awscli
- PATH에 aws 설치 경로 추가
root@master:~# PATH=/root/.local/bin/:$PATH - aws configure
root@master:~# aws configure
AWS Access Key ID [None]: ****
AWS Secret Access Key [None]: ****
Default region name [None]: ap-northeast-1
Default output format [None]: CloudFormation
- base-resources-tokyo.yaml
AWSTemplateFormatVersion: '2010-09-09'
Parameters:
ClusterBaseName:
Type: String
Default: eks-work
TargetRegion:
Type: String
Default: ap-northeast-1
AvailabilityZone1:
Type: String
Default: ap-northeast-1a
AvailabilityZone2:
Type: String
Default: ap-northeast-1c
AvailabilityZone3:
Type: String
Default: ap-northeast-1d
VpcBlock:
Type: String
Default: 192.168.0.0/16
WorkerSubnet1Block:
Type: String
Default: 192.168.0.0/24
WorkerSubnet2Block:
Type: String
Default: 192.168.1.0/24
WorkerSubnet3Block:
Type: String
Default: 192.168.2.0/24
Resources:
EksWorkVPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: !Ref VpcBlock
EnableDnsSupport: true
EnableDnsHostnames: true
Tags:
- Key: Name
Value: !Sub ${ClusterBaseName}-VPC
WorkerSubnet1:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Ref AvailabilityZone1
CidrBlock: !Ref WorkerSubnet1Block
VpcId: !Ref EksWorkVPC
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub ${ClusterBaseName}-WorkerSubnet1
WorkerSubnet2:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Ref AvailabilityZone2
CidrBlock: !Ref WorkerSubnet2Block
VpcId: !Ref EksWorkVPC
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub ${ClusterBaseName}-WorkerSubnet2
WorkerSubnet3:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: !Ref AvailabilityZone3
CidrBlock: !Ref WorkerSubnet3Block
VpcId: !Ref EksWorkVPC
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub ${ClusterBaseName}-WorkerSubnet3
InternetGateway:
Type: AWS::EC2::InternetGateway
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
InternetGatewayId: !Ref InternetGateway
VpcId: !Ref EksWorkVPC
WorkerSubnetRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref EksWorkVPC
Tags:
- Key: Name
Value: !Sub ${ClusterBaseName}-WorkerSubnetRouteTable
WorkerSubnetRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref WorkerSubnetRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
WorkerSubnet1RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref WorkerSubnet1
RouteTableId: !Ref WorkerSubnetRouteTable
WorkerSubnet2RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref WorkerSubnet2
RouteTableId: !Ref WorkerSubnetRouteTable
WorkerSubnet3RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref WorkerSubnet3
RouteTableId: !Ref WorkerSubnetRouteTable
Outputs:
VPC:
Value: !Ref EksWorkVPC
WorkerSubnets:
Value: !Join
- ","
- [!Ref WorkerSubnet1, !Ref WorkerSubnet2, !Ref WorkerSubnet3]
RouteTable:
Value: !Ref WorkerSubnetRouteTableRouteTable rtb-0230488da3e7a77c5 - -
VPC vpc-037241cb5a836aae6 - -
WorkerSubnets
- subnet-027c9798d2190760a,subnet-0800adf69c21ae48c,subnet-0cbb58cc47d042f4cEKS
