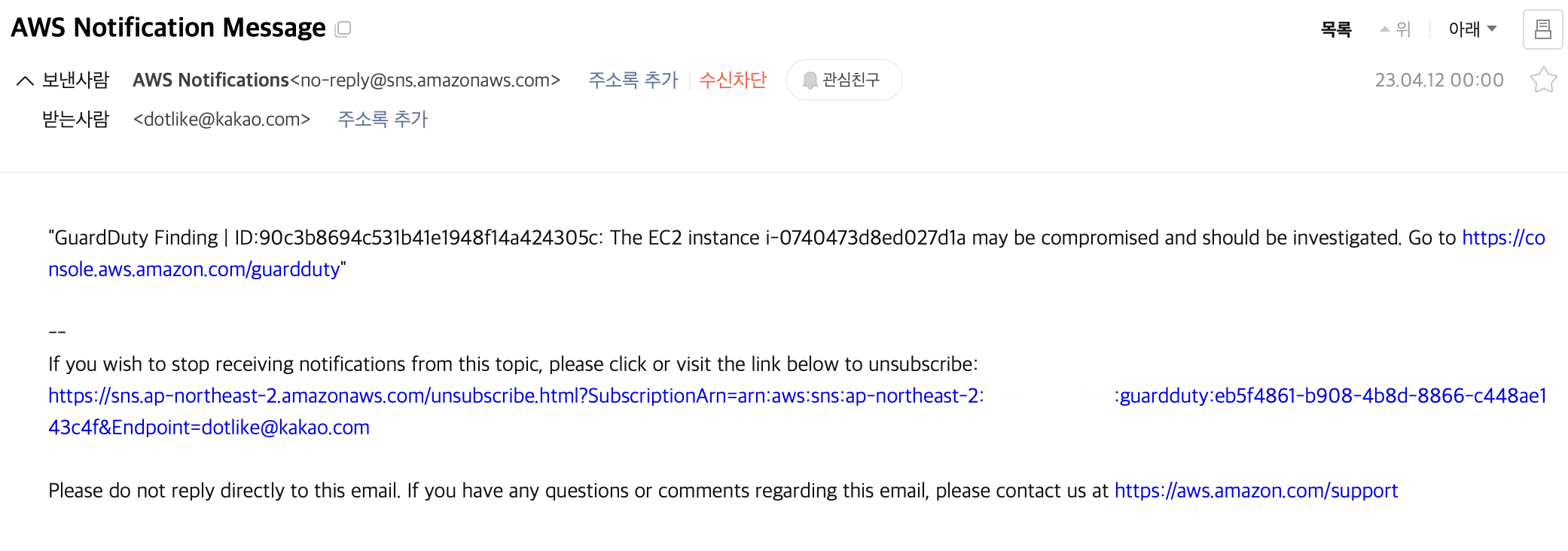
- guardduty 로그 메일 알람
- lambda 실행로그 확인
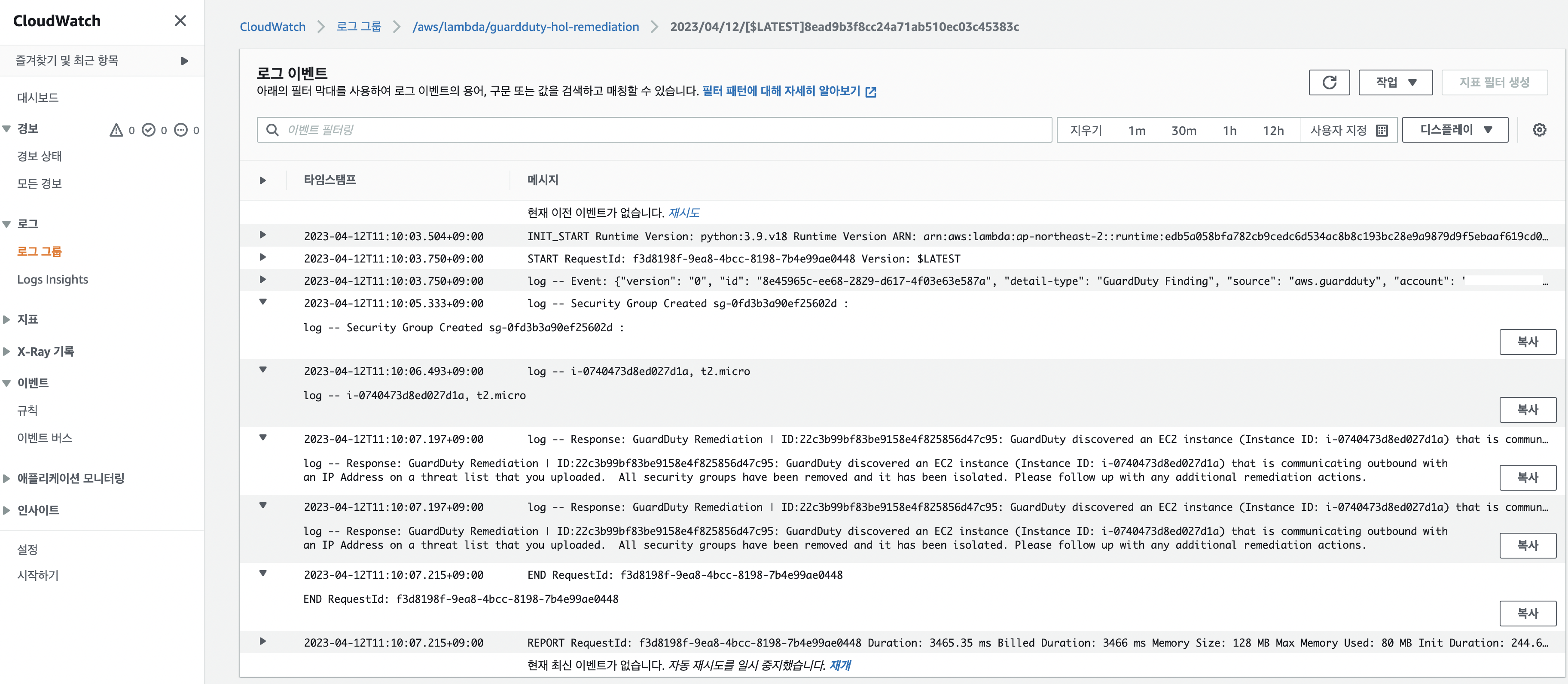
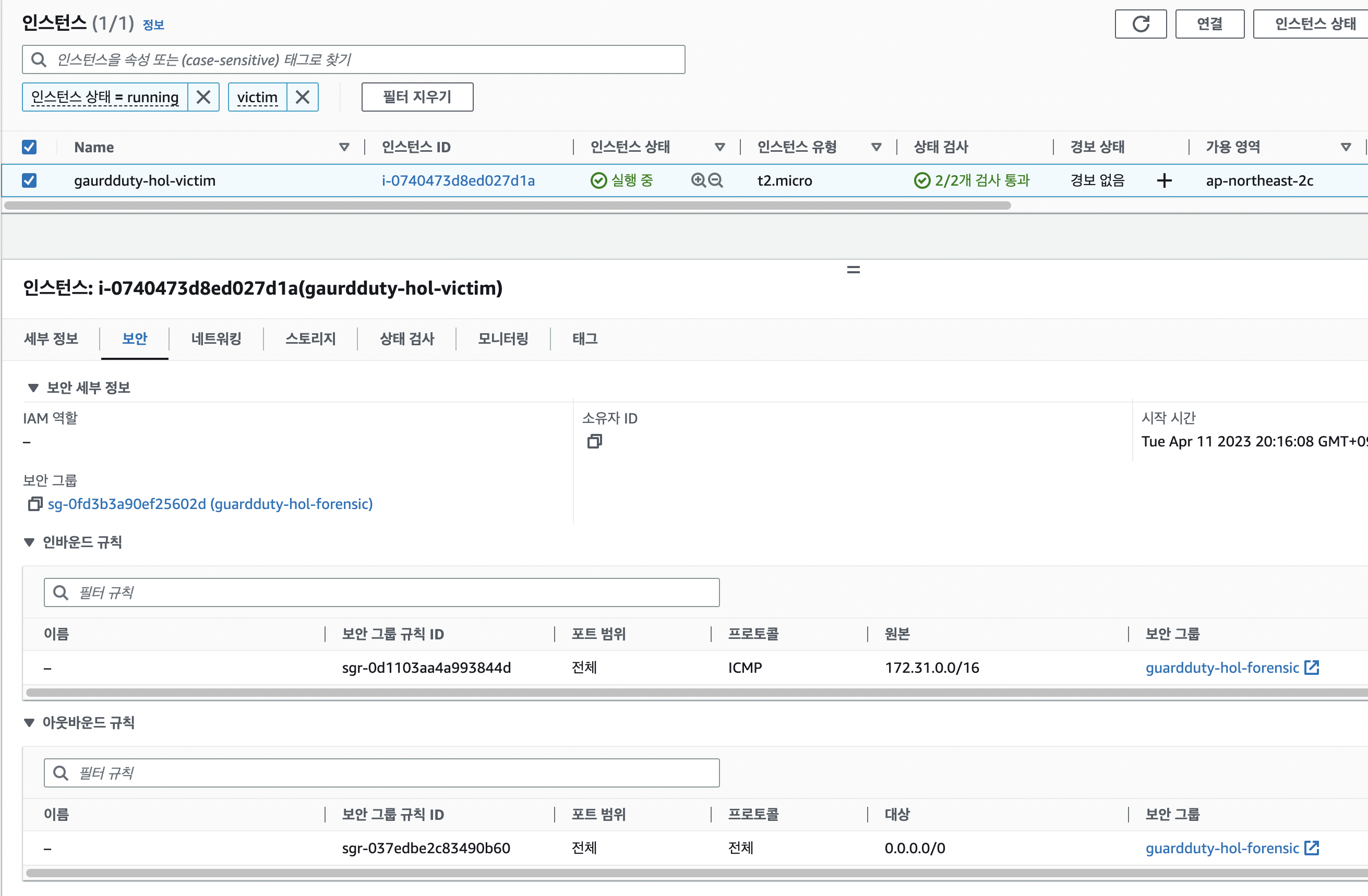
