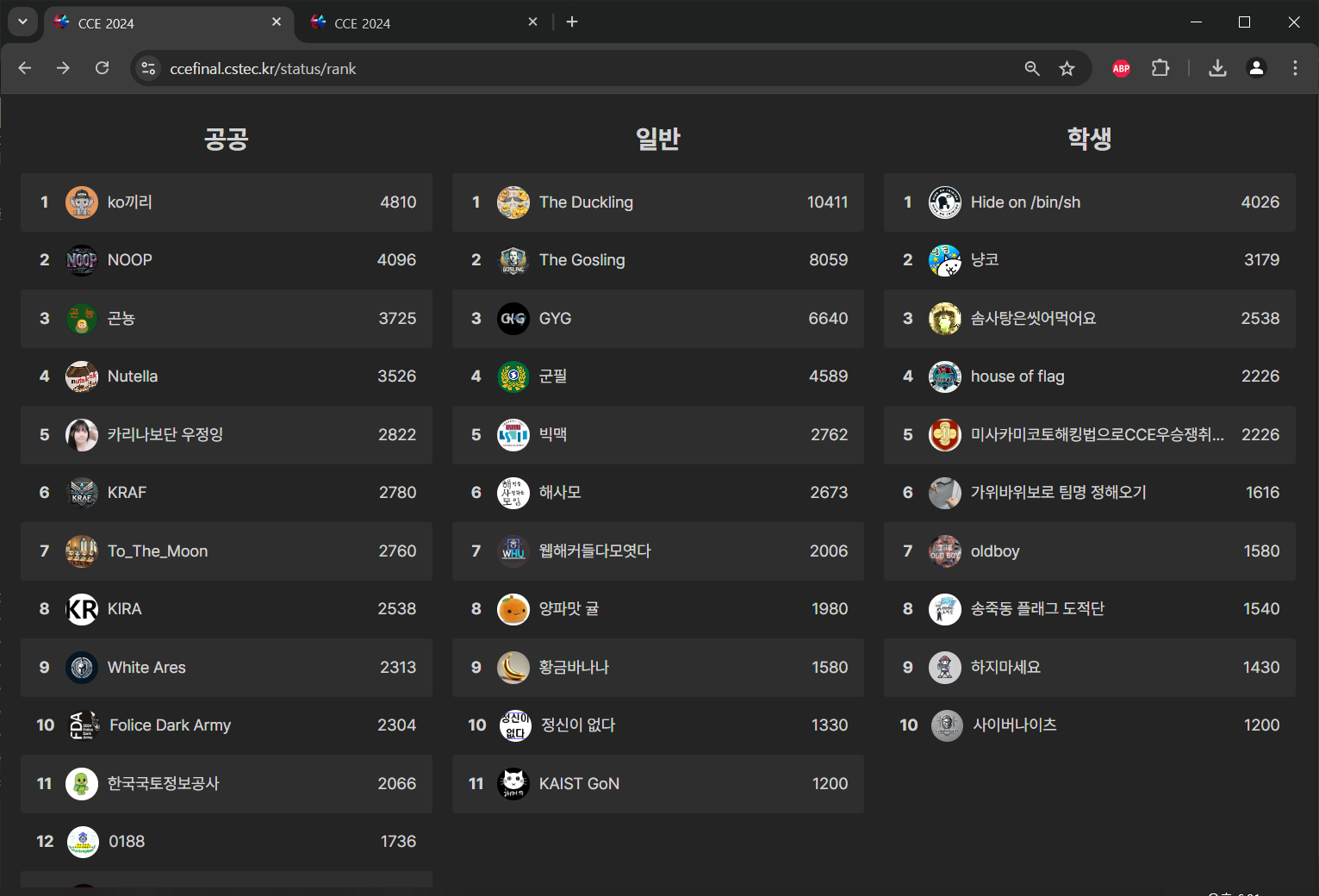
공공부문 2등으로 마무리한 CCE 후기
Jeopardy 2086 점 + Live Fire 2010 점으로 2**12 점을 달성하며 공공 2위 총 6위를 기록했다.
나는 Live Fire 와 01 번 문제를 해결하였다. 01번이 생각보다 늦어지면서 다른 문제를 제대로 못봤는데 대회 시간이 짧다고 느껴졌다. 문제는 다 재밌어보였는데 😥
TMI
우리 팀 NOOP을 소개하자면 육군 사이버작전센터 에서 근무하는 병사 2명과 간부 2명으로 이루어져 있다
병사는 나와 사이버작전병 알동기인 정웅이, 그리고 김종민 소령님, 이도원 대위님까지.
인생에서 아마 하나뿐일 공공 부문 출전이어서 1등을 기대했지만 숨어있던 사국 2분께 1등 자리는 넘어갔다.

Live Fire 는 모든 팀에게 2500 점을 대회 시작할 때 부여하고, 각 팀마다 주어진 서버에 20분마다 5개 취약점을 공격이 이루어졌다. 각 취약점당 10점씩 차감되며 정상적인 기능이 고장날 시 그냥 50점이 까이는 방식이다. 2022년 CCE 때는 바이너리만 주어지고 어셈 패치를 통해 업로드해야 했는데 이번에는 서버 내에 ssh 접속하여 직접 소스코드를 수정 후 빌드하는 방식으로 패치가 진행되었다. 그때 당시 Live Fire 의 도트딜이 생각보다 컸고 (대회 시간이 더 길었기에) 이번에도 Live Fire가 중요할 것 같아 Live Fire 부터 확인했다.
계산해보면 1200점이 최소 점수이다. 150점씩 9시간마다 감소되고 마지막 한번은 아니니 2500점에서 1300점이 까여 1200점이 최소 점수.
2019년부터 매년 대회를 여기저기 다니면서 처음 겪는 상황이 일어났다. 
대회장 입장하는 줄이 뭐이리 길지 의아했는데 저 끝에 육군 본청과 공항에서 볼 수 있는 검색대가 있었다. 안내사항으로도 검색대 통제 시간을 지날 경우 입장이 힘들 수 있다는 의미심장한 문자가 왔었다. 암튼 줄 서다보니 경찰분들과 정장입은 분들이 소지품 검사 및 몸 스캔을 하는데 왜이럴까 싶었다.
