
📌JWT ?
JWT (Json Web Token) 은 RFC 7519 웹 표준으로 지정된 JSON 객체를 사용해서 토큰 자체에 정보를 저장하는 Web Token 입니다. 다른 인증 방식들에 비해 가볍고 간편해서 유용한 인증방식 입니다.
📌JWT 구조
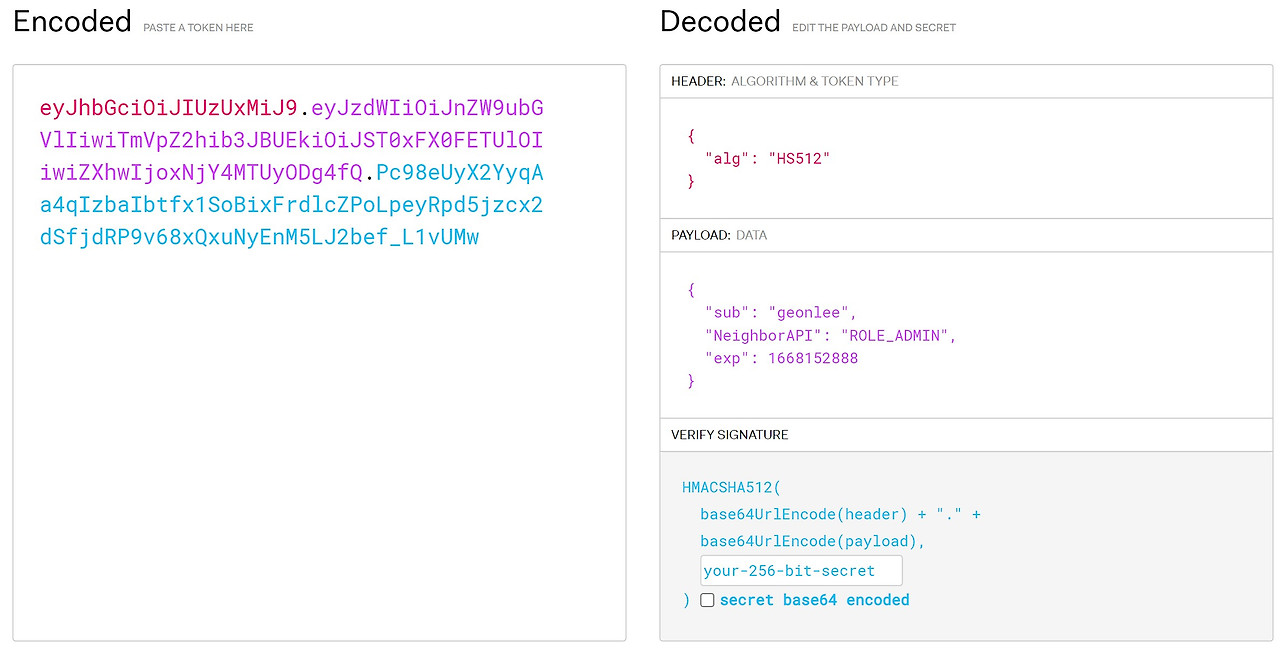
JWT는 Header, Payload, Signature 로 구성되어 있습니다.
Header : Signature를 해싱하기위한 알고리즘 정보.
Payload : 서버와 클라이언트가 주고받는 시스템에서 실제 사용될 데이터 정보.
Signature : 토큰의 유효성 검증을 위한 문자열. 헤더와 페이로드를 비밀키로 서명한 값. 이 서명을 통해 데이터의 무결성을 보장하고, 클라이언트가 토큰을 변조할 수 없게 합니다.
📌JWT의 장점
자체 포함(Self-contained)
JWT는 사용자 정보와 같은 클레임을 자체적으로 포함하므로 별도의 데이터베이스 조회 없이 정보 확인이 가능합니다.
확장성
JWT는 다양한 클레임을 담을 수 있어 유연하게 사용할 수 있습니다. 시스템 수평 확장이 용이합니다.
토큰 기반 인증
서버에 상태 정보를 저장할 필요 없이, 클라이언트가 토큰을 보유해 상태를 유지합니다.(Stateless)
인코딩
Base64 URL Safe Encoding을 사용하기 때문에 URL, Cookie, Header 모두 사용 가능합니다.
📌JWT의 단점
토큰 크기
페이로드에 포함된 정보가 많아지면 토큰 크기가 커집니다.
무효화 어려움
JWT는 발급 후 만료 전까지는 무효화가 어려워, 즉시 로그아웃 처리나 토큰 해지 등의 작업이 어렵습니다.
