[요약]
Cyber-security researchers at NVISO observed a campaign by North Korean-linked threat actors associated with the operation dubbed contagious interview.
These actors are using public JSON storage services such as JSON Keeper, JSON Silo, and npoint.io to host malicious payloads and deliver malware covertly.
How It works
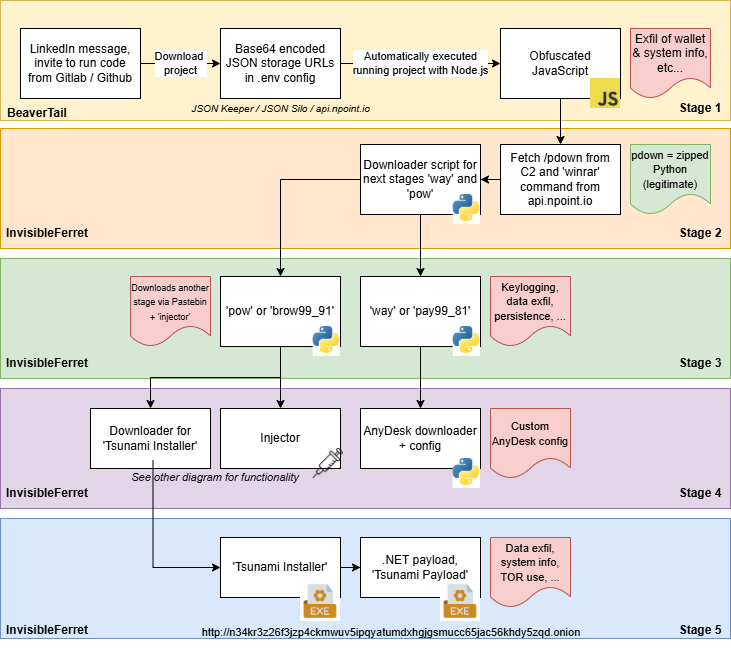
1. The attackers make contact on professional networking platforms (for example, LinkedIn) under the guise of collaborating on a project or conducting a “job assessment”.
The Hacker News
2. Targets are instructed to download a “demo project” from a legitimate code‐repository platform (e.g., GitHub, GitLab).
The Hacker News
3. Within that project is a file (e.g., server/config/.config.env) containing a Base64-encoded string that appears like an API key but actually points to the JSON storage service where the next‐stage payload is hidden.
The Hacker News
4. The payload in one example is a JavaScript malware named BeaverTail, which then installs a Python backdoor called InvisibleFerret.
The Hacker News
5. Additionally, the campaign fetches another toolkit called TsunamiKit (previously observed in September 2025) that can fingerprint systems, collect data, and fetch further payloads from a hidden (“.onion”) address
JSON Keeper
JSON Keeper is a free, public online service that lets users store and share small pieces of JSON data.
article from: https://thehackernews.com/2025/11/north-korean-hackers-turn-json-services.html