설마설마 했는데 대통령이 직접 오셨다. 😵 CCE 행사 옆에 APEX ? 뭔 행사도 같이 하느라 외국인들도 많이 왔고 밖에는 보안 관련 회사들 부스가 있었는데 오전 11시에 대통령의 기념 촬영식이 있었다. 그렇게 이병 부터 병장, 하사부터 준위, 소위부터 5스타까지 모두 도감에 등록되었다.😎
writeup
Live Fire - 1 / SQLI
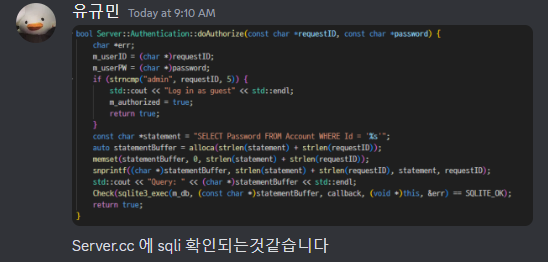
가장 먼저 로그인 코드가 눈에 띄었다.
bool Server::Authentication::initAccount() {
char *err;
const char *statement = "DROP TABLE IF EXISTS Account;"
"CREATE TABLE Account(Id TEXT, Password TEXT);"
"INSERT INTO Account VALUES('admin', 'CCE2024LIVEFIRE');";
Check(sqlite3_open(":memory:", &m_db) == SQLITE_OK);
Check(sqlite3_exec(m_db, statement, 0, 0, &err) == SQLITE_OK);
return true;
}
int callback(void *ptr, int argc, char **argv, char **azColName) {
auto me = (Server::Authentication *)ptr;
for (int i = 0; i < argc; i++) {
if (!strcmp(argv[i], me->userPW())) {
me->setAdmin(true);
me->setAuthorized(true);
break;
}
}
return 0;
}
bool Server::Authentication::doAuthorize(const char *requestID, const char *password) {
char *err;
m_userID = (char *)requestID;
m_userPW = (char *)password;
if (strncmp("admin", requestID, 5)) {
std::cout << "Log in as guest" << std::endl;
m_authorized = true;
return true;
}
const char *statement = "SELECT Password FROM Account WHERE Id = '%s'";
if (res != SQLITE_DONE) {
std::cerr << "Execution failed: " << sqlite3_errmsg(m_db) << std::endl;
}
auto statementBuffer = alloca(strlen(statement) + strlen(requestID));
memset(statementBuffer, 0, strlen(statement) + strlen(requestID));
snprintf((char *)statementBuffer, strlen(statement) + strlen(requestID), statement, requestID);
std::cout << "Query: " << (char *)statementBuffer << std::endl;
Check(sqlite3_exec(m_db, (const char *)statementBuffer, callback, (void *)this, &err) == SQLITE_OK);
return false;
}물구나무 서서 봐도 문제인 '%s' 가 보인다. 게다가 id 비교 또한 strncmp 로 앞 5바이트만 admin 인지 확인하기 때문에 admin' or 1=1 -- 처럼 sqli가 가능해보인다. 시도해보면 잘 된다.
bool Server::Authentication::doAuthorize(const char *requestID, const char *password) {
char *err;
sqlite3_stmt *stmt;
m_userID = (char *)requestID;
m_userPW = (char *)password;
if (strncmp("admin", requestID, 5)) {
std::cout << "Log in as guest" << std::endl;
m_authorized = true;
return true;
}
const char *statement = "SELECT Password FROM Account WHERE Id = ?";
std::cout << "doAuthorize" << std::endl;
if (sqlite3_prepare_v2(m_db, statement, -1, &stmt, nullptr) != SQLITE_OK) {
std::cerr << "Failed to prepare statement: " << sqlite3_errmsg(m_db) << std::endl;
sqlite3_close(m_db);
return 1;
}
if (sqlite3_bind_text(stmt, 1, requestID, -1, SQLITE_STATIC) != SQLITE_OK) {
std::cerr << "Failed to bind text: " << sqlite3_errmsg(m_db) << std::endl;
}
int res = sqlite3_step(stmt);
if (res == SQLITE_ROW) {
const char *_password = (const char*)sqlite3_column_text(stmt, 0);
std::cout << _password << std::endl;
if (!strncmp(_password, password, strlen(_password))) {
std::cout << "Login Success" << std::endl;
sqlite3_finalize(stmt);
this->setAdmin(true);
this->setAuthorized(true);
return true;
}
} else if (res != SQLITE_DONE) {
std::cerr << "Execution failed: " << sqlite3_errmsg(m_db) << std::endl;
}
sqlite3_finalize(stmt);
std::cout << "Login Failed" << std::endl;
return false;
}위 코드처럼 '%s' 를 ? 로 대체하고 prepare - bind - step 순으로 호출하며 파라미터 바인딩을 해준다.
약간 헤매다 로그인 기능이 작동안해서 두 타임? 날려먹었지만 10시에 성공적으로 패치했다.
