PE File Format
- Portable Executable (PE) File Format
- 이식 가능한 실행 파일 형식
- .exe 또는 .dll 파일 확장자를 사용
- 바이너리 파일 형식 구문 분석하는 tool이 아주 많음
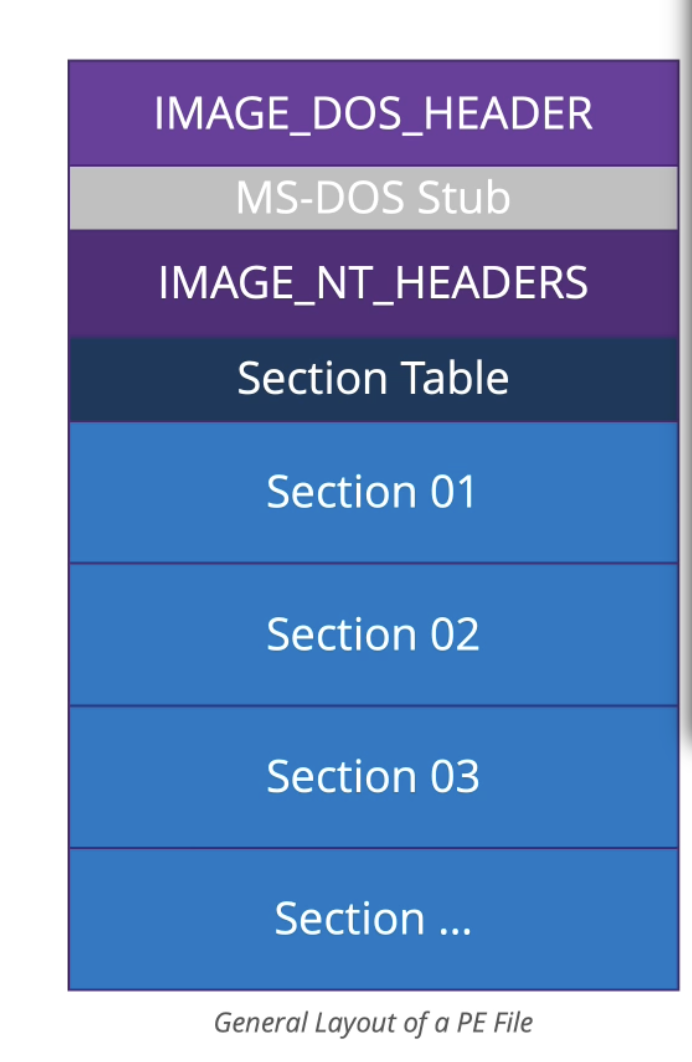
- PE 파일은 일관된 레이아웃을 유지함
- 파일의 시작 부분에 메타데이터가 포함됨 ( 가상 메모리에 로드할 주소, 프로그램의 시작 주소, 컴파일된 날짜/시간 )
- 메타데이터는 섹션테이블
- 섹션에는 중요한 리소스와 데이터가 포함되어있음.
- 섹션에는 프로그램의 실행 가능한 내용이 포함되어있음.
- .TEXT/.CODE - executable code- .data/.rdata - program data
- .rsrc - resources
- .idata - imported libraries/functions
- .debug - debug information
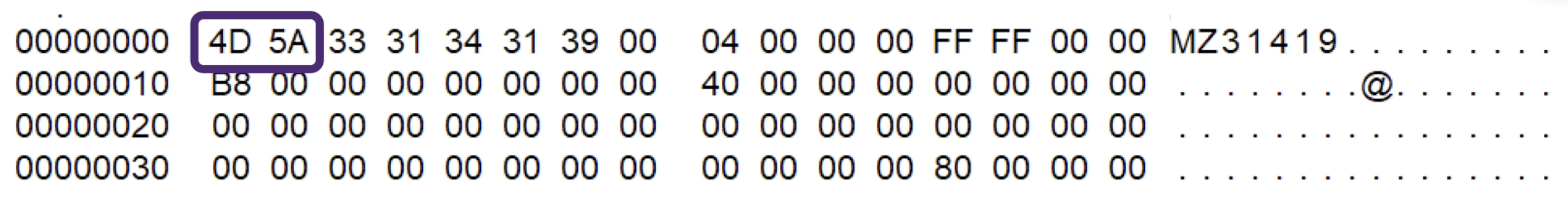
- 각 PE 파일은 IMAGE_DOS_HEADER 구조로 시작됨
