
토큰 기반 인증이란?
토큰(token)은 서버에서 클라이언트를 구분하기 위한 유일한 값이며 서버가 토큰을 생성해서 클라이언트에게 제공하면, 클라이언트는 이 토큰을 갖고 있다가 여러 요청을 이 토큰과 함께 신청한다.
서버는 토큰만 보고 유효한 사용자인지 검증하는 것을 토큰 기반 인증이라고 한다.
토큰을 전달하고 인증받는과정
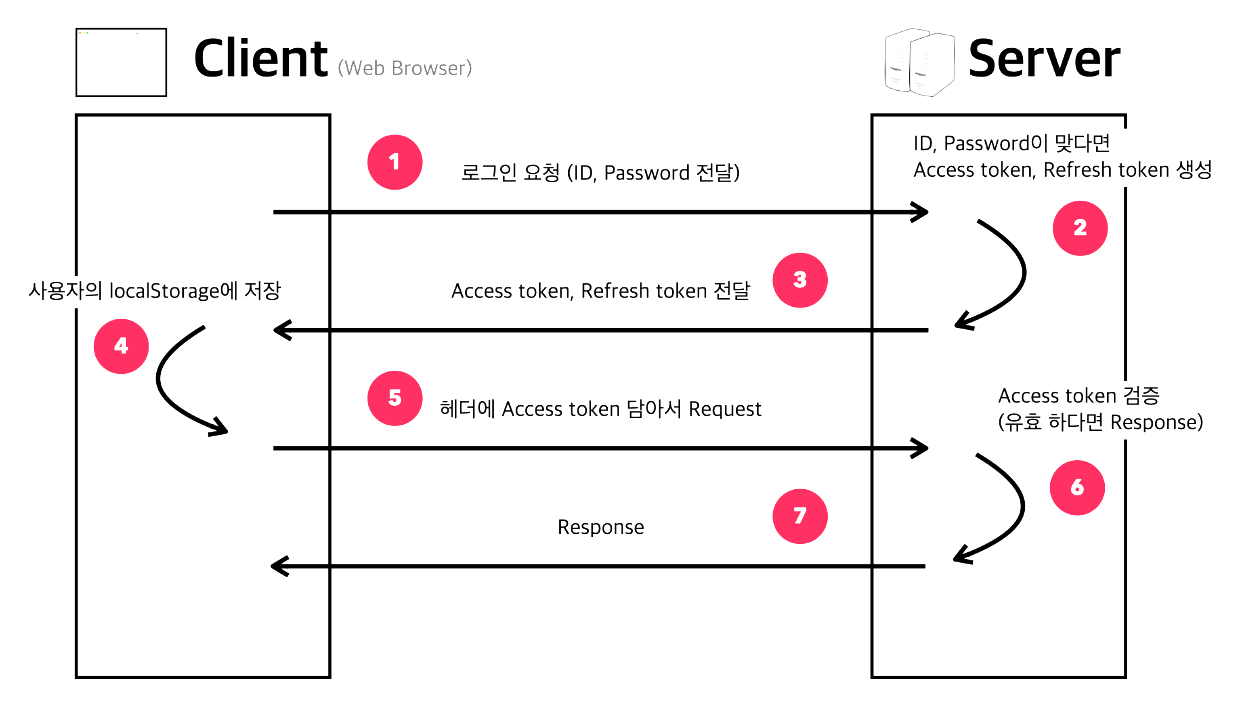
- 클라이언트가 ID와 Password를 서버에게 전달하면서 인증을 요청한다.
- 서버는 ID와 Password를 확인해 유효한 사용자인지 검증한다. 만약 유효한 사용자면 토큰(Access token, Refresh token)을 생성하여 응답한다.
- 클라이언트는 서버에서 준 토큰을 저장한다.
- 이후 인증이 필요한 API를 사용할 때 토큰(Access token)을 함께 보낸다.
- 서버는 토큰이 유효한지 검증한다.
- 토큰이 유효한다면 클라이언트가 요청한 내용을 처리한다.
토큰 기반 인증의 특징
- 무상태성
- 확장성
- 무결성
JWT
aaaaa(헤더) . bbbbb(내용) . cccccc(서명)
.기준으로 헤더(header), 내용(payload), 서명(signature)으로 이루어져 있다.
