
View Certificate Details
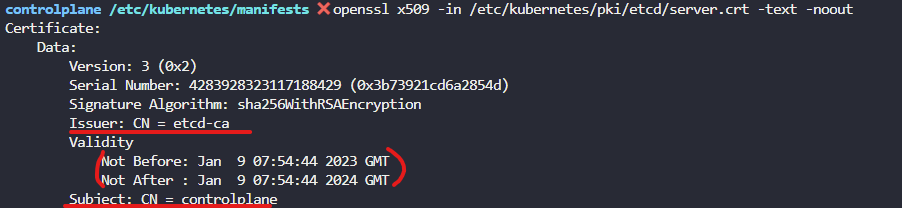
openssl x509 -in XXXXX.crt -text -noout 명령어로 인증서에 대한 정보를 볼 수 있다
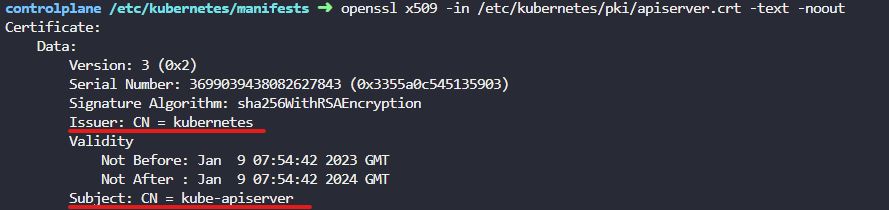
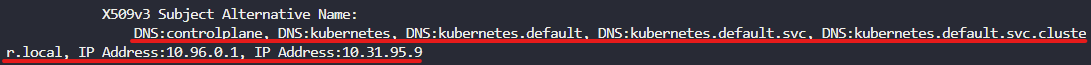
apiserver
-
certificate
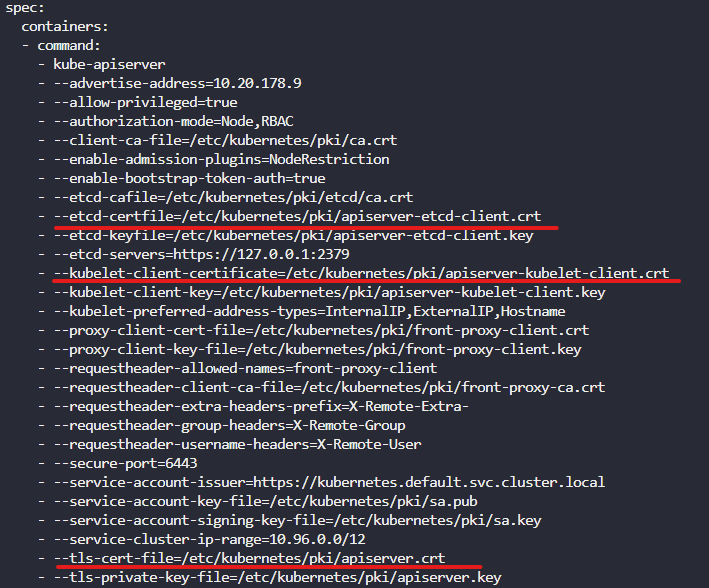
-
openssl x509 인증서
etcd
-
certificate
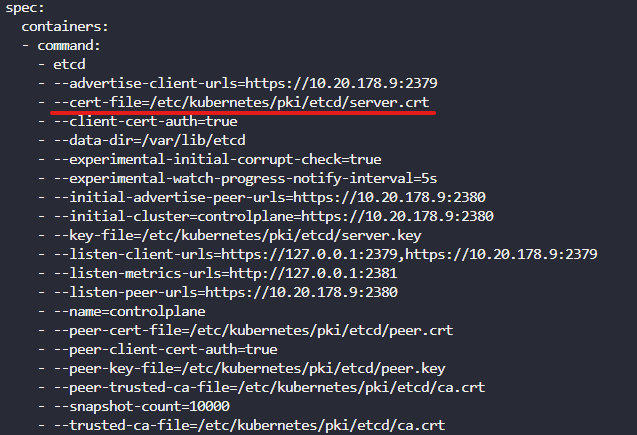
-
openssl x509 인증서
핵심 명령어
crictl ps -acrictl logs XXXXXXX
Reference
https://kubernetes.io/ko/docs/tasks/debug/debug-cluster/crictl/ -> crictl로 kubernetes node 디버깅하는 법
https://github.com/kubernetes-sigs/cri-tools/blob/master/docs/crictl.md -> crictl 관련 github
Certificates API
핵심 명령어
cat > akshay.yamlcat akshay.csr | base64 -w 0k certificate approve akshaykubectl certificate deny agent-smithk delete csr agent-smithk get csr
Reference
https://kubernetes.io/docs/reference/access-authn-authz/certificate-signing-requests/
KubeConfig
KubeConfig은 $root/.kube/config에 있다
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJek1ERXdPVEE0TlRRMU5sb1hEVE16TURFd05qQTROVFExTmxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBUDV2ClJieThGZGlZeTg4Q2oxNURkN0l6QWlaSWdpanhHb0RkRTJkek5nWjNPd3Vya2tiWlIxdlpldlliRTBqaDU0Q08KUjRsMVNZK3lRYmJPOEFvTEpIZk9QeU04R2xPYjlqVS8vT3VxQUR4Q2YySmRBb1N4Zm5qcS9BMFZzZm00bXZ2TQp0YlpRVlZDdjB0ZndJN1BxbUZHSU4wVGNxbTVTZmN5RjUvSXZXNjlMUFZGclhpOWVBMFlQR2h3TDZvUlJlc3pqCkIxYzJQYm5KRTA5M1hxaEZUWEExVXEwYlFSK3REVDl3dDZCaGdHQmxqajA5WGp5TENwU2I2RG9KK0FZT2hlNDkKZ1NHZk5JY21WM00rNHhrbm1HZ2dzM2MrcmhjcHNERlBTOFNTNHlmQ3FsWTVHR3lyYVZmalVvN0dGeFlOZldiNAo2aXJYOHJpbEdKODdFeDNidmljQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPZDVVbmJwaktRdUZmeURXRy9HMkZKcHNNS3BNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBTWxoZnBGZ1VTSW8xMjI3SmxvcApSVEw0NHVVdXUzRVNPOUtYekVMZTAxTC9mVGtPTDUxVUgyTUxjUDNjdHNPeDIxUWhoY21XTUNLdllzYlNsZVErCmViTFhBc0NySHpiMXYvS0IwU2VIaWczTENXWGIrSnZDMnNjdWNGRnUvbHA0T3AyQ0VtclRRQ0hERTFyVWJEWXYKeTNKbEpSMlZ3bEtLM0Nha2xGTDkvSytoeXNZckpHZTZ4K3JvVFY1VnNqYmQ5OE9Nakhrem90a25FM2U5eXNqWQprUHRGUlJrSVVnOGtUb2MyVERxaHd3dDRpQUxaZ1BGZElVRXg0T1V0OE1Xdm42TUV1bnRGaURpcUhGbVBMUHdYCkZFVmlEMmh4UGpHMmVUc2t5UXRiVVRnTURLd01ack5QYU1sYzAzcnZzWU91aldjYmt4MFpBY2lvLzM3V1FWOE0KSUxrPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://controlplane:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJVENDQWdtZ0F3SUJBZ0lJS0VvcW5LUndOZm93RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TXpBeE1Ea3dPRFUwTlRaYUZ3MHlOREF4TURrd09EVTBOVGhhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXdXT3V0T2VnbWcrRVRMa3IKZmJZUGEwZVRBSVVZeU9haURWaHI4VkE3c1lLOVo2UUd0cHdMdnJkN0drZ2lDWjdJbnNSTnV0cGJqNCt2ams3ZApuRFNoWitjbXhCWTNkUGRXY25MTFFOY3VUWUJnQmgvRFZPT3AwRmhRanpWc2hZSkEvdEt1MnA1azZwaGliTXZnCkIwSTJkWDhTVzhZTzlOYUp3blJhZ0w1bUR2T01DTGNoNUpqSmREWXk3RGtSeDJUVHdHQzJVdmxYTm9QZm1UY2MKcUlFT2NpVEV4YStWQlZ2VVloMmlhTUV1Z1RZN0l5N0pIRFFHcFVNMGlXY1VsbjVzbFVtMWord2ZtYXJubDBZeQpwUjZZM2ZXb0g5cFlqQ24zVEJIZ0piMlNVdjhXeWpKK0lyN2ZwUHF2SjVqRURPTklycmVwY2FEODFSdW5MTXh3CnhZcndvd0lEQVFBQm8xWXdWREFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RBWURWUjBUQVFIL0JBSXdBREFmQmdOVkhTTUVHREFXZ0JUbmVWSjI2WXlrTGhYOGcxaHZ4dGhTYWJEQwpxVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBTlBINlhaNmdrcmxQeG1ITzV4STdUNkNhUW8rc1c5NE9JWHZTCkFaUHk1NmRZZTZudDNGdTFlV3dzdmc2dU5IYmVsMEI3YktKQ0c5ZXo5LzRHRm9GQ3NGUUUvdEYvQXNBZ0VuOGQKQllFNmtmSHdpMFRsZ1pLUHZVRngyYVZ0cStyWjZTcnlybW5Kd0ZrVU00d04zODdyZlNqZlFDNkpGTkNLRU9QRQpQWEZPRXJCYkFkZ3d0Y2E3SkZWV1NLRXdMdVBialJVUjQ2cy9RdG9zb3IzUFVUNFRQMkgrTEszM1RibkZjbFJCCnE2RjlUWmpYUlVmMlN6d04vWjdNUXhIYkhjQ2lZZUg3MFp3djhkYVhOMWFpODZRbnFMMU5kMW9jd1RsQmFZTFMKdkJJQlU0ZXFnQXZmcDdzOE5BYTVWN215L3lRU2w0VFp5OVgvQlJoTk5JS3VCT0VielE9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb2dJQkFBS0NBUUVBd1dPdXRPZWdtZytFVExrcmZiWVBhMGVUQUlVWXlPYWlEVmhyOFZBN3NZSzlaNlFHCnRwd0x2cmQ3R2tnaUNaN0luc1JOdXRwYmo0K3ZqazdkbkRTaForY214QlkzZFBkV2NuTExRTmN1VFlCZ0JoL0QKVk9PcDBGaFFqelZzaFlKQS90S3UycDVrNnBoaWJNdmdCMEkyZFg4U1c4WU85TmFKd25SYWdMNW1Edk9NQ0xjaAo1SmpKZERZeTdEa1J4MlRUd0dDMlV2bFhOb1BmbVRjY3FJRU9jaVRFeGErVkJWdlVZaDJpYU1FdWdUWTdJeTdKCkhEUUdwVU0waVdjVWxuNXNsVW0xait3Zm1hcm5sMFl5cFI2WTNmV29IOXBZakNuM1RCSGdKYjJTVXY4V3lqSisKSXI3ZnBQcXZKNWpFRE9OSXJyZXBjYUQ4MVJ1bkxNeHd4WXJ3b3dJREFRQUJBb0lCQUc5Rk42U0hFWFVUTUlBawptczErRDJrZWlZcG5DbGV0dTlnSjVERzRoR0FpWlhCWWhEUlZuTHhqUGNWbGM1QXRlQ2xCc2FldE03bHFad3h1CmZEd0FYRTQ0UmFuVlRwdFNKTDg5SlkxdFFncjlya0pYekQvdnJpbGVaeHUvRlczTUFER2ViMVVDaGZZbEw1eUIKd2FqcmhBSWUxeVZPMUJRenpKZkI4c0RZekVnVkFIbWt5Y2xvZmpObzNnbkZpN0d5RklJd01sNzFQVjQ2b2VNYgoyNE53SFFidmVrc2EvNy9QQjE0cnI0VlljV2xQYXp3RHh2bHhkQUJBZUxlcGxsU0hZRXlST2RldnZCV3NvZWlHCllJSStQdjNFWDVBczR2OWlFaERiYVFmMXdaZ09HeTBoNzViQjNKRWQwbGFNWUxaSlFEQkdJOWhNRUF1VWVaLzkKWFRZQ3pBRUNnWUVBOURKeG5jTGhnZVRja0M5ZFpPVnJNN08xUy9na0RMODFjS1hZdUZLcE9mUjVmb2s5Z0tnRQozU0tmRVVmSUxYY3l6ZEMvalFQeFN1MmM2Z1pnV2V2dHZZOHI1b21zeU9yVnJlTThuNnZzVERKTEZ5eVM0TjczCjQwTkpNQlRZT0EyMW1tK3BGTVY3VmtCOVp3bGw5M2V2cFM0SkFXMS9IZHMvcVFZYW5zR0lKeU1DZ1lFQXlyeVMKeDJqU2R5TlVhWEtkeHRsYXhraUxPMU9INU5vTHRkRHNTcWFHdGpmbTJLdk54Q0JvNitweXR5UG40SVY4ZkNjdQpnR2s4c2VBVTZ3NnppV1FPZHdCWldIUjJqR05Wa1ZQMUYyakREMW9sN1ZUWkI0d2pzKysxZWNJWTZWRCtTNy9nCkpLQ3VzdksrWU9HN0M4aTBFZWlsbk0reDBxWkw4dTY3blpUamFJRUNnWUJZcDZ1cCsrT0ZGZ0toY2lDMURibHkKeHM2T0t5TmpZVlBVZHRHTWNhNHdkVHBhbnhhdUM5SGdPcjZITm9sTlFGWTRkSTNtYzBUNXovUkUzbFhDcjYzYgpRUXhPSVRPU3FmY3pyeWtHU3hONXdsU1NzRU1PMHNRcVJQWmdOMkVjVUpYYTRLa0Erb1ZCbGg0dzl5K0d2WFFPClF2MVFBR0hEQkNORGlRekhFRG9QQXdLQmdGYjUxNjZkRmMzdTVrUG0zREYzQmk2UzZNaW02V0lRK1gwakNIeHUKUE5UbjNxMk41MVVBNG9KenJvdExhQ3MybVZWYUtlVUZRUGkrdmJxcUwvUDliUWM0cXh2N3V2QTNuWG9mbnNKUQpPMzdXbWZiYnM5QTlHd1FURHJRUnhVWXpiU1ZxUitydTFJUUpDQXZnUzdLZWhFSTZvUEpKV0d5YTAzS0JZUlFWCjBBb0JBb0dBQmx0Z002ZllJRDhkWXBoSENyeVlDY0xKUEtyY25xT2xVeXk0MjY1T3VqbUQ0enBnSnlmK2pwcmIKVFE3WUJCYmVHRWNoM0VjWUlINDhQR0s3QWt1aHhlWU42KzNMWFRPWnh1ZzBQRXIyRE11V3ZvVXBET05aT0RDYQpPd2syVVltU1lkRE5ZV2dsV2dRZVZjaGdWdVp2TlREeHJGeFBUTGsycHRIYnc5MUpTZW89Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==핵심 명령어
kubectl config --kubeconfig=config-demo viewmv my-kube-config .kube/config
Reference
https://kubernetes.io/docs/tasks/access-application-cluster/configure-access-multiple-clusters/ -> config에 대한 문서
Role Based Access Controls
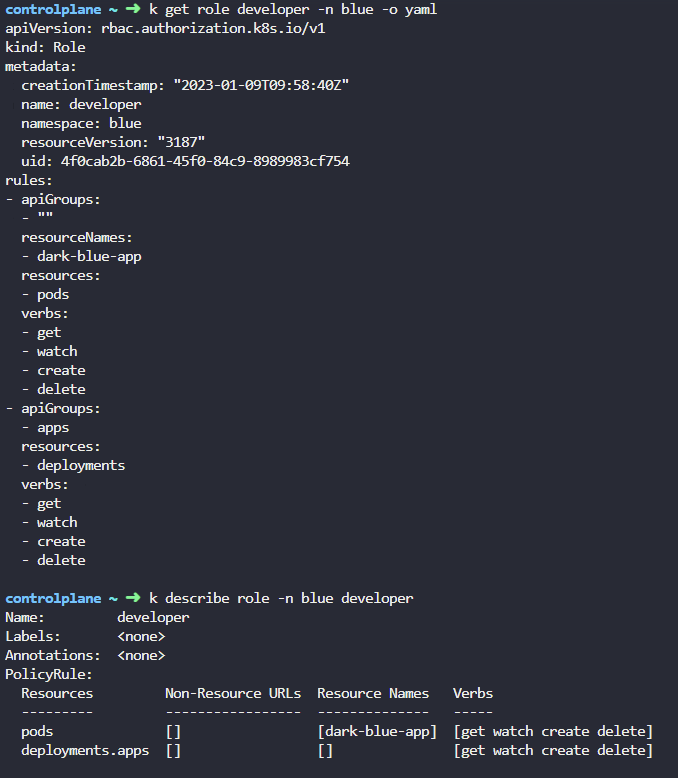
/etc/kubernetes/manifest/kube-apiserver.yaml에서 authorization 확인 가능하다
--as dev-user은 dev-user 사용자로 해당 명령어를 실행하는 것과 같은 결과를 보여준다
핵심 명령어
k get rolesk get roles -A --no-headers | wc -lk describe role -n kube-system kube-proxyk get rolebindingsk describe rolebindings -n kube-system kube-proxyk config viewk get pods --as dev-userkubectl create role developer --verb=list,create,delete --resource=podskubectl create rolebinding dev-user-binding --role=developer --user=dev-user
Reference
https://kubernetes.io/docs/reference/access-authn-authz/rbac/ -> role, rolebinding에 관한 공식 문서
