[과제 1]
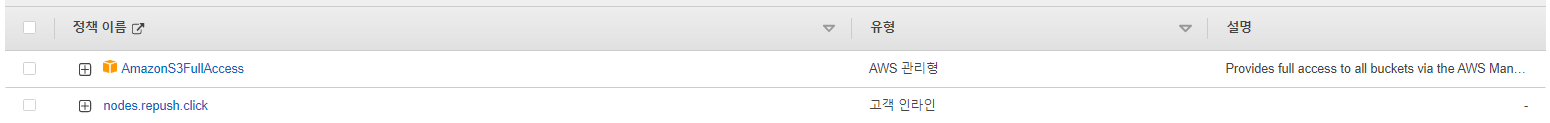
파드에서 EC2 메타데이터의 IAM Role 토큰 정보를 활용하여(boto3), 스터디에서 소개한 것 이외의 다른 AWS 서비스(혹은 Action)를 사용 후 코드나 스샷을 올려주세요
사전준비
cat <<EOF | kubectl create -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: boto3-pod
spec:
replicas: 2
selector:
matchLabels:
app: boto3
template:
metadata:
labels:
app: boto3
spec:
containers:
- name: boto3
image: jpbarto/boto3
command: ["tail"]
args: ["-f", "/dev/null"]
terminationGracePeriodSeconds: 0
EOFPODNAME1=$(kubectl get pod -l app=boto3 -o jsonpath={.items[0].metadata.name})
PODNAME2=$(kubectl get pod -l app=boto3 -o jsonpath={.items[1].metadata.name})kubectl exec -it $PODNAME1 -- shcat <<EOF> s3.py
import boto3
s3 = boto3.client('s3')
response = s3.list_buckets()
print(response)
EOFpython s3.py~/dev # python s3.py
{u'Owner': {u'DisplayName': 'repush', u'ID': '2500c91536f25f0897e7e1ea8859a5274ab813f9c045915b42179cf4f63eb267'}, u'Buckets': [{u'CreationDate': datetime.datetime(2023, 2, 23, 7, 46, 14, tzinfo=tzlocal()), u'Name': 'gitlab-runner-manager-repush'}, {u'CreationDate': datetime.datetime(2023, 2, 21, 13, 41, 31, tzinfo=tzlocal()), u'Name': 'grafana-alert-images-repush'}, {u'CreationDate': datetime.datetime(2023, 1, 19, 13, 58, 36, tzinfo=tzlocal()), u'Name': 'repush-gasida'}], 'ResponseMetadata': {'HTTPStatusCode': 200, 'RetryAttempts': 0, 'HostId': 'kOIXvO3KGJoi5JaQCEvPqlNou5q3qkZiO/imlczedW4s5/nz/gCV1XiiMsNvhRdo7CRpR9Y9F9o=', 'RequestId': '3AD880JB6CP8GKMP', 'HTTPHeaders': {'x-amz-id-2': 'kOIXvO3KGJoi5JaQCEvPqlNou5q3qkZiO/imlczedW4s5/nz/gCV1XiiMsNvhRdo7CRpR9Y9F9o=', 'server': 'AmazonS3', 'transfer-encoding': 'chunked', 'x-amz-request-id': '3AD880JB6CP8GKMP', 'date': 'Mon, 27 Feb 2023 14:17:01 GMT', 'content-type': 'application/xml'}}}
~/dev #
[과제 2]
책 398~400페이지 - kubescape armo 웹 사용 후 관련 스샷을 올려주세요
(repush:N/A) [root@kops-ec2 ~]# curl -s https://raw.githubusercontent.com/kubescape/kubescape/master/install.sh | /bin/bash
Installing Kubescape...
######################################################################## 100.0%
Finished Installation.