헤더(Header)
- 헤더(Header)는 토큰의 타입과 해싱 알고리즘을 지정하는 정보를 담는다.
- JWT 토큰, HS256 해싱 알고리즘을 사용한다는 내용이다.
// 토큰 타입과 해싱 알고리즘 예
{
"typ" : "JWT",
"alg" : "HS256"
}헤더(Header)의 구성
| 이름 | 설명 |
|---|---|
| typ | 토큰의 타입을 지정한다. JWT라는 문자열이 들어가게 된다. |
| alg | 해싱 알고리즘을 지정한다. |
내용(Payload)
- 토큰과 관련된 정보를 담는다.
- 내용의 한 덩어리를
클레임(Claim)이라고 부르며, 클레임은 키값의 한 쌍으로 이루어져 있다.
클레임(Claim)
- 등록된 클레임, 공개 클레임, 비공개 클레임으로 나눈다.
등록된 클레임(Registered claim)
등록된 클레임은 토큰에 대한 정보를 담는데 사용한다.
| 이름 | 설명 |
|---|---|
| iss | 토큰 발급자(issue) |
| sub | 토큰 제목(subject) |
| aud | 토큰 대상자(audience) |
| exp | 토큰의 만료 시간(expiration), 시간은 NumericDate 형식으로 하며, 항상 현재 시간 이후로 설정한다. |
| nbf | 토큰의 활성 날짜와 비슷한 개념으로, nbf는 Not Before를 의미한다. NumericDate 형식으로 날짜를 지정하며, 이 날짜가 지나기 전까지는 토큰이 처리되지 않는다. |
| iat | 토큰이 발급된 시간으로 iat은 issued at을 의미한다. |
| jti | jwt의 고유 식별자로서 주로 일회용 토큰에 사용한다. |
공개 클레임(public claim)
공개 클레임 은 공개되어도 상관없는 클레임을 의미한다.
- 충돌을 방지할 수 있는 이름을 가져야 한다.
- 보통 클레임 이름을 URI로 짓는다.
비공개 클레임(private claim)
비공개 클레임 은 공개되면 안되는 클레임을 의미한다.
- 클라이언트와 서버 간의 통신에 사용된다.
{
"iss" : "kkongdo@gmail.com", // 등록된 클레임
"iat" : 1622370878, // 등록된 클레임
"exp" : 1622372678, // 등록된 클레임
"https://kkongdo.com/jwt_claims/is_admin" : true,
"email" : "kkongdo@gmail.com",
"hello" : "안녕하세요!"
}iss, iat, exp는 JWT 자체에서 등록된 클레임이고, URL로 네이밍된 https://kkongdo.com/jwt_claims/is_admin은 공개 클레임이다. 그 외에 등록된 클레임도, 공개 클레임도 아닌 email과 hello는 비공개 클레임 값이다.
서명(Signature)
서명(Signature)는 해당 토큰이 조작되었거나 변경되지 않았음을 확인하는 용도로 사용하며, 헤더(Header)의 인코딩 값과 내용(Payload)의 인코팅값을 합친 후에 주어진 비밀키를 사용해서 해시값을 생성한다.
리프레쉬 토큰(Refresh token)
리프레쉬 토큰(Refresh token)은 사용자를 인증하기 위한 용도가 아닌 액세스 토큰이 만료되었을 때 새로운 액세스 토큰을 발급하기 위해 사용하는 토큰이다.