📌단점 보완
JWT의 가장 큰 장점은 세션과의 차이에서 알 수 있는데, 세션과 다르게 접근에 대한 상태정보를 서버에서 관리하지 않기 때문에 서버의 부하를 상대적으로 줄일 수 있습니다. 이를 Stateless 하다고 표현 합니다. 하지만 이러한 상태정보를 서버에서 관리하지 않기 때문에 Access Token이 탈취 되었을 때 Token이 만료되기 전까지는 탈취된 Token에 대해서 어떠한 조치를 취할 수가 없습니다. 그래서 Access Token의 만료 시간을 짧게 설정을 하게 됩니다.
📍Refresh Token
Access Token의 만료 시간을 짧게 설정하게 되면 사용자는 그만큼 자주 로그인이라는 과정을 거쳐야 합니다. 자주 사용하는 사이트인데 계속 로그아웃 처리가 된다면 사용자는 엄청 불편해 하겠죠. 그래서 만료 시간이 긴 Refresh Token을 사용하게 됩니다. Access Token이 만료 되었을 때 로그인 시 받은 Refresh Token으로 Token의 갱신을 요청하고, 갱신된 토큰으로 이전에 요청한 API를 다시 요청하는 것이죠.
📍Access & Refresh Token 만료 기한
일반적으로 Access Token은 1분 ~ 30분 정도, Refresh Token은 1주 or 그 이상 정도의 만료시간을 설정합니다. 보안 정책에 따라 다르게 설정합니다.
📍Refresh Token 탈취
만료 시간이 긴 Refresh Token 이 탈취되면 만료 전 까지는 보안상의 문제가 발생 할 것 입니다. 앞에서 말한것과 같이 Refresh Token의 경우에도 Stateless 하기 때문에 Access Token과 마찮가지로 탈취 되었을 때 서버에서는 어떠한 조치를 취할 수 없습니다.
로그인 시 발행 된 Refresh Token 을 저장매체(Database)에 저장하여 탈취 확인 시 저장된 Refresh Token을 변경하므로써 갱신을 막을 순 있겠지만, 이도 탈취를 확인했을 때에 한하여 가능한 대책입니다.
여기에 RTR (Refresh Token Rotation) 을 적용할 수도 있습니다. Refresh Token을 활용하여 갱신을 한 번만 할 수 있게 설정하는 방식인데요. Refresh Token으로 Access Token을 갱신할 때 Refresh Token도 갱신하여 저장매체(Database)에 저장, 이전 Refresh Token으로 갱신 요청 시 탈취된 것으로 판단하여 저장 매체의 Refresh Token 초기화하는 방법입니다.
