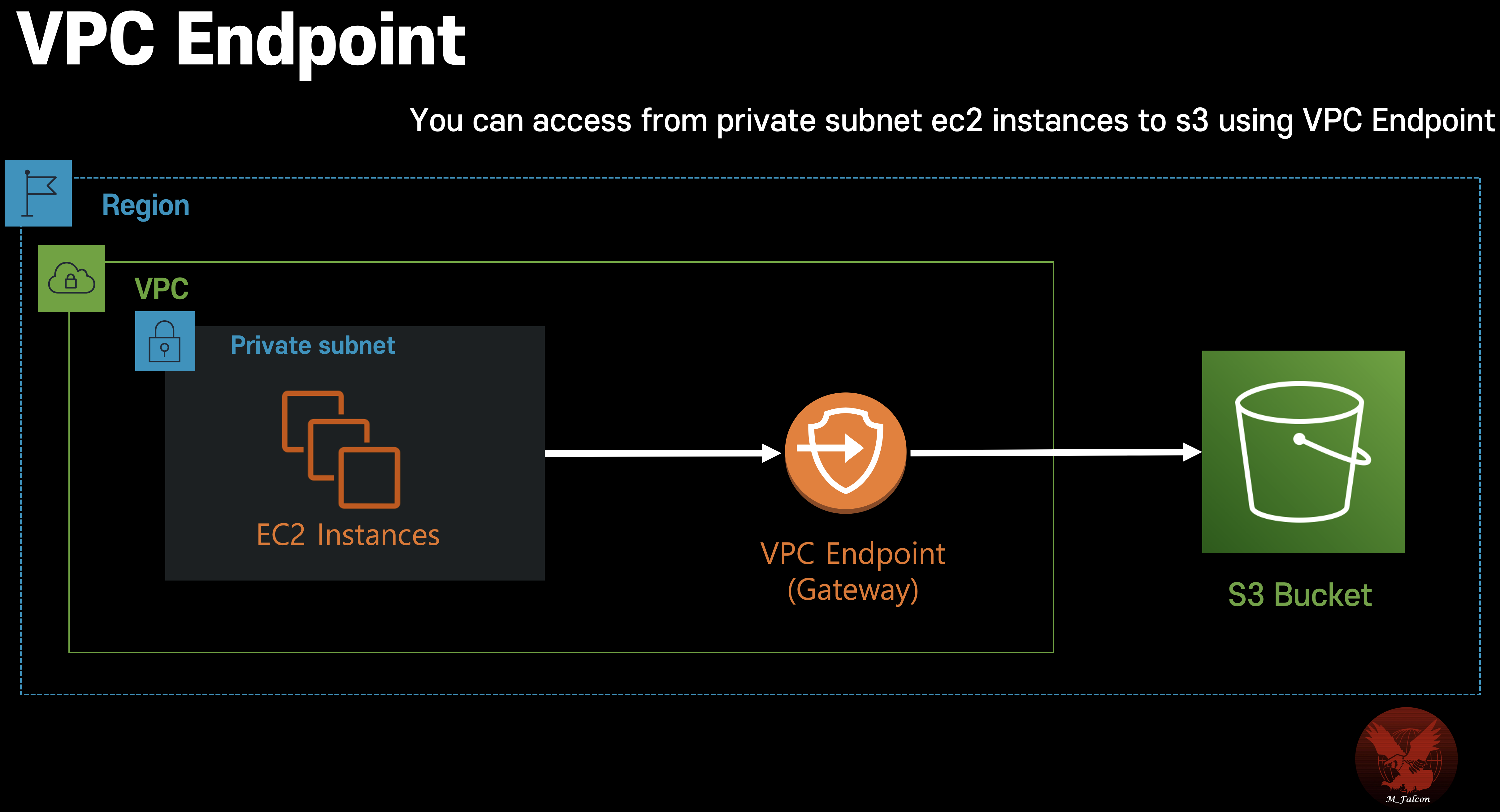
VPC Endpoint
All AWS resources have public URL
but you want use it without public endpoints url
then, use VPC Endpoints!
When to use
- Use DyanmoDB or S3 in private URL by Gateway Endpoint
- Use AWS resources in private network (ENI, Elastic Network Interface) without public URL
Why to use
- No need to public IP Address
- No need Internet gateway, NAT gateway
- Reduce administrative overhead and cost \
private network traffic is half of public one.