- 파일의 처음 64바이트
- 처음 2바이트는 파일의 매직 넘버를 나타냄 ( 4D 5A )
https://learn.microsoft.com/en-us/windows/win32/debug/pe-format
PEView
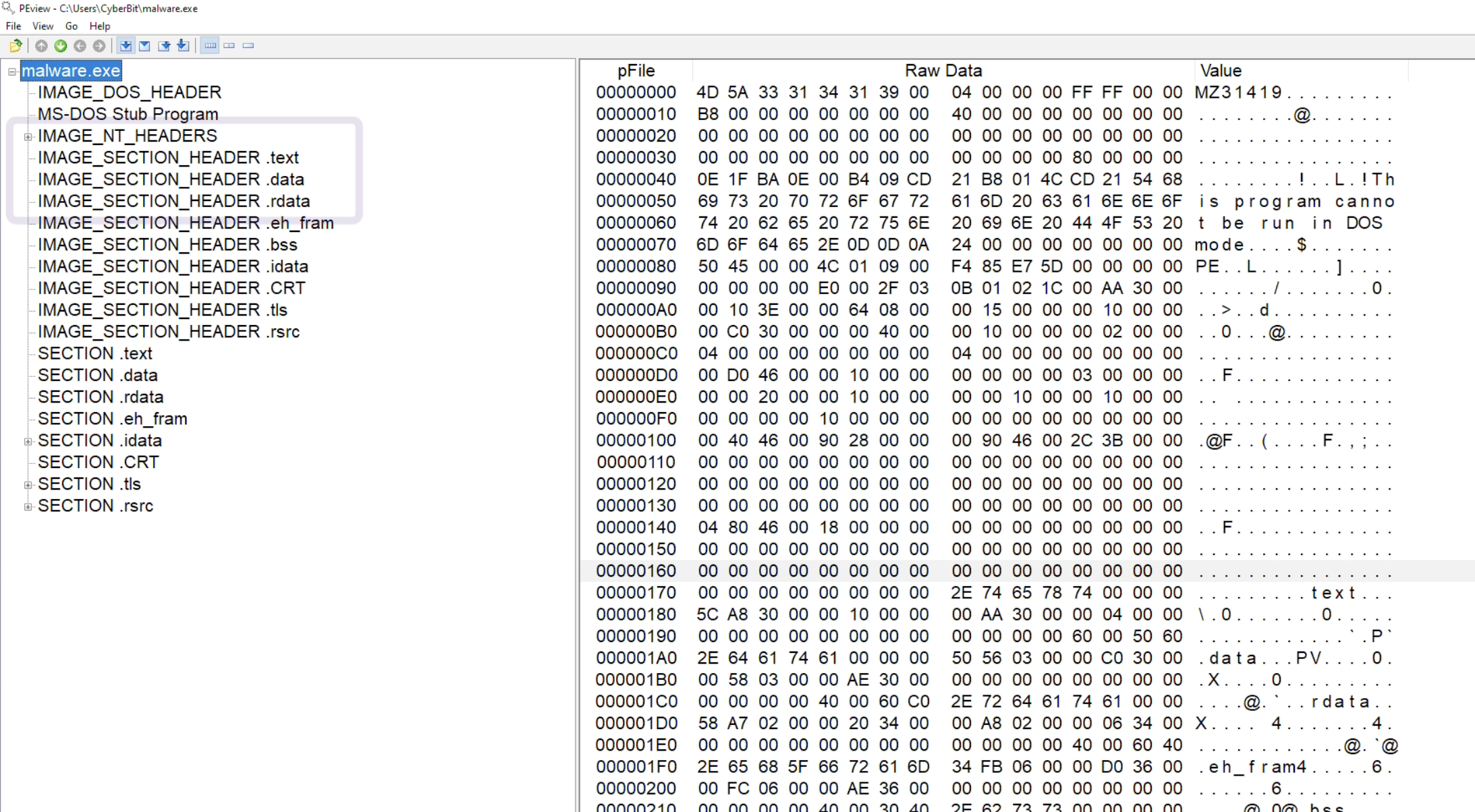
- PEView와 같은 도구에서 PE 파일을 볼 때, 파일의 전체 구조를 레이아웃
- IMAGE_DOS_HEADER로 시작
- 다음엔 DOS-STUB 존재
- IMAGE_NT_HEADERS : signature
- IMAGE_FILE_HEADER : Hex view
- IMAGE_OPTIONAL_HEADER : 프로그램에 대한 주요 정보 ( eg. 프로그램의 진입점, 메모리와 하위 시스템의 의도된 이미지 기반)
- IMAGE_SECTION_HEADER 뒤에는 다양한 PE 파일의 섹션을 정의하는 변수 번호가 옴.
- IMAGE_SECTION_HEADER.text 에서 Virtual Size는 측정값. 메모리에 있는 섹션은 일반적으로 비슷한 크기를 가짐.