Your current version is: v2.2.2 [git enabled in build: true]
Usage: $ kubescape scan --enable-host-scan
(repush:N/A) [root@kops-ec2 ~]# kubescape scan . --submit --account 23cf3d63-75ca-4426-a109-7f6771270514
[info] Kubescape scanner starting
[info] Downloading/Loading policy definitions
[success] Downloaded/Loaded policy
[info] Accessing local objects
[success] Done accessing local objects
[info] Scanning Directory
Control C-0128 100% |█████████████████████████████████████████████████████████████████████████████████████████████| (211/211, 17 it/s)
[success] Done scanning Directory
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
Controls: 211 (Failed: 41, Passed: 164, Action Required: 6)
Failed Resources by Severity: Critical — 0, High — 45, Medium — 173, Low — 66
+----------+-------------------------------------------------------+------------------+---------------+-------------------+
| SEVERITY | CONTROL NAME | FAILED RESOURCES | ALL RESOURCES | % RISK-SCORE |
+----------+-------------------------------------------------------+------------------+---------------+-------------------+
| High | Forbidden Container Registries | 0 | 13 | Action Required * |
| High | Resources memory limit and request | 0 | 13 | Action Required * |
| High | Resource limits | 13 | 13 | 100% |
| High | Applications credentials in configuration files | 0 | 14 | Action Required * |
| High | Resources CPU limit and request | 0 | 13 | Action Required * |
| High | CIS-5.2.2 Minimize the admission of privileged con... | 3 | 3 | 100% |
| High | CIS-5.2.11 Minimize the admission of Windows HostP... | 3 | 3 | 100% |
| High | CIS-5.7.3 Apply Security Context to Your Pods and ... | 13 | 13 | 100% |
| High | Verify image signature | 0 | 13 | Action Required * |
| High | Check if signature exists | 13 | 13 | 100% |
| Medium | Data Destruction | 1 | 1 | 100% |
