Applied Cryptography
1.AES
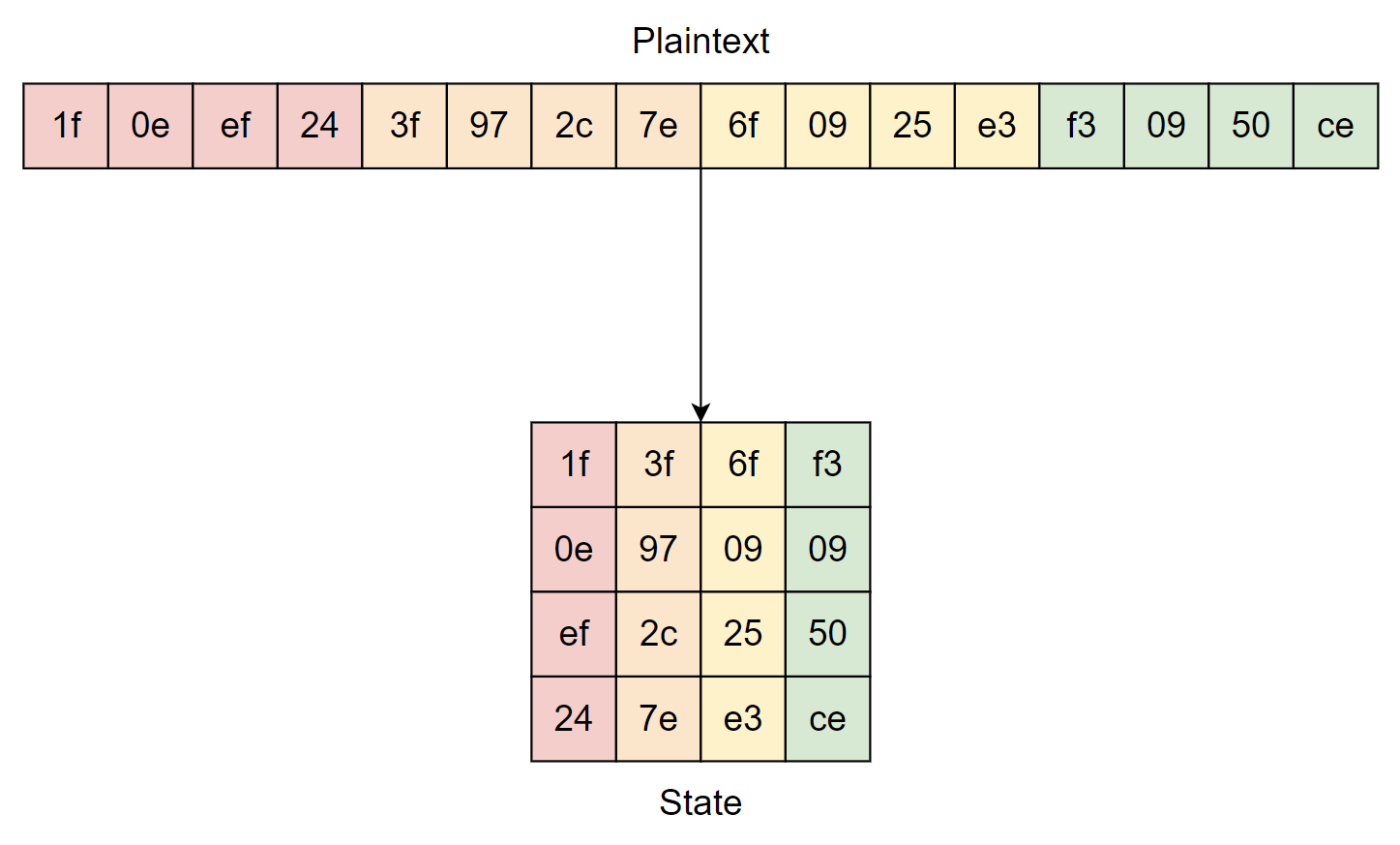
AES에 대해 다룬다.
