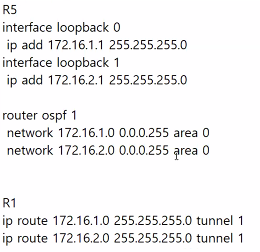
R5에 네트워크가 생긴다면
R5
interface loopback 0
ip add 172.16.1.1 255.255.255.0
interface loopback 1
ip add 172.16.2.1 255.255.255.0
router
이렇게 해야한다.
터널을 생성한다면
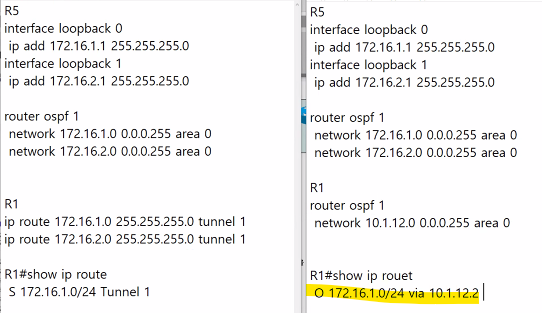
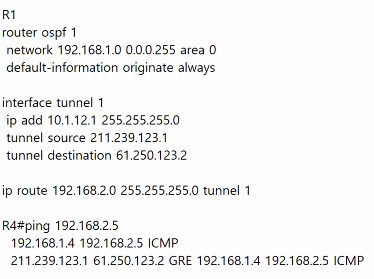
static root를 생성할 필요가 없다. -> 노란색 줄
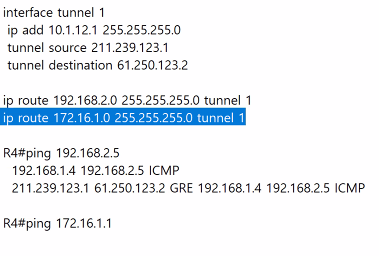
static으로 설정해주어야 터널을 통해서 지사로 간다. -> 파란색 줄
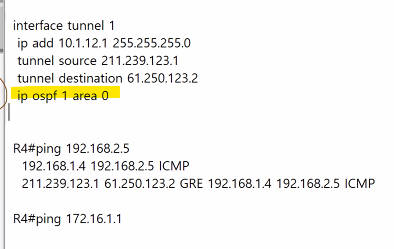
터널을 통해서 neighbor가 맺어지고 터널을 통해서 지사와 맺음 -> GRE를 쓰는 이유.
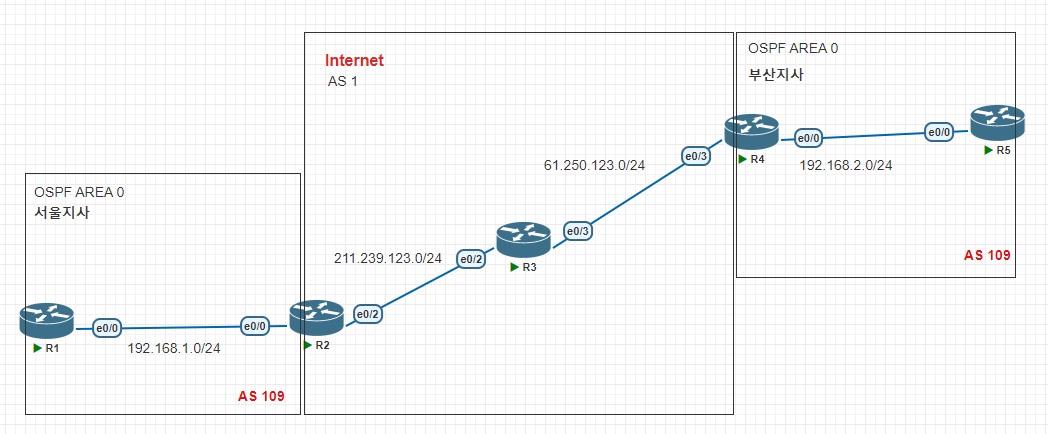
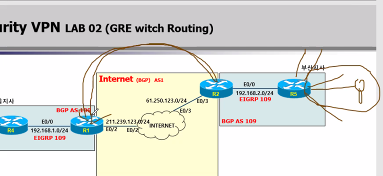
LAB (GRE MultiSite)
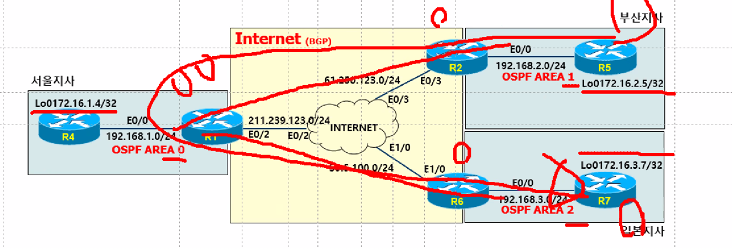
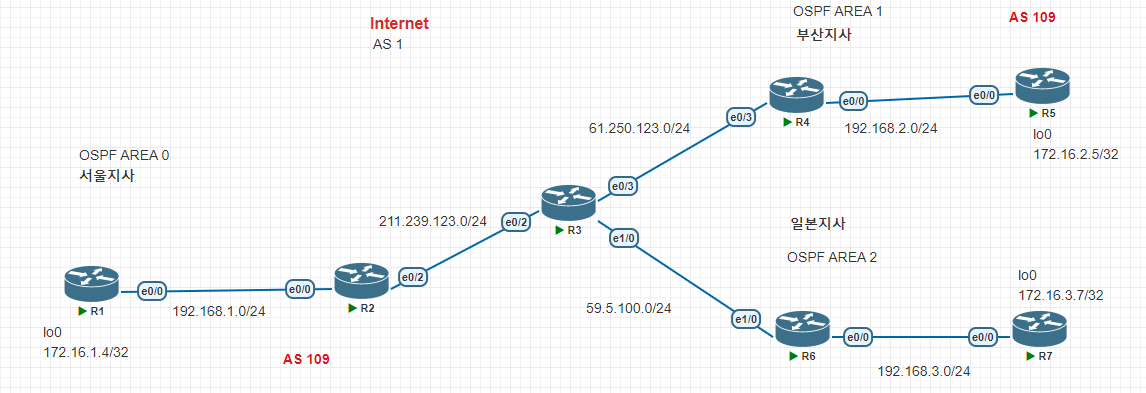
