Terrform 실습 - ASG, RDS, NATGW, Route53
variables.tf
variable "instance_security_group_name" {
description = "The name of the security group for the EC2 Instances"
type = string
default = "terraform-example-instance"
}
variable "http_port" {
description = "The port the server will use for HTTP requests"
type = number
default = 80
}
variable "ssh_port" {
description = "The port the server will use for SSH requests"
type = number
default = 22
}
variable "alb_name" {
description = "The name of the ALB"
type = string
default = "terraform-asg-example"
}
variable "rds_name" {
description = "The SG name of the RDS"
type = string
default = "test-sg-alb"
}
variable "alb_security_group_name" {
description = "The name of the security group for the ALB"
type = string
default = "terraform-example-alb"
}
variable "route53_zone_id" {
description = "The zone id of route53 "
type = string
default = "Z06535841T3IN9MV0MLS0"
}
main.tf
- Resource: aws_db_subnet_group
- Resource: aws_db_instance
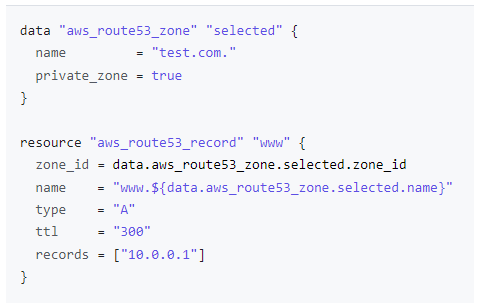
- Resource: aws_route53_record
- Data Source: aws_route53_zone
zone_id와name둘중 하나만 사용한다.
provider "aws" {
region = "ap-northeast-2"
}
### vpc ###
resource "aws_vpc" "test_vpc" {
cidr_block = "192.168.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
tags = {
Name = "test-vpc"
}
}
data "aws_availability_zones" "available" {
state = "available"
}
resource "aws_subnet" "test-pub_2a" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.0.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "test-pub-2a"
}
}
resource "aws_subnet" "test-pub_2b" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.16.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "test-pub-2b"
}
}
resource "aws_subnet" "test-pub_2c" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.32.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "test-pub-2c"
}
}
resource "aws_subnet" "test-pub_2d" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.48.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "test-pub-2d"
}
}
resource "aws_subnet" "test-pvt_2a" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.64.0/20"
map_public_ip_on_launch = false
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "test-pvt-2a"
}
}
resource "aws_subnet" "test-pvt_2b" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.80.0/20"
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "test-pvt-2b"
}
}
resource "aws_subnet" "test-pvt_2c" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.96.0/20"
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "test-pvt-2c"
}
}
resource "aws_subnet" "test-pvt_2d" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.112.0/20"
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "test-pvt-2d"
}
}
resource "aws_internet_gateway" "test_igw" {
vpc_id = aws_vpc.test_vpc.id
tags = {
Name = "test-igw"
}
}
resource "aws_eip" "ngw" {}
resource "aws_nat_gateway" "test_ngw" {
allocation_id = aws_eip.ngw.id
subnet_id = aws_subnet.test-pub_2a.id # 반드시 퍼블릭 서브넷
tags = {
Name = "test-ngw"
}
}
resource "aws_route_table" "test_pub_rtb" {
vpc_id = aws_vpc.test_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.test_igw.id
}
tags = {
Name = "test-pub-rtb"
}
}
resource "aws_route_table" "test_pvt_rtb" {
vpc_id = aws_vpc.test_vpc.id
route {
cidr_block = "0.0.0.0/0"
nat_gateway_id = aws_nat_gateway.test_ngw.id
}
tags = {
Name = "test-pvt-rtb"
}
}
resource "aws_route_table_association" "test-pub_2a_association" {
subnet_id = aws_subnet.test-pub_2a.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2b_association" {
subnet_id = aws_subnet.test-pub_2b.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2c_association" {
subnet_id = aws_subnet.test-pub_2c.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2d_association" {
subnet_id = aws_subnet.test-pub_2d.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pvt_2a_association" {
subnet_id = aws_subnet.test-pvt_2a.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2b_association" {
subnet_id = aws_subnet.test-pvt_2b.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2c_association" {
subnet_id = aws_subnet.test-pvt_2c.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2d_association" {
subnet_id = aws_subnet.test-pvt_2d.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
### vpc end ###
### bastion host ###
resource "aws_instance" "test_bastion" {
ami = "ami-035da6a0773842f64"
instance_type = "t2.micro"
subnet_id = aws_subnet.test-pub_2a.id
vpc_security_group_ids = [aws_security_group.instance.id]
key_name = "test-key"
user_data = file("bastion-data.sh")
tags = {
Name = "terraform-test-bastion"
}
}
### bastion host end ###
### asg ###
resource "aws_security_group" "instance" {
name = var.instance_security_group_name
vpc_id = aws_vpc.test_vpc.id
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_launch_configuration" "example" {
# image_id = "ami-035da6a0773842f64"
image_id = "ami-0ca1dec1938f393f7"
instance_type = "t2.micro"
security_groups = [aws_security_group.instance.id]
key_name = "test-key"