- 크기의 차이가 커지면 malware가 압축되었음을 나타냄
💡 Quiz : Static Analysis - PE Format
1. Investigate IMAGE_DOS_HEADER. The first 64-bytes of all valid PE files contain the value 5A4D or 4D5A.
Is the file a valid PE file?a. The file is a valid PE file
b. 32-bit applications cannot have a PE header
c. 5A4D is not located in the first 64-bytes
d. The file does not contain 5A4D, and is not a valid PE file
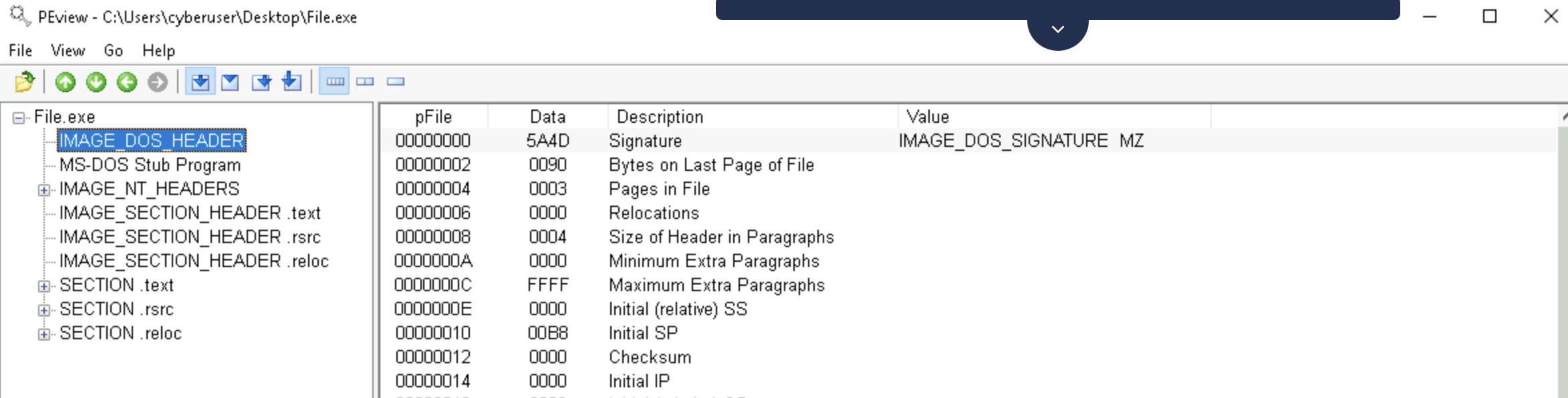
header에 5A4D 존재
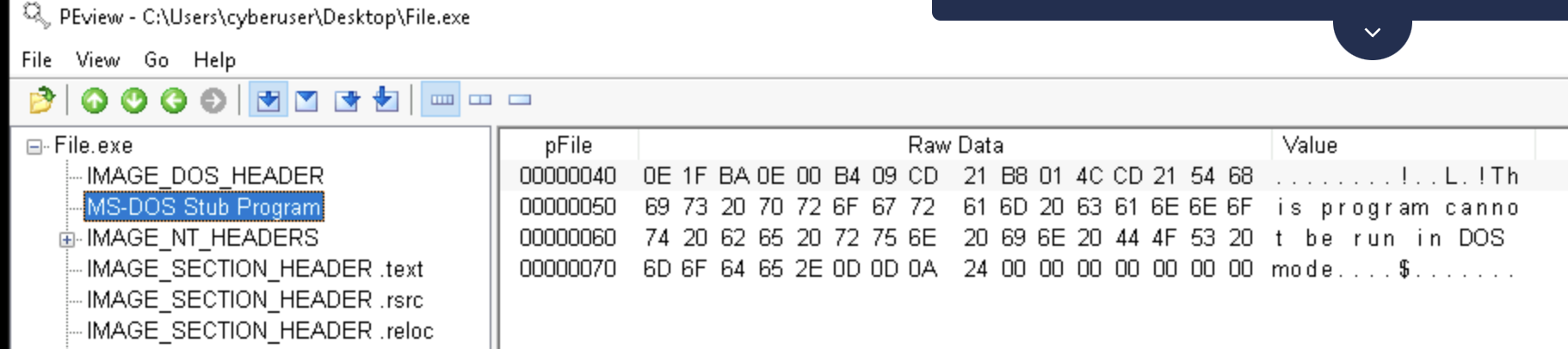
2. Investigate MS-DOS Stub Program.
What error is shown in the Value field?a. Application not found
b. This program cannot be run in DOS mode
c. This program cannot be found
d. The application was unable to start correctly in MS-DOS mode
3. Expand IMAGE_NT_HEADER and investigate the IMAGE_FILE_HEADER block.
When was the executable compiled?a. 1992/06/19
b. 2059/04/20
c. 2021/06/24
d. 1993/05/07
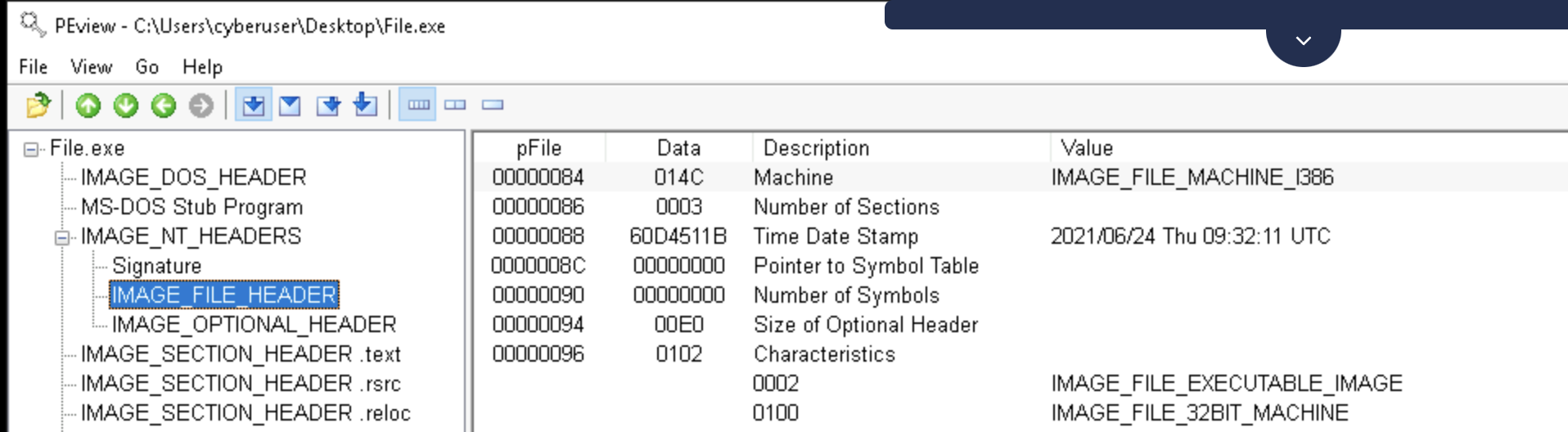
- Investigate the Characteristics field.
Is the executable 32-bit or 64-bit?a. PE files cannot be based on 32-bit or 64-bit architectures
b. It is impossible to know
c. The executable is 32-bit
d. The executable is 64-bit
5. Investigate IMAGE_OPTIONAL_HEADER.
Looking at the Magic field, is the executable 32-bit or 64-bit?a. It is impossible to know
b. The executable is 64-bit
c. PE files cannot be based on 32-bit or 64-bit architectures