문제1. R3(E1/0), R6(E1/0)에 각각 공인 IP를 설정하고, BGP를 구성하여, 인터넷 환경을 추가 구성합니다.
공인 IP
R6
int e1/0
ip add 59.5.100.6 255.255.255.0
no sh
BGP구성
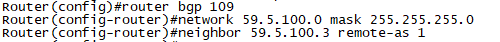
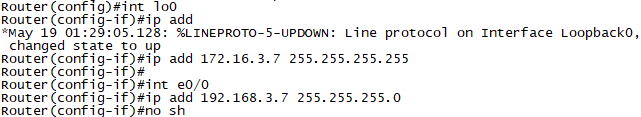
문제2. R6, R7간에 일본지사 OSPF Area 2을 구성합니다.
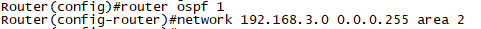
R7에 172.16.3.7/32 Network을 추가합니다.
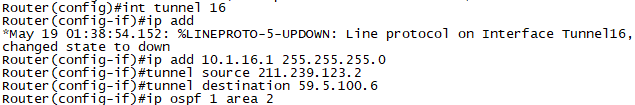
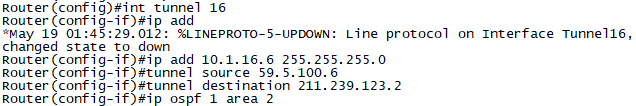
문제3. R2,R6간에 GRE Tunnel을 구성하고, Tunnel에 Routing OSPF를 구성합니다.
R2
interface tunnel 16
ip add 10.1.16.1 255.255.255.0
tunnel source 211.239.123.1
tunnel destination 59.5.100.6
ip ospf 1 area 2
R2
R6
문제4. R2,R4에 구성된 GRE Tunnel에 대한 STATIC Route를 삭제하고, Routing OSPF를 구성합니다.