# user_data = file("user-data.sh")
# Required when using a launch configuration with an auto scaling group.
lifecycle {
create_before_destroy = true
}
}
resource "aws_autoscaling_group" "example" {
launch_configuration = aws_launch_configuration.example.name
vpc_zone_identifier = [
aws_subnet.test-pvt_2a.id,
aws_subnet.test-pvt_2c.id
]
target_group_arns = [aws_lb_target_group.asg.arn]
health_check_type = "ELB"
min_size = 2
desired_capacity = 2
max_size = 4
tag {
key = "Name"
value = "terraform-asg-example"
propagate_at_launch = true
}
}
resource "aws_lb" "example" {
name = var.alb_name
load_balancer_type = "application"
subnets = [
aws_subnet.test-pub_2a.id,
aws_subnet.test-pub_2b.id,
aws_subnet.test-pub_2c.id,
aws_subnet.test-pub_2d.id
]
security_groups = [aws_security_group.alb.id]
}
resource "aws_lb_listener" "http" {
load_balancer_arn = aws_lb.example.arn
port = var.http_port
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.asg.arn
}
}
resource "aws_lb_target_group" "asg" {
name = var.alb_name
port = var.http_port
protocol = "HTTP"
vpc_id = aws_vpc.test_vpc.id
health_check {
path = "/health/"
protocol = "HTTP"
matcher = "200"
interval = 15
timeout = 3
healthy_threshold = 2
unhealthy_threshold = 2
}
}
resource "aws_security_group" "alb" {
vpc_id = aws_vpc.test_vpc.id
name = var.alb_security_group_name
# Allow inbound HTTP requests
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
# Allow all outbound requests
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_autoscaling_policy" "scale_in" {
name = "ScaleInPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = -1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_in" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_in.arn]
alarm_name = "ScaleInAlarm"
comparison_operator = "LessThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "30"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}
resource "aws_autoscaling_policy" "scale_out" {
name = "ScaleOutPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = 1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_out" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_out.arn]
alarm_name = "ScaleOutAlarm"
comparison_operator = "GreaterThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "70"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}
### rds ###
resource "aws_db_subnet_group" "test_rds_subnet" {
name = "main"
subnet_ids = [
aws_subnet.test-pvt_2a.id,
aws_subnet.test-pvt_2c.id,
]
tags = {
Name = "test-rds-subnet"
}
}
resource "aws_security_group" "test_sg_rds" {
name = var.rds_name
vpc_id = aws_vpc.test_vpc.id
ingress {
from_port = 3306
to_port = 3306
protocol = "tcp"
cidr_blocks = ["192.168.0.0/16"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_db_instance" "test_rds" {
allocated_storage = 20 # 데이터베이스 스토리지 크기
db_name = "wordpress"
engine = "mysql"
engine_version = "5.7"
instance_class = "db.t2.micro"
username = "jsb"
password = "Kosa0220!"
parameter_group_name = "default.mysql5.7"
skip_final_snapshot = true
db_subnet_group_name = aws_db_subnet_group.test_rds_subnet.name
vpc_security_group_ids = [aws_security_group.test_sg_rds.id]
}
### rds end ###
### route53 ###
data "aws_route53_zone" "goorm" {
zone_id = var.route53_zone_id
#name = "goorm.shop."