남은 8시간 => 10 point * 3 / 1hour => 240 점 방어
Live Fire - 2 / Command Injection
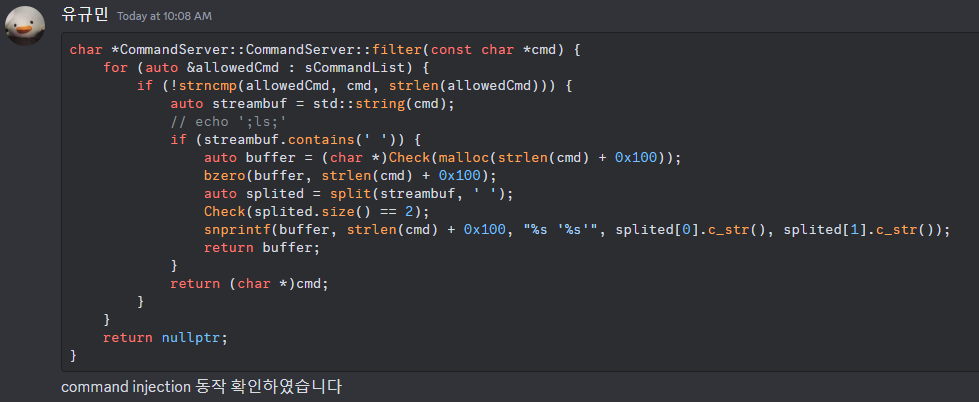
bool CommandServer::CommandServer::runcmd(const httplib::Request &request, std::string &result) {
std::ostringstream tmp;
auto cmd = request.get_param_value("command");
Check(!cmd.empty());
auto runCommand = Check(filter(cmd.c_str()));
std::cout << "Running command: " << runCommand << std::endl;
auto ret = exec(runCommand);
auto rdbuf = ret.rdbuf();
tmp << cmd;
tmp << "\n";
tmp << rdbuf;
result.append(tmp.str());
return true;
}
char *CommandServer::CommandServer::filter(const char *cmd) {
for (auto &allowedCmd : sCommandList) {
if (!strncmp(allowedCmd, cmd, strlen(allowedCmd))) {
auto streambuf = std::string(cmd);
if (streambuf.contains(' ')) {
auto buffer = (char *)Check(malloc(strlen(cmd) + 0x100));
bzero(buffer, strlen(cmd) + 0x100);
auto splited = split(streambuf, ' ');
Check(splited.size() == 2);
snprintf(buffer, strlen(cmd) + 0x100, "%s '%s'", splited[0].c_str(), res.c_str());
std::cout << buffer << std::endl;
return buffer;
}
return (char *)cmd;
}
}
return nullptr;
}보다시피 여기도 %s '%s' 로 sprintf 해주고 있다. 😑 막 command 삽입해버리고 싶은 마음이 들고 그럴 것이다. 역시나 echo ';ls;' 해본 결과 잘 실행됐다. 어떻게 패치할까 하다가 그냥 quote escape 처리 했다. + ` 처리까지.
std::string escapeSpecialChars(const std::string& input) {
std::string result;
for (char c : input) {
if (c == '\'') {
result += "'\\''";
} else if (c == '`') {
result += "\\`";
} else {
result += c;
}
}
return result;
}
char *CommandServer::CommandServer::filter(const char *cmd) {
for (auto &allowedCmd : sCommandList) {
if (!strncmp(allowedCmd, cmd, strlen(allowedCmd))) {
auto streambuf = std::string(cmd);
// echo ';ls;'
if (streambuf.contains(' ')) {
auto buffer = (char *)Check(malloc(strlen(cmd) + 0x100));
bzero(buffer, strlen(cmd) + 0x100);
auto splited = split(streambuf, ' ');
Check(splited.size() == 2);
std::string res = escapeSpecialChars(splited[1]);
snprintf(buffer, strlen(cmd) + 0x100, "%s '%s'", splited[0].c_str(), res.c_str());
std::cout << buffer << std::endl;
return buffer;
}
return (char *)cmd;
}
}
return nullptr;
}
방어 성공 ~
(왜인지 모르게 3개가 방어되어서 뭔가 싶었다)
남은 7시간 => 10p * 3/1h => 210p 방어 ~
Live Fire - 3 / UAF
갑자기 막 50점씩 깎이기 시작하는 점수를 보고 당황스러웠다. 한 두어 차례 어퍼컷 맞고 보니 서버를 잘못 돌리고 있었다. 백그라운드에서 돌아가는 run.sh 가 있는줄 모르고 따로 돌리고 있었는데, 이놈이 패킷을 나눠 먹으면서 비정상적인 결과로 이어지게 된 것이다. 😭
?! 바로 확인해보자
bool Server::Server::prepareTLEs() {
std::ifstream file;
file.open("/home/user/Livefire2024/src/Resource/tles.txt", std::ifstream::in);
Check(file.is_open());
std::string line, temp;
while (std::getline(file, line)) {
line.append("\n");
Check(line.length() == 70);
if (line.at(0) == '\x32') {
std::string TLE;
TLE.append("XXXX \n");
TLE.append(temp);
TLE.append(line);
Check(TLE.length() == 70 * 3);
auto number = Satellite::satellite_number(TLE);
auto it = m_satellites.find(number);
if (it != m_satellites.end()) { continue; }
auto object = std::unique_ptr<Satellite::Satellite>(new Satellite::Satellite(std::to_string(number), TLE));
m_satellites.insert(std::make_pair(number, std::move(object)));
m_numTLEs++;
} else {
temp = line;
}
}
return true;
}
..
m_server.Post("/register", [&](const httplib::Request &request, httplib::Response &response) {
m_mutex.lock();
SCOPE_EXIT({ m_mutex.unlock(); });
DEBUG_DUMP_REQUEST;
if (!m_authenticator.isAuthorized()) {
response.set_redirect("/");
}
auto content = std::make_unique<uint8_t[]>(0x1000);
bzero(content.get(), 0x1000);
auto name = request.get_param_value("name");
CheckVoid(!name.empty());
auto TLE = request.get_param_value("TLE");
auto pos = TLE.find("\n");
CheckVoid(pos != std::string::npos);
auto substr = TLE.substr(pos + 1);
auto number = Satellite::satellite_number(substr);
auto it = m_satellites.find(number);
if (it == m_satellites.end()) {
auto object = std::unique_ptr<Satellite::Satellite>(new Satellite::Satellite(name, TLE));
m_satellites.insert(std::make_pair(number, std::move(object)));
m_numTLEs++;
snprintf((char *)content.get(), 0x1000, "Success to register, Total TLEs: %d", m_numTLEs);
response.set_content((char *)content.get(), "text/plain");
} else {
snprintf((char *)content.get(), 0x1000, "Failed to register, Total TLEs: %d", m_numTLEs);
response.set_content((char *)content.get(), "text/plain");
}
});
m_server.Post("/unregister", [&](const httplib::Request &request, httplib::Response &response) {
m_mutex.lock();
SCOPE_EXIT({ m_mutex.unlock(); });
DEBUG_DUMP_REQUEST;
if (!m_authenticator.isAuthorized()) {
response.set_redirect("/");
}
auto numberAsStr = request.get_param_value("number");
CheckVoid(!numberAsStr.empty());
auto number = stoi(numberAsStr);
auto it = m_satellites.find(number);
if (it != m_satellites.end()) {
auto object = it->second.get();
m_satellites.erase(it);
response.set_content(object->dumpInfo(), "text/plain");
}
});prepareTLEs 에서 사전에 정의된 인공위성 정보들을 std::map<int, std::unique_ptr<Satellite::Satellite>> m_satellites 에 저장한다. 또 register 기능에서도 추가적인 TLE 를 등록할 수 있다. 이때 둘다 m_numTLEs 를 1 증가시키는데, unregister 에는 감소시키는 코드가 없길래 m_numTLEs-- 를 추가해주었다. 그리고 m_satellites.erase(it) 후 object->dumpInfo() 를 실행하는데 UAF로 인한 Segfault가 뜨는 것 같아서 erase 전에 미리 dumpInfo를 저장하고 리턴하는 식으로 바꿔줬다.
