Prerequisites
install Kubernetes v1.21.5
Set a default Storage Class before install kubeflow
install Kubeflow v1.4.0
Understanding Structure of kubeflow
https://github.com/kubeflow/manifests/tree/v1.4.0/common/oidc-authservice/base
There are 3 main directories in kubeflow(apps/common/contrib)
There are fundamental code in apps (Not including Authentication)
and if you want to use keycloak with dex, you should change the code of contrib.
So if you want to use keycloak as OIDC provider NOT USING DEX.
Then we should change the code of common directory.
We don't have to change the "apps" or "contrib". Even the "dex".
There is the dex dir in common dir. But kubeflow doesn't use itself on authentication.
Kubeflow use dex as oidc provider through oidc-authservice.
So got to change the code of oidc-authservice dir.
change the code to keycloak
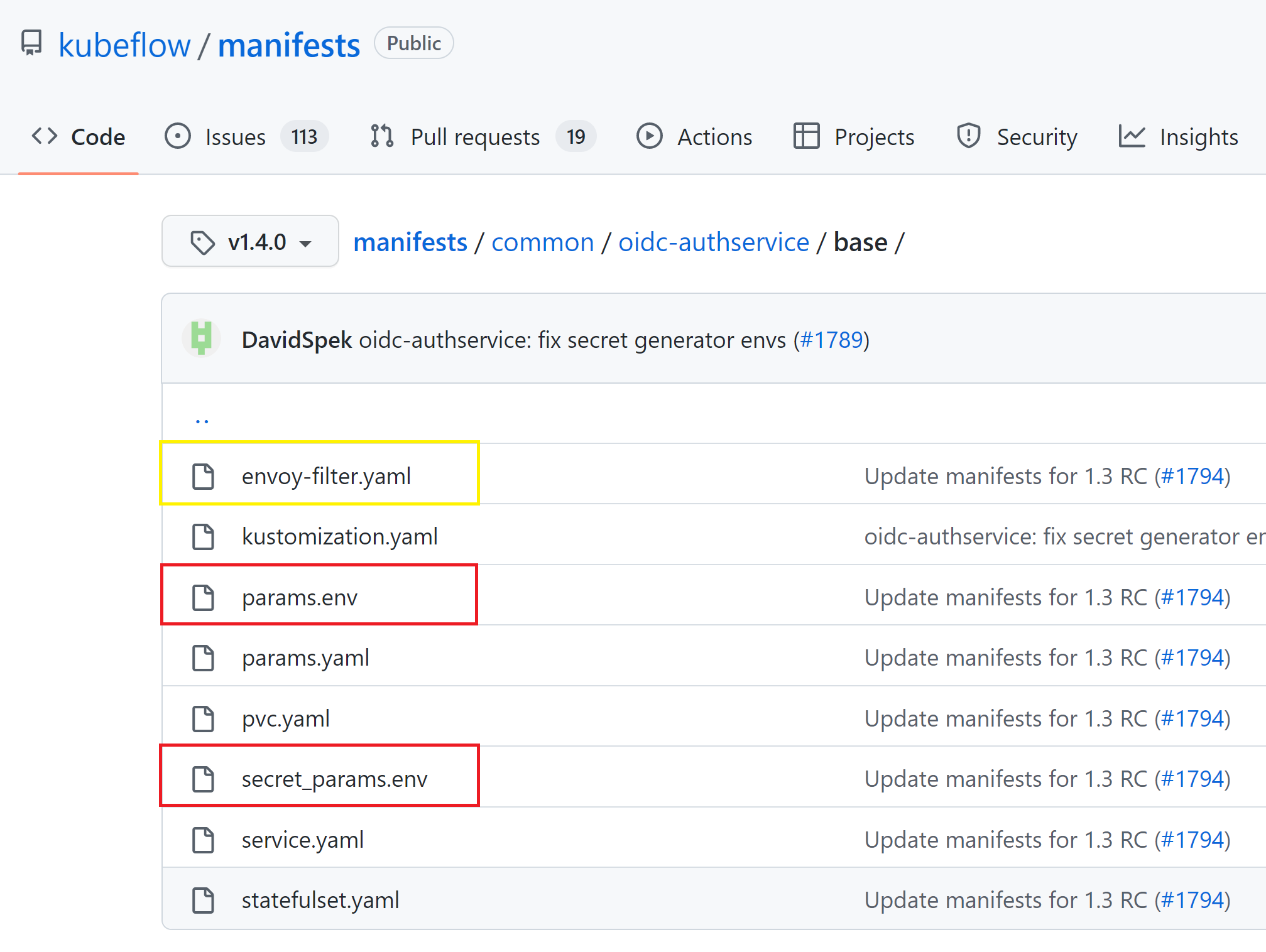
1. change the code of params.env (on kubeflow)
cd manifests/common/oidc-authservice/base/
vi param.env
This is the code about dex (which is default auth. on kubeflow)
OIDC_PROVIDER=http://dex.auth.svc.cluster.local:5556/dex //dex IdP issuer url
OIDC_AUTH_URL=/dex/auth // dex auth url
OIDC_SCOPES=profile email groups
AUTHSERVICE_URL_PREFIX=/authservice/
SKIP_AUTH_URLS=/dex
USERID_HEADER=kubeflow-userid
USERID_PREFIX=
USERID_CLAIM=email
PORT="8080"
STORE_PATH=/var/lib/authservice/data.db
Change the code to use keycloak as OIDC provider
OIDC_PROVIDER=http://{keycloak_server}:{keycloak-port}/realms/{my_realm} //keycloak issuer URL
OIDC_AUTH_URL=http://{keycloak_server}:{keycloak-port}/realms/{my_realm}/protocol/openid-connect/auth // keycloak authorization_endpoint
OIDC_SCOPES=profile email groups // Gotta match to keycloak setting
REDIRECT_URL=http://{kubeflow_server}:{kubeflow-port}/login/oidc
SKIP_AUTH_URI=/keycloak
USERID_HEADER=kubeflow-userid
USERID_PREFIX=
USERID_CLAIM=email
PORT="8080"
STORE_PATH=/var/lib/authservice/data.db
You can figure out the kubeflow port from istio-ingressgateway in namespace istio-system
Make sure that the type = NodePort
Port(s) with 80:{your kubeflow port number}/TCP
2. change the code of secret-params.env (on kubeflow)
cd manifests/common/oidc-authservice/base/
vi secret_param.env
CLIENT_ID=kubeflow (your client id from keycloak)
CLIENT_SECRET={your client secret}
You can configure the secret from keycloak console.
client - credentials.
3. apply (on kubeflow)
Make sure apply it.
~/manifests/common/oidc-authservice/base# kustomize build | kubectl delete -f -
~/manifests/common/oidc-authservice/base# kustomize build | kubectl apply -f -
4. Match the client scope (on keycloak)
Add client scopeds to kubeflow(client)
I added "groups" (Don't forget to add predefined mappers)
5. client setting (on keycloak)
We need to set the "Valid Redirect URI" to "http://{kubeflow_server}:{kubeflow_port}/login/oidc/*"
This should matche with the redirect_url section from params.env of kubeflow.


유저 만들기 추가