내 컴퓨터 192.168.0.14
VMware 192.168.181.0/24
컨테이너 100.100.100.0/24
CNI 200.200.200.0/24
vi /etc/hosts 애들 이름 설정해주기!
192.168.181.10 master
192.168.181.20 node-01
192.168.181.20 node-02
방화벽 설정
- master, node-01, node-02
firewall-cmd --permanent --add-port=6443/tcp
firewall-cmd --permanent --add-port=2379-2380/tcp
firewall-cmd --permanent --add-port=10250/tcp
firewall-cmd --permanent --add-port=10251/tcp
firewall-cmd --permanent --add-port=10252/tcp
firewall-cmd --permanent --add-port=10255/tcp
firewall-cmd --reload
modprobe br_netfilter
echo '1' > /proc/sys/net/bridge/bridge-nf-call-iptables- 필요한 포트들을 열어주고
setenforce 0
sed -i --follow-symlinks 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/sysconfig/selinux
init 6- 다시켜도 실행되지 않도록 설정한 후에 재실행
도커설치
- master, node-01, node-02
- 도커로 이미지만들고 컨테이너 만들 거니깐
yum install -y yum-utils
yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
yum-config-manager --enable docker-ce-nightly
yum-config-manager --enable docker-ce-test
yum install -y docker-ce docker-ce-cli containerd.io --allowerasing- 도커 설치해 주기!
mkdir /etc/docker
cat <<EOF | sudo tee /etc/docker/daemon.json
{
"exec-opts": ["native.cgroupdriver=systemd"],
"log-driver": "json-file",
"log-opts": {
"max-size": "100m"
},
"storage-driver": "overlay2"
}
EOF- 레포추가: 호환이 될수 있도록(곧 k8s가 도커를 버릴예정??)
- 이거 설정하고 잘 적용 되었는지 확인이 필요하다 안그러면 아래와 같은 에러가 나올 수 있다.
docker info|grep "Cgroup Driver"
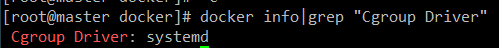
- 레포지터리가 잘 적용되었으면 Cgroup Driver: systemd로 되어있어야한다!
This can take up to 4m0s 에러해결!
systemctl daemon-reload
systemctl restart docker
systemctl enable docker- 도커 설치하고 설정변경 했으니깐 재실행, 그리고 재실행시 자동으로 켜지도록!
k8s 설치
- master, node-01, node-02
firewall-cmd --add-masquerade --permanent
firewall-cmd --reload- 방화벽 설정해주고
cat <<EOF > /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
EOF- 레포 추가해주고
sysctl --system이 명령어로 위 허용해주는 것들이 포함되었는지 확인해 준다.
cat <<EOF > /etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://packages.cloud.google.com/yum/repos/kubernetes-el7-x86_64
enabled=1
gpgcheck=1
repo_gpgcheck=1
gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg
EOF- 레포 추가해주고
dnf install -y kubelet-1.22.5 kubeadm-1.22.5 kubectl-1.22.5 --disableexcludes=kubernetes설치
systemctl enable kubelet
systemctl start kubelet- 실행하고 재실행해도 사용되도록
k8s swap 설정
- master, node-01, node-02
swapoff -a
vi /etc/fstab
#/dev/mapper/cl-swap none swap defaults 0 0 - 주석처리로 변경
- swap 메모리 정리잘 된곳이 있으니깐 찾아보기
- 간단하게 k8s는 메모리에서 동작한다. 근데 새로운 프로그램이 돌아갈때 메모리를 사용하는데 이때 메모리가 부족하면 우선순위가 낮은 친구들을 잠시 이동시켰다가 불렀다해서 사용중이던 친구들을 swap해주는데 이때 HDD 아니면 HDD에 만들어놓은 폴더에서 왔다갔다 하게 되는거다. 그럼 성능도 저하되고 날라갈 수 도있으니깐 꺼두는것을 권장한다!
mastsr 설정
- master
kubeadm init --pod-network-cidr 100.100.100.0/24 --control-plane-endpoint "192.168.0.14"This can take up to 4m0s 에러해결!
- 도커 레포 잘못추가해주면 이 에러나온다 앞에서 한번 언급했다. 자세한 사항은 들어가서 보자!
- 컨테이너 환경의 IP 100.100.100.0/24를 사용하고 엔드포인트로 내 컴퓨터
- 마지막에 나오는 마스터의 join 항목을 워커에게 추가해야 가입이 가능하다! 나는 너의 마스터야라고 알려주는거다!
mkdir -p $HOME/.kube
cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
chown $(id -u):$(id -g) $HOME/.kube/config-
사용자 홈디렉토리에 관리자 설정파일을 넣어줘야 쿠버 명령어를 사용할 수 있다.
-
한번 디렉토리 넣었다가 다시 넣어르했떠니 아래와 같은 에러가 나왔고 그 아래 명령어로 해결했다.
