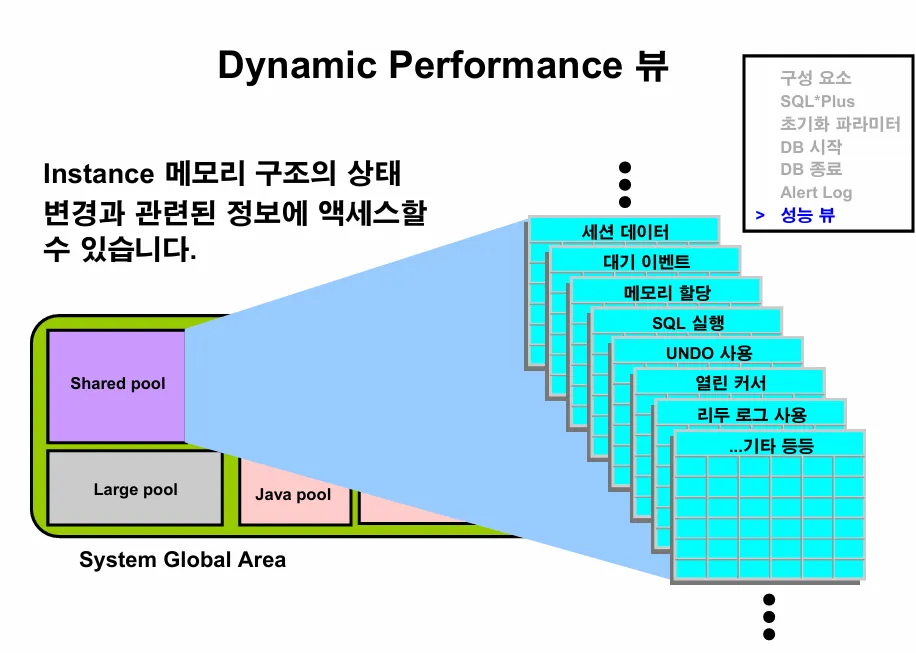
이론1. v$로 시작하는 다이나믹 퍼포먼스 뷰
- 오라클 성능 진단을 위한 데이터가 있는 데이터 사전
이론2. 어떤 성능 정보를 볼 수 있나요?
- 악성 SQL을 찾을 수 있게 해줍니다. (VSQLTEXT)
- 지금 현재 작업을 못하고 Waiting 하는 세션들을 조회할 수 있게 해줍니다.
( VSESSION_WAIT ) - 락(lock)이 발생했을 때 락 홀더와 waiter 를 찾을 수 있게 해줍니다.
( V$LOCK) - 대량 데이터를 update 할 때 취소해야할 데이터(undo) 가 얼마나
되는지 모니터링할 수 있게 해줍니다. ( V$UNDO_XXX )
이론3. v$ 로 시작하는 다이나믹 퍼포먼스 뷰의 소유자는?
- sys 유저
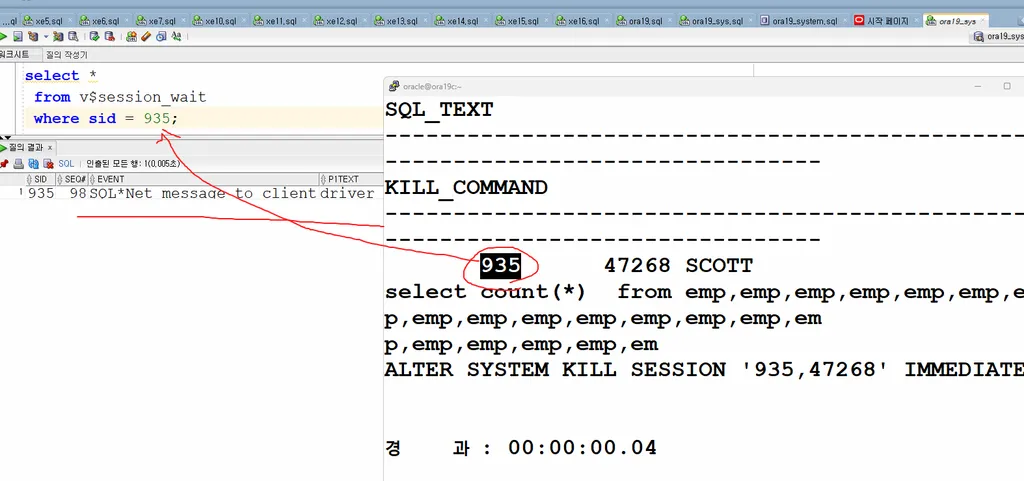
실습1. 악성 SQL을 수행하고 이 악성 SQL을 수행하는 세션정보와 관련 SQL을 조회하시오
[oracle@ora19c ~]$ cat bad.sql
col username for a10
-- 높은 리소스를 사용하는 SQL 세션
WITH resource_intensive AS (
SELECT
sql_id,
sql_text,
executions,
disk_reads,
buffer_gets,
cpu_time/1000000 AS cpu_seconds,
elapsed_time/1000000 AS elapsed_seconds,
CASE
WHEN executions > 0 THEN ROUND(disk_reads/executions, 2)
ELSE disk_reads
END AS disk_reads_per_exec,
CASE
WHEN executions > 0 THEN ROUND(buffer_gets/executions, 2)
ELSE buffer_gets