d. The executable is 32-bit
6. Investigate the Subsystem field within IMAGE_OPTIONAL_HEADER.
Which subsystem is required to run this image?a. A WBA subsystem is required to run this image
b. A GUI subsystem is required to run this image
c. A CUI subsystem is required to run this image
d. A ROM subsystem is required to run this image
7. Investigate IMAGE_SECTION_HEADER .text. Major size differences between Size of Raw Data and Virtual Size may indicate if an executable is packed.
Is the executable packed?a. The executable is packed
b. The executable is obfuscated
c. The executable is not packed
d. Virtual Size and Size of Raw Data are the same size
크기가 다름 = 압축되어있지 않음
8. Investigate the characteristics field within IMAGE_SECTION_HEADER.text
Which flag indicates that the section contains executable code?a. IMAGE_SCN_LNK_COMDAT
b. IMAGE_SCN_MEM_EXECUTE
c. IMAGE_SCN_GPREL
d. IMAGE_SCN_MEM_WRITE
9. Expand SECTION .text and investigate its blocks. Some DLLs and functions may reveal which framework is used by the executable.
What framework does the executable use?a. Visual Basic
b. CherryPy Framework
c. Boost Framework
d. .NET Framework
Resources and RisohEditor Tool
- 실행 가능한 프로그램에는 리소스가 포함된다. ( eg. icon, menu, image, dialog, version )
- 이러한 리소스는 섹션에 저장된다.
- 리소스 섹션으로 알려진 .rsrc - malware 작성자는 난독화된 데이터를 저장하기 위해 이 섹션을 사용할 수 있다. (혹은 악성코드 패키징에)