어제 설정한 STATIC Route를 삭제하고, OSPF를 구성합니다.
STATIC Route 삭제
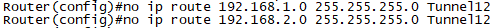
TEST를 위하여, R4,R5에 각각 Loopback0를 생성하고 OSPF에 포함합니다.
loopback 추가
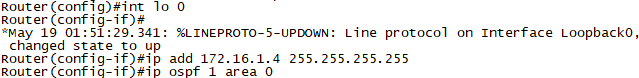
Routing OSPF 구성
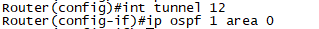
확인1. R2#show ip interface brief로 tunnel interface의 상태를 확인 합니다.
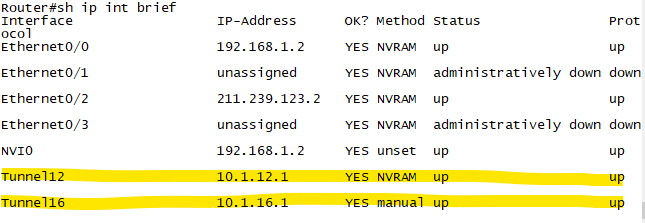
확인2. R2에서 show ip ospf neighbor "Tunnel로 neighbor가 성립된것을 확인합니다."
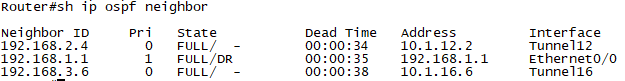
확인3. R2에서 show ip route ospf로 지사의 경로가 tunnel routing이 선택된것을 확인합니다.
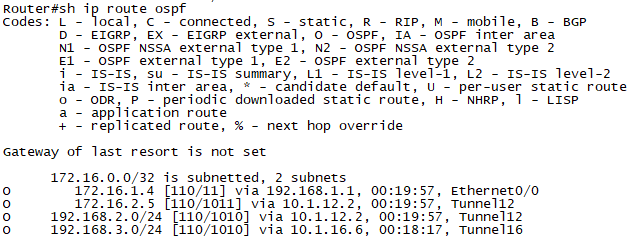
확인4. R1에서 show ip rouite ospf로 자신의 경로를 또한 확인합니다.
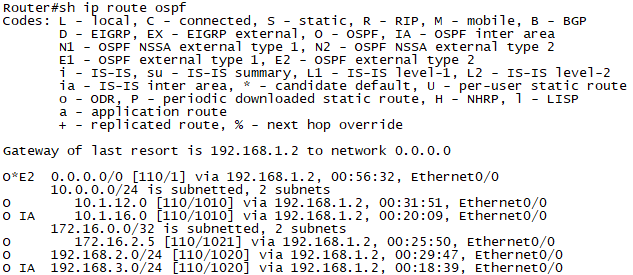
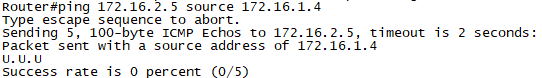
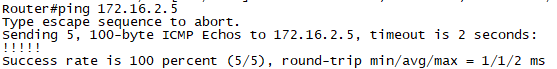
확인5. R1에서 ping 172.16.2.5로 통신을 확인합니다.
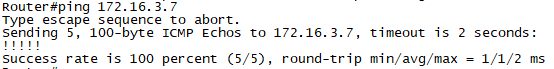
확인6. R1에서 ping 172.16.3.7로 통신을 확인합니다.
확인7. R7에서 traceroute 172.16.2.5로 경로를 확인합니다.
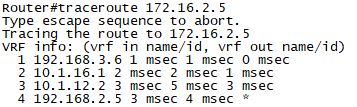
확인8. R2,R3간을 Capture하여, GRE Packet을 확인합니다.