- 격리된 인스턴스 확인
- 격리 메일 알림 확인

# 두번째 시나리오
- 공격자서버(위협ip로 등록된 서버)에서 탈취된 iam계정에 access key, secret key로 권한이 없는 서비스와
권한이 있는 서비스에 접근하려는 시도를 탐지해서 알람을 받도록 설정
step1. 공격자 서버에 sh 생성
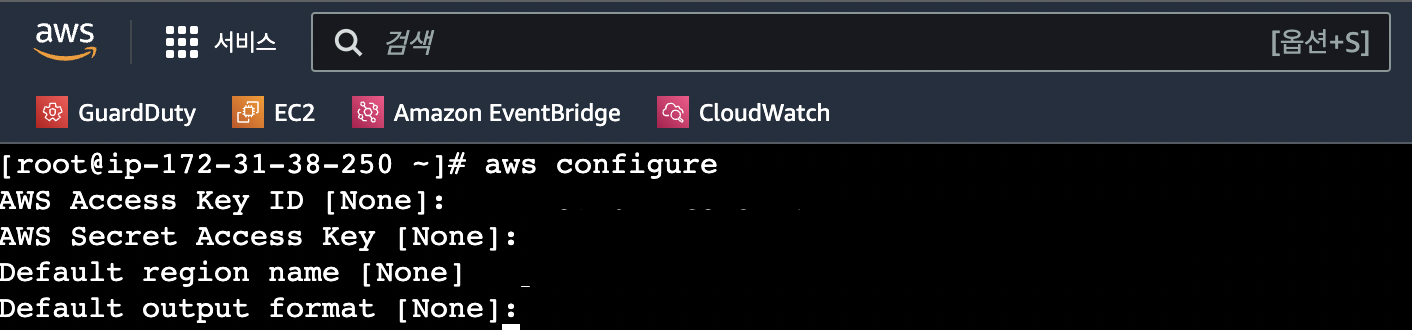
step2. iam 계정 생성시 만든 액세스키 를 “aws configure” 명령을 통해 설정
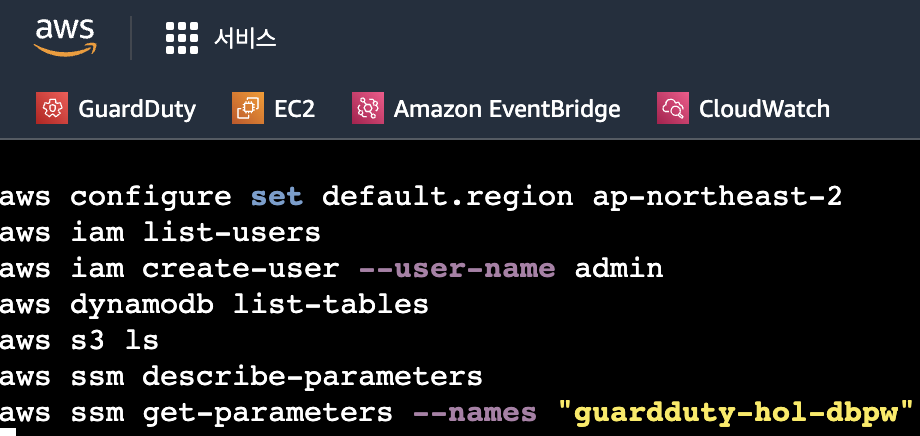
step3. 미리 지정된 스크립트를 실행.