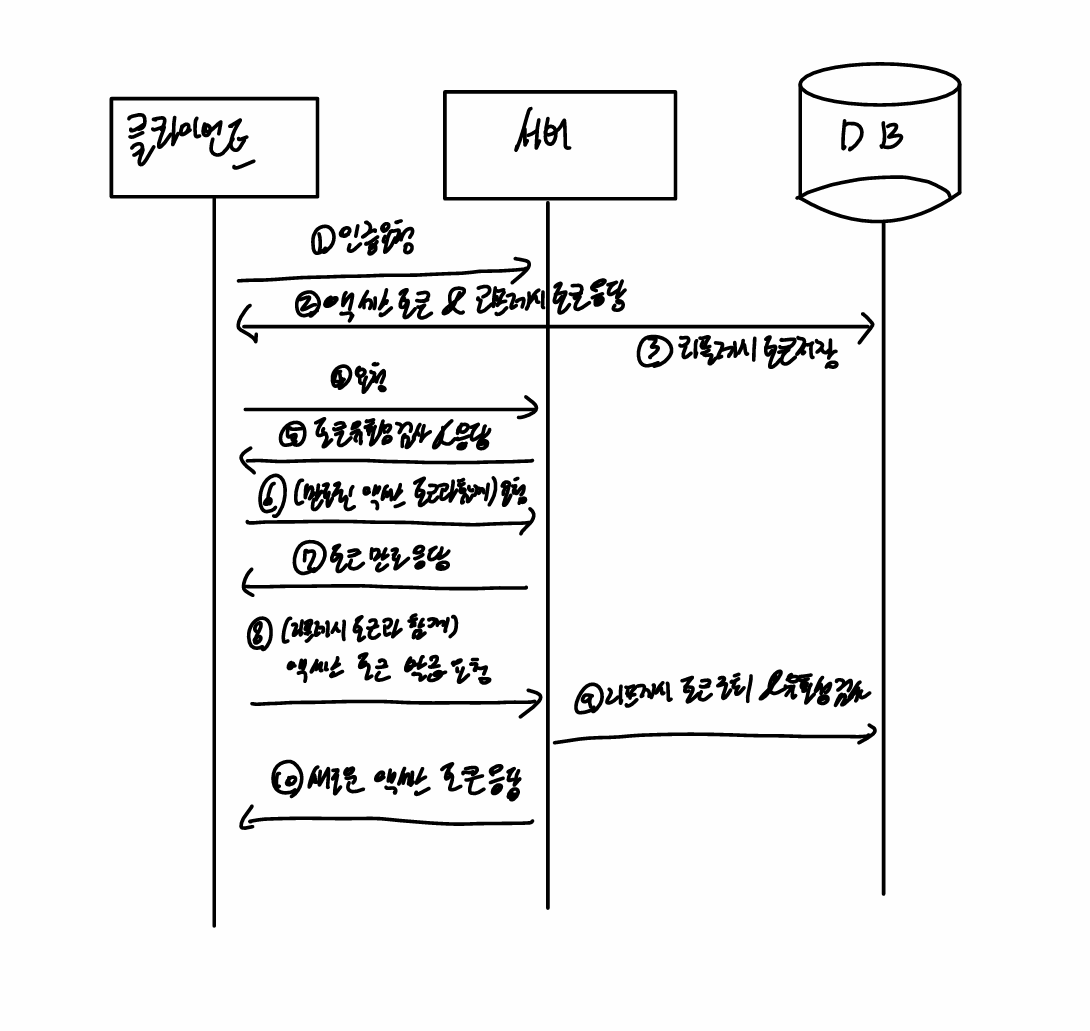
다음 절차를 차근히 따라와 보자🦾
- 1번 : 클라이언트가 서버에게 인증을 요청한다.
- 2번 : 서버는 클라이언트에서 전달한 정보를 바탕으로 인증 정보가 유효한지 확인한 뒤, 액세스 토큰과 리프레시 토큰을 만들어서 클라이언트에게 전달한다. 전달받은 클라이언트는 저장한다.
- 3번 : 서버에서 생성한 리프레시 토큰은 DB에도 저장해둔다.
- 4번 : 인증을 필요로 하는 API를 호출할 때 클라이언트에 저장된 액세스 토큰과 함께 API를 요청한다.
- 5번 : 서버는 전달받은 액세스 토큰이 유효한지 검사한 뒤에 유효하다면 클라이언트에서 요청한 내용을 처리한다.
- 6번 : 시간이 지나고 액세스 토큰이 만료된 뒤에는 클라리언트에서 원하는 정보를 얻기 위해 서버에게 API 요청을 보낸다.
- 7번 : 서버는 액세스 토큰이 유효한지 검사한다. 만약 만료된 토큰이면 유효하지 않기 때문에 토큰이 만료되었다는 에러를 전달한다.
- 8번 : 클라리언트는 이 응답을 받고 저장해둔 리프레시 토큰과 함께 새로운 액세스 토큰을 발급하는 요청을 전송한다.
- 9번 : 서버는 전달받은 리프레시 토큰이 유효한지, DB에서 리프세리 토큰을 조회한 후 저장해둔 리프레시 토큰과 같은지 확인한다.