- RisohEditor : Free resource editor tool
- PEView 랑 사용하는 법 비슷함
https://github.com/katahiromz/RisohEditor?tab=readme-ov-file
💡 Quiz : Static Analysis - Digging for Resources
https://en.wikipedia.org/wiki/List_of_file_signatures
1. Open the properties window of program.exe and navigate to the Details tab.
What program is this file described as?a. Notepad
b. Internet Explorer
c. Onedrive
d. Process Explorer
2. Execute the program. What program is this?
a. Onedrive
b. Internet Explorer
c. Process Explorer
d. Notepad
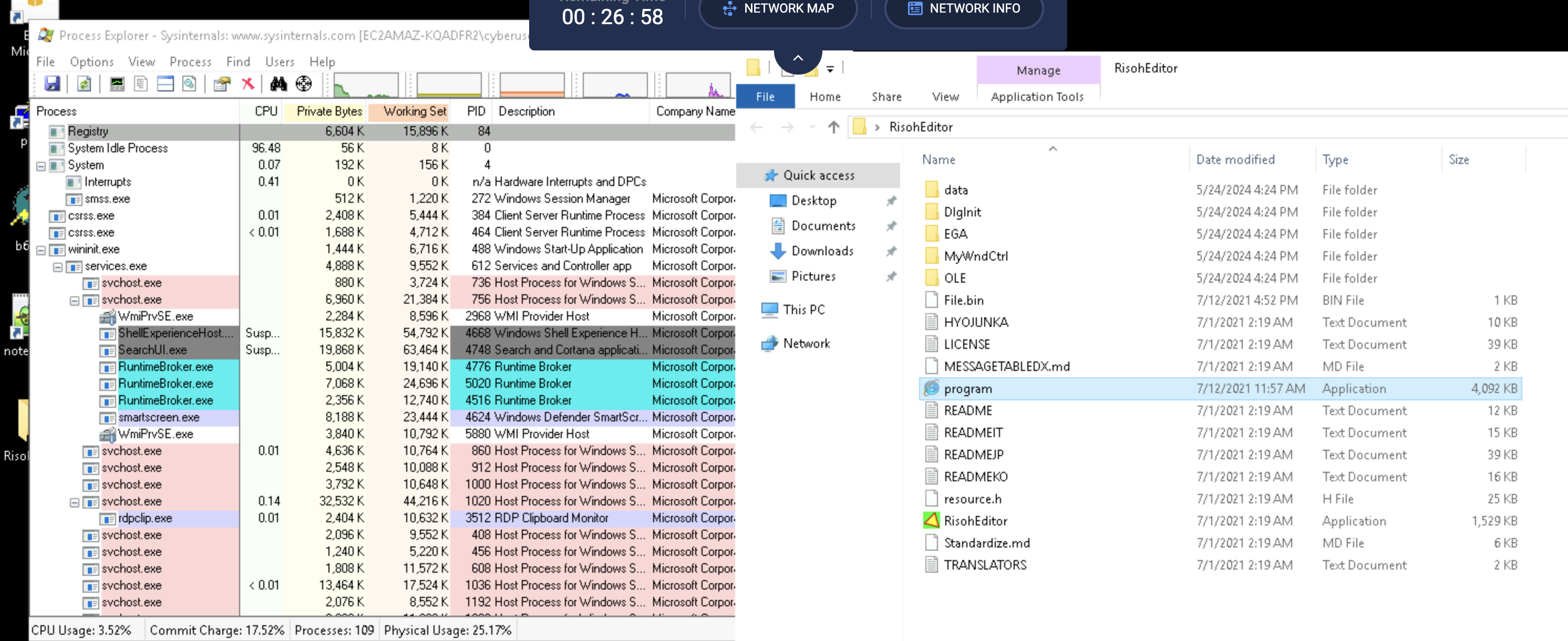
3. Drag program.exe onto the RisohEditor executable to open it. Expand RT_VERSION after closing the list of resource IDs. What is the company name?