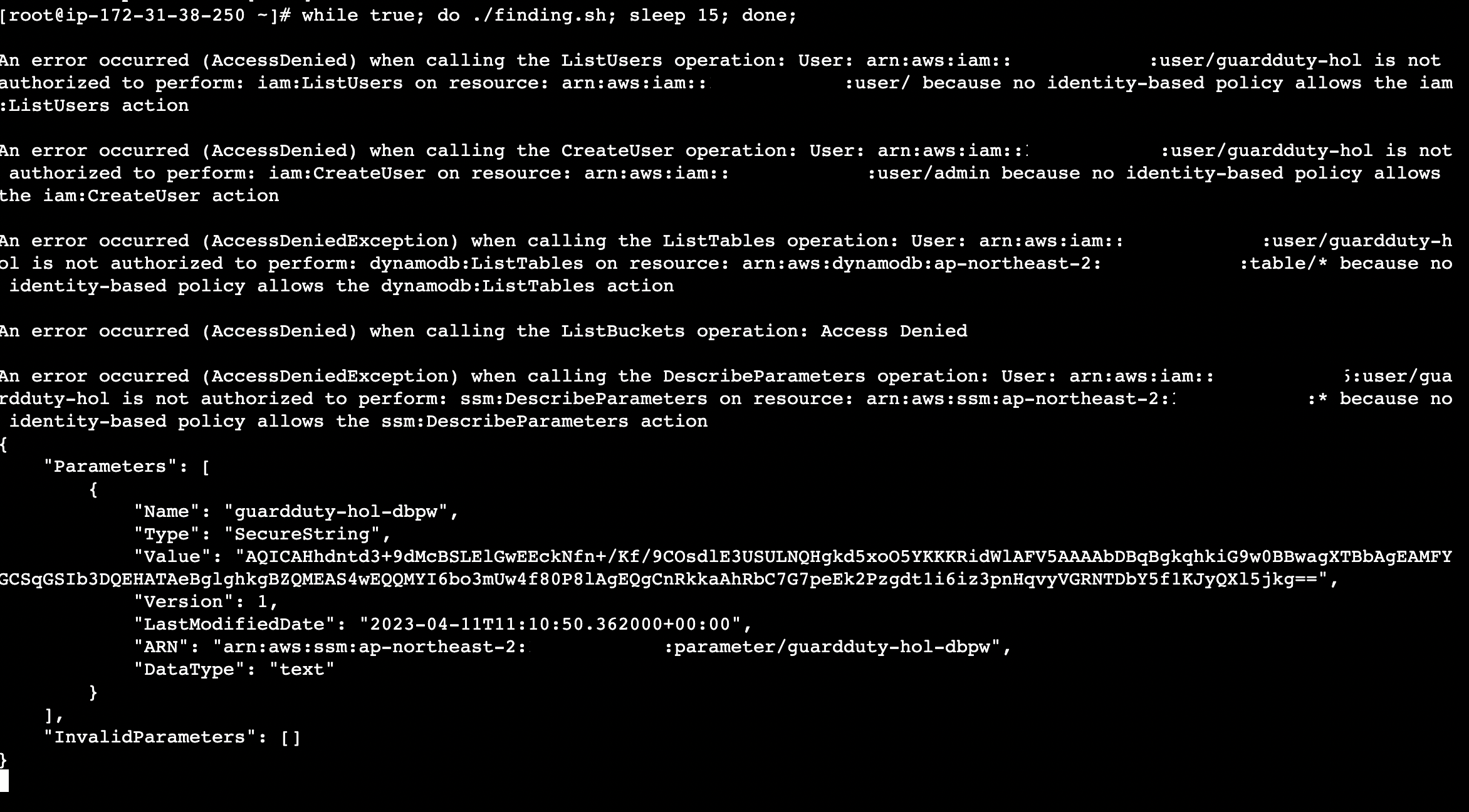
결과
- list user 명령에 대한 탐지