📍Token 탈취에 대한 보안 대책
통신 중에 Token이 탈취되거나 조작되지 않도록 HTTPS 사용.
Token의 만료기간을 짧게 설정.
CSRF(Cross-Site Request Forgery) 방지, security 적용.
📌Example
SpringBoot 3.3.1, gradle Procject 예시 코드입니다.
Spring Security 와 JWT 를 적용하기 위한 의존성 주입을 추가합니다.
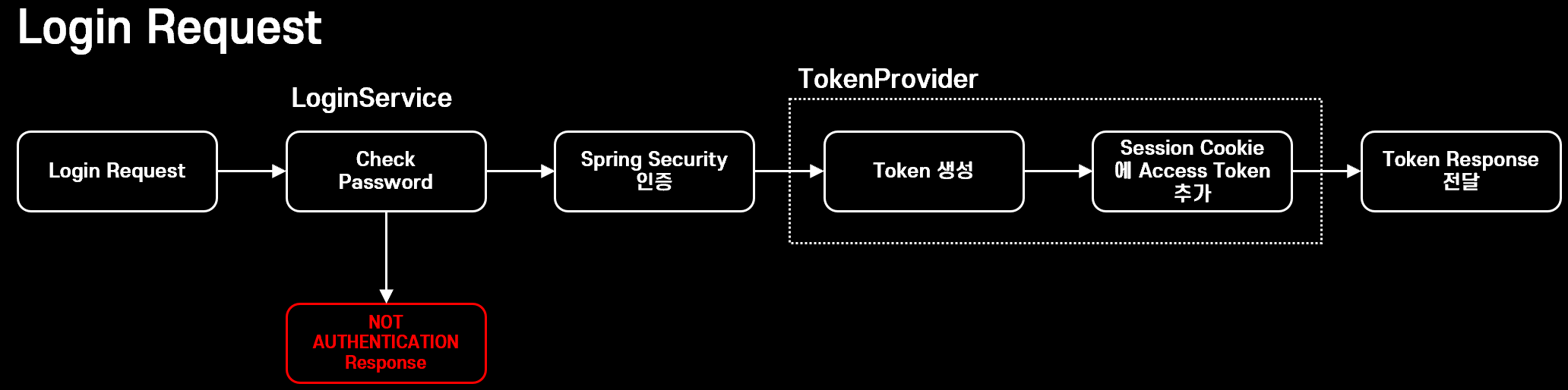
📍로그인 로직
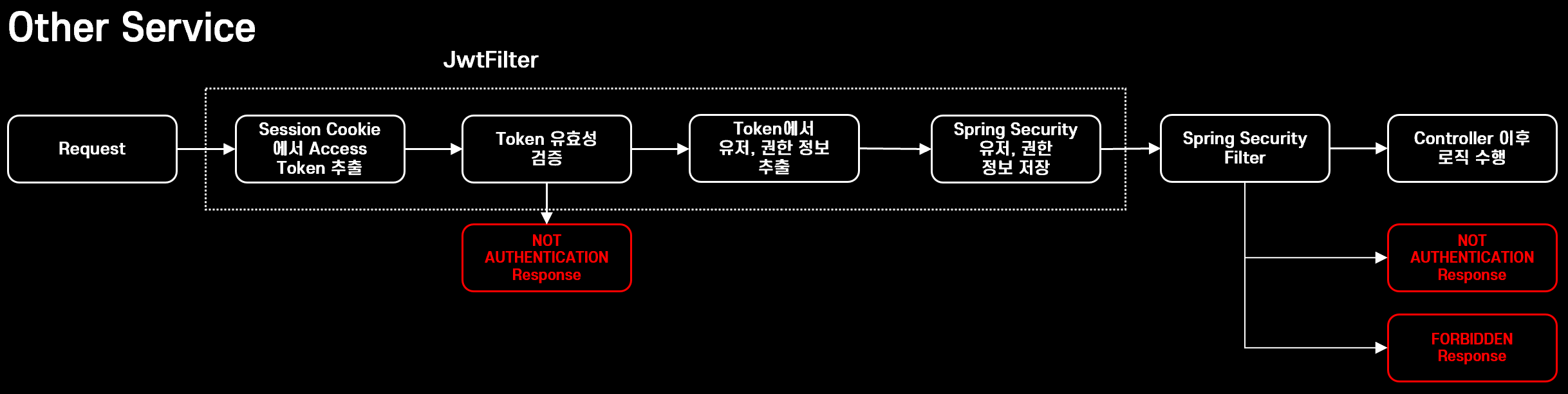
📍로그인 이후 서비스 로직
📍의존성 추가
build.gradle
dependencies {
implementation 'org.springframework.boot:spring-boot-starter-web'
implementation 'org.springframework.boot:spring-boot-starter-security'
//생략..
//JWT
implementation group: 'io.jsonwebtoken', name: 'jjwt-api', version: '0.12.6'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-impl', version: '0.12.6'
runtimeOnly group: 'io.jsonwebtoken', name: 'jjwt-jackson', version: '0.12.6'📍Application 설정
application.yml
jwt:
auth-key: ${jwt-key}
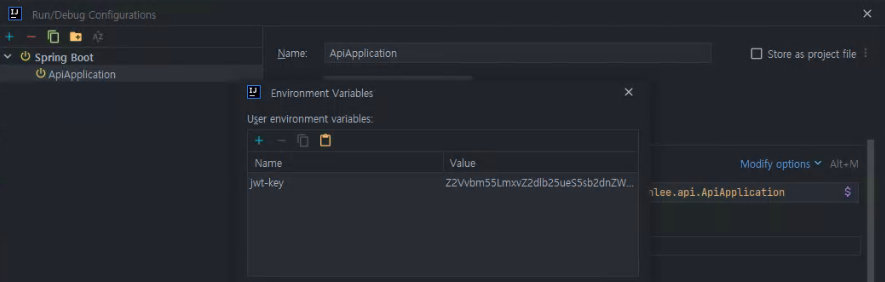
cookie-token-name: "GN_AUT"보안을 위해 jwt-key 는 환경변수에 등록을 합니다.
IntelliJ 에서 환경변수 등록하는 방법은 shift 두번 눌러 edit configurations 을 검색해 나온 팝업 창에서 Environment variables 에 값을 등록하면 됩니다. Environment variables 가 없다면 Modify opetions를 눌러 추가해 주어야 합니다.
jwt-key 는 사용할 알고리즘에 따라 길이를 맞추어 Base64로 인코딩된 값을 설정하시면 됩니다.
(Base64 인코딩은 검색하면 나오는 온라인 인/디코더를 활용하세요.)