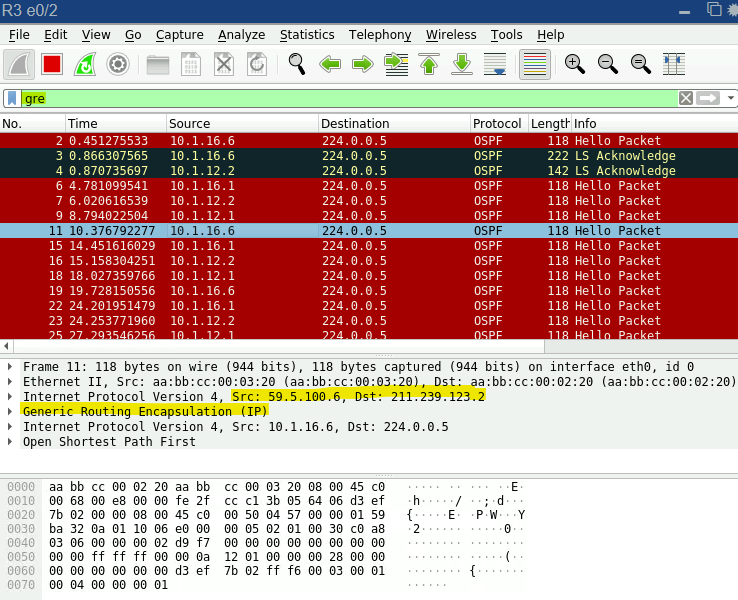
R1(IPSec으로 하는 경우)
STEP1. IPSec Tunnel
crypto isakmp key cisco address 61.250.123.4
-> 61.250.123.2와 IPSec 협상을 시작하세요. (단 Password : cisco를 확인)
-> Peer 인증
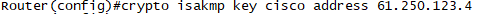
STEP2. Phase1 협상
- IPSec 협상(Phase2)을 해야하는데, 안전하게 하기 위해 미리 협상을 한다.
- isakmp (IKE)
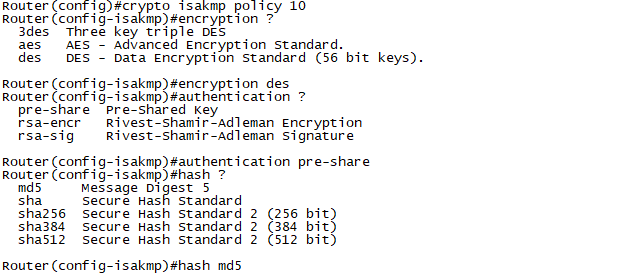
config)#crypto isakmp policy 10
config)#encryption ? (des)
config)#authentication ? (pre-share)
config)#hash ? (md5)
#show crypto isakmp sa
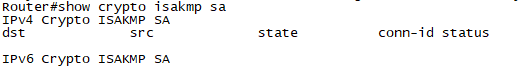
STEP3. Phase2 협상
- 실제 IPSec을 어떻게 만들지 결정하는 협상(SA)
- Phase1을 바탕으로 안전하게 진행된다.
config)#crypto ipsec transform-set MYSET esp-3des
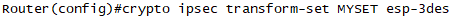
STEP4. IPSec으로 만들 DATA의 정의 -> Interesting Packet
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
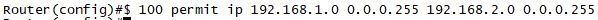
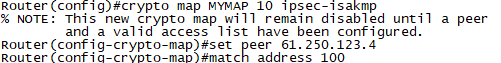
STEP5. 설정한 IPSec을 MAP으로 통합
- GRE는 Tunnel interface를 만들지만,
- IPSec은 MAP을 만들어, 물리적인 interface에 적용합니다.
crypto map MYMAP 10 ipsec-isakmp
set peer 61.250.123.2
set transform-set MYSET
match address 100
STEP6. 설정한 MAC은 Interface에 적용
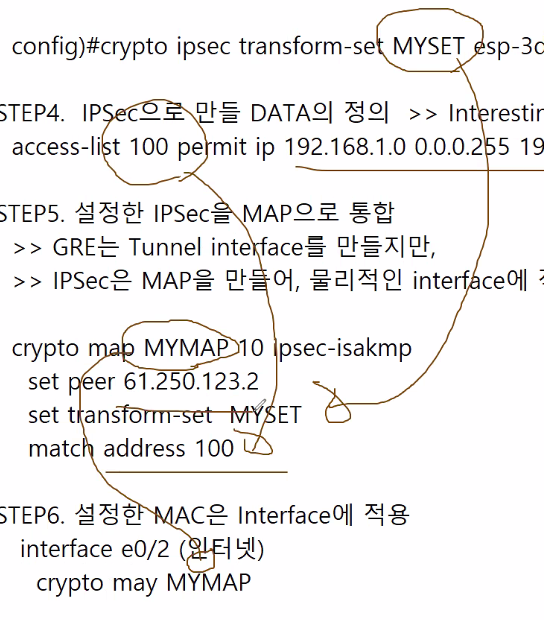
interface e0/2 (인터넷)
crypto map MYMAP
TEST
- 서울지사와 부산지사 간 GRE를 IPSec Tunnel로 변경한다.
