System Hacking
1.Background : Computer Architecture

Background : Computer Architecture
2.Background : Linux Memory Layout

Background : Linux Memory Layout
3.x86 Assembly : Essential Part(1)

x86 Assembly : Essential Part(1)
4.x86 Assembly : Essential Part(2)

x86 Assembly : Essential Part(2)
5.Tool : gdb

Tool : gdb
6.Exploit Tech : Shellcode - orw

Exploit Tech : Shellcode - orw
7.Exploit Tech : Shellcode - execve

Exploit Tech : Shellcode - execve
8.Tool : pwntools

Tool : pwntools
9.Background : Calling Convention

Background : Calling Convention
10.Memory Corruption : Stack Buffer Overflow

Memory Corruption : Stack Buffer Overflow
11.Mitigation : Stack Canary

Mitigation : Stack Canary
12.Exploit Tech : Return to Shellcode

Exploit Tech : Return to Shellcode
13.Mitigation : NX & ASLR

Mitigation : NX & ASLR
14.Background : Library

Background : Library
15.Exploit Tech : Return to Library

Exploit Tech : Return to Library
16.Exploit Tech : Return Oriented Programming

Exploit Tech : Return Oriented Programming
17.Background : RELRO

Background : RELRO
18.Background : PIE

Background : PIE
19.Exploit Tech : Hook Overwrite
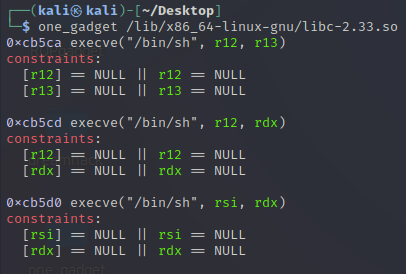
Exploit Tech : Hook Overwrite
20.Memory Corruption : Out of Bounds

Memory Corruption : Out of Bounds
21.Exploit Tech : Format String Bug

Exploit Tech : Format String Bug
22.Memory Corruption : Use After Free

Memory Corruption : Use After Free
23.Background : ptmalloc2

Background : ptmalloc2
24.Memory Corruption : Double Free Bug

Memory Corruption : Double Free Bug
25.Exploit Tech: Use After Free

Exploit Tech: Use After Free
26.DreamHack - System Hacking (진행중)

DreamHack - System Hacking (진행중)
27.System Hacking - 유용한 모음집

System Hacking - 유용한 모음집