TIL: Authentication/Authorization
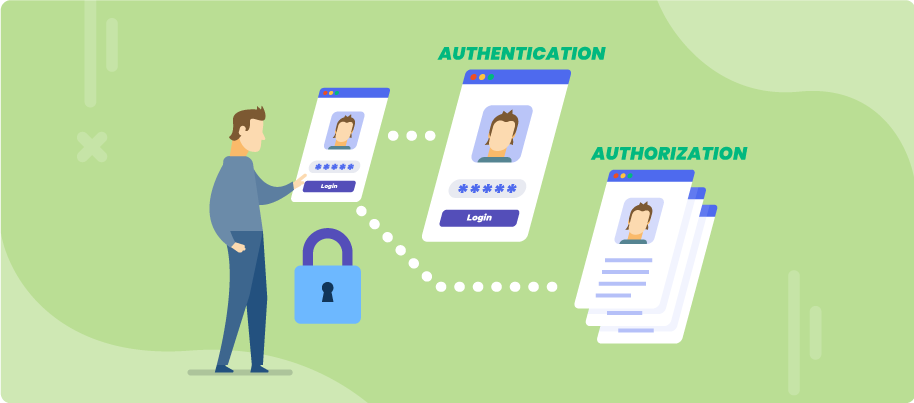
TIL I learned about authentication and authorization, two key features of APIs (both public and private). Since authentication and authorization are used extensively in web-based applications, I thought it'd be a good idea to write a short blogpost on the differences between the two and the reasons why we use them 🤗
Authentication vs authorization... What's the difference? 🤔
Authentication is used to verify the identity of a user. Most websites and applications have login features that prompt users to enter their username and password. Once these fields are entered, an HTTP request is sent to verify whether the submitted username and password match the username and password stored in the database. If there is a match, the user's identity is confirmed and authentication is complete. If there is not a match, the user's identitiy is not confirmed, and an HTTP status=401 error message is sent.
Authorization is used to verify whether a user is allowed access to different features or information offered by a website. Some websites only grant access to their services to paid users. For example, Instagram only allows users who are logged to view stories and comment on posts. Netflix only allows users who have paid subscriptions to view movies and shows. Authorization is therefore a key feature of most websites, since most websites limit their services to a select group of users.
A deeper dive 🧜 into... Authentication
TIL I learned that passwords and private user information must be encrypted before being stored in a database. If a database is leaked and passwords are not encrypted prior to storing, then users are vulnerable to outside attacks. For example, if a user uses the same username-password pair for many different services, then a hacker could gain access to private information, including access to bank accounts 😳. In order to encrypt user passwords effectively, salting and key stretching are used. At the very least, encrypting passwords buys users time to change their passwords for other services, since decrypting encrypted passwords takes time.
Strings vs Bytes
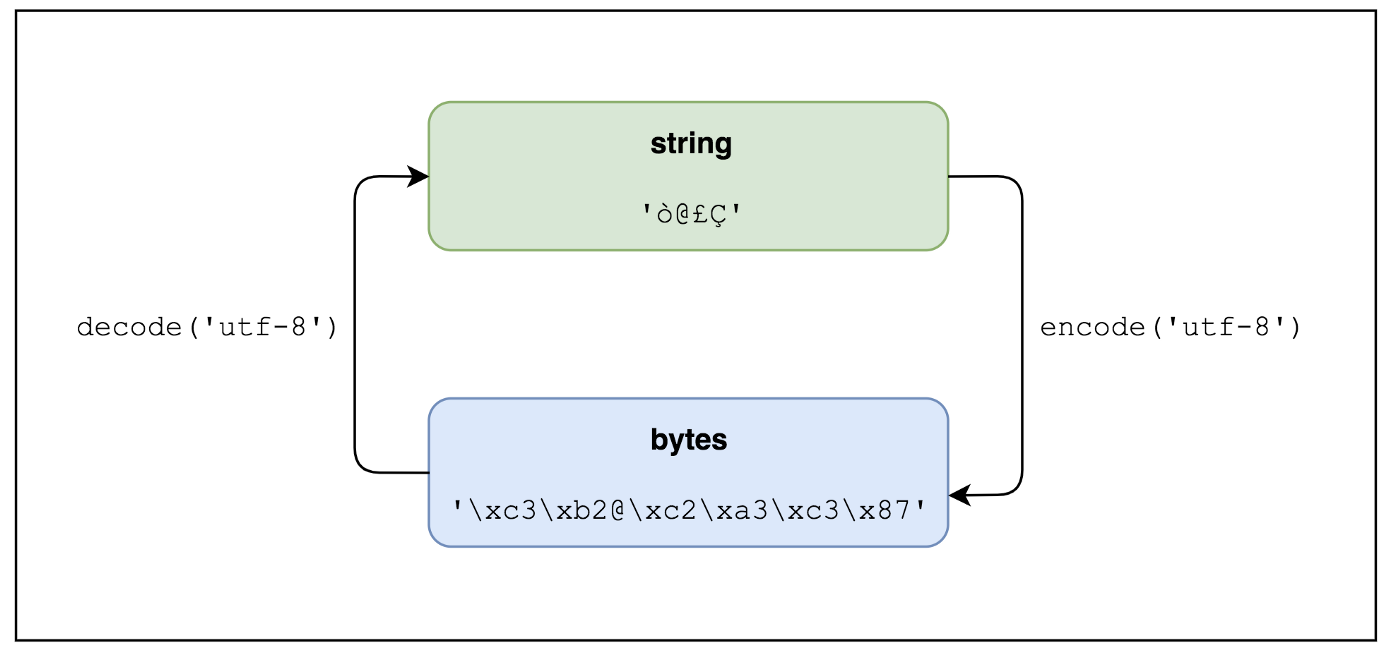
TIL that all data is stored in a computer as bits (1s and 0s). All letters and characters can thus be broken down into bytes (groups of bits usually stored as 8-bit or 4-bit). All characters known to man are mapped to different sets of codepoints (hexidecimal number that represents a symbol) using Unicode, which is a universally accepted convention. These codepoints are then converted to bytes using different encoding methods, with utf-8 being the most commonly used method. In python, strings can be encoded into bytes using the encode() method, and bytes can be decoded into strings using the decode() method. This is super important to remember -- in order to hash (encrypt) passwords, password strings must be encoded into bytes.
Hashing