2023년 2월 8일
2.Properties of hash functions
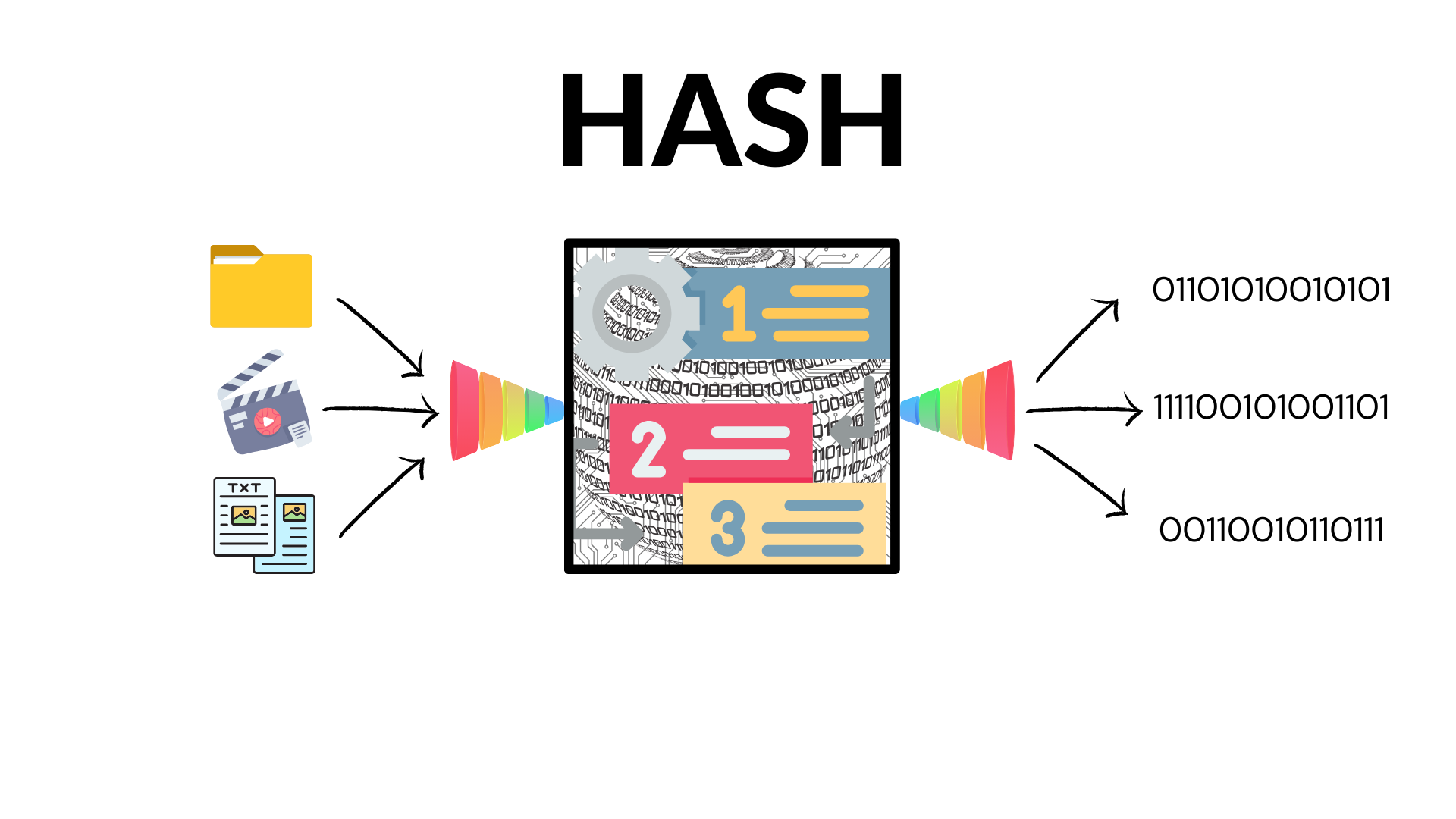
The significance of hash functions is that they provide a unique identifier for everything.
