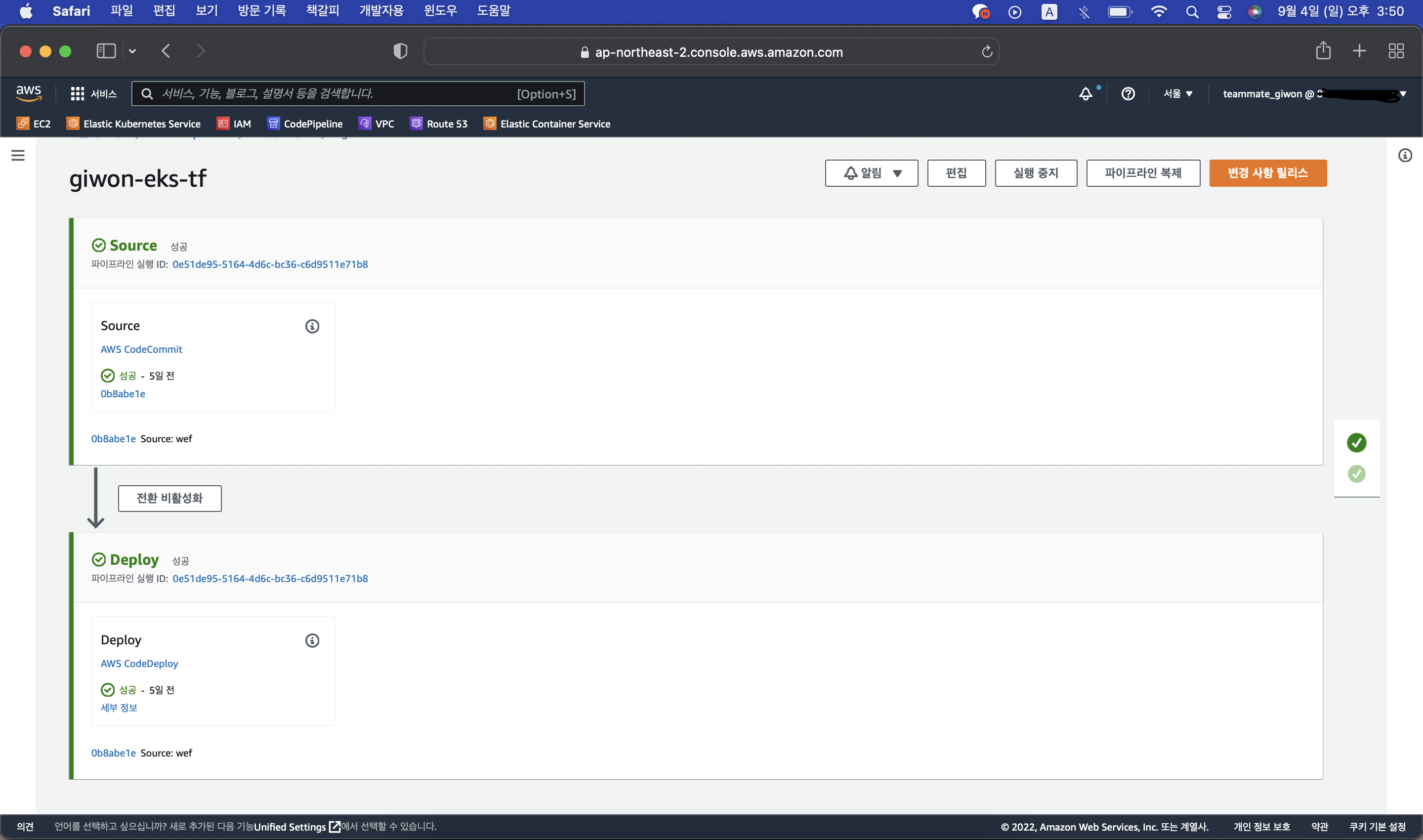
CodeCommit
$ git config --global credential.helper '!aws codecommit credential-helper $@'
$ vi /usr/local/git/etc/gitconfig
[credential "https://git-codecommit.ap-northeast-2.amazonaws\.com"]
helper = !aws --profile CodeCommitProfile codecommit credential-helper $@
UseHttpPath = true
[credential "https://github.com"]
helper = osxkeychain
$ git config --system --unset credential.helper
$ git clone <repo-name>
terraform -chdir=/home/ec2-user/terraform/ init
terraform -chdir=/home/ec2-user/terraform/ apply -auto-approve
appspec.yml
version: 0.0
os: linux
files:
- source: /
destination: /home/ec2-user/terraform/
hooks:
AfterInstall:
- location: /scripts/run_terraform.sh
runas: root
eks.tf
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
}
}
}
resource "aws_iam_role" "eks-cluster" {
name = "eks-cluster"
path = "/"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "eks.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
EOF
}
resource "aws_iam_role_policy_attachment" "AmazonEKSClusterPolicy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKSClusterPolicy"
role = aws_iam_role.eks-cluster.name
}
resource "aws_iam_role_policy_attachment" "AmazonEC2ContainerRegistryReadOnly-EKS" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly"
role = aws_iam_role.eks-cluster.name
}
resource "aws_eks_cluster" "ontheair-cluster" {
name = "ontheair-cluster"
version = "1.21"
role_arn = aws_iam_role.eks-cluster.arn
vpc_config {
subnet_ids = [var.subnet_id_1, var.subnet_id_2]
}
depends_on = [
aws_iam_role.eks-cluster,
]
}
resource "aws_iam_role" "workernodes" {
name = "node-group"
assume_role_policy = jsonencode({
Statement = [{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "ec2.amazonaws.com"