| Medium | Non-root containers | 13 | 13 | 100% |
| Medium | Allow privilege escalation | 13 | 13 | 100% |
| Medium | Ingress and Egress blocked | 13 | 13 | 100% |
| Medium | Automatic mapping of service account | 2 | 14 | 11% |
| Medium | Access container service account | 1 | 1 | 100% |
| Medium | Cluster internal networking | 3 | 3 | 100% |
| Medium | Linux hardening | 13 | 13 | 100% |
| Medium | Configured liveness probe | 13 | 13 | 100% |
| Medium | CIS-5.1.4 Minimize Container Registries to only th... | 0 | 13 | Action Required * |
| Medium | CVE-2022-0492-cgroups-container-escape | 13 | 13 | 100% |
| Medium | CIS-5.1.4 Minimize access to create pods | 1 | 1 | 100% |
| Medium | CIS-5.1.5 Ensure that default service accounts are... | 2 | 3 | 67% |
| Medium | CIS-5.1.6 Ensure that Service Account Tokens are o... | 2 | 14 | 11% |
| Medium | CIS-5.2.1 Ensure that the cluster has at least one... | 3 | 3 | 100% |
| Medium | CIS-5.2.3 Minimize the admission of containers wis... | 3 | 3 | 100% |
| Medium | CIS-5.2.4 Minimize the admission of containers wis... | 3 | 3 | 100% |
| Medium | CIS-5.2.5 Minimize the admission of containers wis... | 3 | 3 | 100% |
| Medium | CIS-5.2.6 Minimize the admission of containers wit... | 3 | 3 | 100% |
| Medium | CIS-5.2.7 Minimize the admission of root container... | 3 | 3 | 100% |
| Medium | CIS-5.2.8 Minimize the admission of containers wit... | 3 | 3 | 100% |
| Medium | CIS-5.2.9 Minimize the admission of containers wit... | 3 | 3 | 100% |
| Medium | CIS-5.2.10 Minimize the admission of containers wi... | 3 | 3 | 100% |
| Medium | CIS-5.2.12 Minimize the admission of HostPath volu... | 3 | 3 | 100% |
| Medium | CIS-5.2.13 Minimize the admission of containers wh... | 3 | 3 | 100% |
| Medium | CIS-5.3.2 Ensure that all Namespaces have Network ... | 3 | 3 | 100% |