2022년 7월 17일
3.SHA-2
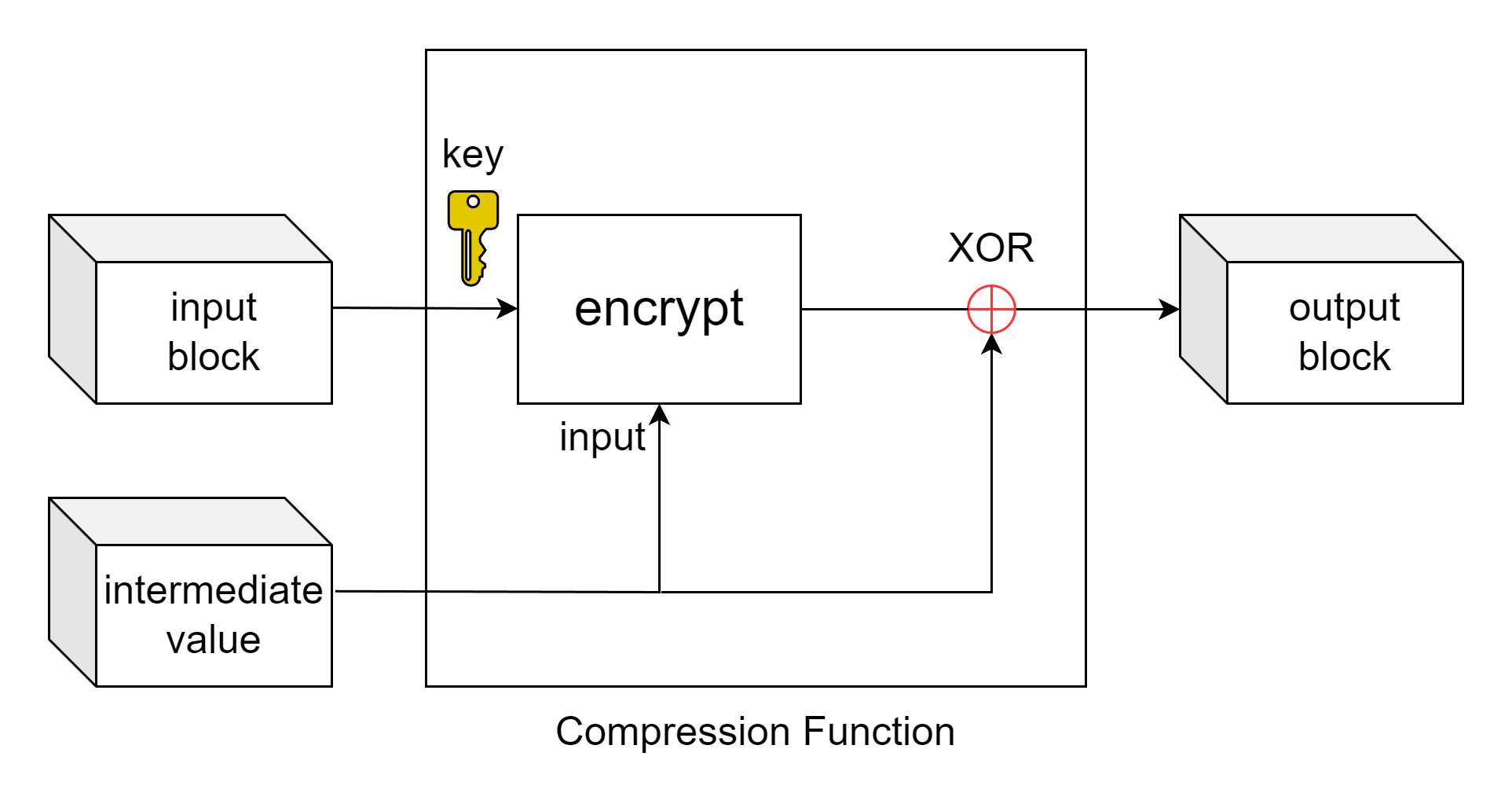
SHA-2에 대해 다룬다.