- 10번 : 유효한 리프레시 토큰이라면 새로운 액세스 토큰을 생성한 뒤에 응답한다. 그 이후 클라이언트는 4번과 같이 다시 API를 요청한다.
구현 방법
1. 의존성 추가하기 (build.gradle)
// jwt 설정하기 위한 dependencies
implementation 'io.jsonwebtoken:jjwt:0.9.1'
implementation 'io.jsonwebtoken:jjwt-api:0.11.5'
runtimeOnly 'io.jsonwebtoken:jjwt-impl:0.11.5'
runtimeOnly 'io.jsonwebtoken:jjwt-jackson:0.11.5'
runtimeOnly 'io.jsonwebtoken:jjwt-gson:0.11.5'2. 토큰 제공자 추가하기
2-1. application.properties에 코드 추가하기
jwt.issuer=kkongdo@gmail.com
jwt.secret_key=study-springboot2-2 JwtProperties 생성 (해당 값들을 변수로 접근하는데 사용)
package com.springboot.springsecurity.config.jwt;
import lombok.Getter;
import lombok.Setter;
import org.springframework.boot.context.properties.ConfigurationProperties;
import org.springframework.stereotype.Component;
@Setter
@Getter
@Component
@ConfigurationProperties("jwt") // 자바 클래스에 프로퍼티값을 가져와서 사용하는 어노테이션이다.
public class JwtProperties {
private String issuer; // kkongdo@gmail.com이 들어간다.
private String secretKey; // study-springboot가 들어간다.
}2-3 TokenProvider 생성 (토큰을 생성하고 올바른 토큰인지 유효성 검사 및 토큰에서 필요한 정보 추출)
package com.springboot.springsecurity.config.jwt;
import io.jsonwebtoken.*;
import lombok.RequiredArgsConstructor;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import com.springboot.springsecurity.domain.User;
import org.springframework.stereotype.Service;
import java.time.Duration;
import java.util.Collections;
import java.util.Date;
import java.util.Set;
// 토큰을 생성하고 올바른 토큰인지 유효성 검사를 하고, 토큰에서 필요한 정보를 가져오는 클래스
@RequiredArgsConstructor
@Service
public class TokenProvider {
private final JwtProperties jwtProperties;
public String generateToken(User user, Duration expiredAt){
Date now = new Date();
return makeToken(new Date(now.getTime() + expiredAt.toMillis()), user);
}
// 1. JWT 토큰 생성 메서드
private String makeToken(Date expiry, User user){
Date now = new Date();
return Jwts.builder()
.setHeaderParam(Header.TYPE, Header.JWT_TYPE)
.setIssuer(jwtProperties.getIssuer()) // 발급자
.setIssuedAt(now) //발급날짜
.setExpiration(expiry) // 만료일
.setSubject(user.getEmail()) // 토큰 제목
.claim("id", user.getId()) // 클레임에 유저 id저장
.signWith(SignatureAlgorithm.HS256, jwtProperties.getSecretKey())
.compact();
}
// 2. JWT 토큰 유효성 검증 메서드
public boolean validToken(String token){
try{
Jwts.parser()
.setSigningKey(jwtProperties.getSecretKey()) //비밀키로 복호화
.parseClaimsJws(token);
return true;
}catch (Exception e){
return false;
}
}
// 3. 토큰 기반으로 인증 정보를 가져오는 메서드
public Authentication getAuthentication(String token){
Claims claims = getClaims(token);
Set<SimpleGrantedAuthority> authorities = Collections.singleton(new SimpleGrantedAuthority("ROLE_USER"));
return new UsernamePasswordAuthenticationToken(new org.springframework.security.core.userdetails.User(
claims.getSubject(), "", authorities),token, authorities);
}
// 4. 토큰 기반으로 유저 ID를 가져오는 메서드
public Long getUserId(String token){
Claims claims = getClaims(token);
return claims.get("id",Long.class);
}
private Claims getClaims(String token) {
return Jwts.parser() // 클레임 조회
.setSigningKey(jwtProperties.getSecretKey())
.parseClaimsJws(token)
.getBody();
}
}
3. 리프레쉬 토큰 도메인 생성
package com.springboot.springsecurity.domain;
import jakarta.persistence.*;
import lombok.AccessLevel;
import lombok.Getter;
import lombok.NoArgsConstructor;
@Getter
@Entity
@NoArgsConstructor(access = AccessLevel.PROTECTED)
public class RefreshToken {
@Id
@GeneratedValue(strategy = GenerationType.IDENTITY)
@Column
private Long id;
@Column(name = "user_id", nullable = false, unique = true)
private Long userId;
@Column(name = "refresh_token", nullable = false)
private String refreshToken;
public RefreshToken(Long userId, String refreshToken){
this.userId = userId;
this.refreshToken = refreshToken;
}
public RefreshToken update(String newRefreshToken){
this.refreshToken = newRefreshToken;
return this;
}
}
4. 토큰 필터 생성
package com.springboot.springsecurity.config;
import com.springboot.springsecurity.config.jwt.TokenProvider;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import lombok.RequiredArgsConstructor;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@RequiredArgsConstructor
public class TokenAuthenticationFilter extends OncePerRequestFilter {
private final TokenProvider tokenProvider;
private final static String HEADER_AUTHORIZATION = "Authorization";
private final static String TOKEN_PREFIX = "Bearer";
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain filterChain) throws ServletException, IOException {
// 요청 헤더의 Authorization 키와 값을 조회한다.