📍TokenProvider 생성
Token의 생성, Cookie 에 Token 추가 및 추출, Claim 데이터 추출, Token 유효성 검증, XSS 공격 방지 기능을 위한 TokenProvider 를 구현합니다.
config.jwt.TokenProvider
@Component
@Slf4j
public class TokenProvider implements InitializingBean {
@Value("${server.servlet.context-path}")
public String contextPath;
@Value("${jwt.auth-key}")
private String jwtAuthKey;
@Value("${jwt.cookie-token-name}")
private String tokenNameInCookie;
private SecretKey signingKey;
public final String authClaimName = "AUTH";
@Override
public void afterPropertiesSet() {
this.signingKey = Keys.hmacShaKeyFor(Base64.getDecoder().decode(this.jwtAuthKey));
}
public TokenResponse createToken(Authentication authentication, Member member) {
String authorities = authentication.getAuthorities().stream()
.map(GrantedAuthority::getAuthority)
.collect(Collectors.joining(","));
Date now = new Date();
long dateTime = (now).getTime();
//1시간
long tokenValidityInMilliseconds = 1000 * 3600;
Date accessValidity = new Date(dateTime + tokenValidityInMilliseconds);
//24시간
long refreshTokenValidityInMilliseconds = 24 * (1000 * 3600);
Date refreshValidity = new Date(dateTime + refreshTokenValidityInMilliseconds);
return TokenResponse.builder()
.accessToken(
Jwts.builder()
.subject(authentication.getName())
.claim(this.authClaimName, authorities)
.issuedAt(now)
.expiration(accessValidity)
.signWith(this.signingKey)
.compact())
.refreshToken(
Jwts.builder()
.subject(authentication.getName())
.claim(this.authClaimName, authorities)
.issuedAt(now)
.expiration(refreshValidity)
.signWith(this.signingKey)
.compact())
.build();
}
public String getTokenFromCookie(HttpServletRequest httpServletRequest) {
Cookie[] cookies = httpServletRequest.getCookies();
String requestURI = httpServletRequest.getRequestURI().replace(this.contextPath, "");
if (cookies == null) {
log.error("No cookies found in request. Request URI: {}", requestURI);
return null;
}
return Arrays.stream(cookies)
.filter(cookie -> this.tokenNameInCookie.equals(cookie.getName()))
.map(Cookie::getValue)
.findFirst()
.map(this::doXssFilter)
.orElseGet(() -> {
log.error("Access token in cookie does not exist. Request URI: {}", requestURI);
return null;
});
}
public void setTokenToCookie(HttpServletResponse httpServletResponse, String accessToken) {
log.info("Add Token in Cookie.");
Cookie cookie = new Cookie(this.tokenNameInCookie, accessToken);
cookie.setHttpOnly(true);
cookie.setPath("/");
httpServletResponse.addCookie(cookie);
}
public String getUserId(String token) {
return Jwts.parser().verifyWith(this.signingKey)
.build().parseSignedClaims(token).getPayload().getSubject();
}
public String getClaim(String token, String claimName) {
return (String) Jwts.parser().verifyWith(this.signingKey)
.build().parseSignedClaims(token).getPayload().get(claimName);
}
public boolean validateToken(String token) throws ExpiredJwtException {
try {
Jwts.parser().verifyWith(this.signingKey).build().parseSignedClaims(token);
return true;
} catch (io.jsonwebtoken.security.SecurityException | MalformedJwtException e) {
log.error("Invalid jwt signature.", e);
} catch (ExpiredJwtException e) {
log.error("This token is expired.", e);
throw e;
} catch (UnsupportedJwtException e) {
log.error("This jwt token is not supported.", e);
} catch (IllegalArgumentException e) {
log.error("Invalid jwt token.", e);
} catch (DecodingException e) {
log.error("JWT token decoding failed", e);
}
return false;
}
/**
* XSS(Cross-Site Scripting) 공격을 방지하기 위해 특수문자를 HTML 로 변환
*/
private String doXssFilter(String origin) {
if (StringUtils.isEmpty(origin)) {
return null;
}
return origin.replace("'", "'")
.replace("\"", """)
.replace("(", "(")
.replace(")", ")")
.replace("/", "/")
.replace("<", "<")
.replace(">", ">")
.replace("&", "&");
}InitializingBean 을 구현하여 Bean 등록 후 jwtAuthKey를 이용해 SecretKey를 생성합니다. Access Token은 1시간, Refresh Token의 만료시간은 24시간으로 설정합니다.
📍JWT filter 추가
GenericFilterBean을 상속받아 코드를 작성합니다. 이는 Spring Security 가 담당하는 인증과정 전에 처리해야합니다. 만료된 Token 에 대해서는 등록된 사용자인지, 권한이 있는지 체크할 필요가 없기 때문입니다.