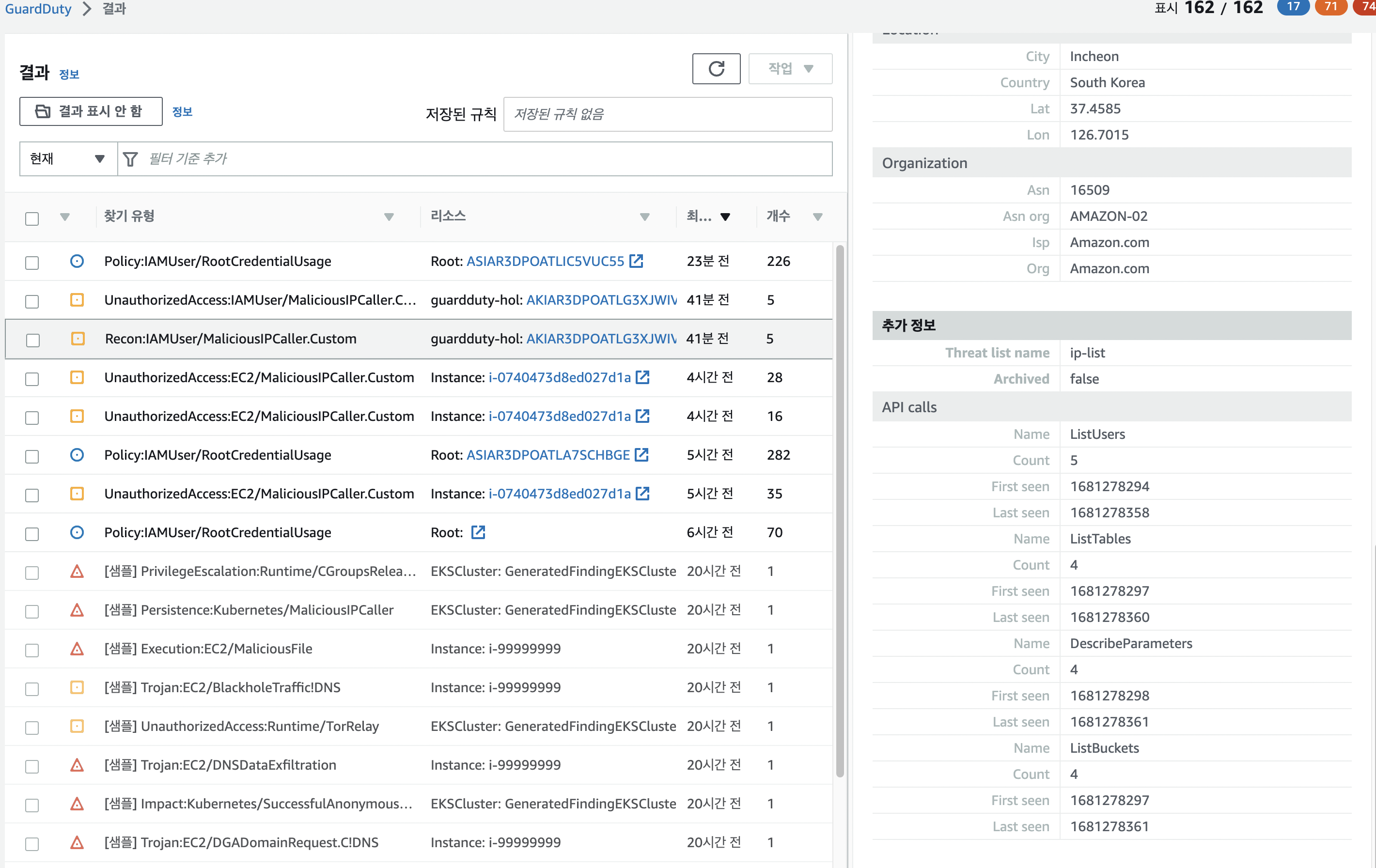
-
create user 명령에 대한 탐지