| Medium | CIS-5.7.1 Create administrative boundaries between... | 3 | 3 | 100% |
| Medium | CIS-5.7.2 Ensure that the seccomp profile is set t... | 13 | 13 | 100% |
| Medium | CIS-5.7.4 The default namespace should not be used | 18 | 25 | 68% |
| Medium | CIS-4.4.2 Consider external secret storage | 13 | 13 | 100% |
| Low | Immutable container filesystem | 13 | 13 | 100% |
| Low | Configured readiness probe | 13 | 13 | 100% |
| Low | Network mapping | 3 | 3 | 100% |
| Low | Pods in default namespace | 10 | 13 | 70% |
| Low | Naked PODs | 6 | 6 | 100% |
| Low | Label usage for resources | 8 | 13 | 65% |
| Low | K8s common labels usage | 13 | 13 | 100% |
+----------+-------------------------------------------------------+------------------+---------------+-------------------+
| | RESOURCE SUMMARY | 26 | 31 | 41.52% |
+----------+-------------------------------------------------------+------------------+---------------+-------------------+
FRAMEWORKS: AllControls (risk: 31.68), NSA (risk: 41.13), MITRE (risk: 3.19), AllControls (risk: 31.68), ArmoBest (risk: 39.05), NSA (risk: 41.13), cis-eks-t1.2.0 (risk: 41.36), cis-v1.23-t1.0.1 (risk: 67.37), DevOpsBest (risk: 31.91), MITRE (risk: 3.19)
* Control configurations are empty
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Scan results have not been submitted:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Run with '--verbose'/'-v' flag for detailed resources view
(repush:N/A) [root@kops-ec2 ~]#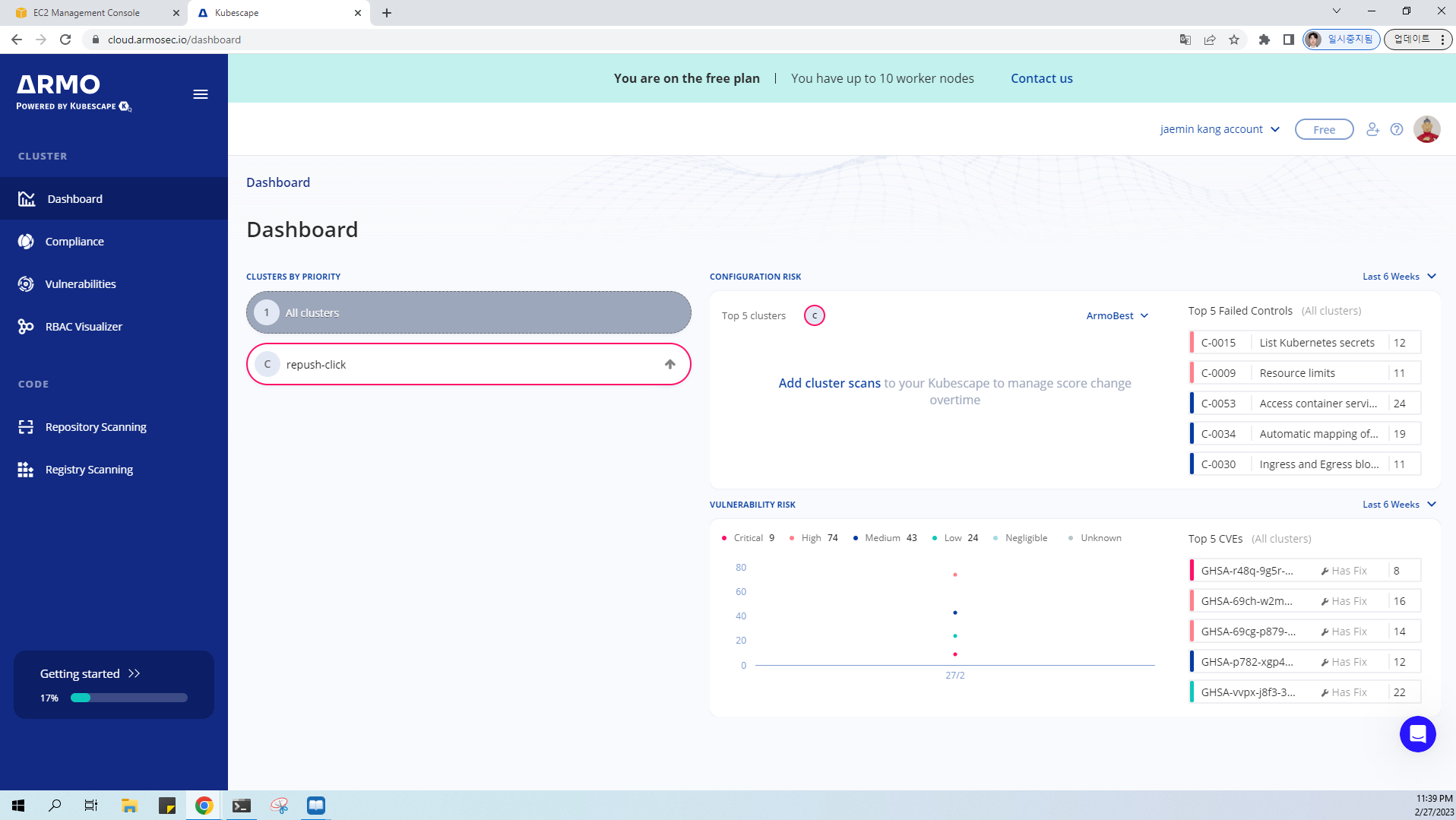
[과제 3]
polaris 관련 실습(아무거나) 후 관련 스샷을 올려주세요
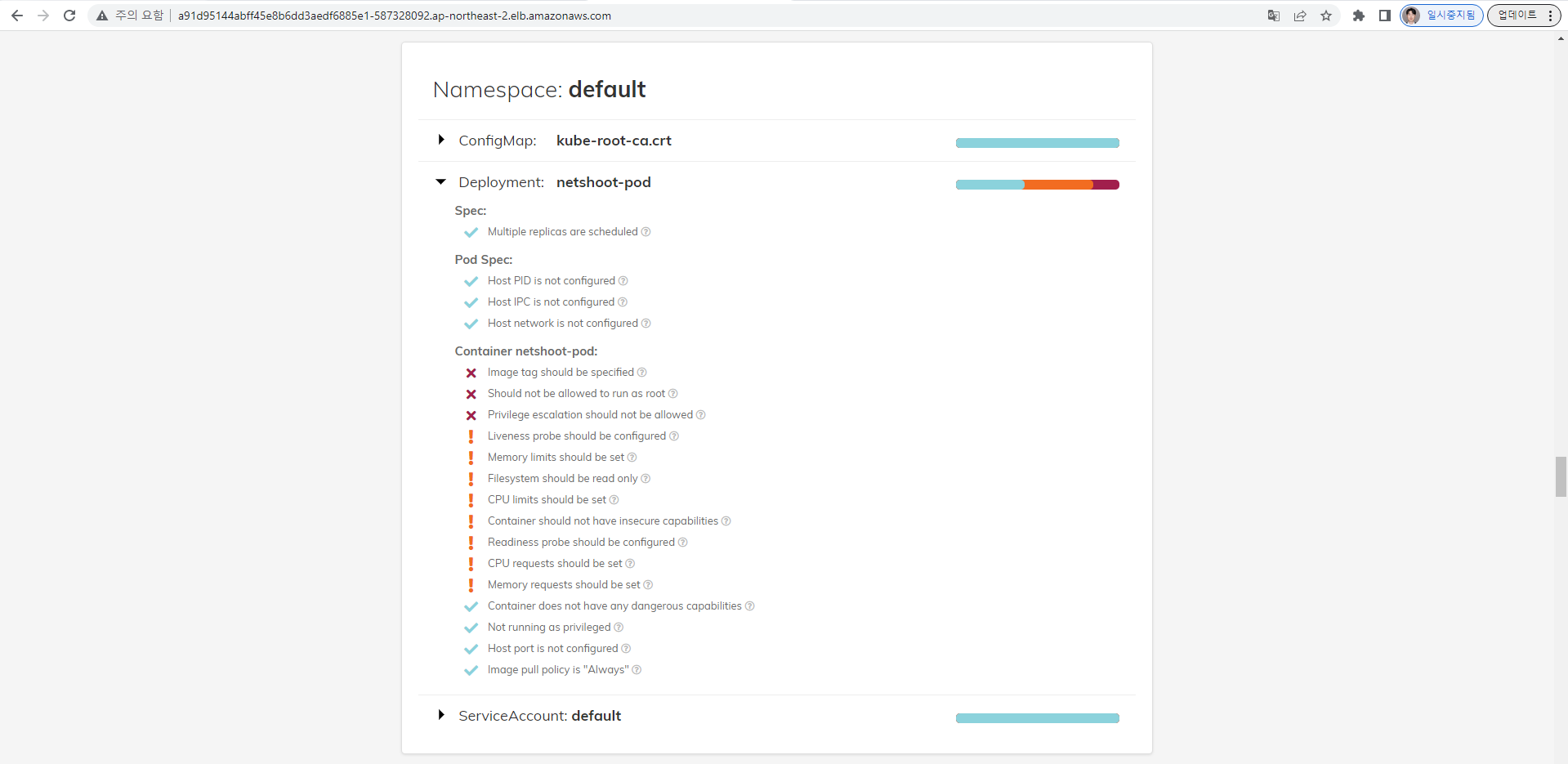
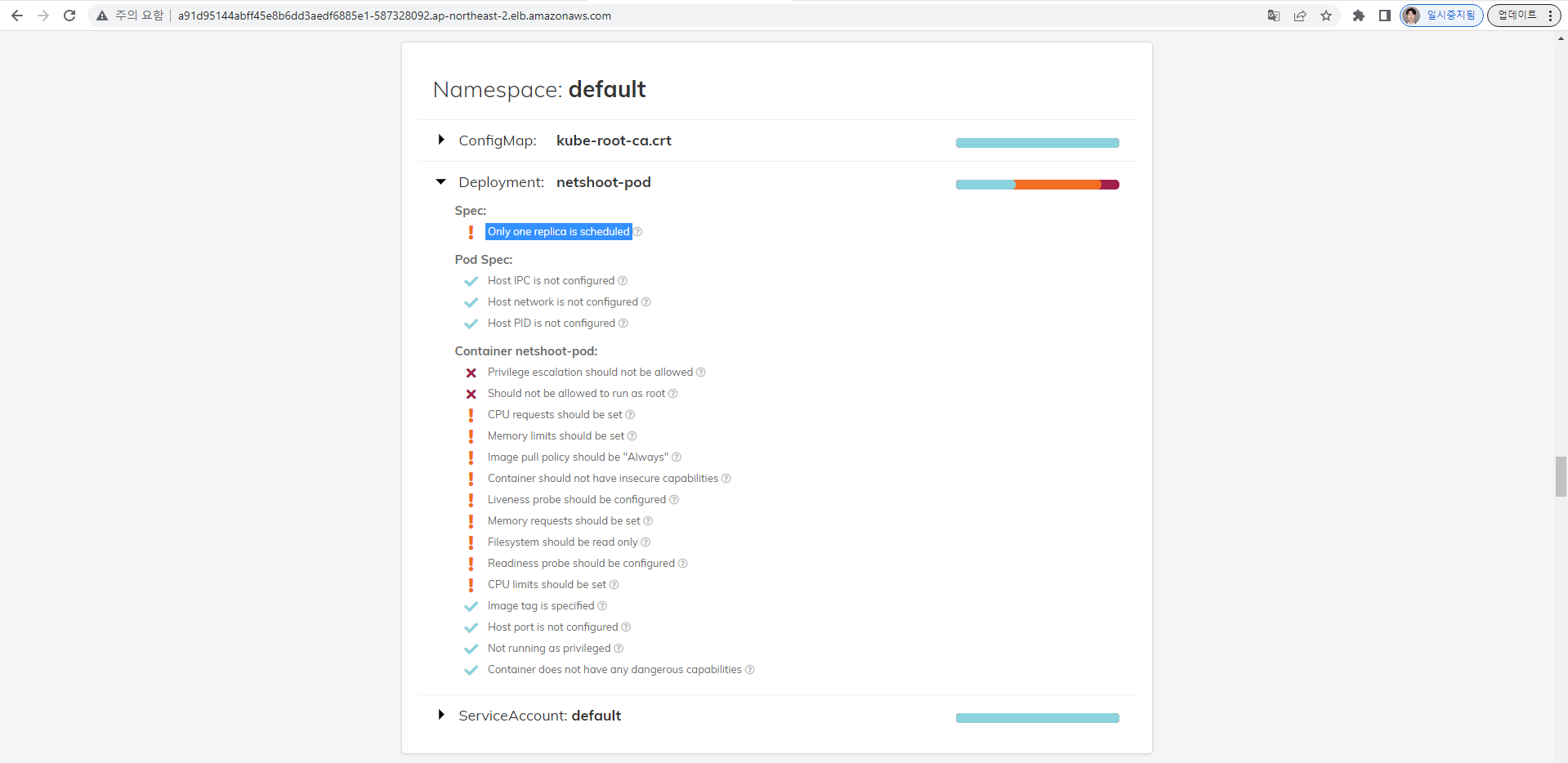
(repush:N/A) [root@kops-ec2 ~]# kubectl scale deployment netshoot-pod --replicas 2
deployment.apps/netshoot-pod scaled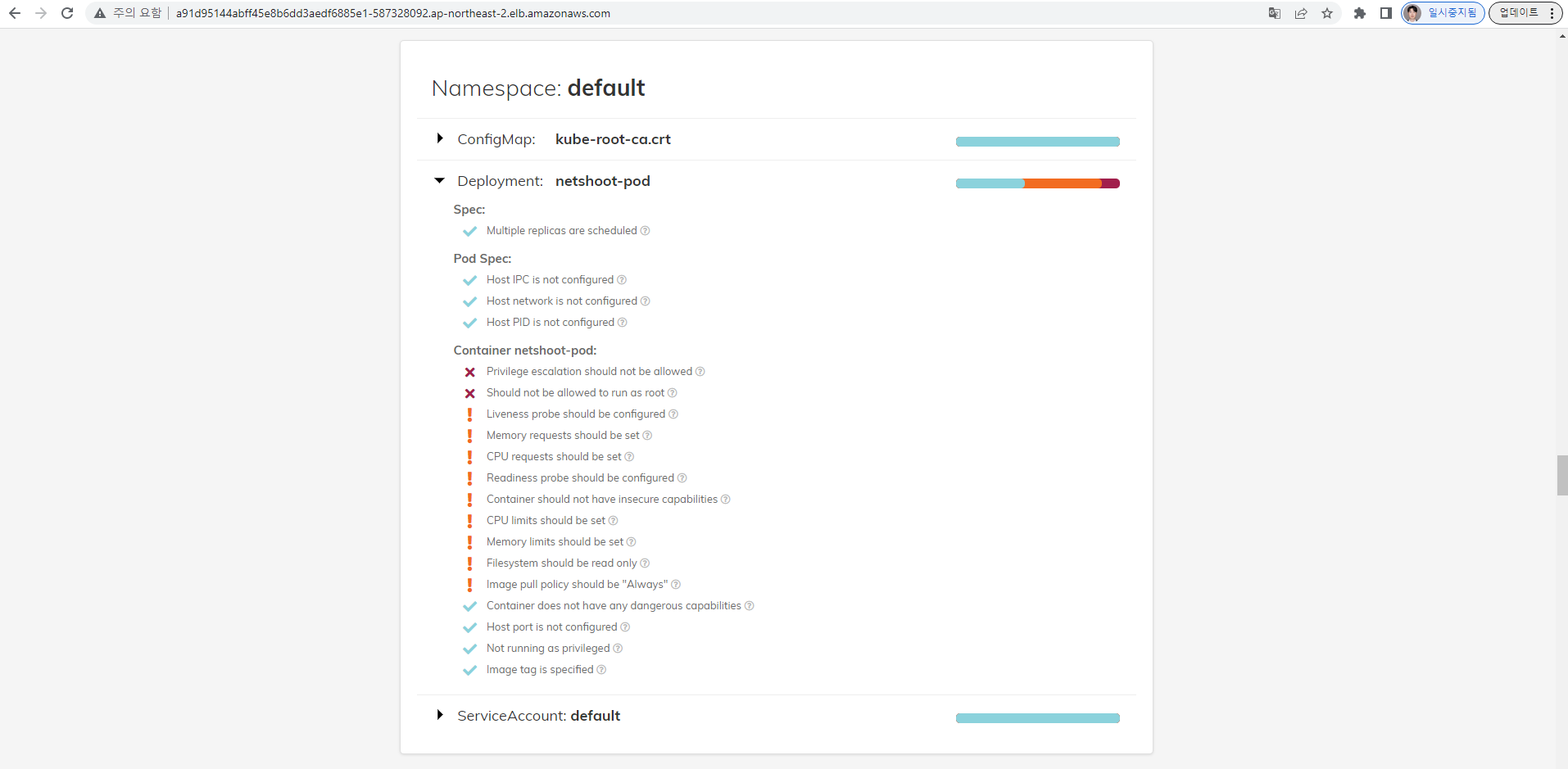
cat <<EOF | kubectl create -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: netshoot-pod