m_server.Post("/unregister", [&](const httplib::Request &request, httplib::Response &response) {
m_mutex.lock();
SCOPE_EXIT({ m_mutex.unlock(); });
DEBUG_DUMP_REQUEST;
if (!m_authenticator.isAuthorized()) {
response.set_redirect("/");
}
auto numberAsStr = request.get_param_value("number");
CheckVoid(!numberAsStr.empty());
auto number = stoi(numberAsStr);
auto it = m_satellites.find(number);
if (it != m_satellites.end()) {
auto object = it->second.get();
std::string res = object->dumpInfo();
m_numTLEs--;
m_satellites.erase(it);
response.set_content(res, "text/plain");
}
});남은 6시간 => 10p * 3/1h => 180 점 방어
Live Fire - 4 / statistic 정상화
m_server.Get("/statistic", [&](const httplib::Request &request, httplib::Response &response) {
std::string content;
m_mutex.lock();
SCOPE_EXIT({ m_mutex.unlock(); });
DEBUG_DUMP_REQUEST;
if (!m_authenticator.isAuthorized()) {
response.set_redirect("/");
}
for (auto const&it : m_satellites) {
auto satellite = it.second.get();
content.append(satellite->dumpInfo());
content.append("\n");
}
response.set_content(content, "text/plain");
}); 저장된 모든 인공위성들의 정보를 출력해주는 기능이 있다.
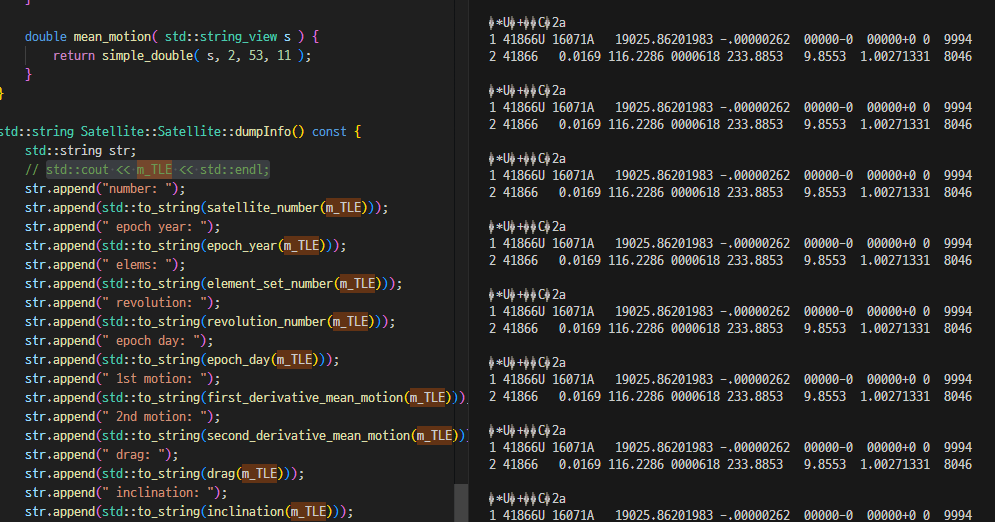
테스트 해봤는데 이게 뭐람 모두 같은 정보를 뱉고 있다. 특징이라면 마지막으로 등록되었던 41866 인공위성의 정보이다. 대개 이런 경우는 앞선 인공위성들의 정보를 가지는 m_TLE 문자열이 모두 41866 인공위성의 m_TLE로 덮어진 상태이다. 확인해본 결과 위 사진처럼 똑같은 문자열을 가지고 있었다.
// Server.cc
bool Server::Server::prepareTLEs() {
std::ifstream file;
file.open("/home/user/Livefire2024/src/Resource/tles.txt", std::ifstream::in);
Check(file.is_open());
std::string line, temp;
while (std::getline(file, line)) {
line.append("\n");
Check(line.length() == 70);
if (line.at(0) == '\x32') {
std::string TLE;
TLE.append("XXXX \n");
TLE.append(temp);
TLE.append(line);
Check(TLE.length() == 70 * 3);
auto number = Satellite::satellite_number(TLE);
auto it = m_satellites.find(number);
if (it != m_satellites.end()) { continue; }
auto object = std::unique_ptr<Satellite::Satellite>(new Satellite::Satellite(std::to_string(number), TLE));
m_satellites.insert(std::make_pair(number, std::move(object)));
m_numTLEs++;
} else {
temp = line;
}
}
return true;
}
//Satellite.h
class Satellite {
public:
Satellite(std::string_view name, std::string_view TLE) {
std::random_device rd;
m_name = (char *)malloc(name.length());
memcpy(m_name, name.data(), name.length());
m_TLE = std::move(TLE);
std::cout << "Adding new satellite " << name << std::endl;
std::mt19937 gen(rd());
std::normal_distribution<float> generator(0, 1);
m_location = std::make_pair(generator(gen) * 160 - 80, generator(gen) * 360 - 180);
}객체마다의 m_TLE 가 마지막의 TLE 를 가리킨다는 것은 prepareTLEs 내의 TLE 를 가리킨다는 것임을 알 수 있다
객체마다 다른 string 을 가리키도록 대충 땜빵해줬다 ㅋㅋ;
if (line.at(0) == '\x32') {
std::string* TLE = new std::string();
TLE->append("XXXX \n");
TLE->append(temp);
TLE->append(line);
Check((*TLE).length() == 70 * 3);
auto number = Satellite::satellite_number(*TLE);
auto it = m_satellites.find(number);
if (it != m_satellites.end()) { continue; }
auto object = std::unique_ptr<Satellite::Satellite>(new Satellite::Satellite(std::to_string(number), *TLE));
m_satellites.insert(std::make_pair(number, std::move(object)));
m_numTLEs++;
}
남은 6시간 => 180점 방어
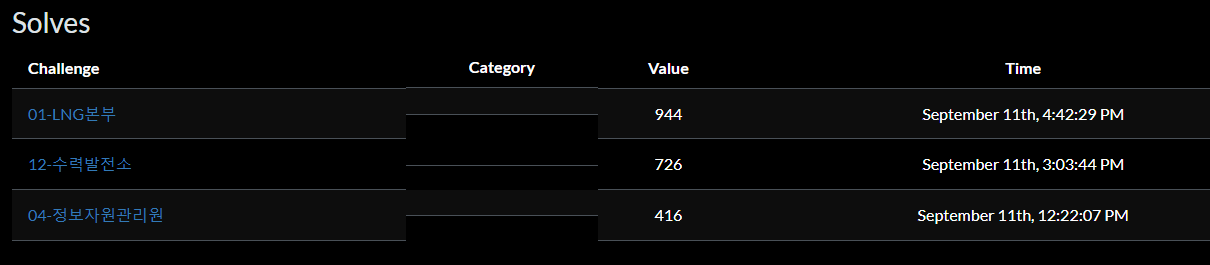
최소 점수 1200 점에서 방어 성공한 240 + 210 + 180 + 180 = 810 점을 더하여 우리 팀은 2010점 Live Fire 점수를 기록하였다.