(S3 to Internet is $0.09 per GB)
💰 Compare price
When transfer data from EC2 instance to S3
| NAT Gateway | VPC Gateway Endpoint |
|---|---|
| 0.045$ per GB (NAT Gatewa data processed) 0.09$ per GB(Data transfer cross-region) Free (Data trasnfer same-region) | $0.01 (Data trasfer same-region) |
Type of Interface
| Interface Endpoint | Gateway Endpoint |
|---|---|
| Almost all resources | DynamoDB, S3 |
| Use ENI gateway | Most AWS services |
How to use
-
Create VPC Link
Select AWS service to connect with private network -
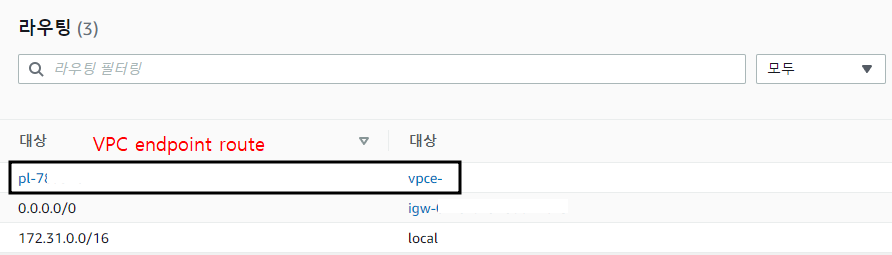
Check Route table
Some traffic should be forwarded by VPC endpoint configuration in route table.
-