2022년 11월 14일
4.symmetric encryption
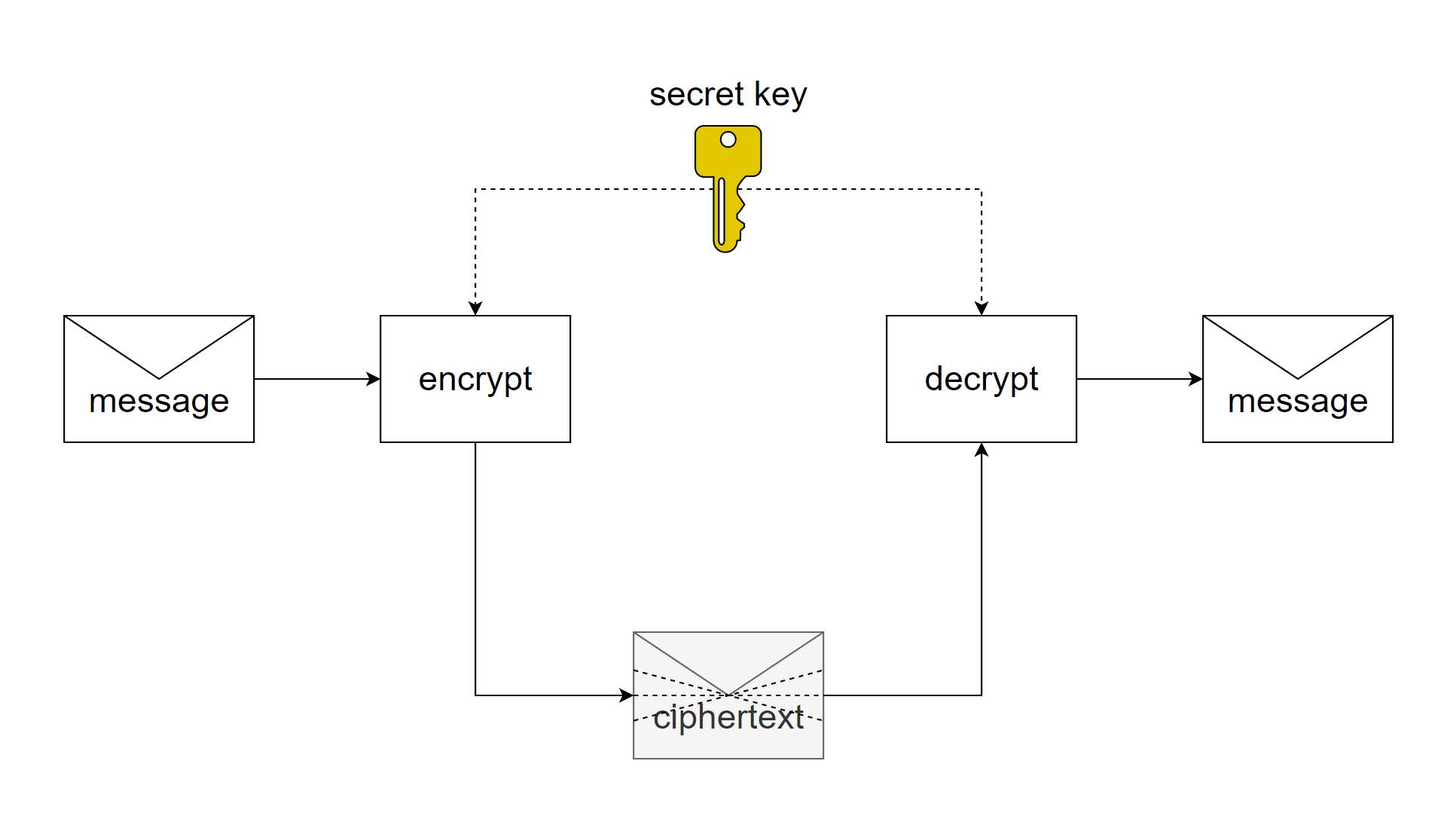
symmetric encryption
2022년 12월 4일