spec:
replicas: 2
selector:
matchLabels:
app: netshoot-pod
template:
metadata:
labels:
app: netshoot-pod
spec:
containers:
- name: netshoot-pod
image: nicolaka/netshoot:v0.9
command: ["tail"]
args: ["-f", "/dev/null"]
imagePullPolicy: Always
resources:
limits:
cpu: 150m
memory: 512Mi
requests:
cpu: 100m
memory: 128Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
privileged: false
readOnlyRootFilesystem: true
runAsNonRoot: true
terminationGracePeriodSeconds: 0
EOF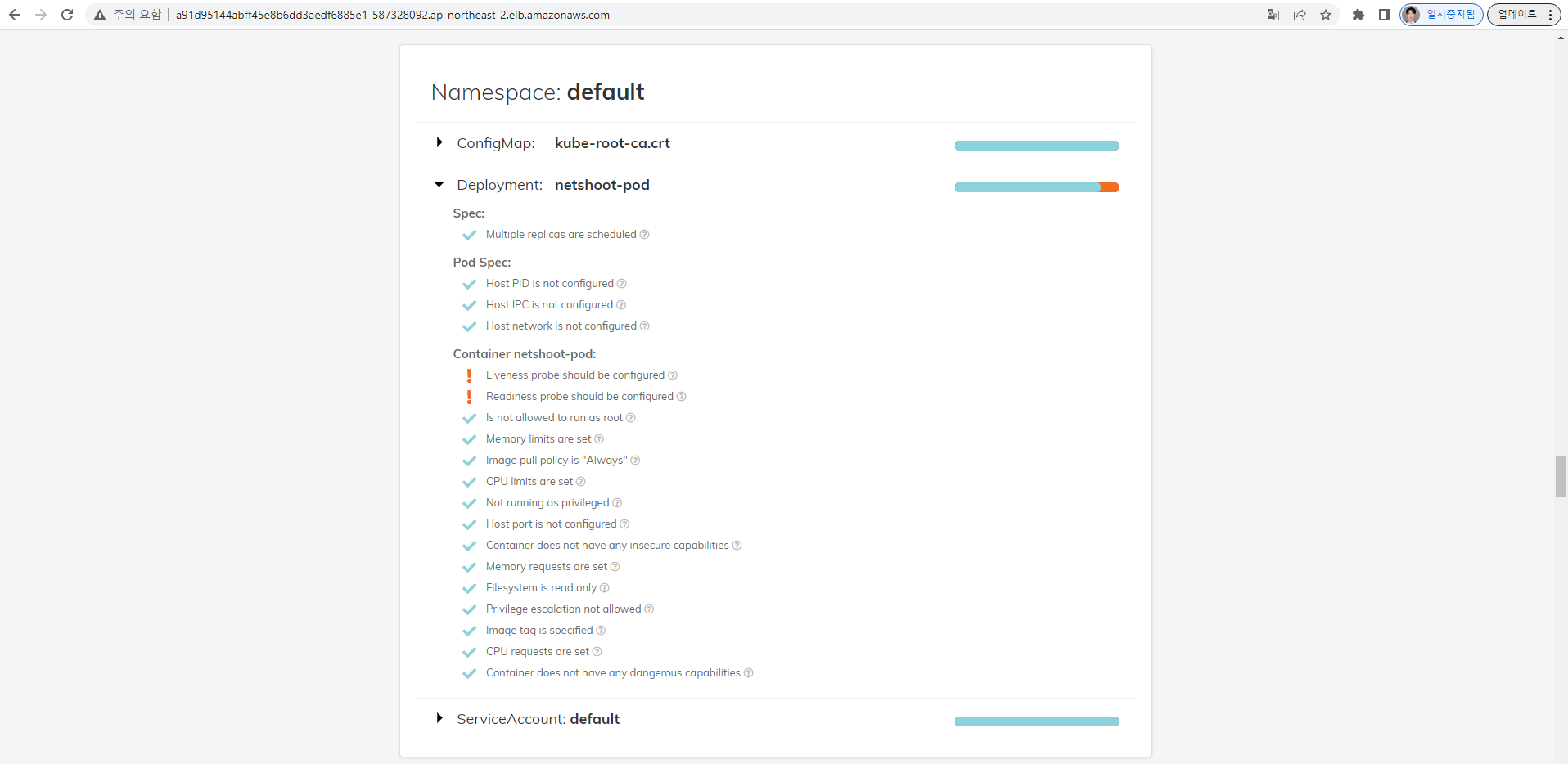
[과제 4]
신규 서비스 어카운트(SA) 생성 후 '클러스터 수준(모든 네임스페이스 포함)에서 읽기 전용'의 권한을 주고 테스트 후 코드나 스샷을 올려주세요
kubectl create sa read-only-k8s -n default
serviceaccount/read-only-k8s createdkubectl get sa -n default
NAME SECRETS AGE
default 0 3h25m
read-only-k8s 0 1skubectl get sa read-only-k8s -n default -o yaml | yh
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2023-02-27T15:24:30Z"
name: read-only-k8s
namespace: default
resourceVersion: "49771"
uid: 3cce6c5c-6ac1-4da6-81d8-d8405d923cc3cat <<EOF | kubectl create -f -
apiVersion: v1
kind: Pod
metadata:
name: read-only-kubectl
namespace: default
spec:
serviceAccountName: read-only-k8s
containers:
- name: kubectl-pod
image: bitnami/kubectl:1.24.10
command: ["tail"]
args: ["-f", "/dev/null"]
terminationGracePeriodSeconds: 0
EOF(repush:N/A) [root@kops-ec2 ~]# kubectl get pod
NAMESPACE NAME READY STATUS RESTARTS AGE
default read-only-kubectl 1/1 Running 0 2m19s(repush:N/A) [root@kops-ec2 ~]# kubectl get pod -o read-only-kubectl -n default -o yaml
apiVersion: v1
items:
- apiVersion: v1
kind: Pod
metadata:
annotations:
kubernetes.io/limit-ranger: 'LimitRanger plugin set: cpu request for container
kubectl-pod'
creationTimestamp: "2023-02-27T15:25:28Z"
name: read-only-kubectl
namespace: default
resourceVersion: "50026"
uid: f690f7ef-feff-4a8c-a61b-e9f4b9ef9e13
spec:
containers:
- args:
- -f
- /dev/null