Unable to connect to the server: x509: certificate signed by unknown authority (possibly because of "crypto/rsa: verification error" while trying to verify candidate authority certificate "kubernetes")
unset KUBECONFIG
export KUBECONFIG=/etc/kubernetes/admin.conf
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/configkubectl get nodes 확인, 일단 마스터만 나옴
kubectl get all --all-namespaces
네트워크가 설정되지 않아서 ready 상태가 아니다.
- k8s는 왜 네트워크를 설정해주지 않는다.. 그래서 칼리오꺼를 사용해서 설정해주려고 한다.
calico 설치 메뉴얼
curl https://raw.githubusercontent.com/projectcalico/calico/v3.25.1/manifests/calico.yaml -O- 우리는 50개 미만으로 사용할 거니깐 요걸로 설치!
vi calico.yaml
# - name: CALICO_IPV4POOL_CIDR
# value: "192.168.0.0/16"
- name: CALICO_IPV4POOL_CIDR
value: "200.200.200.0/24"- 설정변경해주고 이거 yaml파일이니깐 들여쓰기도 문법이다 조심해주자!
kubectl apply -f calico.yaml칼리오 yaml 파일 실행!
worker 설정(node)
- node-01, node-02
firewall-cmd --zone=public --permanent --add-port={10250,30000-32767}/tcp
firewall-cmd --reload- 방화벽 설정해주고
kubeadm join 192.168.0.14:6443 --token 9rcwt1.k4gkq3z9qrhw2fjl \
--discovery-token-ca-cert-hash sha256:2ea844bd0bf24fee4d8124113c8d66b46e335cdb4c5b98ee9568a1a05ec2c916- 마스터에게 가입해주자!
확인
kubectl get pod -n kube-system 전부 Running으로 뜨는지 확인해주고
kubectl get nodes 전부 Ready로 나오는지 확인해주면 된다.
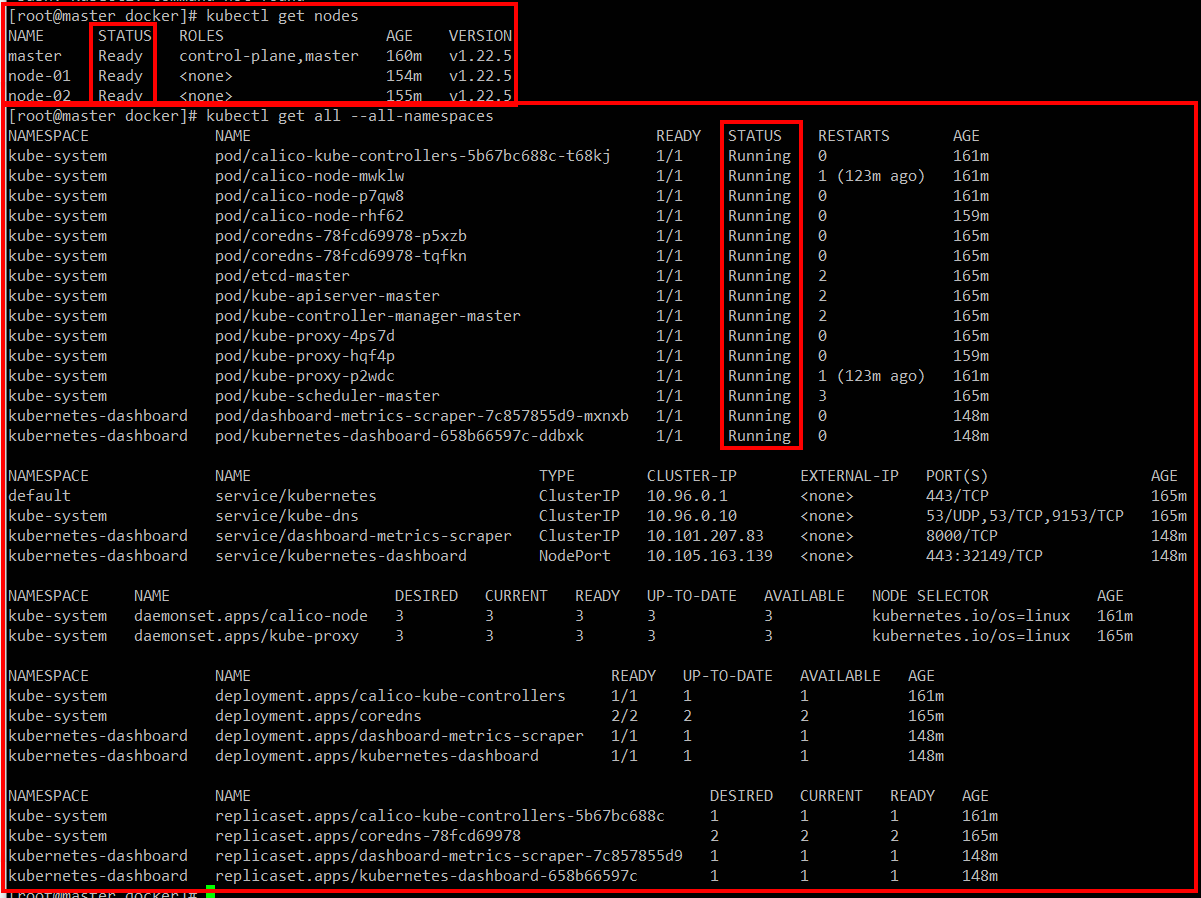
- 최종적으로 잘 설치되어 있는것을 확인하자!
