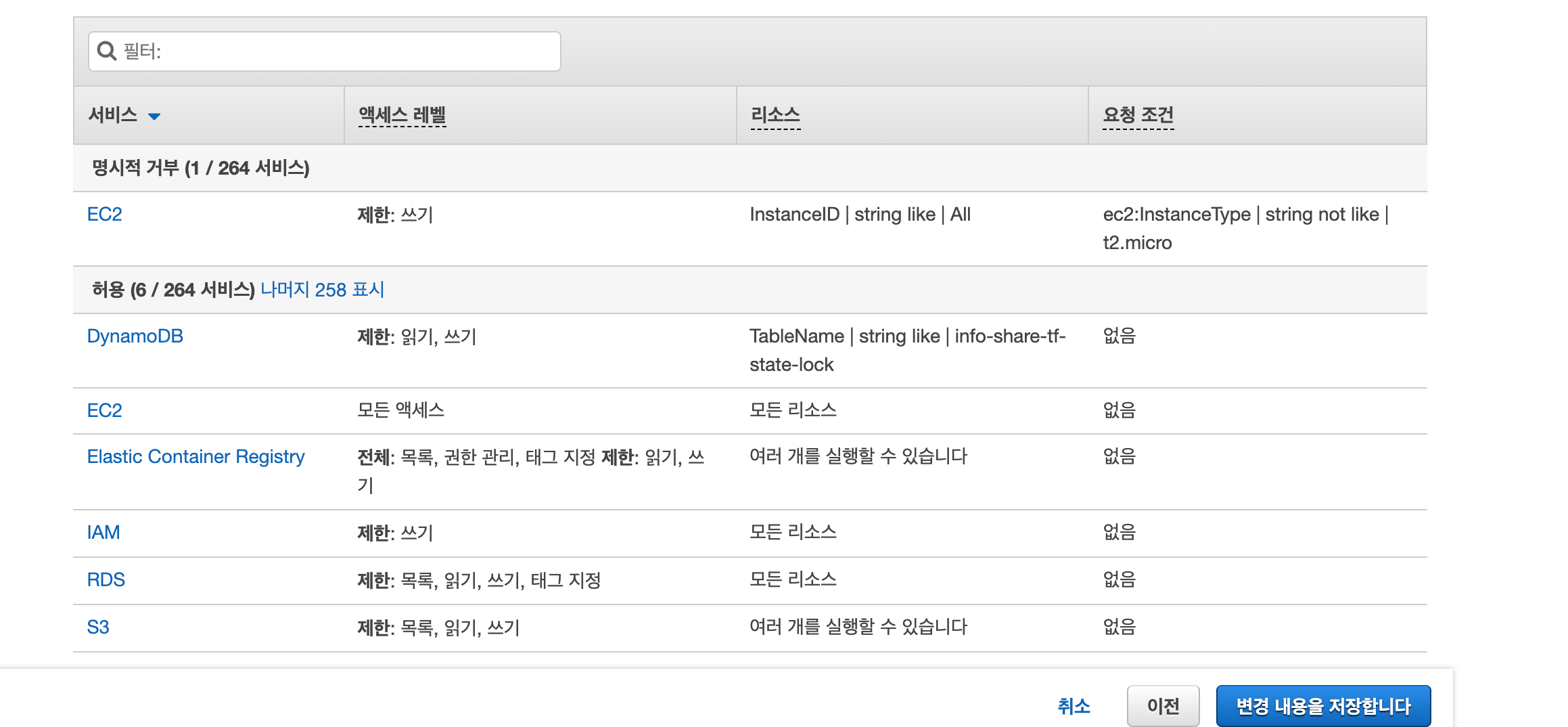
1. CI user 정책 update
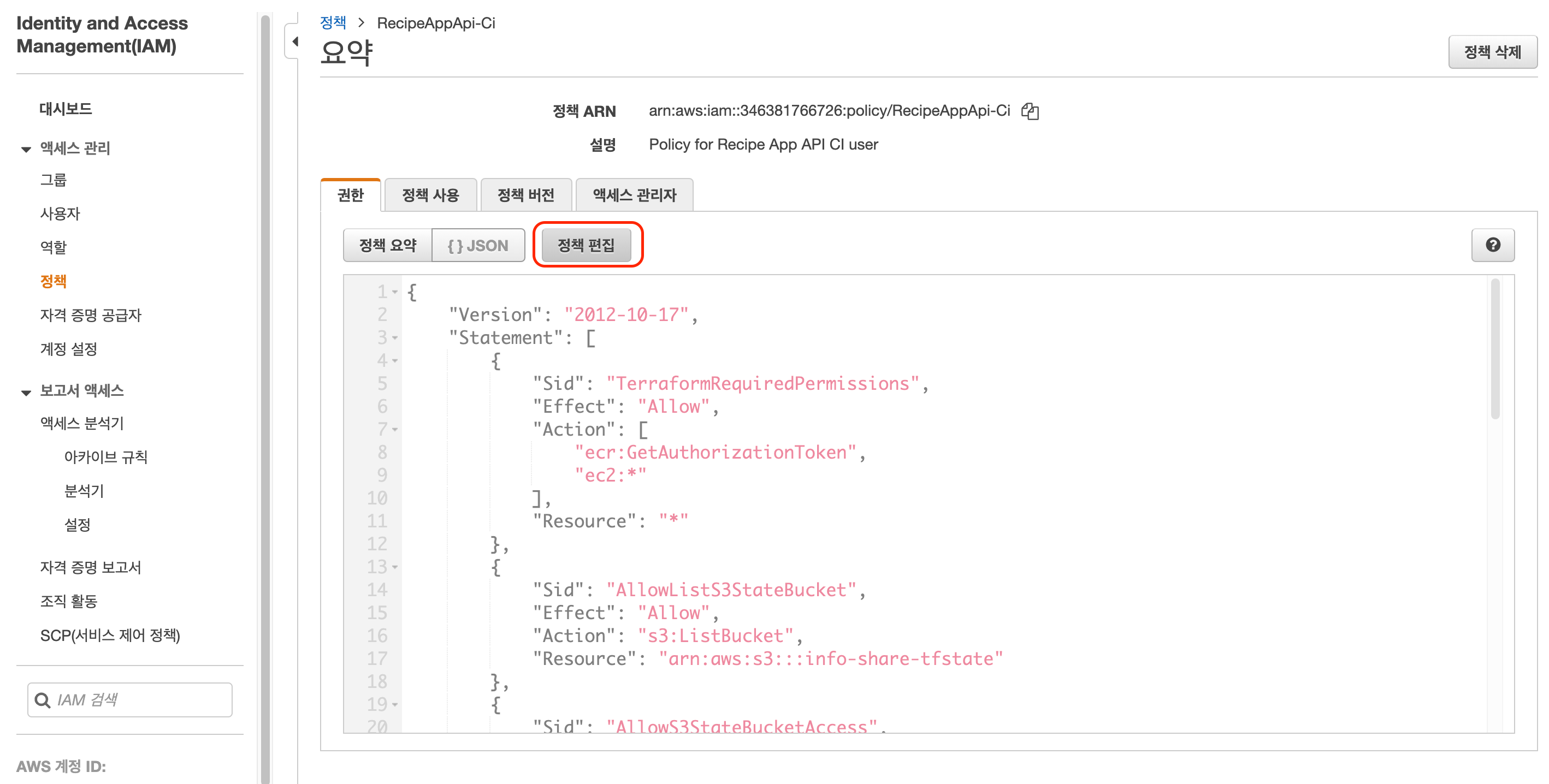
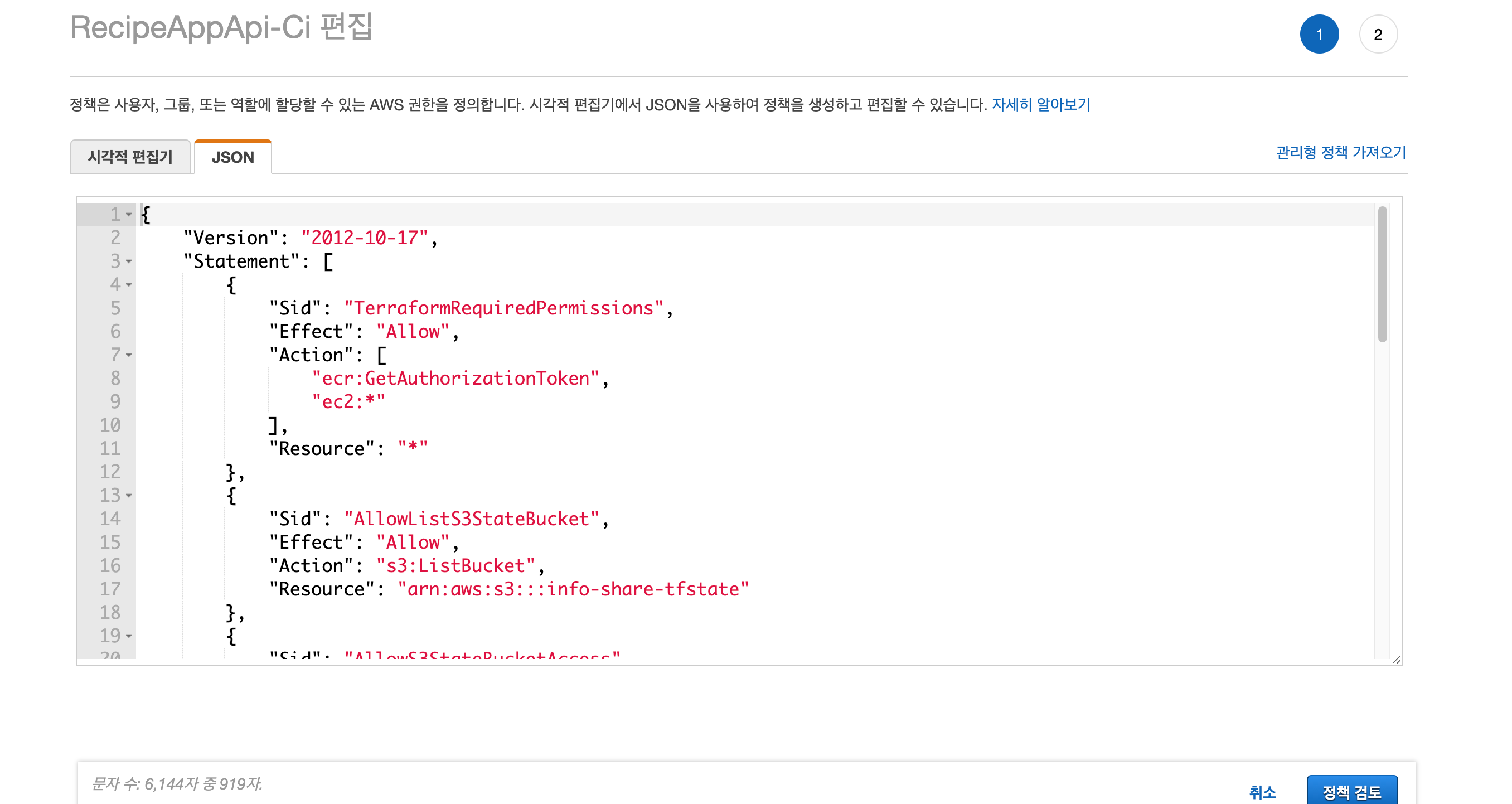
IAM -> User -> CI 관련 유저 선택 -> 정책편집 -> JSON
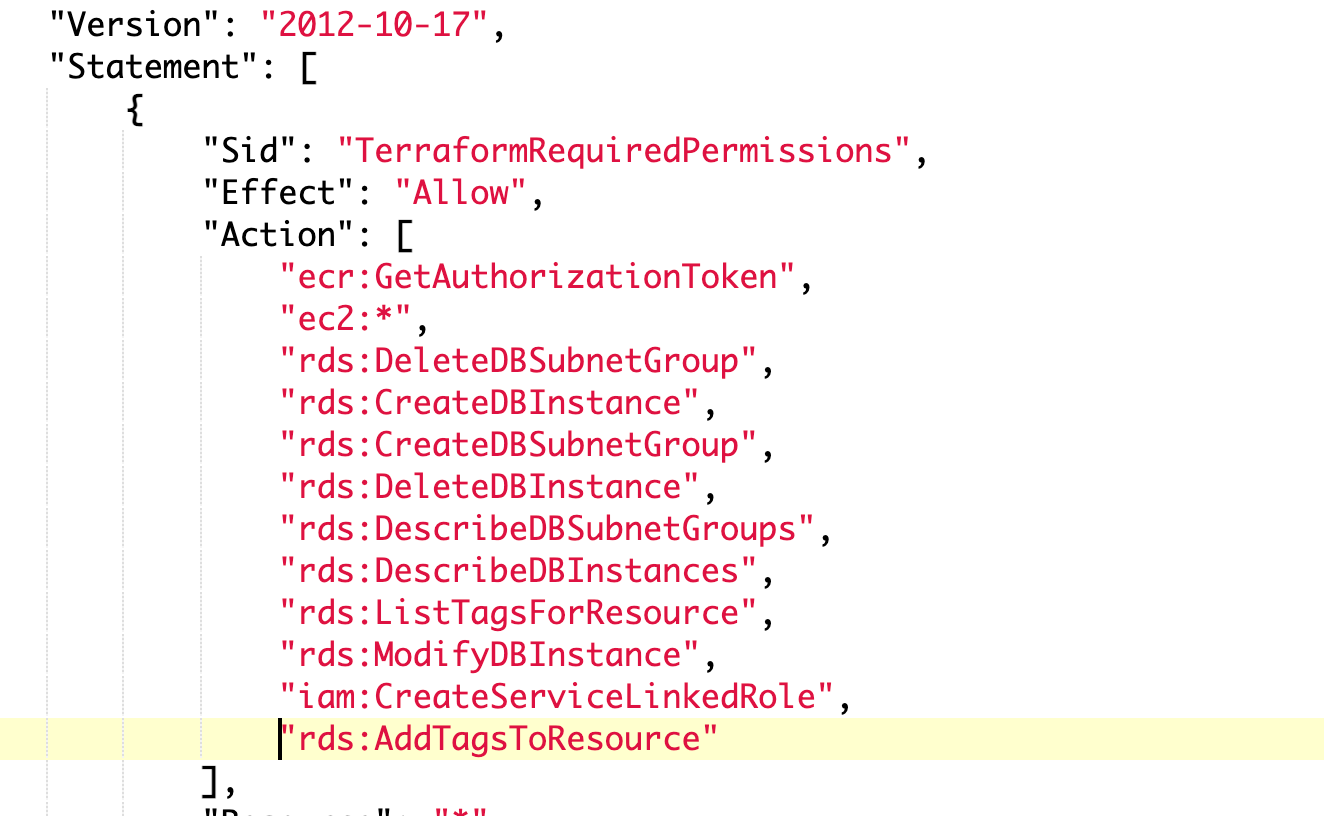
"rds:DeleteDBSubnetGroup",
"rds:CreateDBInstance",
"rds:CreateDBSubnetGroup",
"rds:DeleteDBInstance",
