IDA로 파일을 열어보면 아래와 같이 [rbp+var4]가 5이면 flag_gen을 호출하고, 아니면 END하도록 만들어져있다.
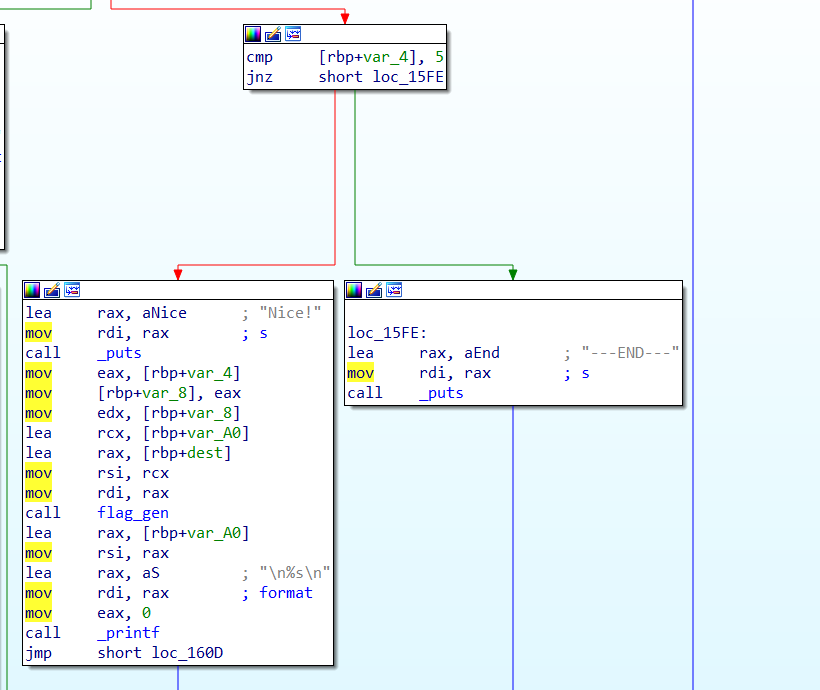
원래는 IDA에서 중단점을 잡고 실행해보려고 했는데 계속 안돼서 gdb로 진행해봤다!
disassemble
0x00000000000015aa <+278>: cmp DWORD PTR [rbp-0x4],0x5
0x00000000000015ae <+282>: jne 0x15fe <main+362>
0x00000000000015b0 <+284>: lea rax,[rip+0xa5f] # 0x2016
0x00000000000015b7 <+291>: mov rdi,rax
0x00000000000015ba <+294>: call 0x1090 <puts@plt>
0x00000000000015bf <+299>: mov eax,DWORD PTR [rbp-0x4]
0x00000000000015c2 <+302>: mov DWORD PTR [rbp-0x8],eax
0x00000000000015c5 <+305>: mov edx,DWORD PTR [rbp-0x8]
0x00000000000015c8 <+308>: lea rcx,[rbp-0xa0]
0x00000000000015cf <+315>: lea rax,[rbp-0x50]
0x00000000000015d3 <+319>: mov rsi,rcx
0x00000000000015d6 <+322>: mov rdi,rax
0x00000000000015d9 <+325>: call 0x11c9 <flag_gen>
0x00000000000015de <+330>: lea rax,[rbp-0xa0]
0x00000000000015e5 <+337>: mov rsi,rax
0x00000000000015e8 <+340>: lea rax,[rip+0xa2d] # 0x201c
0x00000000000015ef <+347>: mov rdi,rax
0x00000000000015f2 <+350>: mov eax,0x0
0x00000000000015f7 <+355>: call 0x10b0 <printf@plt>
0x00000000000015fc <+360>: jmp 0x160d <main+377>
0x00000000000015fe <+362>: lea rax,[rip+0xa1c] # 0x2021
0x0000000000001605 <+369>: mov rdi,rax
0x0000000000001608 <+372>: call 0x1090 <puts@plt>
0x000000000000160d <+377>: mov eax,0x0
0x0000000000001612 <+382>: leave
0x0000000000001613 <+383>: ret
End of assembler dump.따라서 run하기 전에 main+278에 중단점을 잡고 실행한다.
그러고 rbp-0x4에 5를 set하고 continue한다.
pwndbg> set *0x7fffffffe57c=5
pwndbg> c
Continuing.