#private_zone = true
}
resource "aws_route53_record" "blog" {
zone_id = data.aws_route53_zone.goorm.zone_id
name = "blog.${data.aws_route53_zone.goorm.name}"
type = "A"
alias {
name = aws_lb.example.dns_name
zone_id = aws_lb.example.zone_id
evaluate_target_health = true
}
}
### route53 end ###outputs.tf
output "alb_dns_name" {
value = aws_lb.example.dns_name
description = "The domain name of the load balancer"
}
output "rds_endpoint" {
value = aws_db_instance.test_rds.endpoint
description = "The domain name of the rds"
}
output "route53_recode_name" {
value = aws_route53_record.blog.name
description = "The domain name of the route53 record"
}
user-data.sh
#!/bin/bash
amazon-linux-extras install -y php7.4
yum install -y httpd php-gd wget unzip mysql
cd /tmp
wget https://ko.wordpress.org/latest-ko_KR.zip
cd /var/www/html
unzip /tmp/latest-ko_KR.zip
mv ./wordpress/* .
chown -R apache:apache /var/www/*
systemctl enable --now httpd
mkdir /var/www/html/health
echo "<h1>health ok</h1>" > /var/www/html/health/index.htmlbastion-data.sh
#!/bin/bash
cd /tmp
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install결과
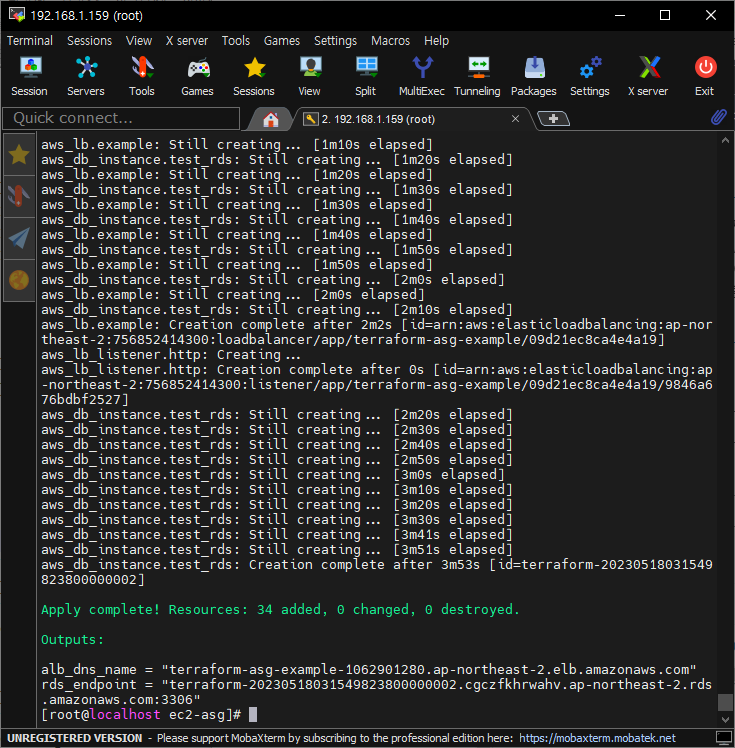
인스턴스 과부하
# bastion host에 파일 복사
scp -i test-key.pem test-key.pem ec2-user@3.34.135.114:/home/ec2-user
# 과부하
sudo yes > /dev/null &
# 과부하 프로세스 제거
sudo pkill -9 yesASG Route53 ALB HTTPS
variables.tf
variable "instance_security_group_name" {
description = "The name of the security group for the EC2 Instances"
type = string
default = "terraform-example-instance"
}
variable "http_port" {
description = "The port the server will use for HTTP requests"
type = number
default = 80
}
variable "https_port" {
description = "The port the server will use for HTTP requests"
type = number
default = 443
}
variable "ssh_port" {
description = "The port the server will use for SSH requests"
type = number
default = 22
}
variable "alb_name" {
description = "The name of the ALB"
type = string
default = "terraform-asg-example"
}
variable "alb_security_group_name" {
description = "The name of the security group for the ALB"
type = string
default = "terraform-example-alb"
}
variable "route53_zone_id" {
description = "The zone id of route53 "
type = string
default = "Z06535841T3IN9MV0MLS0"
}
variable "alb_ssl_policy" {
description = "The policy of elb security policy "
type = string
default = "ELBSecurityPolicy-TLS13-1-2-2021-06"
}
variable "alb_certificate_arn" {
description = "The arn of aws certificate manager"
type = string
default = "arn:aws:acm:ap-northeast-2:756852414300:certificate/472ed6b1-36bc-470a-9cfa-ece48dfc581a"
}main.tf
provider "aws" {
region = "ap-northeast-2"
}
### certificate ###
data "aws_acm_certificate" "issued" {
domain = "*.goorm.shop"
statuses = ["ISSUED"]
}
### certificate end ###
### vpc ###
resource "aws_vpc" "test_vpc" {
cidr_block = "192.168.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
tags = {
Name = "test-vpc"
}
}
data "aws_availability_zones" "available" {
state = "available"
}
resource "aws_subnet" "test-pub_2a" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.0.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "test-pub-2a"
}
}
resource "aws_subnet" "test-pub_2b" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.16.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "test-pub-2b"