"rds:DescribeDBSubnetGroups",
"rds:DescribeDBInstances",
"rds:ListTagsForResource",
"rds:ModifyDBInstance",
"iam:CreateServiceLinkedRole",
"rds:AddTagsToResource"
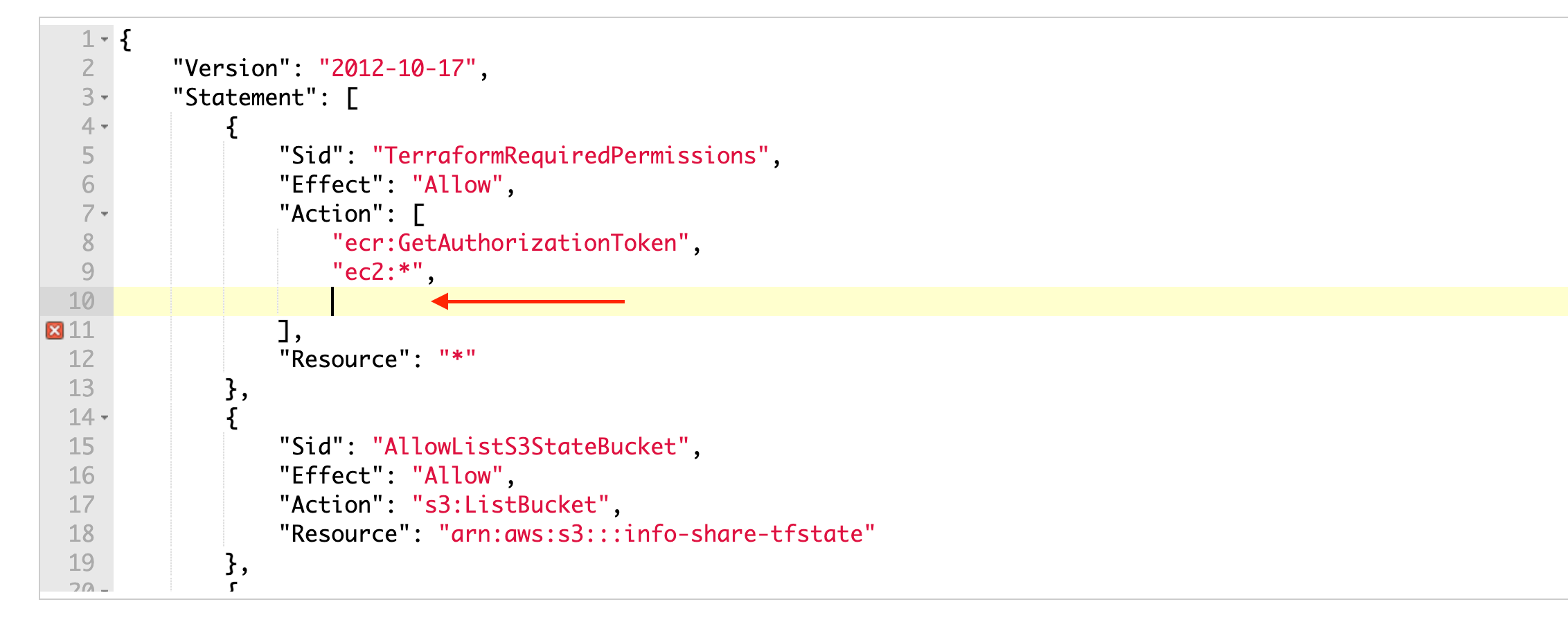
'정책 검토' 클릭
2. RDS 인스턴스 생성(feat.terraform)
- variable.tf 파일 추가
variable "db_username" {
description = "Username for the RDS postgres instance"