command:
- tail
image: bitnami/kubectl:1.24.10
imagePullPolicy: IfNotPresent
name: kubectl-pod
resources:
requests:
cpu: 100m
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
volumeMounts:
- mountPath: /var/run/secrets/kubernetes.io/serviceaccount
name: kube-api-access-nvsv9
readOnly: true
dnsPolicy: ClusterFirst
enableServiceLinks: true
nodeName: i-0f63e14d2d5d5f119
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
serviceAccount: read-only-k8s
serviceAccountName: read-only-k8s
terminationGracePeriodSeconds: 0
tolerations:
- effect: NoExecute
key: node.kubernetes.io/not-ready
operator: Exists
tolerationSeconds: 300
- effect: NoExecute
key: node.kubernetes.io/unreachable
operator: Exists
tolerationSeconds: 300
volumes:
- name: kube-api-access-nvsv9
projected:
defaultMode: 420
sources:
- serviceAccountToken:
expirationSeconds: 3607
path: token
- configMap:
items:
- key: ca.crt
path: ca.crt
name: kube-root-ca.crt
- downwardAPI:
items:
- fieldRef:
apiVersion: v1
fieldPath: metadata.namespace
path: namespace
status:
conditions:
- lastProbeTime: null
lastTransitionTime: "2023-02-27T15:25:28Z"
status: "True"
type: Initialized
- lastProbeTime: null
lastTransitionTime: "2023-02-27T15:25:35Z"
status: "True"
type: Ready
- lastProbeTime: null
lastTransitionTime: "2023-02-27T15:25:35Z"
status: "True"
type: ContainersReady
- lastProbeTime: null
lastTransitionTime: "2023-02-27T15:25:28Z"
status: "True"
type: PodScheduled
containerStatuses:
- containerID: containerd://47b93b32b78fdff22d9c1ea990458bf22339cce1df24e232967dfe4ee8dd5bd1
image: docker.io/bitnami/kubectl:1.24.10
imageID: docker.io/bitnami/kubectl@sha256:a6d7ef461d5160e47f8761a2c2afcc1ce720039dd14fc5d2ac55bfd73a065236
lastState: {}
name: kubectl-pod
ready: true
restartCount: 0
started: true
state:
running:
startedAt: "2023-02-27T15:25:35Z"
hostIP: 172.30.57.163
phase: Running