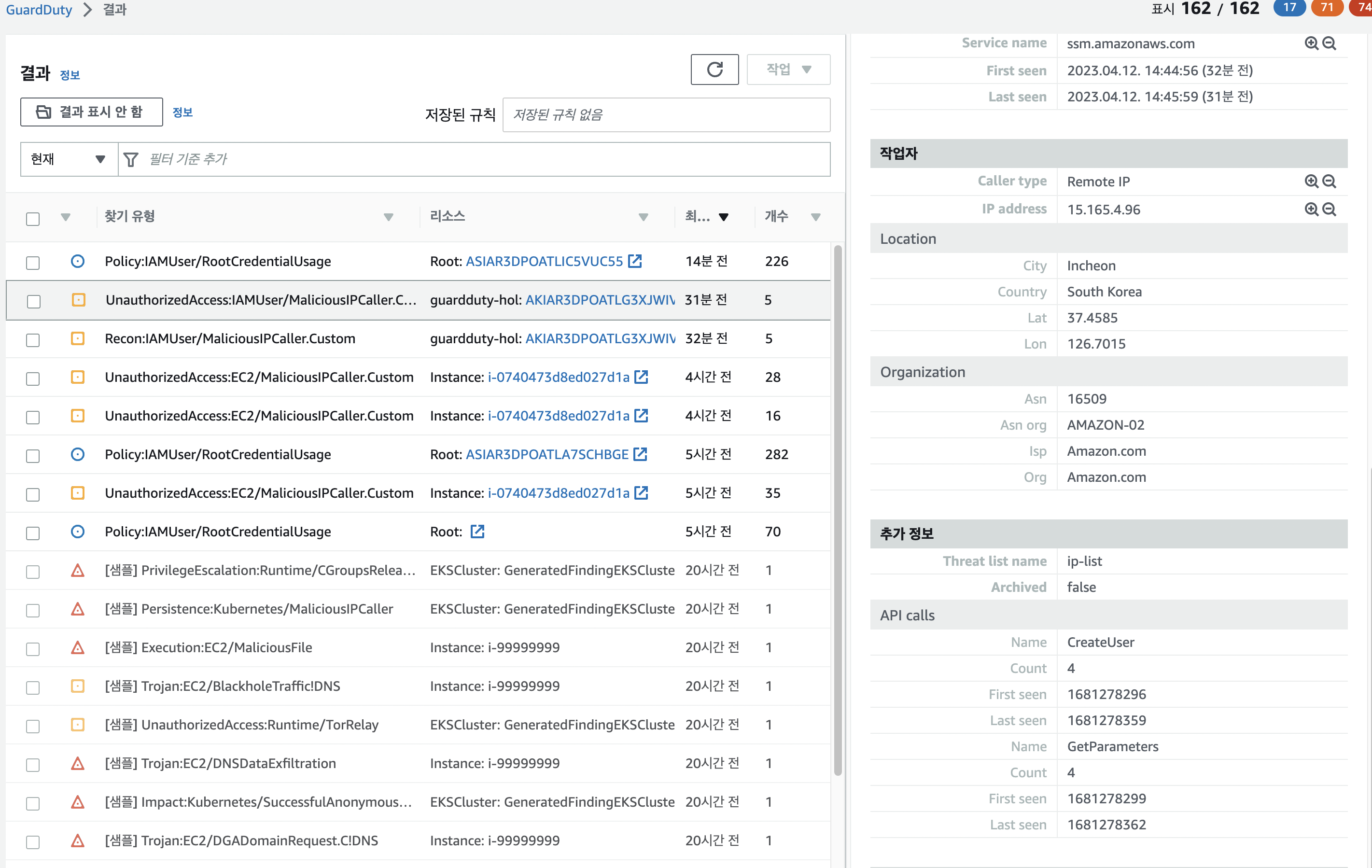
-
sns event 확인