참고 - https://aws.amazon.com/ko/premiumsupport/knowledge-center/eks-iam-permissions-namespaces/
참고 3 - https://bscnote.tistory.com/129
User
https://kubernetes.io/docs/reference/access-authn-authz/rbac/
- 먼저 User를 생성합니다. User에게는 아래와 같은 Policy를 부여합니다.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<<Account Number>>:role/EKS-Developer-Policy"
},
{
"Effect": "Allow",
"Action": [
"eks:DescribeCluster",
"eks:ListClusters"
],
"Resource": "*"
}
]
}- 이제 Admin 즉, 현재 Cluster에 대해서 작업이 가능한 Instance에서 작업을 합니다. 먼저 API, Resource에 모든 행동을 할 수 있는 Role을 생성합니다. 대신 조건은 dev라는 Namespace에 대한 작업만 허용합니다.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: dev-access-role
namespace: dev
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs: ["*"]- 그런 다음 위에서 생성한 Role을 Binding 해주기 위해서 Role Binding을 생성해주겠습니다.
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: dev-access-role-binding
namespace: dev
## Role
roleRef:
kind: Role
name: dev-access-role
apiGroup: rbac.authorization.k8s.io
## Service Account
subjects:
- kind: Group
apiGroup: rbac.authorization.k8s.io
name: developer- 이제 aws-auth ConfigMap에 해당 IAM User를 추가해줍니다.
apiVersion: v1
data:
mapRoles: |
- groups:
- system:bootstrappers
- system:nodes
rolearn: arn:aws:iam::111111111111:role/eks_worker_role
username: system:node:{{EC2PrivateDNSName}}
mapUsers: |
- userarn: arn:aws:iam::680360122082:root
groups:
- system:masters
- userarn: arn:aws:iam::111111111111:user/developer_hongGu #이 부분을 추가해야합니다.
username: developer_hongGu
groups:
- developer
kind: ConfigMap- 이제 생성한 User에 Access Key와 Account Key를 사용해서 aws configure을 설정합니다.
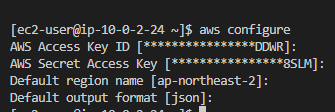
- 이제 dev namespace를 생성해주도록하겠습니다. Admin Instance에서 작업합니다.
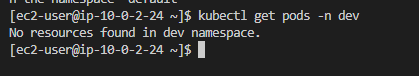
kubectl create namespace dev- 그럼 이제 aws configure을 설정한 Instance에서 dev에 대한 작업과 default에 대한 Namespace 작업을 2가지 진행해보겠습니다.
- default
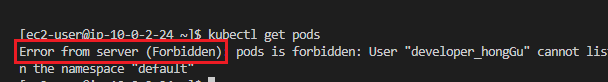
- dev(현재 dev namespace에 pod가 생성되있지 않아서 No resource가 뜨는 겁니다. 정상적으로 작동하는 것 입니다.)