podIP: 172.30.61.77
podIPs:
- ip: 172.30.61.77
qosClass: Burstable
startTime: "2023-02-27T15:25:28Z"
kind: List
metadata:
resourceVersion: ""kubectl exec -it read-only-kubectl -n default -- ls /run/secrets/kubernetes.io/serviceaccount
kubectl exec -it read-only-kubectl -n default -- cat /run/secrets/kubernetes.io/serviceaccount/token
kubectl exec -it read-only-kubectl -n default -- cat /run/secrets/kubernetes.io/serviceaccount/namespace
kubectl exec -it read-only-kubectl -n default -- cat /run/secrets/kubernetes.io/serviceaccount/ca.crtalias k3='kubectl exec -it read-only-kubectl -n default -- kubectl'k3 get pods
k3 run nginx --image nginx:1.20-alpine
k3 get pods -n kube-system
k3 auth can-i get pods
### 불가능cat <<EOF | kubectl create -f -
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: role-read-only
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs:
- get
- list
- watch
EOFkubectl get roles -n default
kubectl get roles -n default -o yaml
kubectl describe clusterroles role-read-only -n defaultcat <<EOF | kubectl create -f -
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: roleB-read-only
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: role-read-only
subjects:
- kind: ServiceAccount
name: read-only-k8s
namespace: default
EOFI have no name!@read-only-kubectl:/$ kubectl get pods -A
NAMESPACE NAME READY STATUS RESTARTS AGE
default read-only-kubectl 1/1 Running 0 74m
kube-system aws-cloud-controller-manager-6g5gd 1/1 Running 0 4h40m
kube-system aws-load-balancer-controller-595c8bbbbf-8d99m 1/1 Running 0 4h40m
kube-system aws-node-jzzlt 1/1 Running 0 4h39m
kube-system aws-node-r7428 1/1 Running 0 4h40m
kube-system aws-node-xtjf6 1/1 Running 0 4h28m
kube-system cert-manager-6b55fb8f96-m7nvv 1/1 Running 0 4h40m
kube-system cert-manager-cainjector-5cf5bd97fc-gffjv 1/1 Running 0 4h40m
