Argocd profile 생성
eksctl create fargateprofile \
--cluster fordong-cluster-dev \
--region your-region-code \
--name argocd \
--namespace argocdArgocd namespace 생성
kubectl create namespace argocdInstall Argo CD
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/core-install.yamlArgocd 설치 확인
kubectl get all -n argocdDownload Argo CD CLI
brew install argocdLogin Using The CLI
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echoAccess The Argo CD API Server
kubectl patch svc argocd-server -n prd-cicd -p '{"spec": {"type": "NodePort"}}'Argocd Ingress 생성
- argocd는 backend-protocol을 HTTPS로 해주지 않으면, too many redirect에러가 발생
kubectl apply -f argocd-ingress.yamlargocd-ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
namespace: argocd
name: ingress-argocd
annotations:
kubernetes.io/ingress.class: alb
alb.ingress.kubernetes.io/scheme: internet-facing
alb.ingress.kubernetes.io/target-type: ip
alb.ingress.kubernetes.io/backend-protocol: HTTPS
alb.ingress.kubernetes.io/healthcheck-path: /login
# SSL Settings
alb.ingress.kubernetes.io/listen-ports: '[{"HTTP": 80}, {"HTTPS":443}]'
alb.ingress.kubernetes.io/certificate-arn: 'arn:aws:acm:ap-northeast-2:300081888502:certificate/66031d62-4c54-4d96-b325-99cc9a4b6670'
alb.ingress.kubernetes.io/ssl-redirect: '443'
spec:
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: argocd-server
port:
number: 443route53 host 등록
- 위에서 생성한 alb와 route53의 host 레코드를 연결
login Argo CD API Server
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; ech- Arogo CD password update
argocd account update-passwordArgocd 접속
- route53에서 생성한 url 실행
- id : admin
- pw : update 한 password
repository 등록
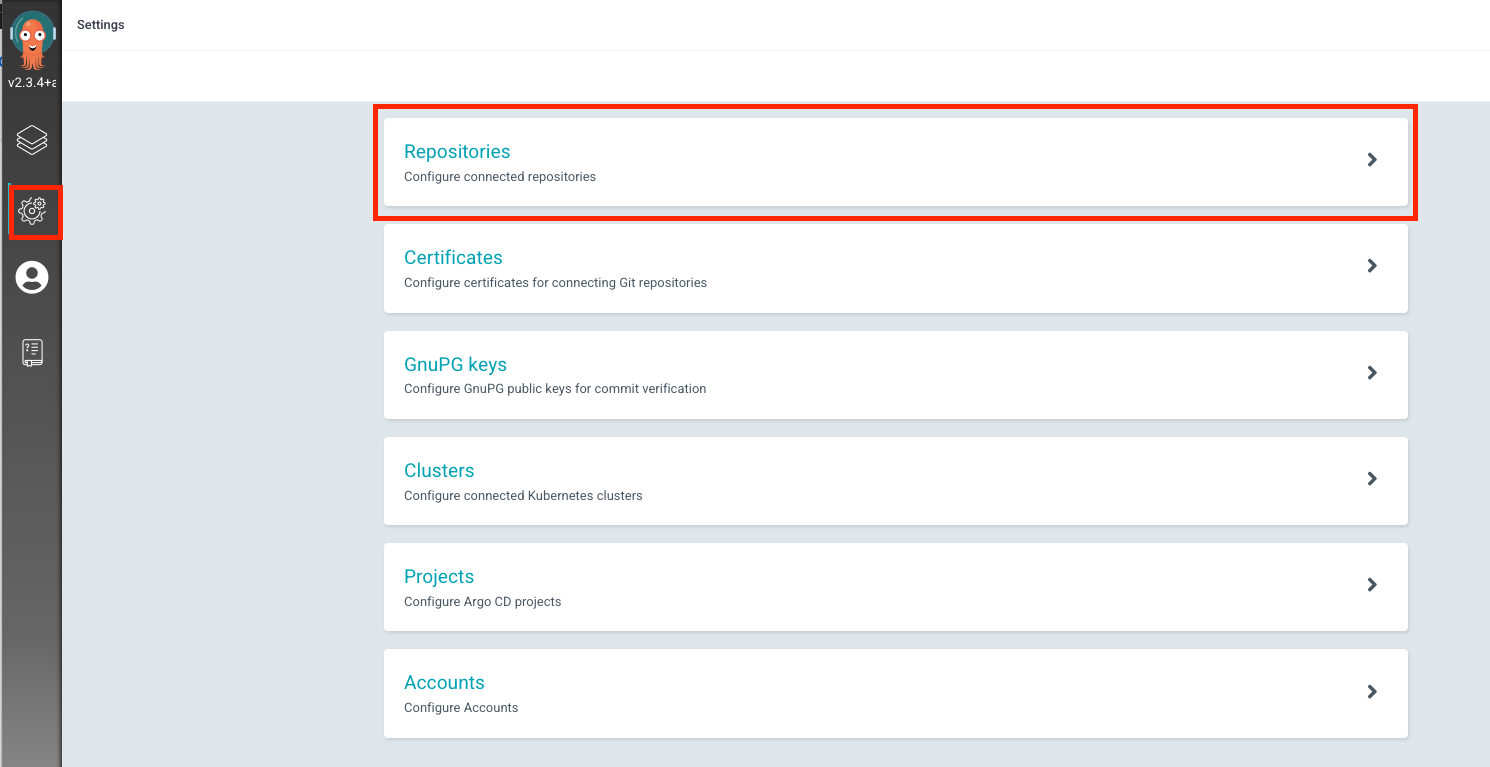
- username : git id
- password : git access token 추가 (repo 권한 포함)
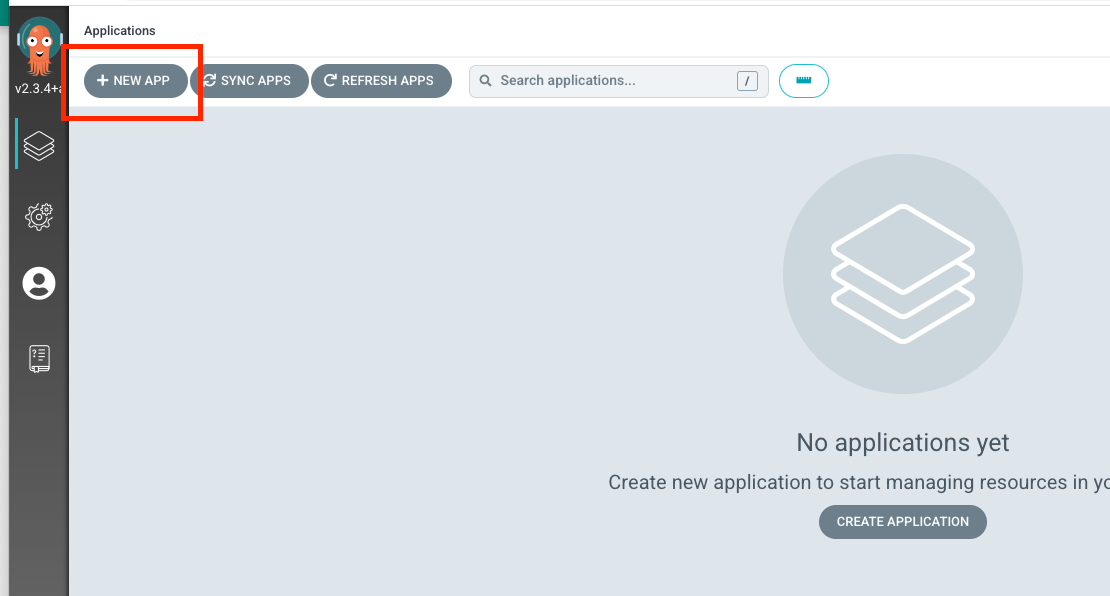
new app 클릭
- syncPolicy
- dev 환경에서는 automated
- prod 환경에서는 maunal
ref.