Check IAM role
For resource.
Example
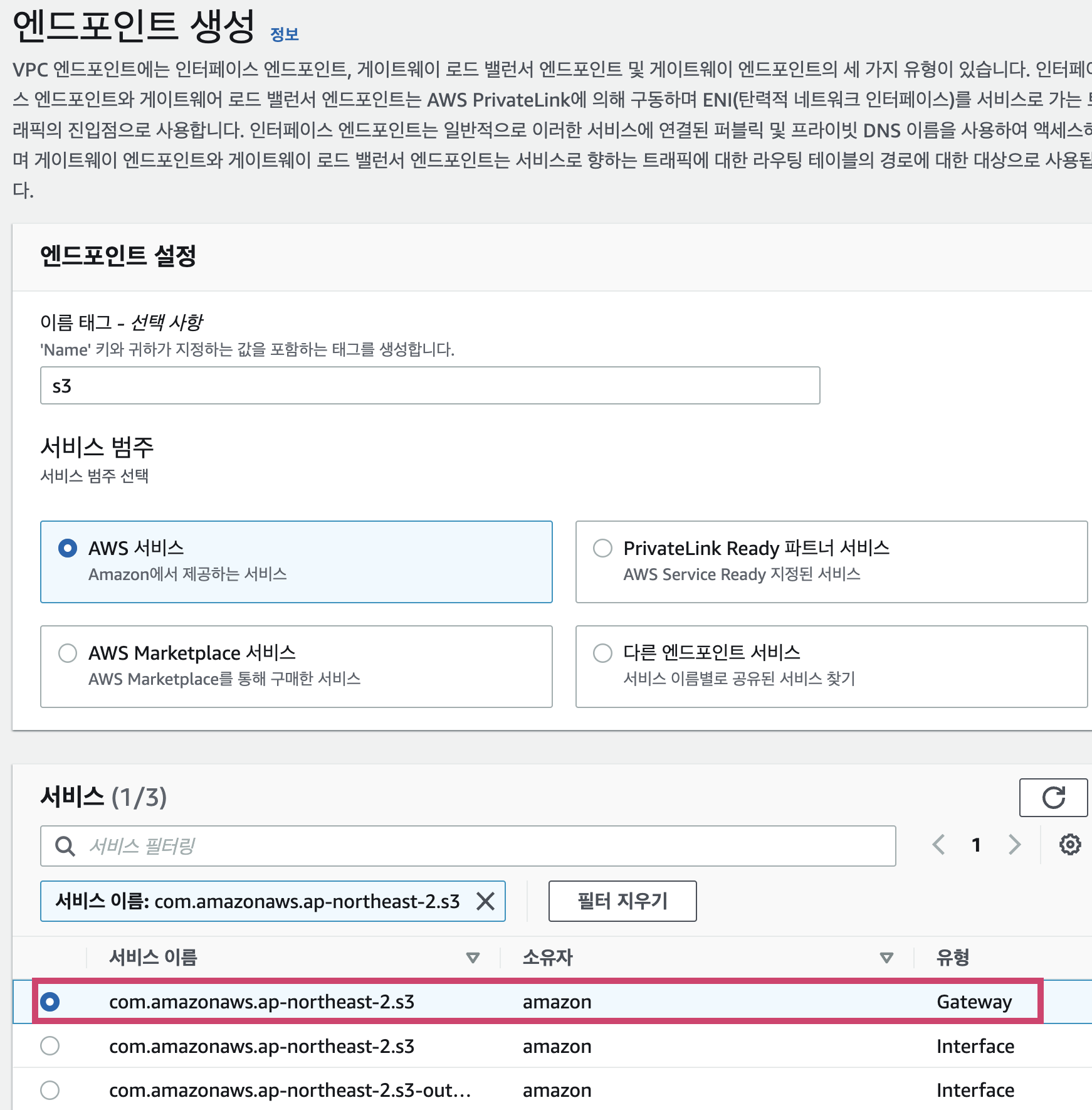
1. Create VPC Endpoint
2. Add access policy in IAM Role
$ aws s3 ls --region ap-northeast-2
# if ec2 instance couldn't have IAM role to access s3 policy
# error occurs like below
⚠️ An error occurred (AccessDenied) when calling the ListBuckets operation: Access DeniedDefine IAM policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObjectRetention",
"s3:DeleteObjectVersion",
"s3:GetObjectVersionTagging",
"s3:GetObjectAttributes",
"s3:RestoreObject",
"s3:PutObjectLegalHold",
"s3:InitiateReplication",
"s3:GetObjectLegalHold",
"s3:GetObjectVersionAttributes",
"s3:ListMultipartUploadParts",