문제 점수 2086 점과 더하면 4096점, 최종 점수가 나온다.
01. LNG 본부 (rev)
arm PE 파일과 암호화된 파일이 주어진다.
암호화 과정을 분석하여 복호화해야하는 문제일 것이다.
IDA로 슥 보면 바로 WinCrypt 라이브러리로 간단하게 암호화 진행하는 것을 볼 수 있고, 금방 풀릴 거라 예상했다.
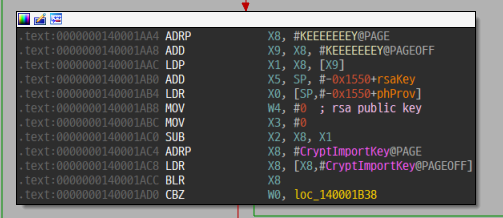
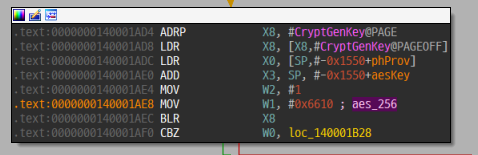
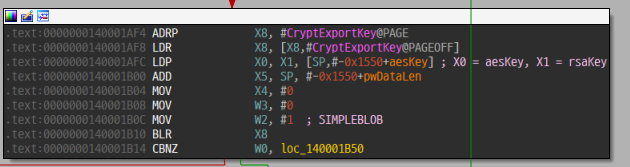
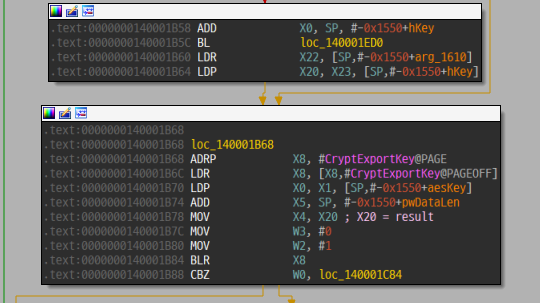
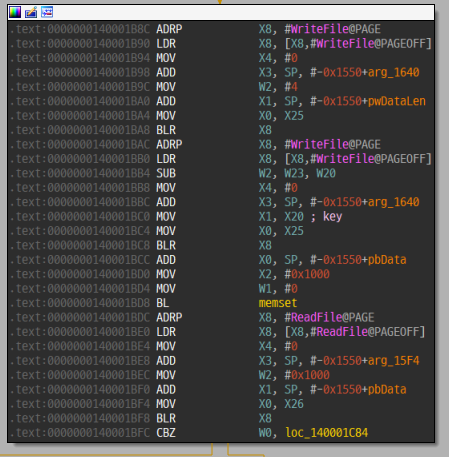
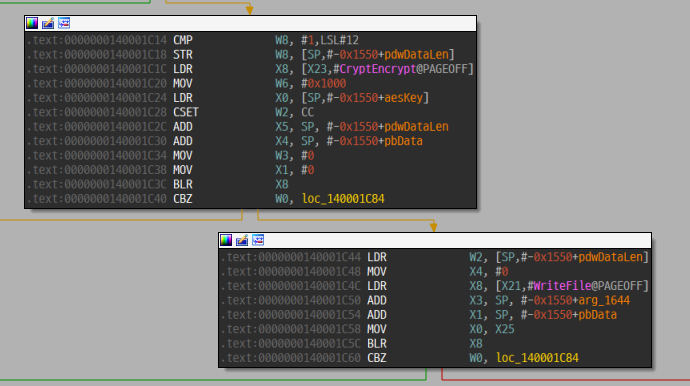
AES 256비트 키를 생성한 후 파일을 암호화한다. AES 키를 RSA 공개키로 암호화하여 암호화 파일 앞부분에 저장하는데, RSA 공개키는 바이너리 내에 짱박혀있다.
