1. User-password Encryption
JWT : JSON Web Token is mostly used for data encryption
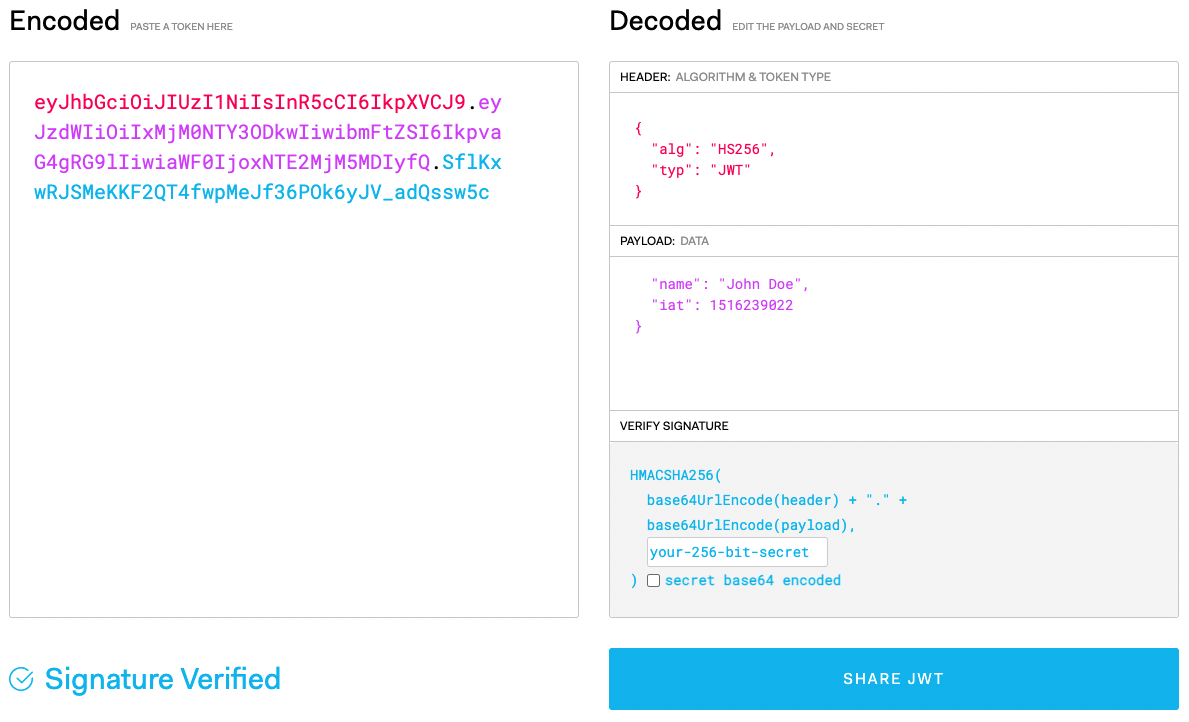
Here, key is the string-type password
--> Using this key, only the one who knows the password is able to access for decoding.
2. Authentication / Authorization
Authentication
// ============== Authorization Resolver ==============
@Mutation(() => String)
async login(
@Args('email') email: string, //
@Args('password') password: string,
) {
// 1. 로그인 (DB에서 이메일과 비밀번호가 일치하는 유저 찾기)
const user = await this.userService.findOne({ email });
// 2. 일치하는 유저가 없으면 ==> 에러 던지기
if (!user) {
throw new UnprocessableEntityException('존재하지 않는 이메일입니다'); // 422 error -> 로직상에 문제가 있을때
}
// 3. 일치하는 유저가 있지만 암호가 틀렸다면 ==> 에러 던지기
const isAuth = await bcrypt.compare(password, user.password); // 순서 중요함
if (!isAuth) {
throw new UnprocessableEntityException('암호가 일치하지 않습니다');
}
// 4. 일치하는 유저가 있으면 ==> accessToken (JWT) 토큰 만들어서 프론트앤드에 주기
return this.authService.getAccessToken({ user });
}// ============== Authentication Services ==============
@Injectable()
export class AuthService {
constructor(private readonly jwtService: JwtService) {}
getAccessToken({ user }) {
// sub안하고 id해도 됨 - just written in jwt docs
return this.jwtService.sign(
{ email: user.email, sub: user.id },
{ secret: 'myAccessKey', expiresIn: '1h' },
);
}
}Authorization
file route - commons/auth
export class GqlAuthAccessGuard extends AuthGuard('access') {
getRequest(context: ExecutionContext) {
// 검증하는 함수 ==> 함수를 바꿔치기해주는거임 AuthGuard('access)를 get Request로 바꿔줌
const ctx = GqlExecutionContext.create(context);
return ctx.getContext().req;
}
}==> gql 풀어내기 (=guard 뚫기)
@Injectable()
export class JwtAccessStrategy extends PassportStrategy(Strategy, 'access') {
// 여기 작성한대로 userResolver의 fetchUser 검증하겠다
constructor() {
super({
// 검증부 (먼저 실행되고 검증에 성공하면)
jwtFromRequest: ExtractJwt.fromAuthHeaderAsBearerToken(),
secretOrKey: 'myAccessKey',
});
}
// 검증 완료되면 실행 (검증 성공)
validate(payload) {
console.log(payload);
return {
email: payload.email,
id: payload.sub,
};
}
}