a. Microsoft
b. Sysinternals
c. McAfee
d. Google
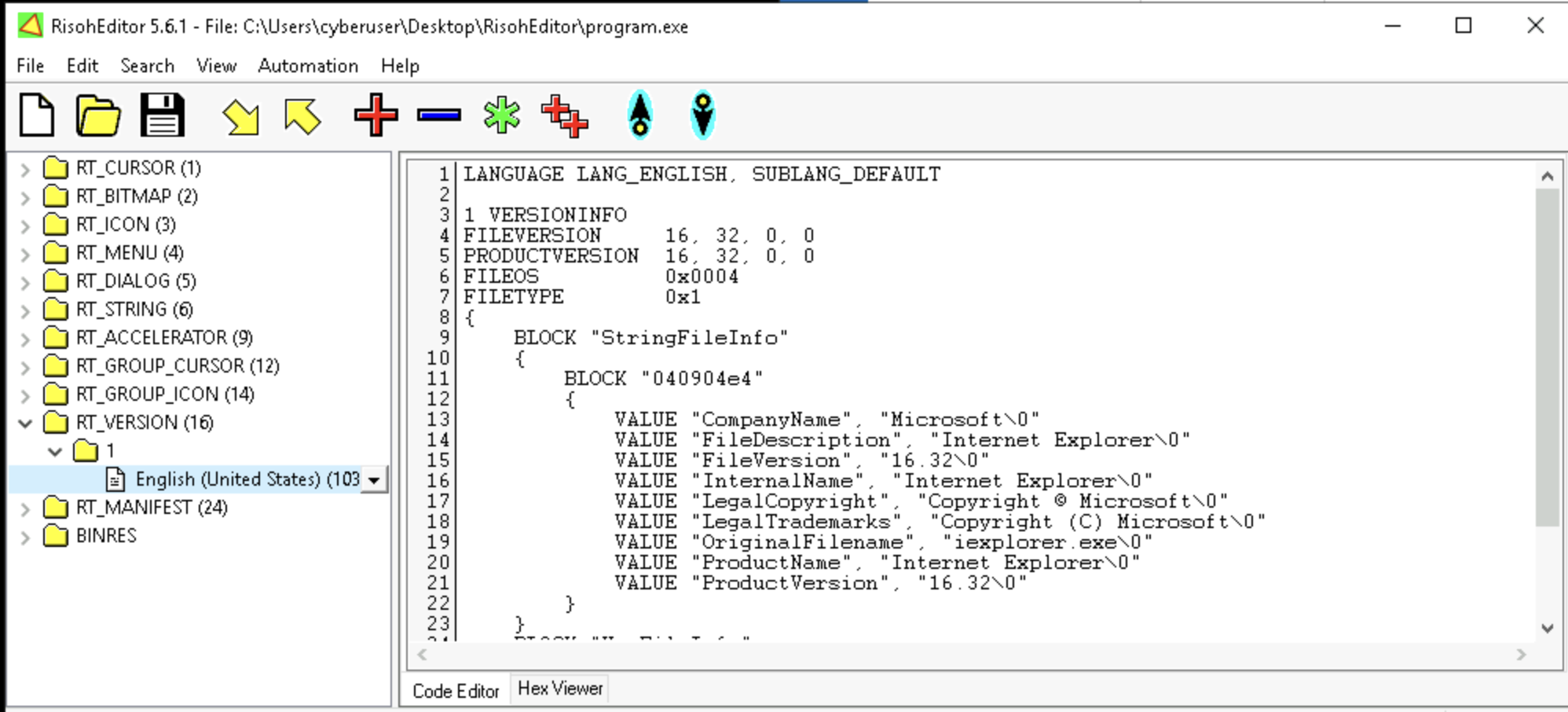
4. The .rsrc section may contain other embedded code the executable depends on. In this case, this is the BINRES section.
Expand the BINRES section and investigate the files found under the 150 and 152 folders using Hex Viewer mode (found at the bottom of the right window). What are the first 4-bits in each of the files?a. EF BB, BF 3C
b. 50 4B, 4D 5A
c. 2C 93, 34, 00
d. 5A 4D, 50 4B
5. What file extensions are embedded into the BINRES section? Use the Hex Viewer mode when investigating.
a. JPEG, MPG
b. DOC, DOCX
c. PDF, TXT
d. ZIP, EXE
파일을 마우스 오른쪽 버튼으로 클릭하고 추출 옵션을 선택하면 심층 분석을 위해 리소스 파일을 별도의 파일로 추출할 수 있음. 추출되는 일반적인 파일 형식은 바이너리 리소스(.res)와 바이너리 파일(.bin)임.
6. Extract the files found under the BINRES section as Binary Files. While extracting the files, name them according to their extension (if the magic number associates with a .pdf extension, name the file example.pdf). One of these resources contains a file.
What is the name of the file?a. PKFile.txtPK
b. English (United States)
c. File.txt
d. English (United States) (1033)
- What is the main purpose of digging through resources?
a. To perform a deeper analysis of the .rsrc section and check for different methods of disguise
b. To investigate fake version and company information
c. To make sure the file hash is not fake
d. To understand if the executable contains both 32-bit and 64-bit versions
DLL (Dynamic Link Libraries)
- 주요 목적은 프로그램 간에 코드를 공유하는 것
- DLL은 PE 파일 형식을 사용한다.
- DLLs export functions, defined in an export table
- DLL은 일반적으로 코드를 공유하는데 사용되지만, malware 작성자가 직접 사용할 수도 있다. rundll32와 같은 프로그램을 사용해서. ( Can be executed directly through programs like rundll32)
-> May have an entry point : DllMain
- 실행 파일은 라이브러리를 통해 필요한 기능을 가져온다.