"s3:ReplicateObject",
"s3:GetObjectVersionTorrent",
"s3:PutObject",
"s3:GetObjectAcl",
"s3:GetObject",
"s3:GetObjectTorrent",
"s3:AbortMultipartUpload",
"s3:PutObjectRetention",
"s3:GetObjectVersionAcl",
"s3:GetObjectTagging",
"s3:GetObjectVersionForReplication",
"s3:DeleteObject",
"s3:ReplicateDelete",
"s3:GetObjectVersion"
],
"Resource": "arn:aws:s3:::{BUCKET_NAME}/*"
},
"Resource": [
"arn:aws:s3::{ACCOUNT_ID}:{BUCKET_NAME}",
]
}
]
}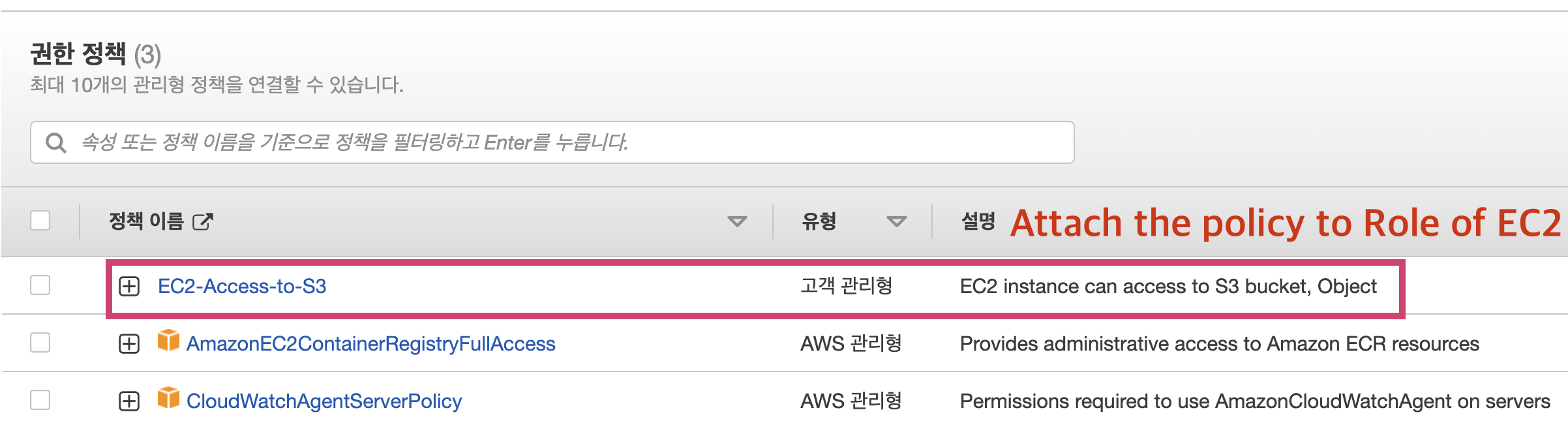
Diagram of result (VPC endpoint)
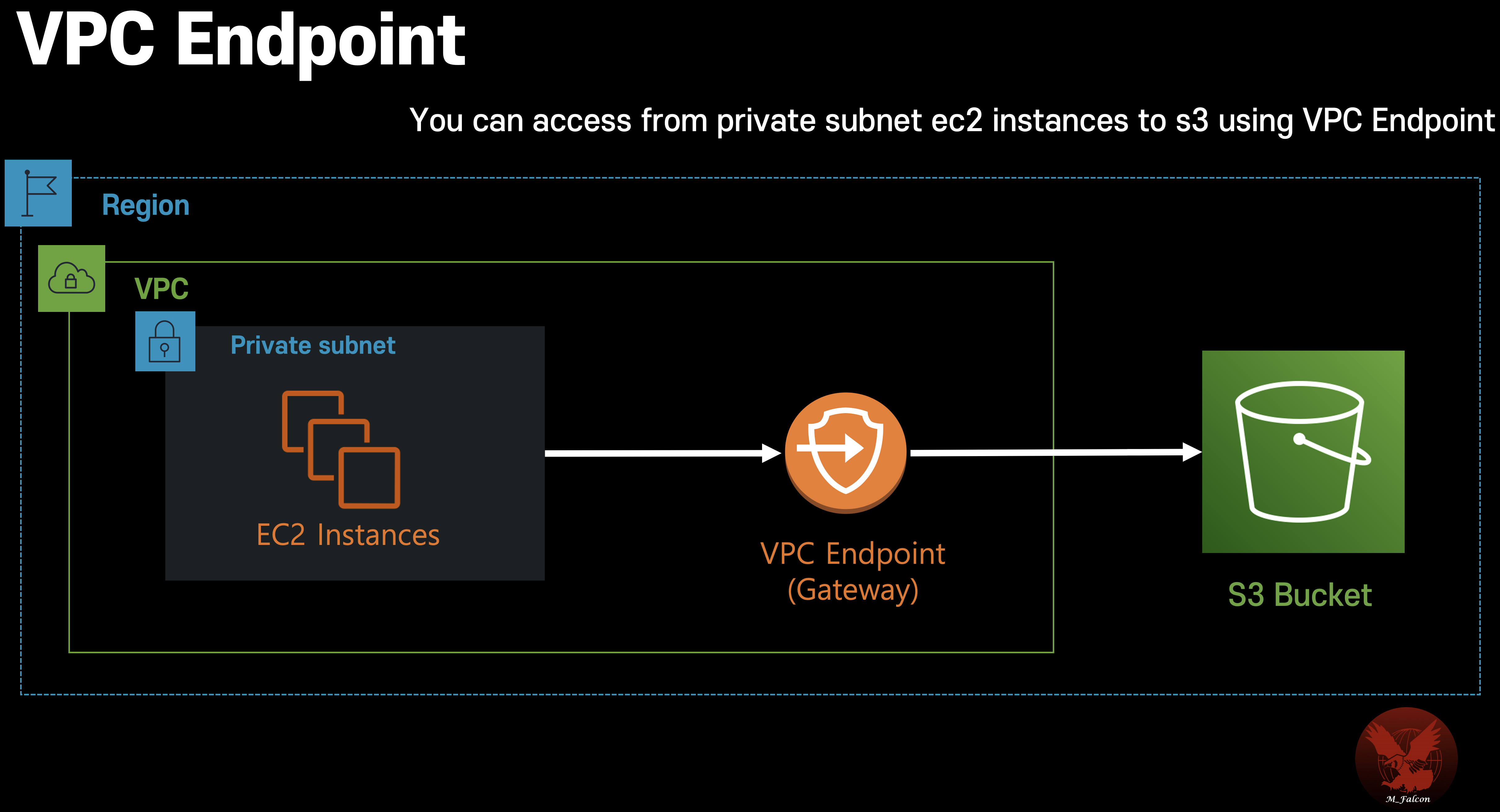
Any EC2 instance scale-out, No need Internet gateway, NAT, and configuring any other IAM policy and role.