R2 shutdown
R4 shutdown
R6 shutdown
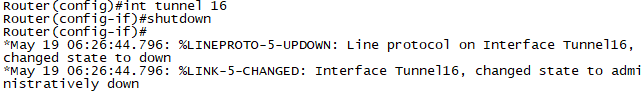
문제1. R2에 IPSec VPN설정을 적용합니다.
-
메모장에 있는 STEP1~STEP6까지의 설정을 적용합니다.
-
지사간 Routing이 없기 때문에, Static Route를 적용합니다.
R2(config)#ip route 192.168.2.0 255.255.255.0 211.239.123.3
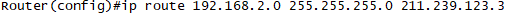
-
지사간 통신의 경우, NAT에서 제외합니다.
R2(config)#no ip nat inside source list 1 interface e0/2 overload
R2(config)#ip nat inside source list 101 itnerface e0/2 overload

R2(config)#access-list 101 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
R2(config)#access-list 101 permit ip any any
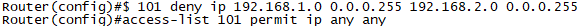
Phase1에 대한 정책은 아래와 같이 설정합니다.
Encryption algorithm = 3DES
integrity algorithm = MD5
Authentication alogirthm = Pre-shared Key
Phase2에 대한 정책은 아래와 같이 설정합니다.
IPSec Protocol = ESP
Encryption algorithm = 3DES
integrity algorithm = sha
IPSec Configuration
R1
crypto isakmp key cisco address 61.250.123.2
crypto isakmp policy 10
encryption des
authentication pre-shar
hash md5
crypto ipsec transform-set MYSET esp-3des esp-sha-hmac
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
crypto map MYMAP 10 ipsec-isakmp
set peer 61.250.123.2
set transform-set MYSET
match address 100
interface e0/2
crypto map MYMAP
ip route 192.168.2.0 255.255.255.0 211.239.123.3
R2
crypto isakmp key cisco address 211.239.123.1
crypto isakmp policy 10
encryption des
authentication pre-shar
hash md5
crypto ipsec transform-set MYSET esp-3des esp-sha-hmac
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
crypto map MYMAP 10 ipsec-isakmp
set peer 211.239.123.1
set transform-set MYSET
match address 100
interface e0/3
crypto map MYMAP
ip route 192.168.1.0 255.255.255.0 61.250.123.3
확인1. R1에서 ping 192.168.2.5 (R5)로 통신이 되는것을 확인합니다.
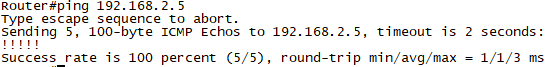
확인2. R2에서 show crypto isakmp sa로 Phase1에 대한 SA가 성립이 된것을 확인 합니다. "Active 확인"
Seoul#show crypto isakmp sa
dst src state conn-id status
61.250.123.2 211.239.123.1 QM_IDLE 1001 ACTIVE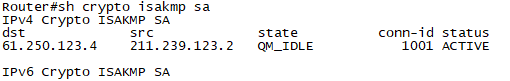
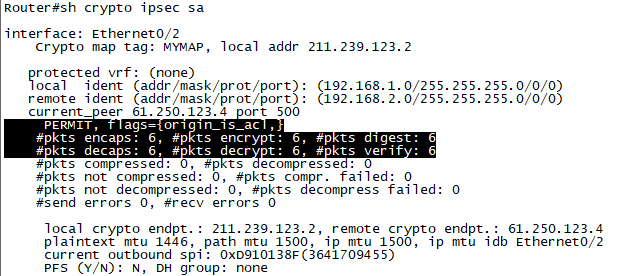
확인3. R2에서 show crypto ipsec sa로 Phase2에 대한 SA가 성립이 된것을 확인 합니다.