}
}
resource "aws_subnet" "test-pub_2c" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.32.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "test-pub-2c"
}
}
resource "aws_subnet" "test-pub_2d" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.48.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "test-pub-2d"
}
}
resource "aws_subnet" "test-pvt_2a" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.64.0/20"
map_public_ip_on_launch = false
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "test-pvt-2a"
}
}
resource "aws_subnet" "test-pvt_2b" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.80.0/20"
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "test-pvt-2b"
}
}
resource "aws_subnet" "test-pvt_2c" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.96.0/20"
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "test-pvt-2c"
}
}
resource "aws_subnet" "test-pvt_2d" {
vpc_id = aws_vpc.test_vpc.id
cidr_block = "192.168.112.0/20"
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "test-pvt-2d"
}
}
resource "aws_internet_gateway" "test_igw" {
vpc_id = aws_vpc.test_vpc.id
tags = {
Name = "test-igw"
}
}
resource "aws_route_table" "test_pub_rtb" {
vpc_id = aws_vpc.test_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.test_igw.id
}
tags = {
Name = "test-pub-rtb"
}
}
resource "aws_route_table" "test_pvt_rtb" {
vpc_id = aws_vpc.test_vpc.id
tags = {
Name = "test-pvt-rtb"
}
}
resource "aws_route_table_association" "test-pub_2a_association" {
subnet_id = aws_subnet.test-pub_2a.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2b_association" {
subnet_id = aws_subnet.test-pub_2b.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2c_association" {
subnet_id = aws_subnet.test-pub_2c.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pub_2d_association" {
subnet_id = aws_subnet.test-pub_2d.id
route_table_id = aws_route_table.test_pub_rtb.id
}
resource "aws_route_table_association" "test-pvt_2a_association" {
subnet_id = aws_subnet.test-pvt_2a.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2b_association" {
subnet_id = aws_subnet.test-pvt_2b.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2c_association" {
subnet_id = aws_subnet.test-pvt_2c.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
resource "aws_route_table_association" "test-pvt_2d_association" {
subnet_id = aws_subnet.test-pvt_2d.id
route_table_id = aws_route_table.test_pvt_rtb.id
}
### vpc end ###
### bastion host ###
resource "aws_instance" "test_bastion" {
ami = "ami-035da6a0773842f64"
instance_type = "t2.micro"
subnet_id = aws_subnet.test-pub_2a.id
vpc_security_group_ids = [aws_security_group.instance.id]
key_name = "test-key"
user_data = file("bastion-data.sh")
tags = {
Name = "terraform-test-bastion"
}
}
### bastion host end ###
### asg ###
resource "aws_security_group" "instance" {
name = var.instance_security_group_name
vpc_id = aws_vpc.test_vpc.id
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = var.https_port
to_port = var.https_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_launch_configuration" "example" {
# image_id = "ami-035da6a0773842f64"
image_id = "ami-0ca1dec1938f393f7"
instance_type = "t2.micro"
security_groups = [aws_security_group.instance.id]
key_name = "test-key"