5.asymmetric cryptography
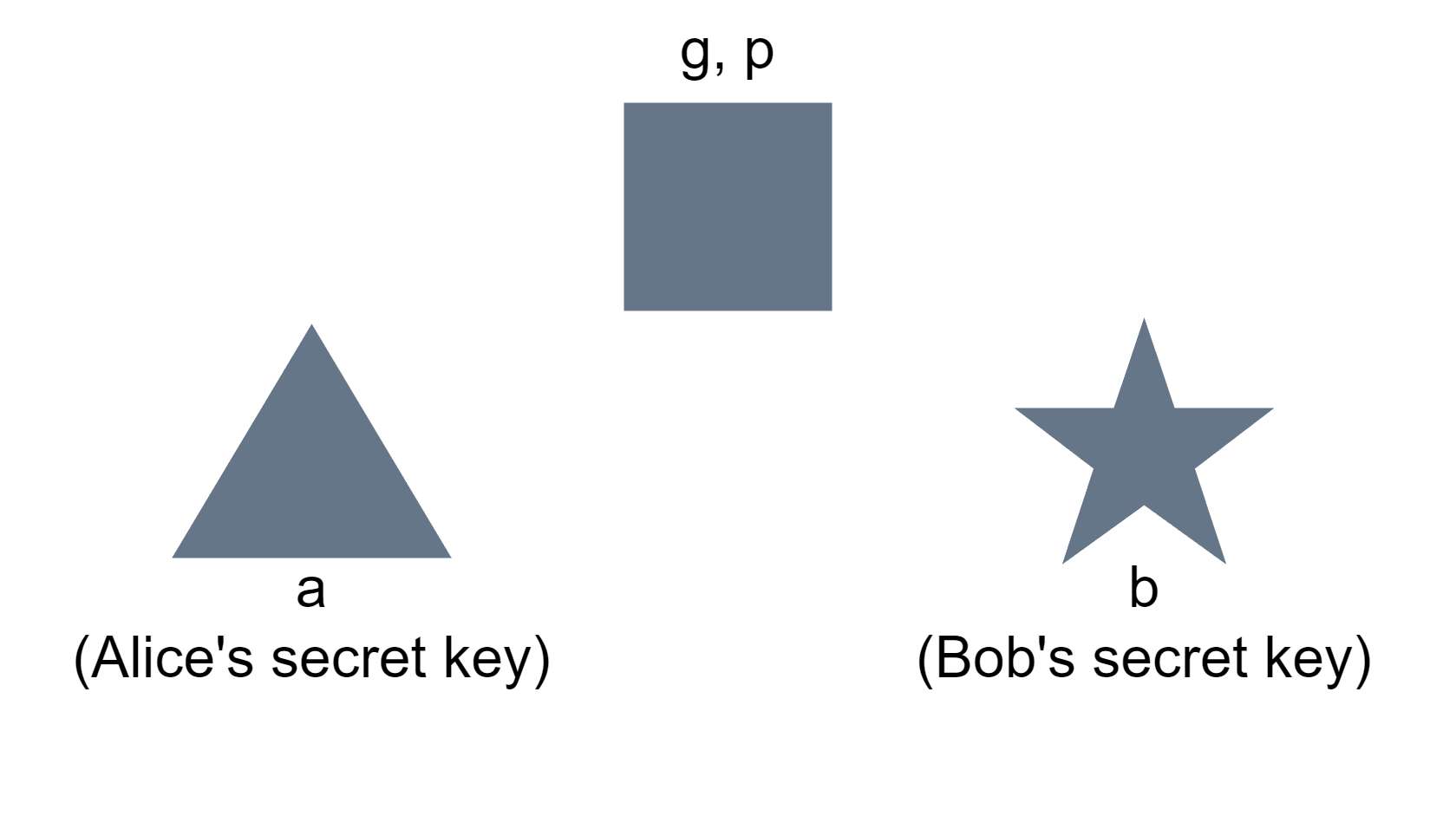
asymmetric cryptography에 대해 간략히 알아본다.