current_peer 61.250.123.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9 >>>> couter 증가 확인
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
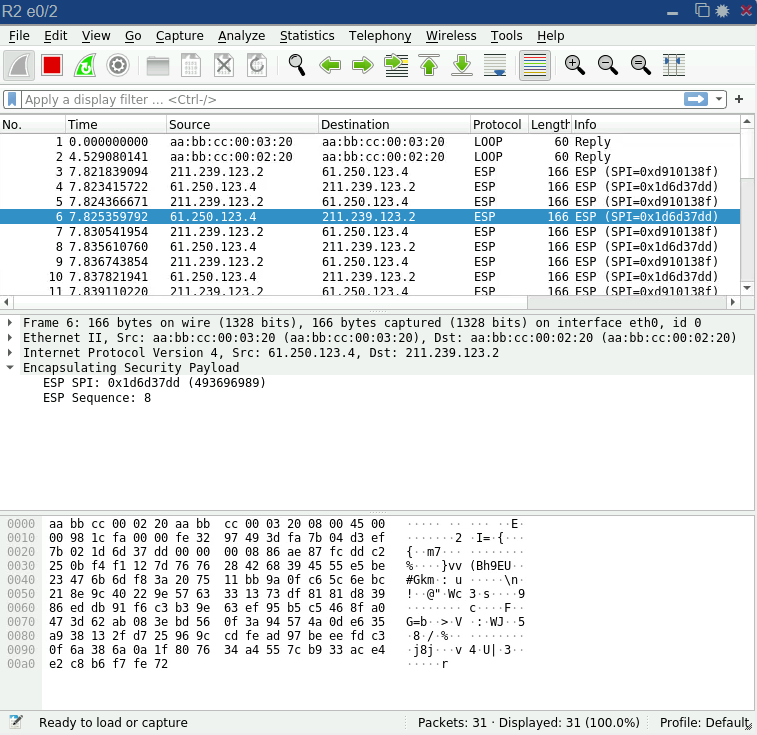
확인4. R2,R3구간 E0/2을 Wireshark로 Capture하면, ICMP는 보이지 않음, ESP만 보임 !!!
도전과제
1. R1에서 ping 172.16.2.5로 통신이 되도록 설정한다.
R3(ISP에서 Default Route를 전파해줌)

R2(R1에서 R5의 Loopback으로 가는 Traffic을 정의)
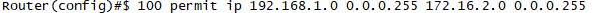
R4
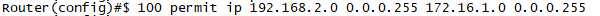
clear crypto isakmp
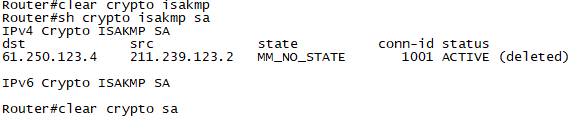
access-list 설정
R2
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 100 permit ip 192.168.1.0 0.0.0.255 172.16.2.0 0.0.0.255
access-list 101 deny ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 101 deny ip 192.168.1.0 0.0.0.255 172.16.2.0. 0.0.0.255
access-list 101 permit ip any any
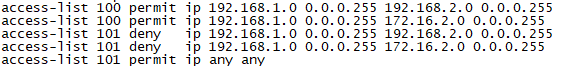
R4
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.2.0 0.0.0.255
access-list 100 permit ip 172.16.2.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 101 deny ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 101 deny ip 172.16.2.0 0.0.0.255 192.168.1.0. 0.0.0.255
access-list 101 permit ip any any
확인1. R1#ping 192.168.2.5
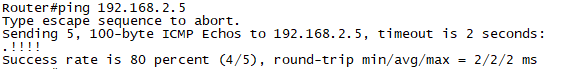
확인2. R1#ping 172.168.2.5
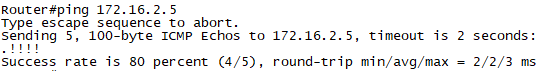
확인3. R1#ping 172.16.2.5 source 172.16.1.4 -> 통신안됨