로그인, Swagger 관련 주소를 제외한 모든 요청에 대해서 Token 검증을 진행합니다. Cookie 에서 Access Token을 추출해 유효성 검증을 하고 유효하다면 Spring Security에 사용자 인증정보를 저장합니다. Token이 유효사지 않을 경우 클라이언트에게 바로 ErrorResponse를 전달합니다.
config.jwt.JwtFilter
@RequiredArgsConstructor
@Slf4j
public class JwtFilter extends GenericFilterBean {
private final TokenProvider tokenProvider;
private final List<String> ignoreUris = List.of(SecurityConfig.ignoreUris);
@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain)
throws ServletException, IOException {
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
HttpServletResponse httpServletResponse = (HttpServletResponse) response;
String requestURI = httpServletRequest.getRequestURI().replace(this.tokenProvider.contextPath, "");
if (!this.ignoreUris.contains(requestURI)
&& !requestURI.startsWith("/swagger-") && !requestURI.startsWith("/api-docs")) {
log.info("Request URI : " + requestURI);
//1. SessionsCookie 에서 Access Token 추출
String accessToken = tokenProvider.getTokenFromCookie(httpServletRequest);
TokenValidDto tokenValidDto = new TokenValidDto(false, null, accessToken);
//2. Token 유효성 검증
if (StringUtils.isNotEmpty(accessToken)) {
try {
checkTokenValidity(tokenValidDto);
} catch (ExpiredJwtException e) {
// Token 만료 시 바로 Token 만료 메시지 전송
ResponseUtils.sendResponse(httpServletResponse, ErrorCode.EXPIRED_TOKEN);
return;
}
}
//3. Spring Security Authentication token 추가
if (tokenValidDto.isValid()) {
log.info(tokenValidDto.getUserId() + "'s token is valid.");
Collection<SimpleGrantedAuthority> authorities =
Arrays.stream(this.tokenProvider.getClaim(tokenValidDto.getAccessToken()
, this.tokenProvider.authClaimName).split(","))
.map(SimpleGrantedAuthority::new).toList();
Authentication authentication = new UsernamePasswordAuthenticationToken(
new User(this.tokenProvider.getUserId(
tokenValidDto.getAccessToken()), "", authorities),
tokenValidDto.getAccessToken(),
authorities
);
SecurityContextHolder.getContext().setAuthentication(authentication);
}
}
chain.doFilter(request, response);
}
private void checkTokenValidity(TokenValidDto tokenValidDto) {
if (StringUtils.isNotEmpty(tokenValidDto.getAccessToken())
&& tokenProvider.validateToken(tokenValidDto.getAccessToken())) {
String userId = tokenProvider.getUserId(tokenValidDto.getAccessToken());
tokenValidDto.setValid(true);
tokenValidDto.setUserId(userId);
}
}
}common.response.util.ResponseUtils
@Slf4j
public class ResponseUtils {
public static void sendResponse(ServletResponse response, ResponseCode errorCode) {
MessageConfig messageConfig = ApplicationContextHolder.getContext()
.getBean(MessageConfig.class);
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
ObjectMapper objectMapper = new ObjectMapper();
try (PrintWriter writer = response.getWriter()) {
writer.write(objectMapper.writeValueAsString(ErrorResponse.builder()
.status(errorCode.code())
.message(messageConfig.getMessage(errorCode))
.build()));
} catch (IOException e) {
log.error("Fail to send response.");
}
}
}config.jwt.dto.TokenValidDto
@Getter
@Setter
@AllArgsConstructor
public class TokenValidDto {
private boolean valid;
private String userId;
private String accessToken;
}common.response.ErrorResponse
@Builder
public record ErrorResponse(
String status,
String message,
@JsonInclude(JsonInclude.Include.NON_NULL)
String detailMessage
) {
}📍Spring Security Config 설정
JWT 와 Spring Security 를 함께 사용하면 보안성과 확장성 측면에서 장점이 많습니다. 접근 경로에 대한 401 UNAUTHORIZED, 403 FORBIDDEN 설정을 쉽게 할 수 있고 필터를 추가하여 서블릿 이전에 Token의 유효성을 검증할 수도 있습니다.
Spring Security filter 이전에 JwtFilter가 동작하도록 추가하고, 401, 403 처리에 대한 class 를 생성하여 exceptionHandling 설정을 하겠습니다.
