AWS IAM User의 Access Key와 Secret Key를 사용하는 대신 OIDC를 적용한 Role을 만들어 Github Action으로 배포 테스트!
💡 Github Docs에 의하면 OIDC를 사용하면 여러 보안상의 이점을 얻을 수 있다고 한다.진행중인 사이드 프로젝트에 이 방식을 사용하여 Github Action 파이프라인을 구성해보았다.
-
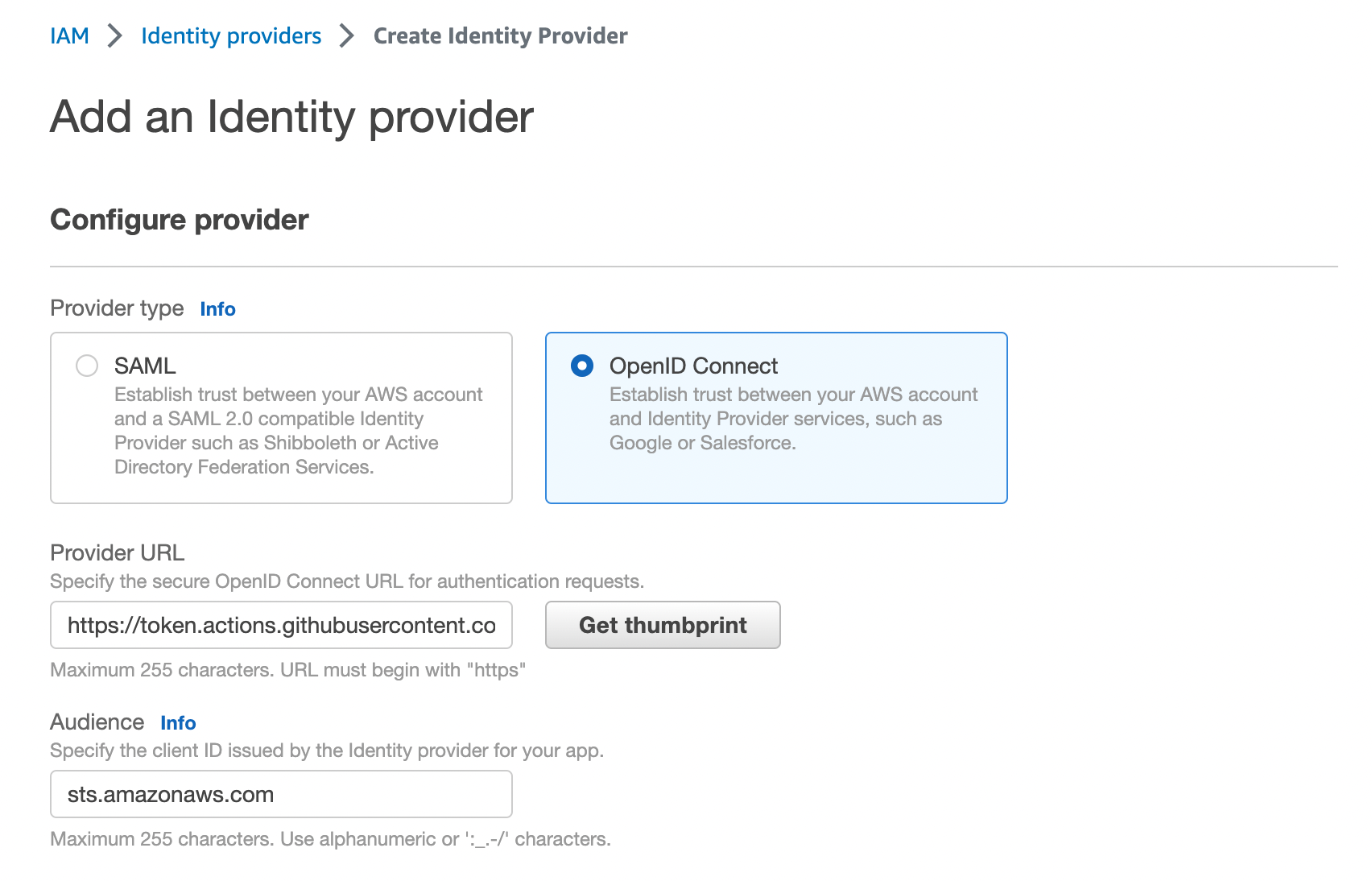
Identity providers 생성
- ProviderURL: https://token.actions.githubusercontent.com
- Audience: sts.amazonaws.com
-
Role 생성
- Github Action에서 사용할 IAM Role을 생성
- Web Identity를 선택하고 1에서 만든 provider를 선택
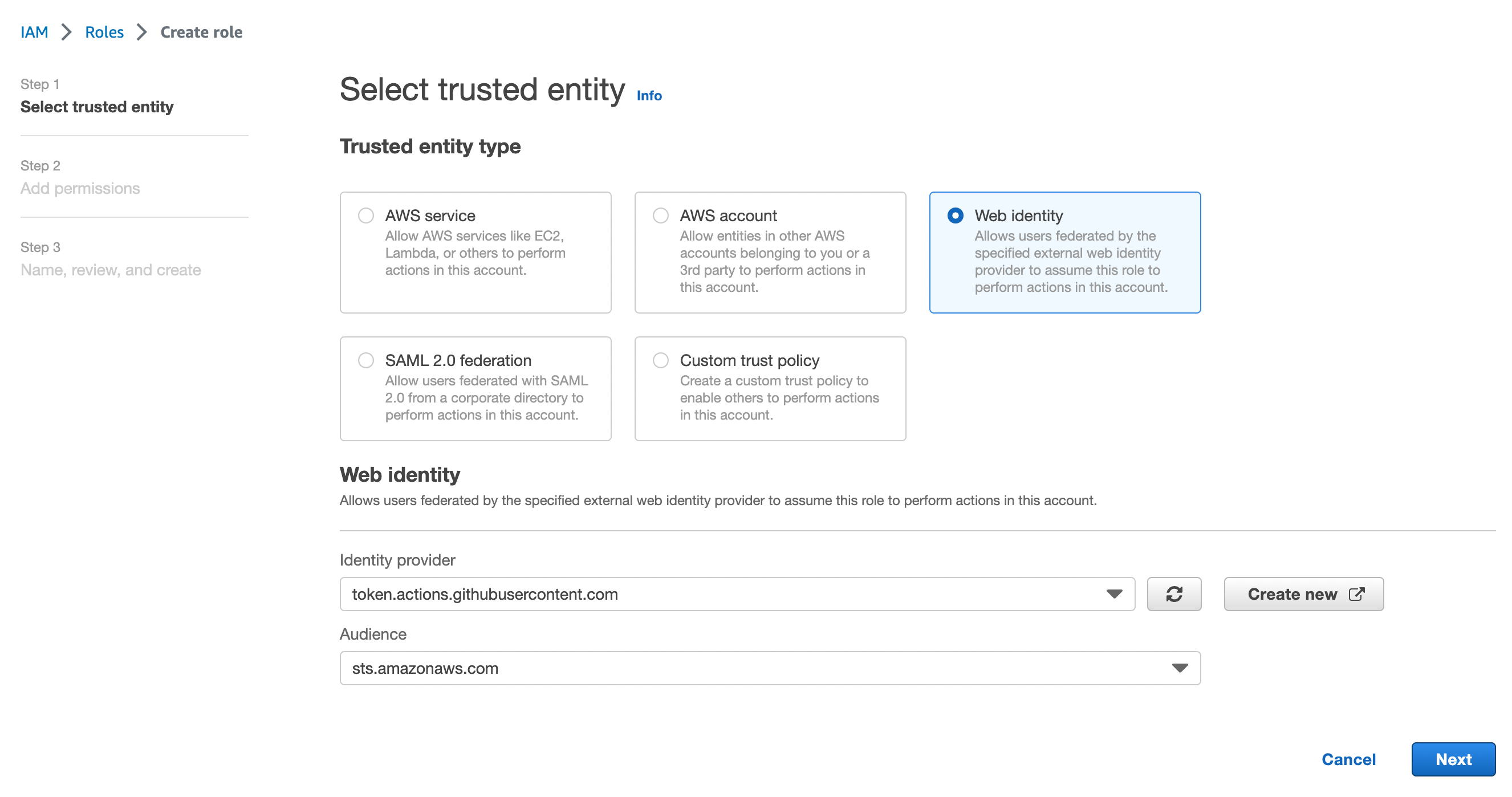
- Trust relationships에 Orginization과 Repository를 명시해줍니다.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::123456789012:oidc-provider/token.actions.githubusercontent.com" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringLike": { "token.actions.githubusercontent.com:sub": "repo:[Orginization/Repository]:*" }, "ForAllValues:StringEquals": { "token.actions.githubusercontent.com:aud": "sts.amazonaws.com", "token.actions.githubusercontent.com:iss": "https://token.actions.githubusercontent.com" } } } ] }
-
Policy 생성
- ECR Policy를 생성하여 Role에 연결
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "ecr:GetDownloadUrlForLayer", "ecr:BatchGetImage", "ecr:CompleteLayerUpload", "ecr:DescribeImages", "ecr:GetAuthorizationToken", "ecr:DescribeRepositories", "ecr:UploadLayerPart", "ecr:ListImages", "ecr:InitiateLayerUpload", "ecr:BatchCheckLayerAvailability", "ecr:GetRepositoryPolicy", "ecr:PutImage" ], "Resource": "*" } ] }
-
Github Action에 적용하기
- Gradle 프로젝트를 도커 이미지로 말아서 ECR에 올리는 workflow
name: Java CI with Gradle on: push: branches: [ "develop" ] env: ecr_url: 123456789.dkr.ecr.ap-northeast-2.amazonaws.com/movie-api role_arn: arn:aws:iam::123456789:role/ci-github-action-movie-oidc-role aws_region: ap-northeast-2 jobs: prepare: name: Prepare Build runs-on: ubuntu-latest outputs: tag_date: ${{ steps.tag.outputs.date }} tag_git_hash: ${{ steps.tag.outputs.git_hash }} steps: - uses: actions/checkout@v3 - name: Get time TAG id: tag run: | echo "date=$(date +'%Y%m%d.%H%M')" >> $GITHUB_OUTPUT echo "git_hash=$(git rev-parse --short HEAD)" >> $GITHUB_OUTPUT build: name: Build runs-on: ubuntu-latest needs: prepare permissions: id-token: write # This is required for requesting the JWT contents: read # This is required for actions/checkout outputs: tag_date: ${{ steps.tag.outputs.date }} tag_git_hash: ${{ steps.tag.outputs.git_hash }} steps: - uses: actions/checkout@v3 - name: set JDK uses: actions/setup-java@v3 with: distribution: 'corretto' java-version: '17' cache: 'gradle' - name: Run chmod to make gradlew executable run: chmod +x gradlew - name: Gradle