Compare with NAT + IGW (public internet endpoint)
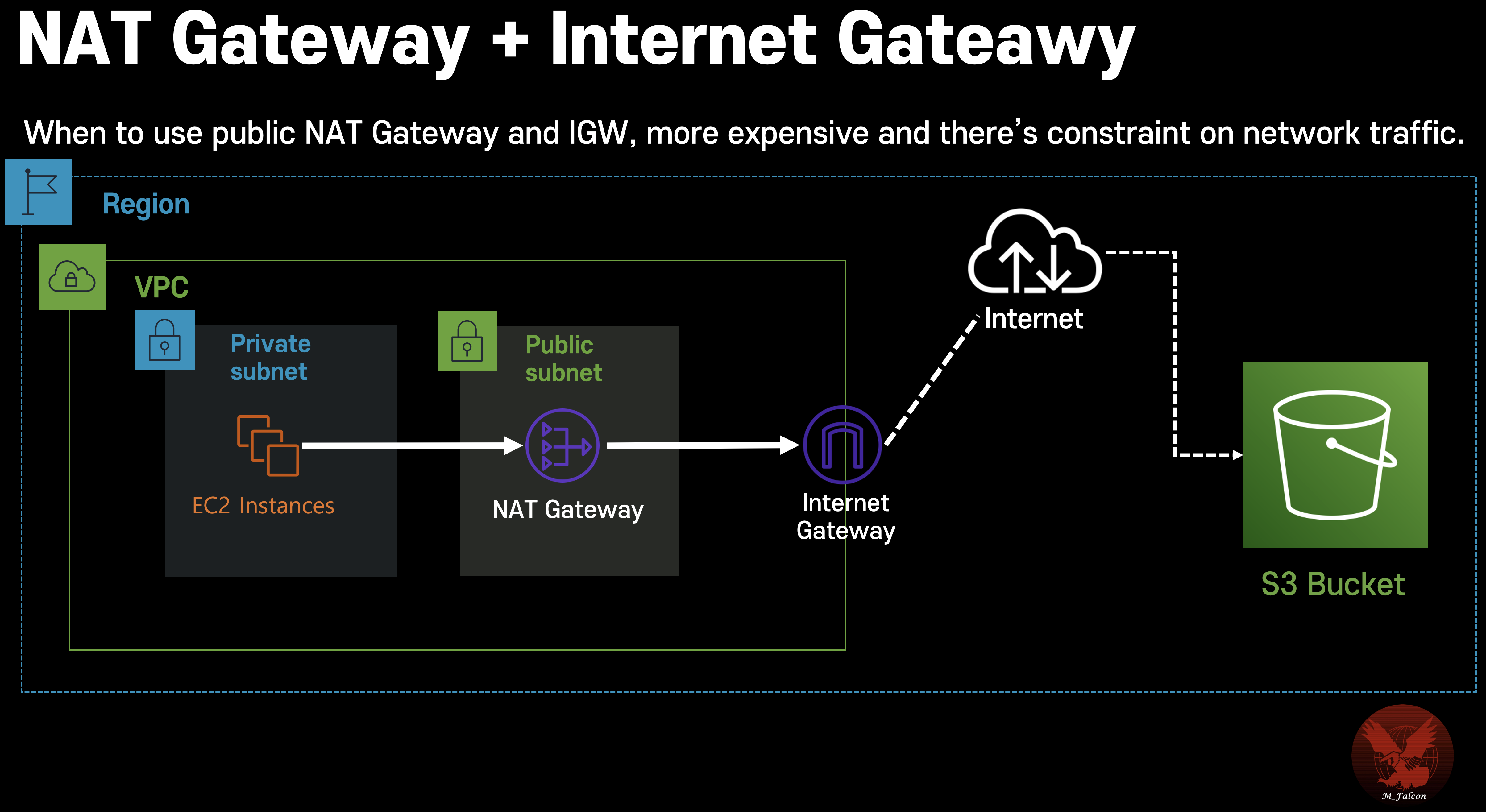
Furthermore?
S3 Access point support limit the access point specific VPC. You can use for managing s3 policy easily.
Refer to this docs
VPC flow logs
Capture network traffic and save logs on S3 or CloudWatch Logs infomration on AWS managed interface.
Source & Destination IP address, Port, Account ID
AWS managed resource
Next resources are can be monitored by VPC flow
- ELB
- RDS
- NAT Gateway
- RedShift
When to use
Monitor and anaylize, trouble shoot about connectivity or network traffic.
How to use
logs can be saved on S3 or CloudWatch Logs
- Query using athena on S3
- Query using CloudWatch Log Insights