🎈JwtAuthenticationEntryPoint
401 UNAUTHORIZED 처리를 위해 AuthenticationEntryPoint의 구현체 JwtAuthenticationEntryPoint 를 작성합니다.
config.jwt.JwtAuthenticationEntryPoint
@Component
@Slf4j
public class JwtAuthenticationEntryPoint implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest request, HttpServletResponse response,
AuthenticationException authException) {
log.error("401 UNAUTHORIZED");
ResponseUtils.sendResponse(response, ErrorCode.NOT_AUTHENTICATION);
}
}🎈JwtAccessDeniedHandler
403 FORBIDDEN 처리를 위해 AccessDeniedHandler의 구현체 JwtAccessDeniedHandler 를 작성합니다.
@Component
@Slf4j
public class JwtAccessDeniedHandler implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest request, HttpServletResponse response,
AccessDeniedException accessDeniedException) {
log.error("403 FORBIDDEN");
ResponseUtils.sendResponse(response, ErrorCode.FORBIDDEN);
}
}📍SecurityConfig
PasswordEncoder 설정에 필요한 정보를 설정파일에 추가합니다. Bcrypt 암호화 방식을 사용하면 간단하지만, 아직 SHA-256 + salt key 에 대한 수요도 많기 때문에 여기서는 SHA-256 + salt key 를 사용하겠습니다.
application.yml
pdkdf2:
key: geonny.log
salt-length: 16
iterations: 256
algorithm: PBKDF2WithHmacSHA256config.SecurityConfig
@Configuration
@EnableWebSecurity
@EnableMethodSecurity
@RequiredArgsConstructor
public class SecurityConfig {
public static final String[] ignoreUris = {"/v1/login"};
private final TokenProvider tokenProvider;
private final MessageConfig messageConfig;
private final JwtAuthenticationEntryPoint jwtAuthenticationEntryPoint;
private final JwtAccessDeniedHandler jwtAccessDeniedHandler;
private final String[] swaggerUris = {"swagger-ui.html", "/swagger-ui/**", "/api-docs/**"};
@Value("${pdkdf2.key}")
private String pdkdf2Key;
@Value("${pdkdf2.salt-length}")
private Integer saltLength;
@Value("${pdkdf2.iterations}")
private Integer iterations;
@Value("${pdkdf2.algorithm}")
private String algorithm;
@Bean
public PasswordEncoder passwordEncoder() {
Map<String, PasswordEncoder> encoders = new HashMap<>();
encoders.put("bcrypt", new BCryptPasswordEncoder());
encoders.put("SHA-256", new Pbkdf2PasswordEncoder(
this.pdkdf2Key, this.saltLength, this.iterations,
Pbkdf2PasswordEncoder.SecretKeyFactoryAlgorithm.valueOf(this.algorithm)));
return new DelegatingPasswordEncoder("SHA-256", encoders);
}
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.csrf(AbstractHttpConfigurer::disable)
.cors(AbstractHttpConfigurer::disable)
.headers(c -> c.frameOptions(HeadersConfigurer.FrameOptionsConfig::disable)
.disable())
.authorizeHttpRequests(auth -> {
auth
.requestMatchers(ignoreUris).permitAll()
.requestMatchers(this.swaggerUris).permitAll()
.anyRequest().authenticated();
})
.exceptionHandling(c ->
c.authenticationEntryPoint(this.jwtAuthenticationEntryPoint)
.accessDeniedHandler(this.jwtAccessDeniedHandler))
.sessionManagement(c -> c.sessionCreationPolicy(SessionCreationPolicy.STATELESS))
.addFilterBefore(new JwtFilter(tokenProvider),
UsernamePasswordAuthenticationFilter.class);
return http.build();
}
}📍Login
🎈LoginController
domain.login.LoginController
@RestController
@RequiredArgsConstructor
@Tag(name = "로그인", description = "로그인 요청")
@RequestMapping("v1")
public class LoginController {
private final LoginService loginService;
private final MessageConfig messageConfig;
@Operation(summary = "로그인 요청", description = """
""", operationId = "API-000-01")
@PostMapping(value = "/login", consumes = MediaType.APPLICATION_JSON_VALUE,
produces = MediaType.APPLICATION_JSON_VALUE)
public ResponseEntity<ItemResponse<TokenResponse>> getMemberById(