}
variable "db_password" {
description = "Password for the RDS postgres instance"
}- database.tf 파일 생성
resource "aws_db_subnet_group" "main" {
name = "${local.prefix}-main"
subnet_ids = [
aws_subnet.private_a.id,
aws_subnet.private_b.id
]
tags = merge(
local.common_tags,
map("Name", "${local.prefix}-main")
)
}
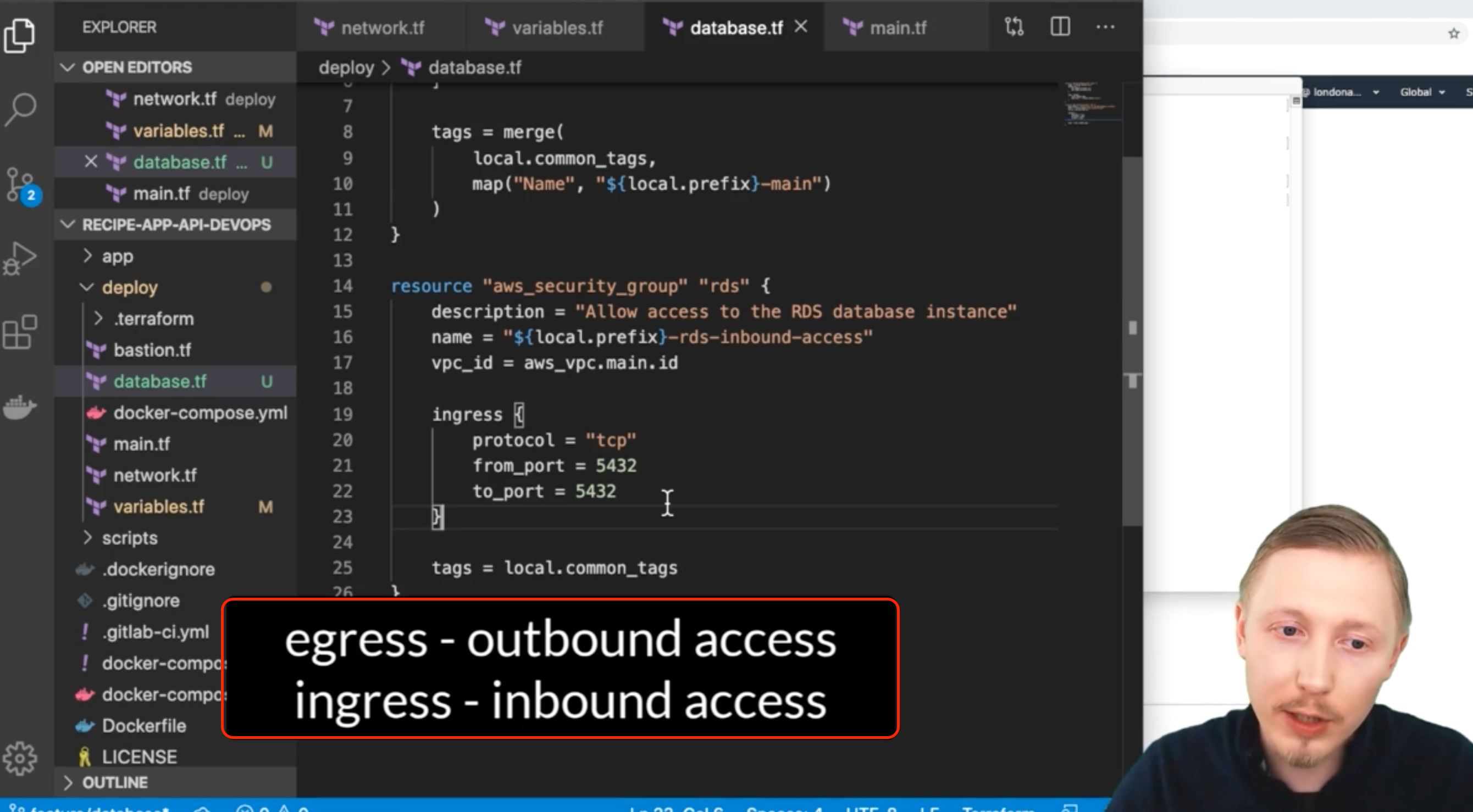
resource "aws_security_group" "rds" {
description = "Allow access to the RDS database instance"
name = "${local.prefix}-rds-inbound-access"
vpc_id = aws_vpc.main.id
ingress {
protocol = "tcp"
from_port = 5432
to_port = 5432
}
tags = local.common_tags
}
resource "aws_db_instance" "main" {
identifier = "${local.prefix}-db"
name = "recipe"
allocated_storage = 20
storage_type = "gp2"
engine = "postgres"
engine_version = "11.4"
instance_class = "db.t2.micro"
db_subnet_group_name = aws_db_subnet_group.main.name
password = var.db_password
username = var.db_username
backup_retention_period = 0
multi_az = false
skip_final_snapshot = true
vpc_security_group_ids = [aws_security_group.rds.id]
tags = merge(
local.common_tags,
map("Name", "${local.prefix}-main")
)
}
- outputs.tf
output "db_host" {
value = aws_db_instance.main.address
}terraform 자료:
https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/db_instance