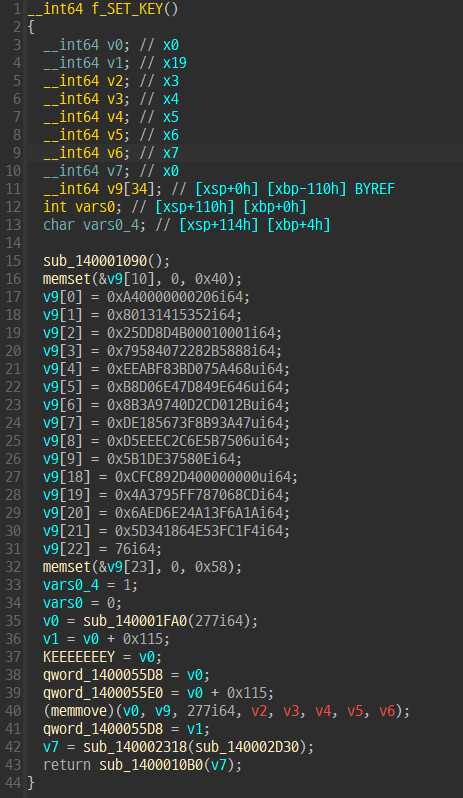
저 v9 에 저장되는 값을 뽑아보면
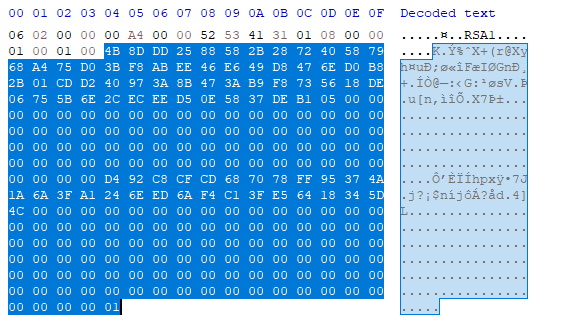
와 같은데 이는 PUBLICKEYBLOB 구조체 형식이다. CryptExportKey 할 때 PUBLICKEYBLOB 형식으로 내보낸 결과와 같은데 구조체는 다음과 같다.
그렇게 2049비트짜리 N 을 추출해보면(Little Endian 으로 저장됨)
N = 0x10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004c5d341864e53fc1f46aed6e24a13f6a1a4a3795ff787068cdcfc892d40000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005b1de37580ed5eeec2c6e5b7506de185673f8b93a478b3a9740d2cd012bb8d06e47d849e646eeabf83bd075a46879584072282b588825dd8d4b
보면 중간에 00이 엄청 많다. 딱 봐도 수상해보이길래 옆에 앉은 정웅이에게 보여줬다.
혼자 슥슥 하더니 노트에 이걸 적어서 보여줬다.
N = (2^1024 + a) * (2^1024 + b) = 2^2048 + 2^1024(a + b) + ab
WOW 😮 위 식이면 저 빵꾸 뚫린 N 을 설명할 수 있었다. 최상위의 1이 1 << 2048 이고, 중간에 4c5d341...2d4 는 2^1024(a+b), 5b1d..8d4b 는 ab 인 것이다.
a+b 와 ab를 알기 때문에 a 와 b 를 알 수 있고, 그 값은
from z3 import *
n = 0x10000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004c5d341864e53fc1f46aed6e24a13f6a1a4a3795ff787068cdcfc892d40000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005b1de37580ed5eeec2c6e5b7506de185673f8b93a478b3a9740d2cd012bb8d06e47d849e646eeabf83bd075a46879584072282b588825dd8d4b
5b1de37580ed5eeec2c6e5b7506de185673f8b93a478b3a9740d2cd012bb8d06e47d849e646eeabf83bd075a46879584072282b588825dd8d4b
pab = 0x4c5d341864e53fc1f46aed6e24a13f6a1a4a3795ff787068cdcfc892d4
ab = 0x5b1de37580ed5eeec2c6e5b7506de185673f8b93a478b3a9740d2cd012bb8d06e47d849e646eeabf83bd075a46879584072282b588825dd8d4b
a = Int('a')
b = Int('b')
s = Solver()
s.add(a > 0)
s.add(b > 0)
s.add(a * b == ab)
s.add(a + b == pab)
'''
s.check()
m = s.model()
[b = 1029385710293857012310298374019823740519823750198237501982375019825445,
a = 1029385710293857012310298374019823740519823750198237501982375019825583]
'''위와 같다.
그러면 p와 q는 각각 ((1 << 1024) + a), ((1 << 1024) + b) 가 되고 RSA 개인키를 구할 수 있게 되었다.
q = 1029385710293857012310298374019823740519823750198237501982375019825445
p = 1029385710293857012310298374019823740519823750198237501982375019825583
p, q = ((1 << 1024) + p), ((1 << 1024) + q)
assert p * q == n
e = 0x10001
phi = (p-1) * (q-1)
d = pow(e, -1, phi)그리고 삽질의 시간이 이어졌는데, WinCrypt 가 aes key 를 RSA 로 CryptExportKey 할 때 PKCS 패딩을 하는 것 같은데, python 으로 decrypt 할 때 자꾸 뻑났다. n 이 2049 비트인데 암호화된 데이터는 257 바이트, 이 두개가 PKCS와 RSA 사이에서 충돌? 이 일어난 것 같았다. 그래서 CryptExportKey 로 개인키를 PRIVATEKEYBLOB 구조체로 출력한 blob 을 직접 만들어서 cpp 코드에서 CryptImportKey 한 담에 CryptDecrypt 하는 꽤 멍청한 방법으로 aes key 를 복구했다. ks 님의 솔버를 보니 aes_key = long_to_bytes(pow(int.from_bytes(aes_key, 'little'), d, n))[::-1][:32][::-1] 와 같이 복구할 수 있었다. 시도를 해봤던 건데 little 엔디안으로 읽고 뒤집고 32바이트 가져오고 다시 뒤집는 구조를 아예 몰랐다 ㅋㅋ;
출제자분 솔버 보면 아래와 같은데(나도 저걸 바랐다.)