END AS buffer_gets_per_exec
FROM v$sqlarea
WHERE (disk_reads > 100000 OR buffer_gets > 1000000 OR cpu_time > 10000000)
)
SELECT
s.sid,
s.serial#,
s.username,
SUBSTR(ri.sql_text, 1, 100) AS sql_text,
'ALTER SYSTEM KILL SESSION ''' || s.sid || ',' || s.serial# || ''' IMMEDIATE;' AS kill_command
FROM
v$session s,
resource_intensive ri,
v$sqlarea sa
WHERE
s.sql_address = sa.address
AND s.sql_hash_value = sa.hash_value
AND sa.sql_id = ri.sql_id
AND s.username IS NOT NULL
ORDER BY ri.cpu_seconds DESC, ri.disk_reads DESC;
exit;scott 유져에서 악성 SQL을 수행하고 다른 창에서 dba.sh 를 실행해서 악성 SQL을 찾습니다.
실습3. vsession_wait 를 조인해서 현재 waiting 하는 세션이 왜 느린지 대기이벤트를 확인하시오
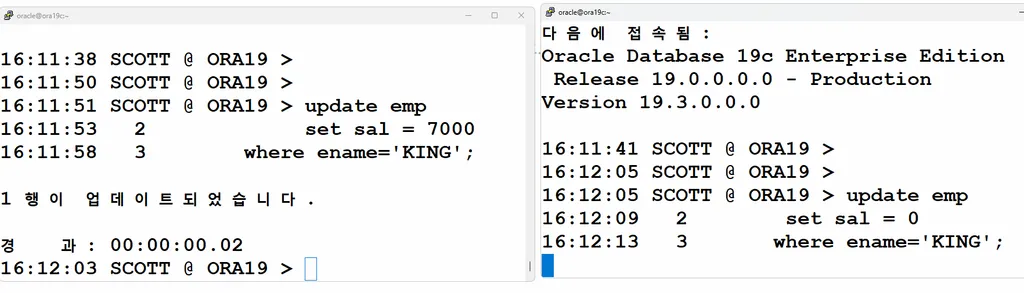
실습4. scott 으로 putty 창을 2개를 열고 접속해서 락이 발생할 수 있도록 update 를 하고 dba.sh 를 이용해서 락을 확인하시오
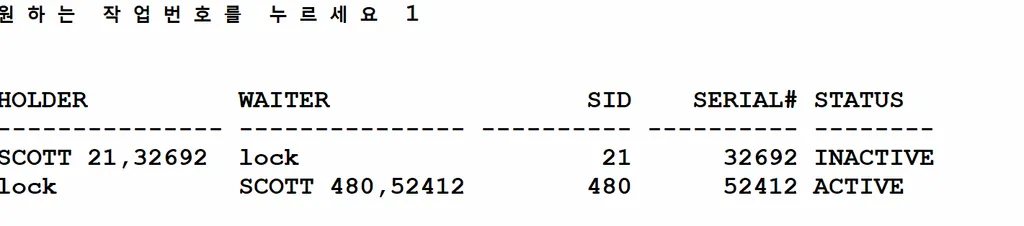
실습5. lock에 관련한 dynamic performce view를 조회하시오
select *
from v$fixed_table
where name like '%V$%LOCK%';