String authorizationHeader = request.getHeader(HEADER_AUTHORIZATION);
// 가져온 값에서 접두사 제거한다.
String token = getAccessToken(authorizationHeader);
// 가져온 토큰이 유효한지 확인 및 유효한 때는 인증 정보 설정을 한다.
if(tokenProvider.validToken(token)){
Authentication authentication = tokenProvider.getAuthentication(token);
SecurityContextHolder.getContext().setAuthentication(authentication);
}
filterChain.doFilter(request, response);
}
private String getAccessToken(String authorizationHeader) {
if(authorizationHeader != null && authorizationHeader.startsWith(TOKEN_PREFIX)){
return authorizationHeader.substring(TOKEN_PREFIX.length());
}
return null;
}
}
5. 토큰 API 구현
- 리프레쉬 토큰을 전달받아 검증하고, 유효한 리프세시 토큰이라면 새로운 액세스 토큰을 생성하는 토큰 API를 구현해보겠다.
5-1. UserService에 유저 ID로 유저를 검색해서 전달하는 findById() 메서드 추가
package com.springboot.springsecurity.service;
import com.springboot.springsecurity.domain.User;
import com.springboot.springsecurity.dto.AddUserRequest;
import com.springboot.springsecurity.repository.UserRepository;
import lombok.RequiredArgsConstructor;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.stereotype.Service;
@Service
@RequiredArgsConstructor
public class UserService {
private final UserRepository userRepository;
private final BCryptPasswordEncoder bCryptPasswordEncoder;
public Long save(AddUserRequest dto) {
return userRepository.save(User.builder()
.email(dto.getEmail())
// 패스워드 암호화
.password(bCryptPasswordEncoder.encode(dto.getPassword()))
.build()).getId();
}
public User findById(Long userId) {
return userRepository.findById(userId).orElseThrow(() -> new IllegalArgumentException("UnExpected user"));
}
}5-2. RefreshTokenService 생성
- 전달받은 리프레시 토큰으로 리프레시 토큰 객체를 검색해서 전달하는 메서드를 만든다.
package com.springboot.springsecurity.service;
import com.springboot.springsecurity.domain.RefreshToken;
import com.springboot.springsecurity.repository.RefreshTokenRepository;
import lombok.RequiredArgsConstructor;
import org.springframework.stereotype.Service;
@Service
@RequiredArgsConstructor
public class RefreshTokenService {
private final RefreshTokenRepository refreshTokenRepository;
public RefreshToken findByRefreshToken(String refreshToken) {
return refreshTokenRepository.findByRefreshToken(refreshToken).orElseThrow(() -> new IllegalArgumentException("Unexpected toekn"));
}
}
5-3. TokenService 생성
- createNewAccessToken() 메서드를 만들어서 전달받은 리프레시 토큰으로 토큰 유효성을 검사하고 유효한 토큰일 때는 리프레시 토큰으로 사용자 ID를 찾는다.