- 클러스터 생성
eksctl create cluster \
--vpc-public-subnets subnet-027c9798d2190760a,subnet-0800adf69c21ae48c,subnet-0cbb58cc47d042f4c \
--name eks-work-cluster \
--region ap-northeast-1 \
--nodegroup-name eks-work-nodegroup \
--version 1.20 \
--node-type t2.small \
--nodes 2 \
--nodes-min 2 \
--nodes-max 4 - lb, deploy 배포
apiVersion: v1
kind: Namespace
metadata:
name: sk
---
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: sk # NameSpace
name: sk-deploy
spec: # Replcaset 설정
strategy:
type: Recreate # Rolling Update 방식이 아닌 Recreate 방식
replicas: 3
selector: # 아래의 label 개수를 확인하여 pod 관리
matchLabels:
app: sk # label은 app: sk
template: # Pod 구성
metadata:
labels:
app: sk
spec: # 컨테이너 구성
containers:
- name: sk-nginx # 컨테이너 이름
image: nginx
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
namespace: sk
name: sk-lb
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
spec:
externalTrafficPolicy: Local
ports:
- port: 80
targetPort: 80
selector:
app: sk
type: LoadBalancerECR
394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp
- 도커 로그인
root@master:~/k8slab# aws ecr get-login-password --region ap-northeast-1 \
> | docker login --username AWS --password-stdin 394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded- 테스트 이미지 풀
root@master:~/k8slab# docker pull httpd
Using default tag: latest
latest: Pulling from library/httpd
Digest: sha256:5fa96551b61359de5dfb7fd8c9e97e4153232eb520a8e883e2f47fc80dbfc33e
Status: Image is up to date for httpd:latest
docker.io/library/httpd:latest- 이미지 태그 생성
root@master:~/k8slab# docker tag \
httpd:latest \
394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp:1.0 - 푸쉬
root@master:~/k8slab# docker push 394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp:1.0
The push refers to repository [394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp]
1617cfaff5dd: Pushed
36de10a434ef: Pushed
6437b1170b0b: Pushed
13fb8799144c: Pushed
a12586ed027f: Pushed
1.0: digest: sha256:8c353fea0ce30e79d03e487d31f3a37eb5aae5127bde9580387e74e77c5952a2 size: 1366- 확인
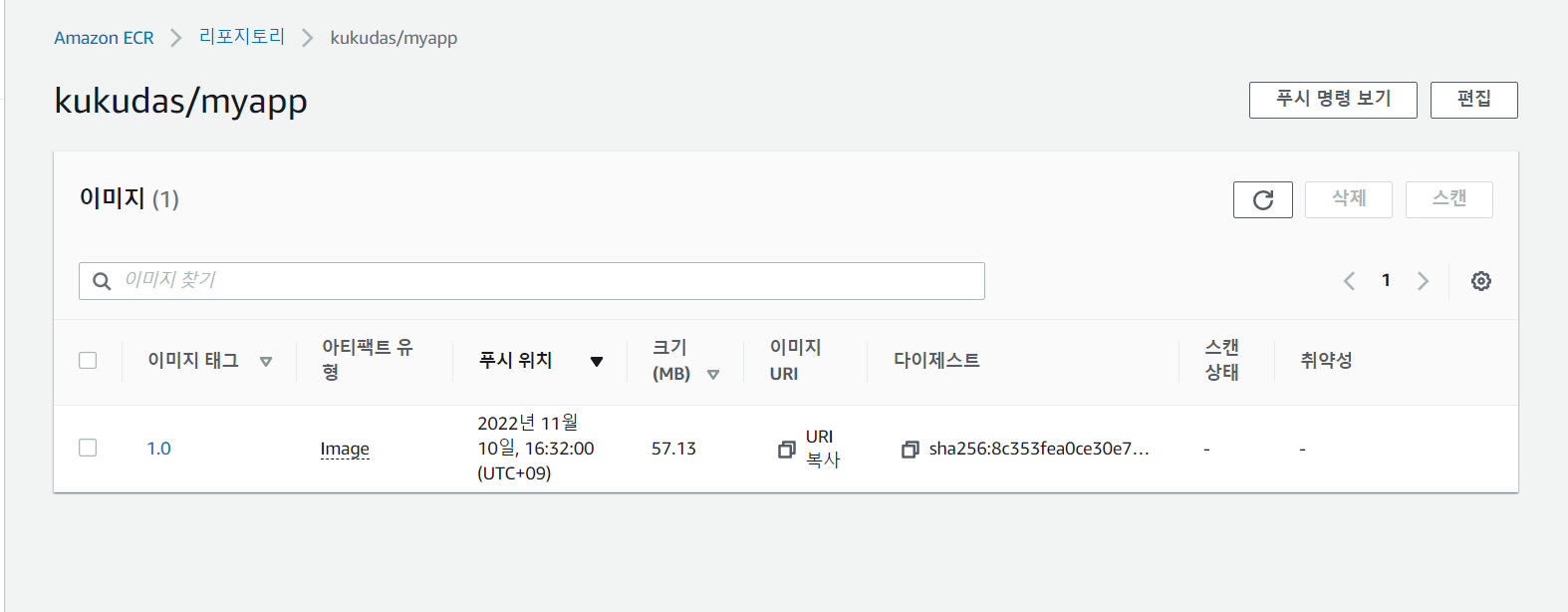
- 배포!
apiVersion: v1
kind: Namespace
metadata:
name: sk
---
apiVersion: apps/v1
kind: Deployment
metadata:
namespace: sk # NameSpace
name: sk-deploy
spec: # Replcaset 설정
strategy:
type: Recreate # Rolling Update 방식이 아닌 Recreate 방식
replicas: 3
selector: # 아래의 label 개수를 확인하여 pod 관리
matchLabels:
app: sk # label은 app: sk
template: # Pod 구성
metadata:
labels:
app: sk
spec: # 컨테이너 구성
containers:
- name: sk-nginx # 컨테이너 이름
image: 394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp:1.0
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
namespace: sk
name: sk-lb
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
spec:
externalTrafficPolicy: Local
ports:
- port: 80
targetPort: 80
selector:
app: sk
type: LoadBalancerimage: 394652119040.dkr.ecr.ap-northeast-1.amazonaws.com/kukudas/myapp:1.0
- 이미지 pull 후 배포 성공 확인