2022년 7월 17일
6.Sponge function

related to SHA3
2022년 12월 4일
7.XOF (SHAKE & cSHAKE)

SHA-3계열의 XOF에 대해 다룬다.
2023년 1월 6일
8.MAC (Message Authentication Code)
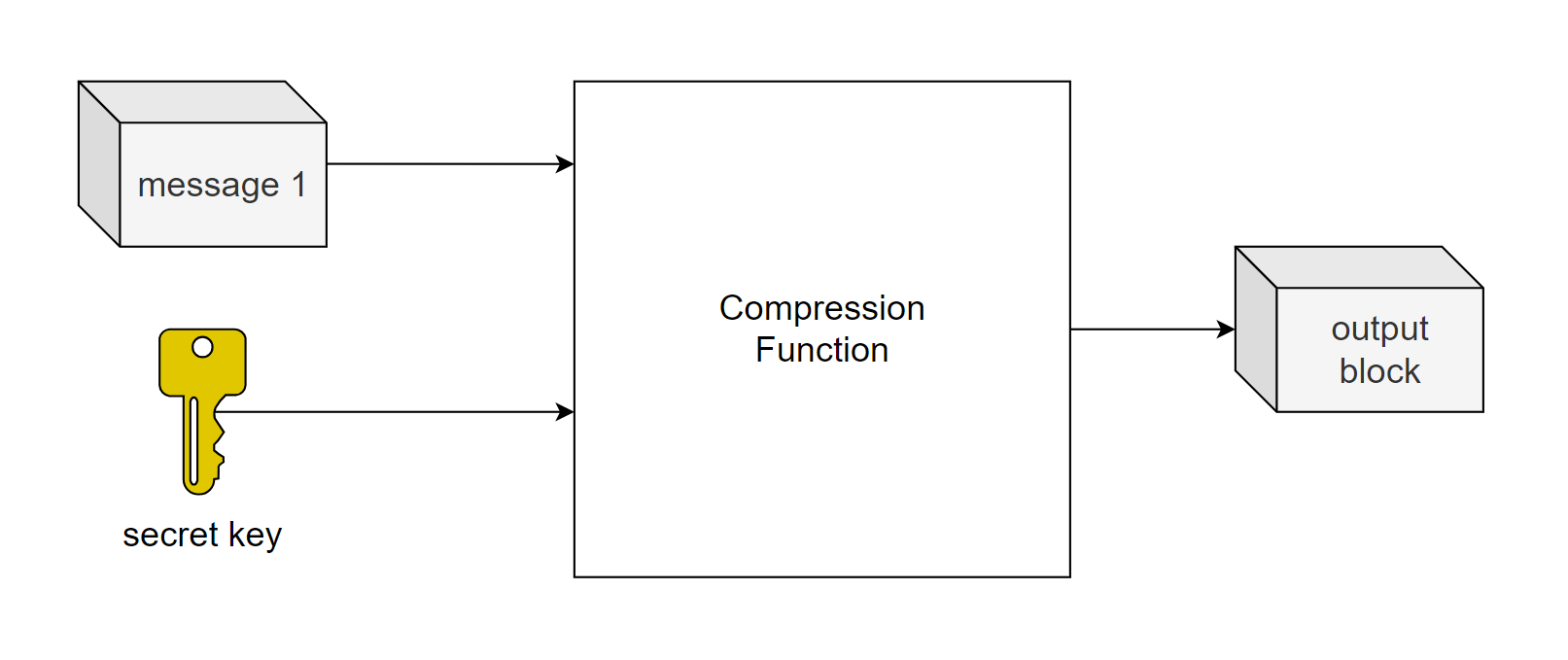
Message Authentication Code