Nice!
DH{389998e56e90e8eb34238948469cecd6dd89c04dce359c345e0b2f3ef9edc66a}
[Inferior 1 (process 42575) exited normally]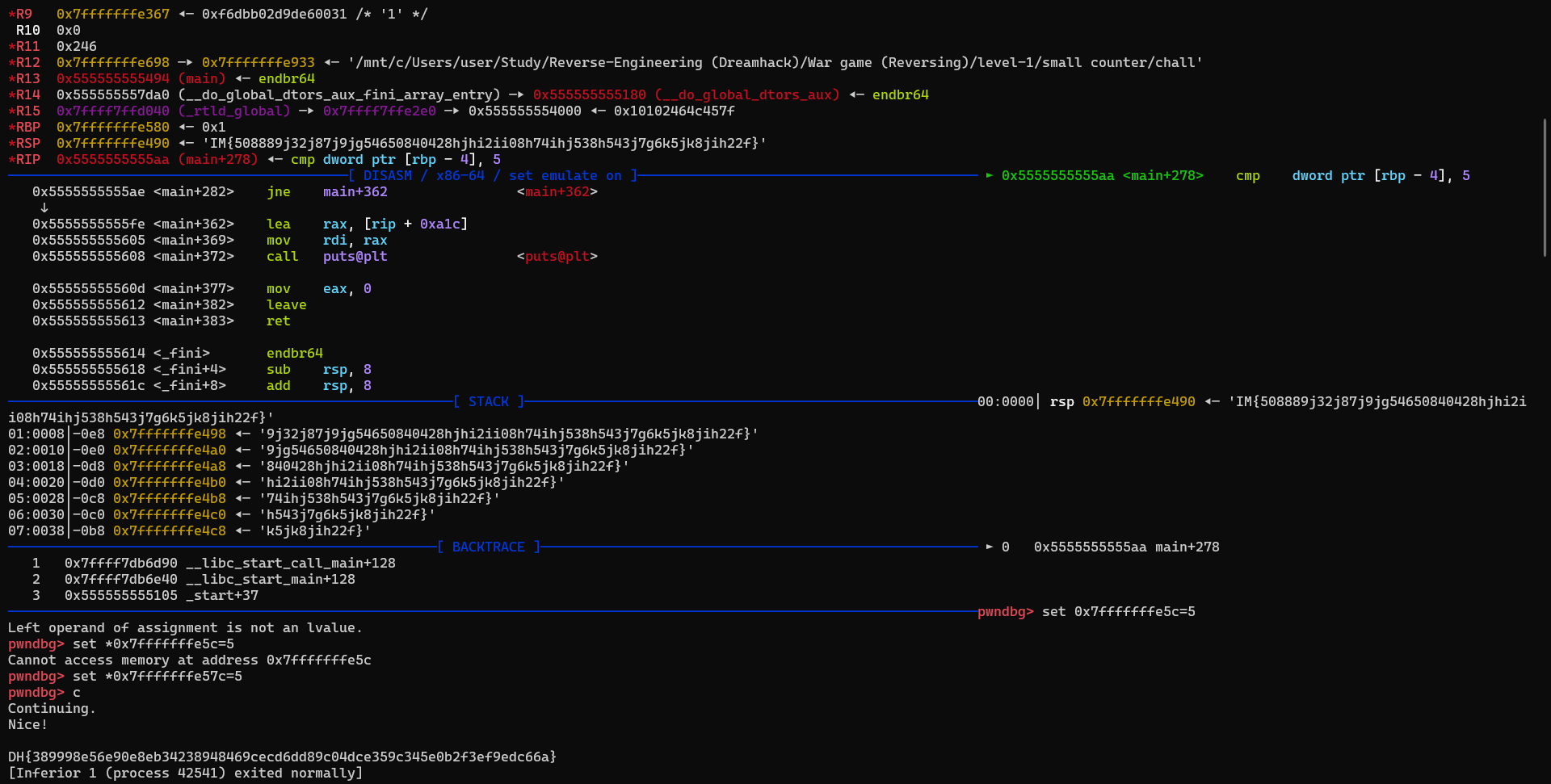
결과로 flag값을 찾을 수 있다!