@RequestBody @Valid LoginRequest parameter,
HttpServletResponse httpServletResponse) {
return ResponseEntity.ok()
.body(ItemResponse.<TokenResponse>builder()
.status(messageConfig.getCode(NormalCode.SEARCH_SUCCESS))
.message(messageConfig.getMessage(NormalCode.SEARCH_SUCCESS))
.item(loginService.login(httpServletResponse, parameter))
.build());
}
}🎈LoginService
domain.login.LoginService
@Service
@RequiredArgsConstructor
public class LoginService {
private final MemberQueryMethodRepository memberQueryMethodRepository;
private final AuthenticationManagerBuilder authenticationManagerBuilder;
private final TokenProvider tokenProvider;
private final PasswordEncoder passwordEncoder;
@Transactional
public TokenResponse login(
HttpServletResponse httpServletResponse, LoginRequest parameter) {
Member member = this.memberQueryMethodRepository.findById(parameter.memberId())
.orElseThrow(() -> new ServiceException(ErrorCode.NOT_AUTHENTICATION));
if (!this.passwordEncoder.matches(parameter.password(), member.getPassword())) {
throw new ServiceException(ErrorCode.NOT_AUTHENTICATION);
}
UsernamePasswordAuthenticationToken authenticationToken
= new UsernamePasswordAuthenticationToken(parameter.memberId(),
parameter.password());
try {
Authentication authentication =
this.authenticationManagerBuilder.getObject()
.authenticate(authenticationToken);
SecurityContextHolder.getContext()
.setAuthentication(authentication);
TokenResponse tokenResponse = this.tokenProvider
.createToken(authentication, member);
this.tokenProvider.setTokenToCookie(httpServletResponse, t
tokenResponse.accessToken());
return tokenResponse;
} catch (BadCredentialsException e) {
throw new ServiceException(ErrorCode.SERVICE_ERROR);
}
}
}🎈CustomUserDetailService
domain.login.CustomUserDetailService
CustomUserDetailService 는 LoginService 에서 AuthenticationManagerBuilder 에 의해 호출되며 인증정보를 포함한 Security UserDetail 정보를 리턴합니다.
@Service
@RequiredArgsConstructor
@Slf4j
public class CustomUserDetailService implements UserDetailsService {
private final MemberQueryMethodRepository memberQueryMethodRepository;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
return memberQueryMethodRepository.findById(username)
.map(user -> createUser(username, user))
.orElseThrow(() -> new UsernameNotFoundException(username + " -> not found."));
}
private User createUser(String username, Member member) {
if (member.getAuthority() == null) {
throw new ServiceException(ErrorCode.FORBIDDEN);
}
List<GrantedAuthority> grantedAuthorities = new ArrayList<>();
grantedAuthorities.add(new SimpleGrantedAuthority(member.getAuthority()
.getAuthorityCode()));
log.info(username + "'s Authority : {}", grantedAuthorities);
return new User(
member.getMemberId(),
member.getPassword(),
grantedAuthorities
);
}
}🎈추가 변경 사항
common.code.ErrorCode 코드 추가
EXISTS_DATA("ERR_DT_02"),
SQL_ERROR("ERR_SQ_01"),
NOT_AUTHENTICATION("ERR_AT_01"),
FORBIDDEN("ERR_AT_02"),
EXPIRED_TOKEN("ERR_AT_03");resources/messages/message.properties 메시지 추가
EXISTS_DATA=이미 존재는 데이터 입니다.
SQL_ERROR=데이터를 처리하는데 실패하였습니다.
NOT_AUTHENTICATION=자격증명에 실패하였습니다.
FORBIDDEN=접근이 거부되었습니다.
EXPIRED_TOKEN=토근정보가 만료되었습니다.📍결과 확인
이제 Swagger 를 통해 로그인을 해보겠습니다. http://localhost:13713/my-api/swagger-ui/index.html 에 접속하여 로그인 Operation 을 Try it out 합니다.

🎈잘못된 Member 정보 (Id or Password)

🎈올바른 정보
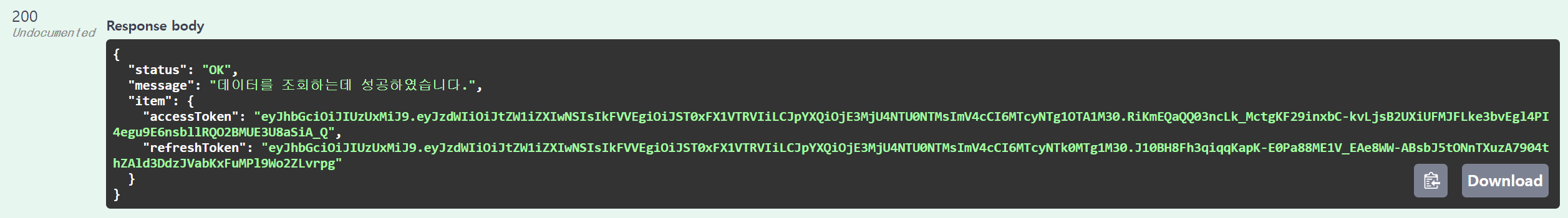
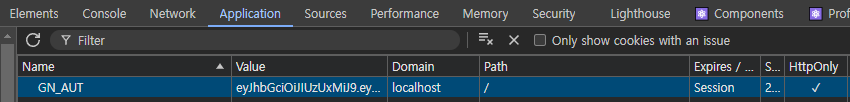
로그인 성공 시 Cookie 확인 (개발자모드 > Application > Cookies > domain주소)
🎈유효하지 않은 토큰 정보

console
This jwt token is not supported.