Build Movie uses: gradle/gradle-build-action@v2 with: arguments: build - name: Docker build movie-api run: docker build -t movie-api ./ - name: Configure AWS Credentials uses: aws-actions/configure-aws-credentials@v1-node16 with: aws-region: ${{ env.aws_region }} role-session-name: GitHubActions role-to-assume: ${{ env.role_arn }} - name: Login to Amazon ECR id: login-ecr uses: aws-actions/amazon-ecr-login@v1 - name: Publish Image to ECR(movie-api) run: | docker tag movie-api:latest ${{ env.ecr_url }}:${{ needs.prepare.outputs.tag_date }}.${{ needs.prepare.outputs.tag_git_hash }} docker push ${{ env.ecr_url }}:${{ needs.prepare.outputs.tag_date }}.${{ needs.prepare.outputs.tag_git_hash }}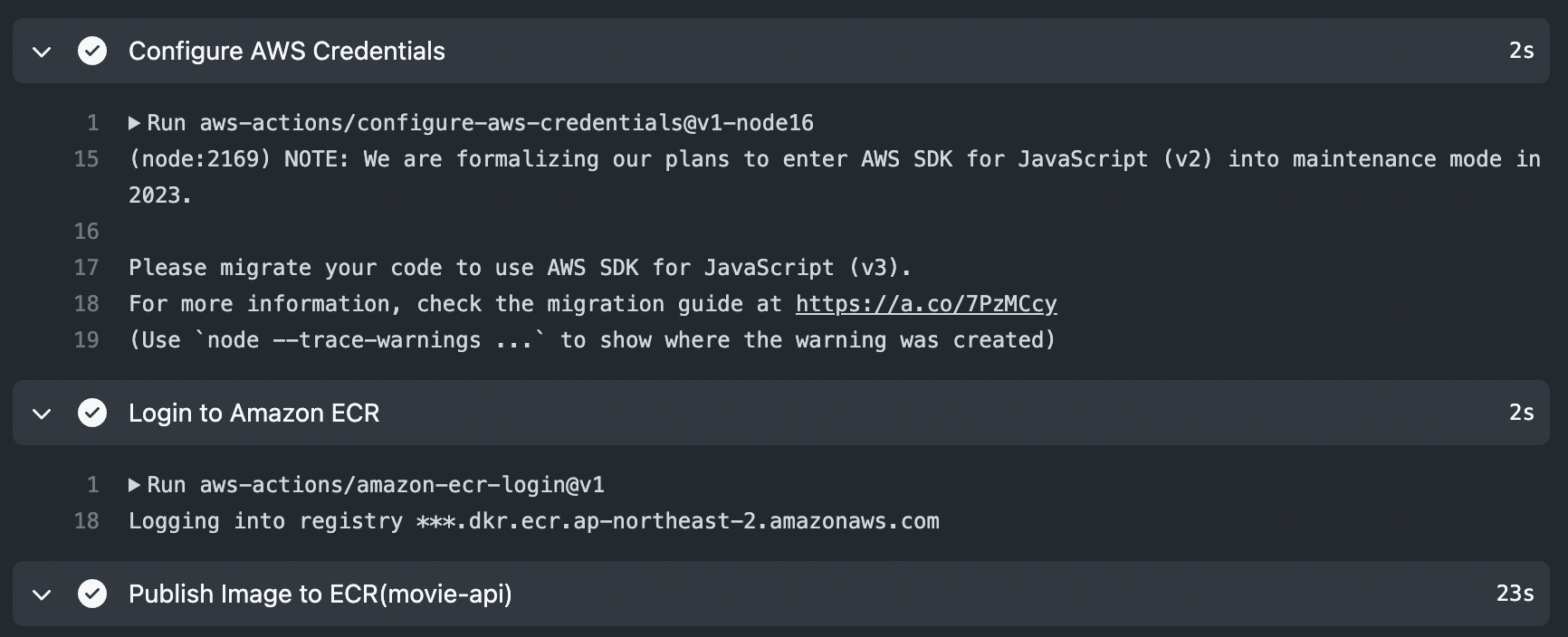
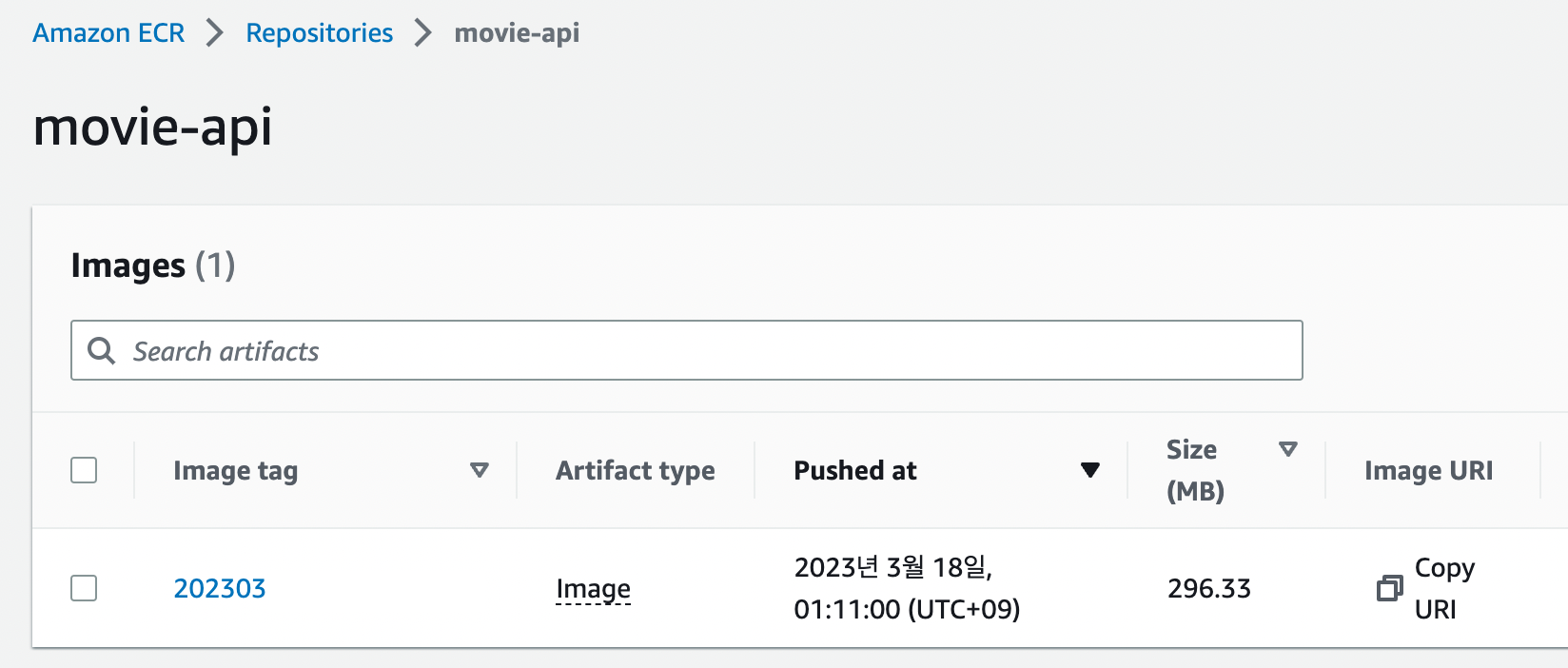
설정 후 Github Action을 실행시켜보면 정상적으로 AWS에 접근하여 ECR에 이미지가 올라간 것을 확인할 수 있다.
참조