Passwords are encrypted using a one-way hash function. One-way hash functions convert password strings into encrypted messages. These functions are called one-way hash functions because they can only be converted in one direction. In other words, hackers cannot decipher user passwords using the corresponding encrypted messages. However, the risk of using these one-way hash functions is that the same password string will result in the same encrypted message. Hackers thus create "rainbow tables," which are tables of commonly used passwords (i.e. 1234, password, 0000) hashed into encrypted messages. That's why it's so important to use unique, long, and complex passwords that are probably not yet stored on these "rainbow tables."
Salting

In order to prevent malicious hackers from accessing user passwords using rainbow tables salting is used to add random complexity to passwords. Salting involves sprinkling randomly generated data on user passwords (like salt bae!). The password+salt is then encrypted using a one-way hash function. This adds increased complexity to the encrypted password that is then stored in the database.
Key Stretching
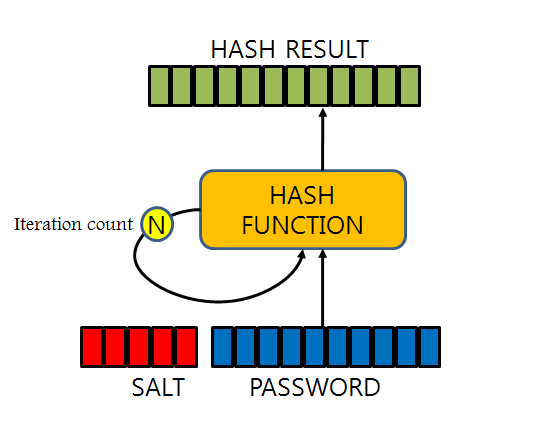
Once you hash the password, re-hash the hashed password, re-hash the re-hashed password, and repeat multiple times to further increase the complexity of the encrypted password. This makes it even more difficult to decipher encrypted passwords using rainbow tables.

I recently got the chance to use the Protectimus On-Premise MFA platform, and I'm beyond impressed. The flexibility of being able to deploy it either on-premises or in a private cloud adds a layer of convenience that aligns with our organization's requirements. The easy integration with various systems such as programmable MFA device Active Directory, and more is a testament to its versatility. What truly stands out is the dynamic strong password authentication feature, which enhances security significantly. It's evident that Protectimus takes security seriously, and their on-premise MFA platform is a prime example of their commitment.