kube-system cert-manager-webhook-66ccfc975d-2mt64 1/1 Running 0 4h40m
kube-system coredns-6897c49dc4-4tp5t 1/1 Running 0 4h38m
kube-system coredns-6897c49dc4-w9cbr 1/1 Running 0 4h27m
kube-system coredns-autoscaler-5685d4f67b-tq5jn 1/1 Running 0 4h27m
kube-system ebs-csi-controller-8656988bdb-f9sjx 5/5 Running 0 4h40m
kube-system ebs-csi-node-dnpb7 3/3 Running 0 4h40m
kube-system ebs-csi-node-w2xq8 3/3 Running 0 4h39m
kube-system ebs-csi-node-w547f 3/3 Running 0 4h28m
kube-system etcd-manager-events-i-08cf02ccf77956bd2 1/1 Running 0 4h39m
kube-system etcd-manager-main-i-08cf02ccf77956bd2 1/1 Running 0 4h39m
kube-system external-dns-6c69cd4c65-8xjnn 1/1 Running 0 4h40m
kube-system kops-controller-6x5df 1/1 Running 0 4h40m
kube-system kube-apiserver-i-08cf02ccf77956bd2 2/2 Running 1 (4h41m ago) 4h39m
kube-system kube-controller-manager-i-08cf02ccf77956bd2 1/1 Running 2 (4h40m ago) 4h40m
kube-system kube-proxy-i-08cf02ccf77956bd2 1/1 Running 0 4h39m
kube-system kube-proxy-i-0ab0a111bba087bae 1/1 Running 0 4h39m
kube-system kube-proxy-i-0f63e14d2d5d5f119 1/1 Running 0 4h28m
kube-system kube-scheduler-i-08cf02ccf77956bd2 1/1 Running 0 4h40m
kube-system metrics-server-6d48674cf8-8k426 1/1 Running 0 4h27m
kube-system metrics-server-6d48674cf8-wc6xc 1/1 Running 0 4h40m
kubescape gateway-58f55d6448-smdgv 1/1 Running 0 126m
kubescape kollector-0 1/1 Running 0 126m
kubescape kubescape-6d98699958-nbvcr 1/1 Running 0 126m
kubescape kubevuln-5f6cfc7d7f-dr2nh 1/1 Running 0 126m
kubescape operator-6764b4bddc-djznq 1/1 Running 0 126m
I have no name!@read-only-kubectl:/$I have no name!@read-only-kubectl:/$ kubectl run nginx --image nginx:1.20-alpine
Error from server (Forbidden): pods is forbidden: User "system:serviceaccount:default:read-only-k8s" cannot create resource "pods" in API group "" in the namespace "default"
I have no name!@read-only-kubectl:/$Cluster Role 이용해서 완료