rsakey = RSA.construct((n, e, d))
cipher = PKCS1_v1_5.new(rsakey)
aes_key = cipher.decrypt(aes_key[::-1], None)PKCS1_v1_5 에 256바이트를 넘줘야 된다. 깔끔하게
#include <windows.h>
#include <wincrypt.h>
#include <stdio.h>
HCRYPTKEY* ImportRSAKey(HCRYPTPROV hProv) {
BYTE aa[] = {0x4B, 0x8D, 0xDD, 0x25, 0x88, 0x58, 0x2B, 0x28, 0x72, 0x40, 0x58, 0x79, 0x68, 0xA4, 0x75, 0xD0, 0x3B, 0xF8, 0xAB, 0xEE, 0x46, 0xE6, 0x49, 0xD8, 0x47, 0x6E, 0xD0, 0xB8, 0x2B, 0x01, 0xCD, 0xD2, 0x40, 0x97, 0x3A, 0x8B, 0x47, 0x3A, 0xB9, 0xF8, 0x73, 0x56, 0x18, 0xDE, 0x06, 0x75, 0x5B, 0x6E, 0x2C, 0xEC, 0xEE, 0xD5, 0x0E, 0x58, 0x37, 0xDE, 0xB1, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0xD4, 0x92, 0xC8, 0xCF, 0xCD, 0x68, 0x70, 0x78, 0xFF, 0x95, 0x37, 0x4A, 0x1A, 0x6A, 0x3F, 0xA1, 0x24, 0x6E, 0xED, 0x6A, 0xF4, 0xC1, 0x3F, 0xE5, 0x64, 0x18, 0x34, 0x5D, 0x4C, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0xAF, 0x49, 0xE4, 0xE7, 0x66, 0x34, 0x38, 0xBC, 0xFF, 0xCA, 0x1B, 0x25, 0x0D, 0xB5, 0x9F, 0x50, 0x12, 0xB7, 0x76, 0x35, 0xFA, 0xE0, 0x9F, 0x72, 0x32, 0x0C, 0x9A, 0x2E, 0x26, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x25, 0x49, 0xE4, 0xE7, 0x66, 0x34, 0x38, 0xBC, 0xFF, 0xCA, 0x1B, 0x25, 0x0D, 0xB5, 0x9F, 0x50, 0x12, 0xB7, 0x76, 0x35, 0xFA, 0xE0, 0x9F, 0x72, 0x32, 0x0C, 0x9A, 0x2E, 0x26, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x69, 0xF8, 0xF4, 0x6B, 0x2D, 0xD0, 0x1F, 0x22, 0x1D, 0xD0, 0x59, 0xFC, 0x0E, 0x93, 0xAA, 0xCE, 0x09, 0x64, 0xA4, 0x4F, 0x64, 0x12, 0x69, 0x33, 0xE8, 0xB6, 0x79, 0x36, 0xB8, 0x91, 0xBA, 0x4E, 0x25, 0x71, 0x9C, 0xDF, 0x6C, 0x94, 0x70, 0xC8, 0xD2, 0xAA, 0xF2, 0xE6, 0x2E, 0x20, 0x83, 0xC0, 0x60, 0xAF, 0x4C, 0xF0, 0xA5, 0x80, 0xD8, 0xE9, 0x01, 0x51, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xA0, 0x4C, 0x5F, 0xB3, 0xD6, 0x44, 0x6C, 0x8A, 0x28, 0xF7, 0xC1, 0xE4, 0xFB, 0xB4, 0x25, 0xA9, 0xFC, 0x8C, 0x7A, 0xFB, 0x74, 0xBA, 0x67, 0xDE, 0x30, 0x3F, 0xD7, 0xD8, 0x24, 0x08, 0xBA, 0x7F, 0x58, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0x1D, 0x3B, 0xE2, 0xC4, 0xCD, 0x8A, 0x46, 0x94, 0x53, 0xE6, 0x5C, 0xDB, 0x38, 0x79, 0xC4, 0xCC, 0xC7, 0x3F, 0x85, 0x4A, 0xA9, 0x86, 0xEC, 0xD1, 0x8B, 0x2A, 0xFC, 0x02, 0xD0, 0x72, 0x1A, 0xCD, 0xF0, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0xE5, 0xB2, 0x1A, 0x4D, 0x83, 0x73, 0xA4, 0x38, 0xFC, 0x0B, 0x61, 0x11, 0x32, 0xD0, 0x22, 0x82, 0x19, 0x48, 0xA4, 0xD3, 0xB0, 0x23, 0x25, 0xF2, 0xF3, 0x5A, 0x31, 0xF6, 0xBE, 0x5E, 0xC5, 0x9A, 0xDF, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0xD9, 0xD4, 0x26, 0x2B, 0x27, 0x2C, 0x8C, 0x7C, 0x6C, 0x91, 0x05, 0xDD, 0xB3, 0xDD, 0x66, 0x39, 0x66, 0x94, 0x3A, 0xA1, 0x5C, 0x50, 0xFC, 0x34, 0x3F, 0x57, 0x3E, 0xF9, 0x9B, 0x90, 0xE3, 0x66, 0xD7, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0xCC, 0xB5, 0x03, 0x73, 0xED, 0xC0, 0x5C, 0x3B, 0x30, 0xD7, 0x0E, 0x4C};
DWORD bitlen = 2049;
BLOBHEADER blobHeader;
blobHeader.bType = PRIVATEKEYBLOB;
blobHeader.bVersion = 0x02;
blobHeader.reserved = 0;
blobHeader.aiKeyAlg = CALG_RSA_KEYX;
RSAPUBKEY rsaPubKey;
rsaPubKey.magic = 0x32415352;
rsaPubKey.bitlen = bitlen;
rsaPubKey.pubexp = 65537;
DWORD blobSize = sizeof(BLOBHEADER) + sizeof(RSAPUBKEY) +
bitlen / 8 * 7;
BYTE *keyBlob = (BYTE*)malloc(blobSize);
BYTE *ptr = keyBlob;
memcpy(ptr, &blobHeader, sizeof(BLOBHEADER));
ptr += sizeof(BLOBHEADER);
memcpy(ptr, &rsaPubKey, sizeof(RSAPUBKEY));
ptr += sizeof(RSAPUBKEY);
memcpy(ptr, aa, sizeof(aa));
ptr += sizeof(aa);
HCRYPTKEY* hKey = (HCRYPTKEY*) malloc(sizeof(HCRYPTKEY));
if (!CryptImportKey(hProv, keyBlob, blobSize, 0, 0, hKey)) {