Cluster Roles
clusterrole과 clusterrolebinding은 role과 rolebinding과 다르게 namespace에 한정되지 않는다
핵심 명령어
k get clusterrolek get clusterrole --no-headers | wc -lk get clusterrolebindingsk get clusterrolebindings --no-headers | wc -lkubectl create clusterrole storage-admin --verb=get,list,watch,create,delete --resource=persistentvolumes,storageclasseskubectl create clusterrolebinding michelle-storage-admin --clusterrole=storage-admin --user=michelle
Reference
https://kubernetes.io/docs/reference/access-authn-authz/rbac/ -> clusterrole, clusterrolebinding에 관한 공식 문서
Service Account
Reference
https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/
Image Security
Private Image를 다운받기 위한 방법
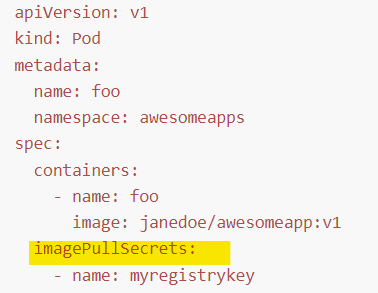
핵심 명령어
k get secretkubectl create secret docker-registry private-reg-cred --docker-server=myprivateregistry.com:5000 --docker-username=dock_user --docker-password=dock_password --docker-email=dock_user@myprivateregistry.com
Reference
https://kubernetes.io/ko/docs/concepts/containers/images/#%EC%9D%B4%EB%AF%B8%EC%A7%80-%ED%92%80-pull-%EC%A0%95%EC%B1%85 -> imagePullSecrets 설정 방법
Security Contexts
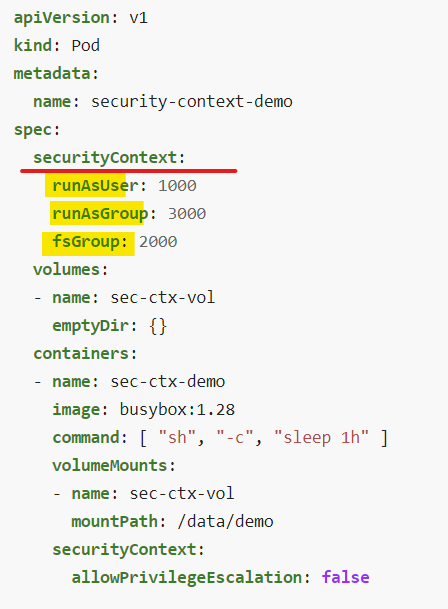
Pod 수준의 Security Contexts와 Container 수준의 Security Contexts이 존재한다
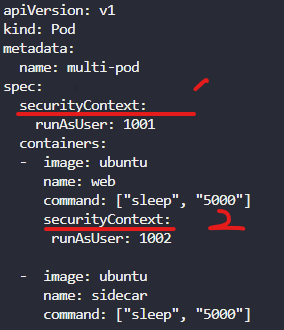
핵심 명령어
k exec ubuntu-sleeper -- whoami
Reference
https://www.udemy.com/course/certified-kubernetes-administrator-with-practice-tests/learn/lecture/32211174#overview -> security context 설정하는 방법
Network Policies
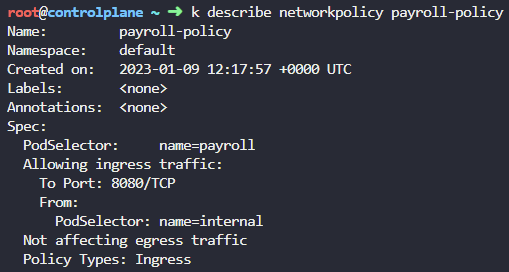
핵심 명령어
k get networkpoliciesk get netpolk describe networkpolicy payroll-policyk get ingressesk get pods --show-labels