401 UNAUTHORIZED🎈권한 없음
Controller method 에 @PreAuthorize("hasRole('ADMIN')") 과 같이 추가하면 확인하실 수 있습니다.
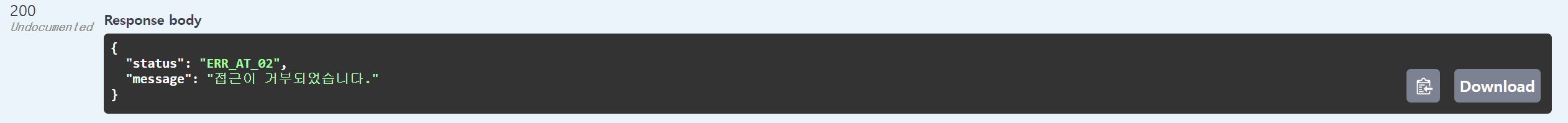
console
403 FORBIDDEN🎈Token 만료
TokenProvider 에 tokenValidityInMilliseconds 를 짧게 설정하면 확인하실 수 있습니다.
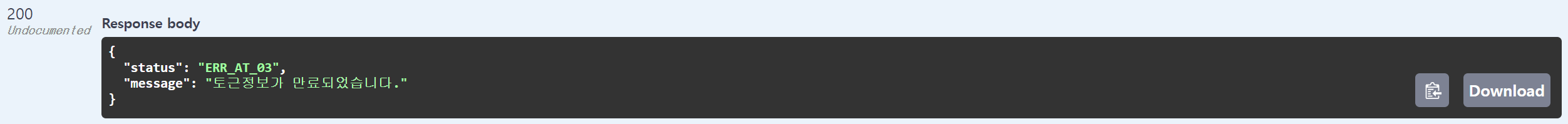
console
This token is expired.
JWT expired 1159987 milliseconds ago at 2024-09-09T06:01:31.000Z.
Current time: 2024-09-09T06:20:50.987Z. Allowed clock skew: 0 milliseconds.📌개선 사항
📍RSA
Example Code 에서는 Front로 부터 password 를 받을 때 암호화에 대해서는 생략되어 있습니다. RSA 를 활용하여 Front 로 RSA Public key 를 전달하고, Front는 password 를 RSA Public key로 암호화 하여 전송, API 서버는 Private Key로 복호화 하여 처리하는 로직을 추가하여 보안을 높일 수 있습니다.
📍Refresh Token
Refresh Token을 활용하여 Access Token 이 만료되었을 때 Front로 만료코드를 전송하고, Front 가 만료 코드를 받으면 Refresh Token 을 서버로 다시 전송하여 Token 을 갱신하는 로직을 추가하면 사용자 편의성과 보안을 높일 수 있습니다.
📌Conclusion
세션 방식보다 Token 방식을 선호하는 이유는 확장성과 경제성 입니다. 서비스가 확장되어도 토큰의 유효성만 검증하면 되고, 서버의 부하가 상대적으로 적기 때문에 하드웨어에 드는 비용도 줄일 수 있을 것 입니다. 최대한 보안적인 조치들을 취함으로써 안전하게 JWT 를 사용할 수 있도록 하는 것이 중요합니다.
📚참고
📕GenericFilterBean
GenericFilterBean은 표준 Filter Interface 와 달리 Spring Bean 으로 관리되므로, 필터의 생명주기가 Spring Context에 의해 관리됩니다. 이로 인해 Spring Container의 시작과 종료에 따라 필터도 자동으로 초기화 및 소멸되며, 추가적인 설정 없이 Spring bean 관리 기능을 활용할 수 있습니다. (Spring Bean DI 가능)
6개의 댓글
아래 sendResponse 함수에서 ApplicationContext의 인스턴스를 생성하지 않고 ApplicationContextHolder를 별도로 구현하여 Context를 받아오는 이유가 무엇인가요?
public static void sendResponse(ServletResponse response, ResponseCode errorCode) {
MessageConfig messageConfig = ApplicationContextHolder.getContext()
.getBean(MessageConfig.class);
// omission...
}


doXssFilter의 origin 두번째 replace("\"", """) 에서 변환하려는 문자는 \ 인가요, " 인가요 🤓❓