printf("CryptImportKey failed: %d\n", GetLastError());
} else {
printf("Key imported successfully\n");
}
free(keyBlob);
return hKey;
}
BOOL DecryptAESKey(HCRYPTKEY hPrivateKey, const BYTE* pbEncryptedAESKey, DWORD dwEncryptedAESKeyLen, BYTE** ppDecryptedAESKey, DWORD* pdwDecryptedAESKeyLen) {
*pdwDecryptedAESKeyLen = dwEncryptedAESKeyLen;
*ppDecryptedAESKey = (BYTE*)malloc(*pdwDecryptedAESKeyLen);
if (*ppDecryptedAESKey == NULL) {
printf("Memory allocation failed\n");
return FALSE;
}
memcpy(*ppDecryptedAESKey, pbEncryptedAESKey, dwEncryptedAESKeyLen);
if (!CryptDecrypt(hPrivateKey, 0, TRUE, 0, *ppDecryptedAESKey, pdwDecryptedAESKeyLen)) {
printf("CryptDecrypt failed: %d\n", GetLastError());
free(*ppDecryptedAESKey);
return FALSE;
}
return TRUE;
}
int main() {
HCRYPTPROV hProv;
if (!CryptAcquireContext(&hProv, NULL, MS_ENHANCED_PROV, PROV_RSA_FULL, CRYPT_VERIFYCONTEXT)) {
printf("CryptAcquireContext failed: %d\n", GetLastError());
return 1;
}
BYTE encryptedAESKey[] = { 0xB5, 0x14, 0x9D, 0x1F, 0x12, 0x0B, 0x68, 0xF8, 0xF0, 0x9B, 0xD0, 0x53, 0xFB, 0x04, 0x60, 0xDF, 0xE8, 0xEB, 0x70, 0x8D, 0x28, 0xEA, 0x51, 0xAE, 0xCB, 0xBC, 0x0C, 0x40, 0xFD, 0x8B, 0x72, 0x89, 0xE9, 0x52, 0x5E, 0x32, 0xCF, 0x93, 0x72, 0x0C, 0x83, 0x62, 0xC5, 0xC3, 0xCF, 0xFD, 0xBB, 0x03, 0x3A, 0x19, 0xA0, 0x49, 0x33, 0x0B, 0x29, 0x2B, 0x19, 0x13, 0xB2, 0x1C, 0xD4, 0x83, 0x41, 0x82, 0xF2, 0xEC, 0xD5, 0x3C, 0xAD, 0x66, 0xD7, 0xDA, 0x83, 0x31, 0x8D, 0x0F, 0x01, 0xE3, 0x25, 0xBE, 0x50, 0x52, 0xBE, 0x1C, 0x7A, 0x0D, 0x12, 0x4F, 0x82, 0x7C, 0x48, 0x15, 0x32, 0xF1, 0xD5, 0x76, 0x42, 0x77, 0x02, 0x2F, 0x39, 0x3D, 0x14, 0x21, 0x7F, 0x24, 0x80, 0x51, 0x6B, 0xE2, 0xCA, 0xDF, 0xEB, 0xC5, 0x76, 0x17, 0x0F, 0x3E, 0x57, 0xB3, 0x27, 0x7A, 0x59, 0xAC, 0x12, 0x08, 0x9D, 0x0C, 0xAE, 0x9F, 0x65, 0xDB, 0xBE, 0x60, 0x31, 0x9D, 0xA1, 0xD6, 0x2D, 0xEF, 0x91, 0x66, 0x2C, 0x24, 0x21, 0xC2, 0xF5, 0x82, 0x4B, 0xA7, 0xE1, 0x79, 0x23, 0x68, 0x7C, 0xBE, 0x59, 0xF0, 0x55, 0xB8, 0x1B, 0xB9, 0xF6, 0x3A, 0xDB, 0x24, 0xED, 0x9D, 0x5A, 0xAC, 0xB2, 0x43, 0x1C, 0xF2, 0x31, 0xB3, 0x82, 0x35, 0x36, 0xD4, 0xDC, 0xE0, 0xB8, 0xB8, 0x4B, 0xCB, 0xAE, 0xFE, 0xE7, 0x0B, 0x85, 0x37, 0x13, 0xFC, 0x26, 0xBF, 0x49, 0x20, 0xC3, 0xCC, 0x22, 0x5D, 0xA6, 0x1F, 0x1F, 0xE8, 0x07, 0xE2, 0x96, 0xE5, 0x4B, 0x73, 0x61, 0xD1, 0x82, 0x67, 0x7C, 0x4F, 0xFC, 0xF0, 0x97, 0x49, 0x11, 0x88, 0x7C, 0x27, 0x65, 0x8C, 0x73, 0x4D, 0x36, 0x56, 0xC7, 0x10, 0x36, 0x90, 0x0E, 0xD6, 0xA9, 0xC1, 0xEB, 0x61, 0x09, 0xC5, 0x93, 0x54, 0x0F, 0xAB, 0xAD, 0xBF, 0x7A, 0x2F, 0x5C, 0x3E, 0x9B, 0x4B, 0x00 };
DWORD encryptedAESKeyLen = sizeof(encryptedAESKey);
HCRYPTKEY* hPrivateKey = ImportRSAKey(hProv);
BYTE* decryptedAESKey = NULL;
DWORD decryptedAESKeyLen = 0;
if (DecryptAESKey(*hPrivateKey, encryptedAESKey, encryptedAESKeyLen, &decryptedAESKey, &decryptedAESKeyLen)) {
printf("Decrypted AES Key: ");
for (DWORD i = 0; i < decryptedAESKeyLen; i++) {
printf("%02X", decryptedAESKey[i]);
}
printf("\n");
free(decryptedAESKey);
} else {
printf("Failed to decrypt AES key\n");
}
CryptReleaseContext(hProv, 0);
return 0;
}GPT 가 짜준 코드를 실행해보면
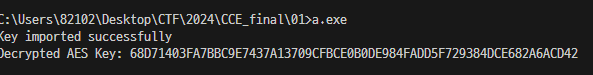
👍👍👍
aes_key = bytes.fromhex('68D71403FA7BBC9E7437A13709CFBCE0B0DE984FADD5F729384DCE682A6ACD42')
print(f'Decrypted aes key : ', len(aes_key), aes_key.hex())
i = 4 + size
cipher = AES.new(aes_key, AES.MODE_CBC)
out = b''
while i < len(enc):
data = enc[i:i+1024]
out += cipher.decrypt(data)
i += 1024
open('./important.pdf', 'wb').write(out)IV 땜에 맨 앞 16바이트가 깨진다.
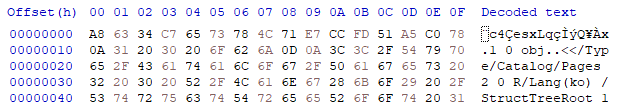
정상 pdf 파일 앞부분으로 바꿔치기
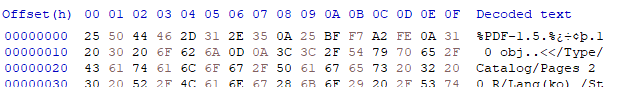
복구 완료~