대시보드
- master
- 보기 편하도록
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yamlvi recommended.yaml
39 spec:
40 ports:
41 - port: 443
42 targetPort: 8443
43 selector:
44 k8s-app: kubernetes-dashboard
45 type: NodePort- 45번 라인에 넣어주자!
kubectl apply -f recommended.yaml yaml 실행
kubectl get services -n kubernetes-dashboard 대시보드 포트번호 확인
firewall-cmd --permanent --add-port=[확인한포트번호]/tcp
firewall-cmd --reload- 윈도우의 웹 브라우저로 https://[마스터노드IP]:[확인한포트번호] 접속
- 크롬에서 안전하지 않은페이지 뜰 때 브라우저 아무 곳에나 thisisunsafe 입력
- 이제 접속하려면 토큰이 필요하다!
cat <<EOF | kubectl create -f -
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
EOF- 유저를 만들어주고
cat <<EOF | kubectl create -f -
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system
EOF- 권한과 역할을 주면
kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep admin-user | awk '{print $1}')이친구로 토큰을 확인할 수 있고 접속할 수 가 있다.

- 시간이 지남에 따라 토큰값이 사라지는데 그 때마다 저 명령어를 칠 수는 없으니깐
history로 저 명령어 실행했던 번호 확인한 다음에![번호]해주면 토큰값을 바로 얻을 수 있다.
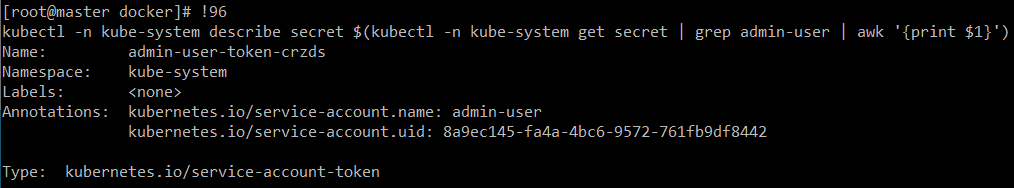
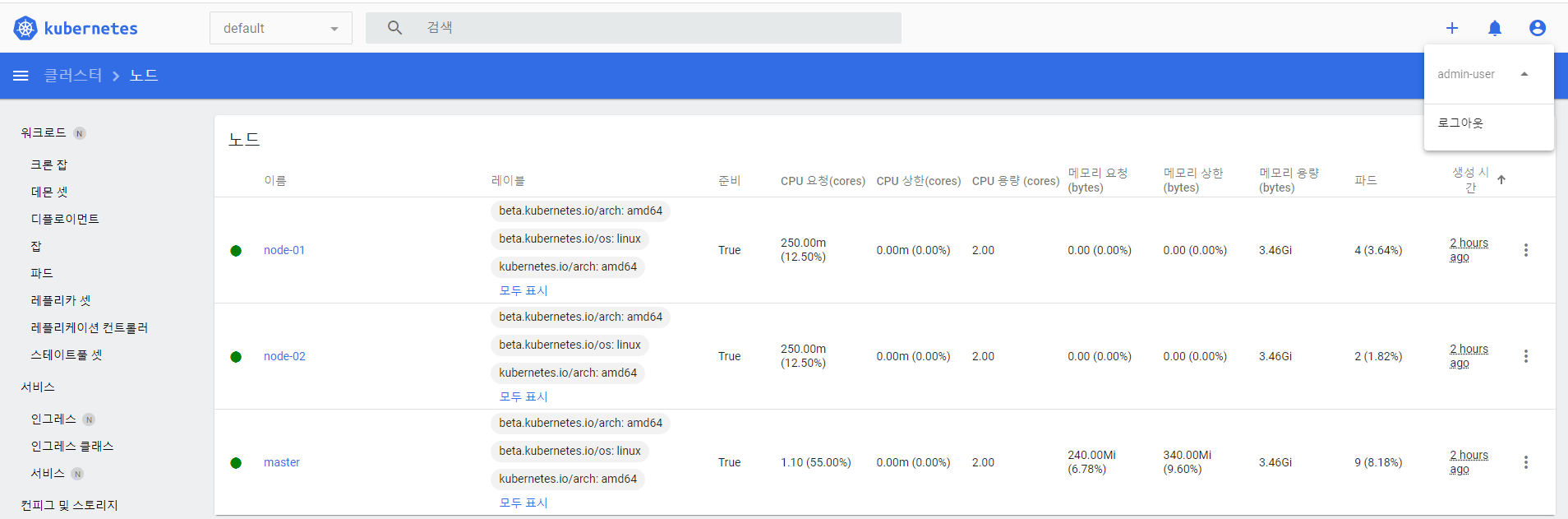
- 대시보드에서 확인할 수 있다.