- 라이브러리 연결 과정의 3가지 주요 방법
- 정적 연결 이용 (Static) - libraries are compiled into the program
- Dynamic - libraries are loaded based on defined imports
- Runtime - libraries are loaded on-demand
Common Microsoft DLLS
https://en.wikipedia.org/wiki/Microsoft_Windows_library_files
- Kernel32.dll : Core library that allows for process, memory and file access
- Ws2_32.dll : Contains functions that allows for low-level networking
- AdvAPi32.dll : Provides access to advanced functions, such as the ability to modify the registry
- Ntdll.dll : Provides an interface to the Kernel, imported by Kernel32
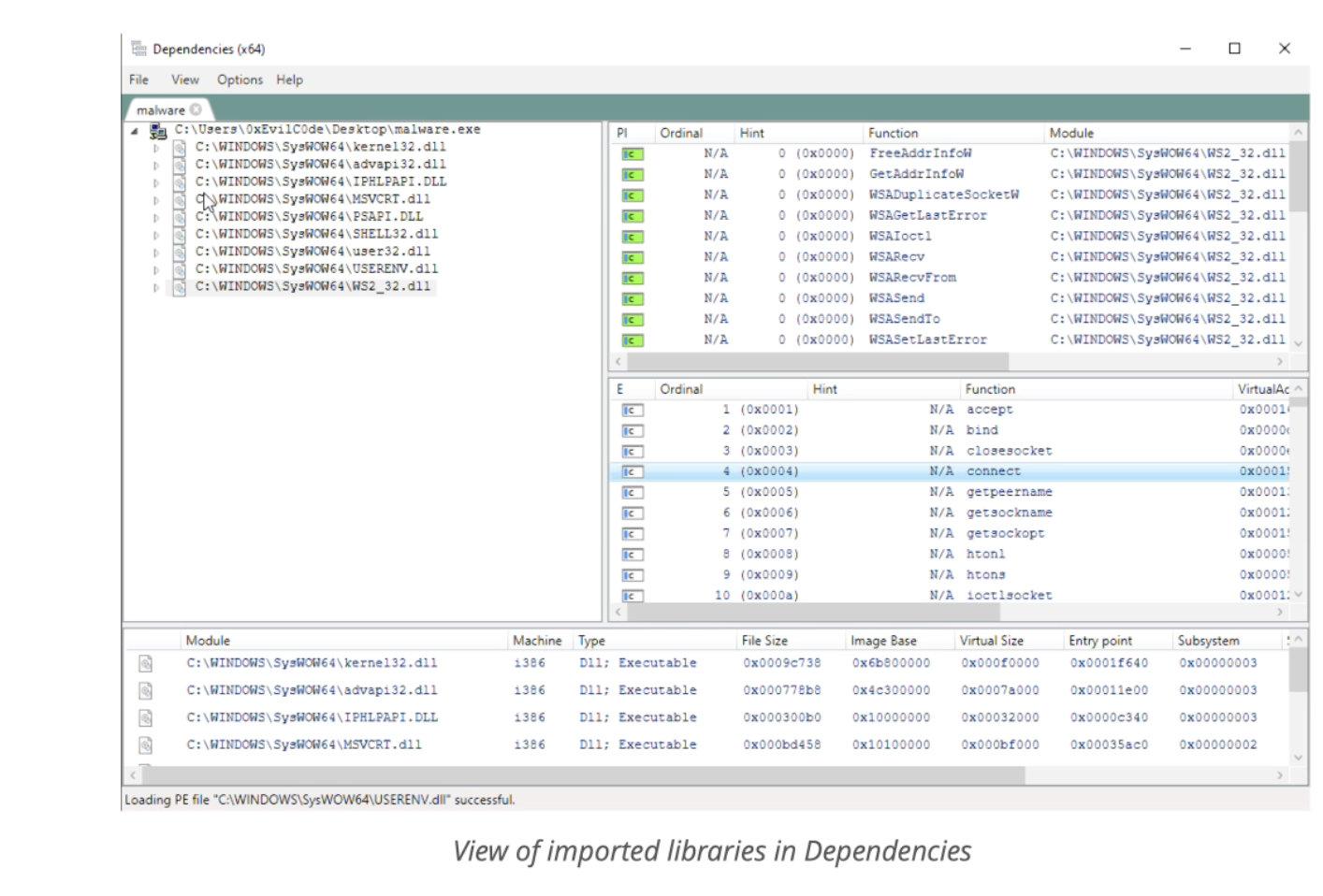
- Dependencies : Free dependency investigation tool
💡 Quiz : Static Analysis - DLLs and Imported Functions
1. Expand mscoree.dll found in the top-left window of Dependencies. How many DLLs are imported by mscoree.dll?
a. 6
b. 8
c. 7
d. 5
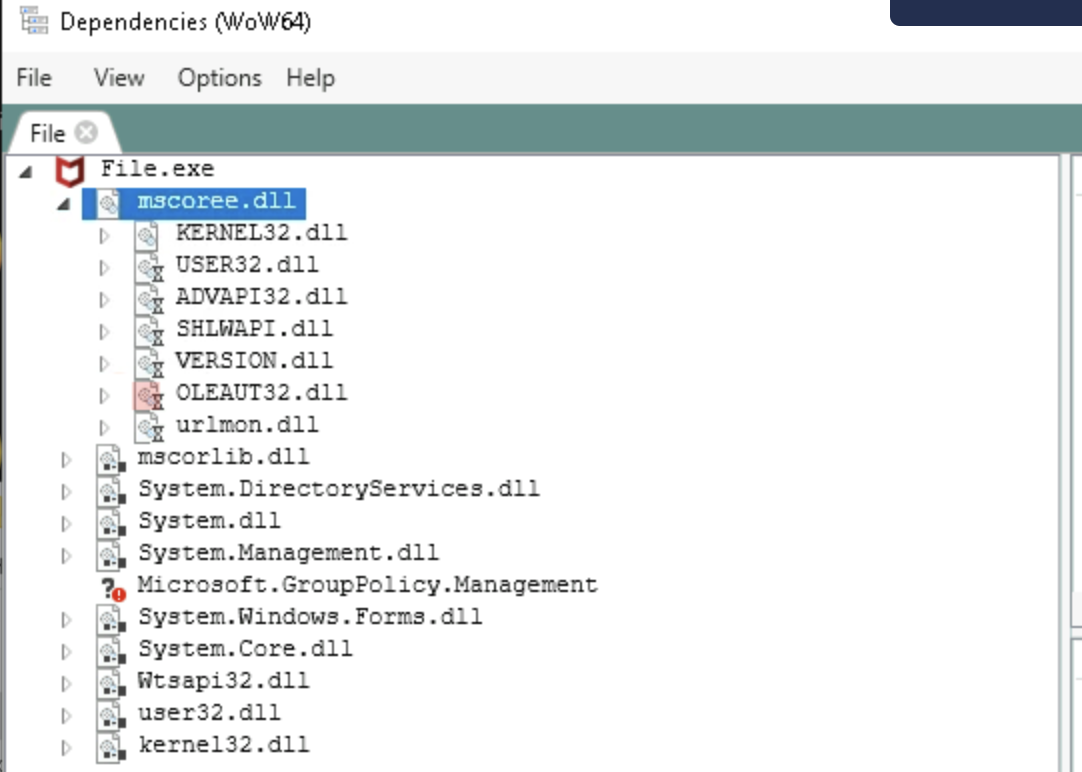
2. Click on mscoree.dll to select it. Find the _CorExeMain function by looking in the top-right window under the Function column.
What framework does the function _CorExeMain belong to? Search for the function name in the "Microsoft Function Search" provided in "About the Unit".a. Boost Framework
b. .NET Framework
c. CherryPy Framework
d. Visual Basic
3. Investigate the functions of KERNEL32.dll nested within mscoree.dll. GetProcAddress and LoadLibrary are typically used for Run-time linking.
Does the executable allow Run-time linking?a. Yes, with LocalFree
b. Yes, GetProcAddress and LoadLibrary functions are present
c. The software only uses dynamically linked libraries
d. 32-bit applications cannot use Run-time linking
4. Within KERNEL32.dll, investigate functions that mention processes. Use “Microsoft Function Search” to understand the functionality of those functions.
Does the executable contain process manipulation functions?a. The software cannot manipulate processes