}
}]
Version = "2012-10-17"
})
}
resource "aws_iam_role_policy_attachment" "AmazonEKSWorkerNodePolicy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy"
role = aws_iam_role.workernodes.name
}
resource "aws_iam_role_policy_attachment" "AmazonEKS_CNI_Policy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy"
role = aws_iam_role.workernodes.name
}
resource "aws_iam_role_policy_attachment" "EC2InstanceProfileForImageBuilderECRContainerBuilds" {
policy_arn = "arn:aws:iam::aws:policy/EC2InstanceProfileForImageBuilderECRContainerBuilds"
role = aws_iam_role.workernodes.name
}
resource "aws_iam_role_policy_attachment" "AmazonEC2ContainerRegistryReadOnly" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly"
role = aws_iam_role.workernodes.name
}
resource "aws_eks_node_group" "worker-node-group" {
cluster_name = aws_eks_cluster.ontheair-cluster.name
node_group_name = "user-ontheair-workernodes"
node_role_arn = aws_iam_role.workernodes.arn
subnet_ids = [var.subnet_id_1, var.subnet_id_2]
instance_types = ["t2.small"]
scaling_config {
desired_size = 3
max_size = 5
min_size = 3
}
depends_on = [
aws_iam_role_policy_attachment.AmazonEKSWorkerNodePolicy,
aws_iam_role_policy_attachment.AmazonEKS_CNI_Policy,
]
}
CodeDeploy
Production EC2 User Data
#!/bin/bash
yum update -y
yum install -y ruby
curl -O https://aws-codedeploy-ap-northeast-2.s3.amazonaws.com/latest/install
chmod +x ./install
sudo ./install auto
wget https://releases.hashicorp.com/terraform/1.2.3/terraform_1.2.3_linux_amd64.zip
unzip terraform_1.2.3_linux_amd64.zip
mv terraform /usr/local/bin/
Application 생성 후 배포 그룹 생성
배포 그룹
- EC2 tag
key : Name / value : EC2 tag
- 서비스 역할
CodeDeployRoleForApp 생성 후 AWSCodeDeployRole 권한 추가
CodePipeline으로 EKS 자동화