# user_data = file("user-data.sh")
# Required when using a launch configuration with an auto scaling group.
lifecycle {
create_before_destroy = true
}
}
resource "aws_autoscaling_group" "example" {
launch_configuration = aws_launch_configuration.example.name
vpc_zone_identifier = [
aws_subnet.test-pvt_2a.id,
aws_subnet.test-pvt_2c.id
]
target_group_arns = [aws_lb_target_group.asg.arn]
health_check_type = "ELB"
min_size = 2
desired_capacity = 2
max_size = 4
tag {
key = "Name"
value = "terraform-asg-example"
propagate_at_launch = true
}
}
resource "aws_lb" "example" {
name = var.alb_name
load_balancer_type = "application"
subnets = [
aws_subnet.test-pub_2a.id,
aws_subnet.test-pub_2b.id,
aws_subnet.test-pub_2c.id,
aws_subnet.test-pub_2d.id
]
security_groups = [aws_security_group.alb.id]
}
resource "aws_lb_listener" "http" {
load_balancer_arn = aws_lb.example.arn
port = var.http_port
protocol = "HTTP"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.asg.arn
}
}
### SSL Listener ###
resource "aws_lb_listener" "https" {
load_balancer_arn = aws_lb.example.arn
port = var.https_port
protocol = "HTTPS"
ssl_policy = var.alb_ssl_policy
certificate_arn = var.alb_certificate_arn
#ssl_policy = "ELBSecurityPolicy-TLS13-1-2-2021-06"
#certificate_arn = "arn:aws:acm:ap-northeast-2:756852414300:certificate/472ed6b1-36bc-470a-9cfa-ece48dfc581a"
default_action {
type = "forward"
target_group_arn = aws_lb_target_group.asg.arn
}
}
### SSL Listener end ###
resource "aws_lb_target_group" "asg" {
name = var.alb_name
port = var.http_port
protocol = "HTTP"
vpc_id = aws_vpc.test_vpc.id
health_check {
path = "/health/"
protocol = "HTTP"
matcher = "200"
interval = 15
timeout = 3
healthy_threshold = 2
unhealthy_threshold = 2
}
}
resource "aws_security_group" "alb" {
vpc_id = aws_vpc.test_vpc.id
name = var.alb_security_group_name
# Allow inbound HTTP requests
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
# Allow inbound HTTPS requests
ingress {
from_port = var.https_port
to_port = var.https_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
# Allow all outbound requests
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_autoscaling_policy" "scale_in" {
name = "ScaleInPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = -1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_in" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_in.arn]
alarm_name = "ScaleInAlarm"
comparison_operator = "LessThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "30"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}
resource "aws_autoscaling_policy" "scale_out" {
name = "ScaleOutPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = 1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_out" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_out.arn]
alarm_name = "ScaleOutAlarm"
comparison_operator = "GreaterThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "70"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}
### route53 ###
data "aws_route53_zone" "goorm" {
zone_id = var.route53_zone_id
#name = "goorm.shop."
#private_zone = true
}
resource "aws_route53_record" "blog" {
zone_id = data.aws_route53_zone.goorm.zone_id
name = "blog.${data.aws_route53_zone.goorm.name}"
type = "A"
alias {
name = aws_lb.example.dns_name
zone_id = aws_lb.example.zone_id
evaluate_target_health = true
}
}
### route53 end ###outputs.tf
output "alb_dns_name" {
value = aws_lb.example.dns_name
description = "The domain name of the load balancer"
}
output "route53_recode_name" {
value = aws_route53_record.blog.name
description = "The record name of the route53 record"
}
output "acm_arn" {
value = data.aws_acm_certificate.issued.arn
description = "The arn of the aws certificate manager"
}
output "acm_certificate" {
value = data.aws_acm_certificate.issued.certificate
description = "The certificate of the aws certificate manager"
}참고
depends_on