2022년 7월 20일
9.HMAC (Hash-based Message Authentication Code)
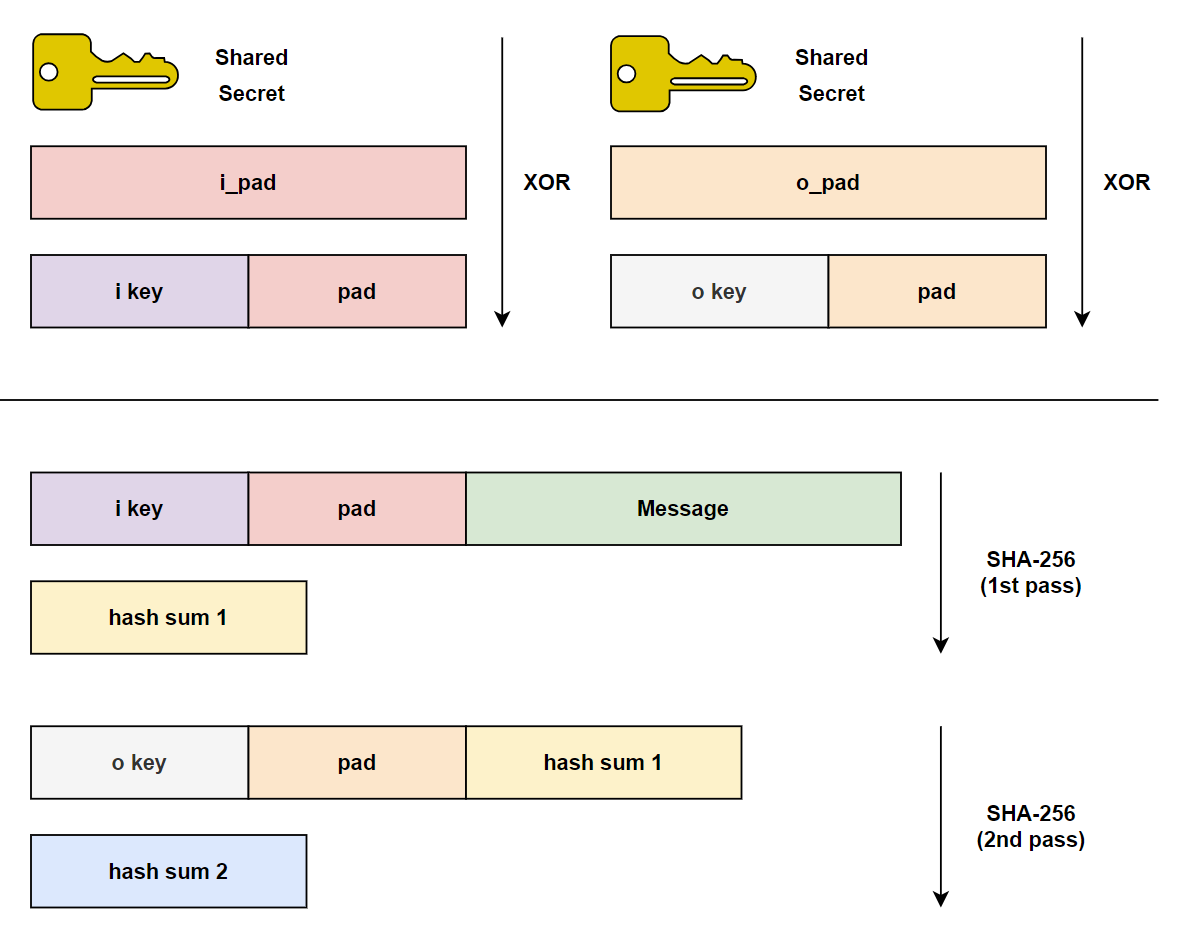
HMAC에 대해 다룬다.
2022년 9월 3일
10.Properties of Digital Signature

-
2023년 1월 8일
11.KMAC

KMAC에 대해 다룬다.
2024년 6월 9일