- 이후 사용자 ID로 사용자를 찾은 후에 토큰 제공자 generateToken() 메서드를 호출해서 새로운 액세스 토큰을 생성한다.
package com.springboot.springsecurity.service;
import com.springboot.springsecurity.config.jwt.TokenProvider;
import com.springboot.springsecurity.domain.User;
import lombok.RequiredArgsConstructor;
import org.springframework.stereotype.Service;
import java.time.Duration;
@Service
@RequiredArgsConstructor
public class TokenService {
private final TokenProvider tokenProvider;
private final RefreshTokenService refreshTokenService;
private final UserService userService;
public String createNewAccessToken(String refreshToken) throws IllegalAccessException {
// 토큰 유효성 검사에 실패하면 예외 발생
if(!tokenProvider.validToken(refreshToken)){
throw new IllegalAccessException("Unexpected token");
}
Long userId = refreshTokenService.findByRefreshToken(refreshToken).getUserId();
User user = userService.findById(userId);
return tokenProvider.generateToken(user, Duration.ofHours(2));
}
}6. 토큰을 발급받는 API 생성
6-1. 토큰 생성 요청 CreateAccessTokenRequest와 토큰 생성 응답 CreateAccessTokenResponse를 만든다.
package com.springboot.springsecurity.dto;
import lombok.Getter;
import lombok.Setter;
@Getter
@Setter
public class CreateAccessTokenRequest {
private String refreshToken;
}
package com.springboot.springsecurity.dto;
import lombok.AllArgsConstructor;
import lombok.Getter;
@Getter
@AllArgsConstructor
public class CreateAccessTokenResponse {
private String accessToken;
}
6-2. TokenApiController 구현
- Post 요청이 오면 토큰 서비스에서 리프레시 토큰을 기반으로 새로운 액세스 토큰을 만들어준다.
package com.springboot.springsecurity.controller;
import com.springboot.springsecurity.dto.CreateAccessTokenRequest;
import com.springboot.springsecurity.dto.CreateAccessTokenResponse;
import com.springboot.springsecurity.service.TokenService;
import lombok.RequiredArgsConstructor;
import org.springframework.http.HttpStatus;
import org.springframework.http.ResponseEntity;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RestController;
@RequiredArgsConstructor
@RestController
public class TokenApiController {
private final TokenService tokenService;
@PostMapping("/api/token")
public ResponseEntity<CreateAccessTokenResponse> createNewAccessToken(@RequestBody CreateAccessTokenRequest request) throws IllegalAccessException {
String newAccessToken = tokenService.createNewAccessToken(request.getRefreshToken());
return ResponseEntity.status(HttpStatus.CREATED).body(new CreateAccessTokenResponse(newAccessToken));
}
}
그럼 어디에 JWT는 어디에서 언제 사용이 될까?🧐
JWT(JSON Web Token)는 주로 인증 및 정보 교환 목적으로 사용되는 토큰 기반의 인증 메커니즘이기 때문에 클라이언트와 서버 간의 신뢰할 수 있는 정보 교환을 위해 사용된다.
사용자 인증 (Authentication)
사용자 로그인 후 서버는 사용자 정보를 기반으로 JWT를 생성하여 클라이언트에게 전달한다. 이후 클라이언트는 해당 JWT를 요청 헤더에 포함시켜 서버에 요청을 보낸다. 서버는 JWT를 검증하여 사용자를 인증한다.
권한 부여 (Authorization)
JWT는 사용자의 권한 정보를 포함할 수 있기 때문에 따라서 서버는 JWT를 통해 클라이언트의 권한을 확인하고, 특정 자원에 대한 접근을 허용하거나 제한할 수 있다.
정보 교환
JWT는 신뢰할 수 있는 정보 교환을 위해 사용된다.
그러므로 서버 간에 사용자 정보나 설정 데이터를 주고 받을 때 JWT를 사용하면 데이터의 무결성을 보장할 수 있다.
결론
JWT는 신뢰할 수 있는 정보 교환을 위해 사용된다. 예를 들어, 서버 간에 사용자 정보나 설정 데이터를 주고 받을 때 JWT를 사용하면 데이터의 무결성을 보장할 수 있을 것 같다.
참고문헌 및 교재📒
https://joie-kim.github.io/JWT-Auth/
스프링 부트 3 백엔드 개발자 되기: 자바 편 - 신선영 -
하... 이메일 가입 딱 기다려 이거 보고 구현한다.