b. Multiple process manipulation functions are present
c. Only if the user is an administrator
d. Yes, only with TerminateProcess
5. Can the executable create files?
a. The executable cannot create files
b. Multiple file manipulation functions are present
c. Only if the user is an administrator
d. Yes, with CreateFile
6. Functions for Graphical User Interface (GUI) are located inside USER32.DLL. Investigate each function in the top-right window.
Does the executable have a GUI?a. GUI functions are present
b. The software does not have a GUI
c. Executable applications cannot have a GUI
d. 32-bit applications cannot have a GUI
7. Functions for Registry manipulation are located inside ADVAPI32.DLL.
Does the executable access registries?a. There are functions that allow Registry access present in ADVAPI32.DLL
b. The executable cannot access registries
c. The executable can create, modify, and delete registries
d. The executable achieves persistence through the Run Registry key
8. Does the executable achieve persistence through the Registry?
a. There is no way of knowing
b. 32-bit applications cannot be added into the Registry
c. The executable does not achieve persistence
d. The executable has the proper Registry functions to achieve persistence
9. Functions for color settings, URL, and UNC paths are located inside of SHLWAPI.DLL.
Can the executable check for UNC paths?a. The executable will check for UNC paths
b. The executable cannot check for UNC paths
c. The functions are only called by ordinals
d. The executable does not import SHLWAPI.DLL
10. Investigate urlmon.dll.
What functionality does the function provide to the executable?a. The function downloads data from a URL
b. The function executes programs with an ordinal
c. The function manipulates the memory
d. The function opens a blocking stream
