VMware Tanzu supports k8s infrastructure on legacy VMware vCenter.(well you need version 7.0+) with VMware Tanzu you can manage k8s resources with vCenter UI or CLI(kubectl-vsphere, tanzucli)
Permission is always a beginning to everything. a sso user can be added to Tanzu namespace and then has access to k8s resources on kubectl.
and it's that easy to add on vCenter UI.
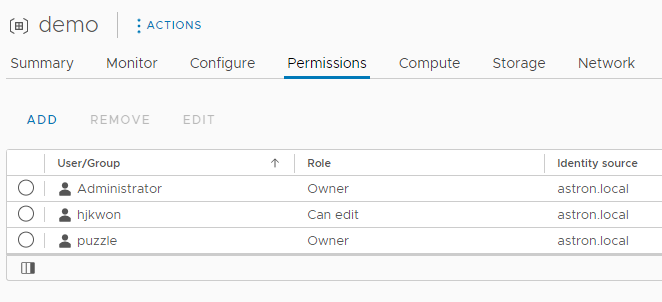
I'm restless. can't do this every time manually. do Tanzu have a API for this?
opened a SR and here's the answer.
Below is my answer on your query:-
Yes, you can give permission to users using kubectl command also, in both supervisor cluster as well as in TKCs. To give permission, you need to create clusterrolebinding/rolebinding inside the cluster.
You can check the role on cluster and bind it with user to give permission:-
1) To check roles in cluster, run below command (where you will also find “admin”, “view”, “edit” role).
kubectl get clusterrole
kubectl get role -n <namespace>
2) And to assign that role to users, you need to create clusterrolebinding/rolebinding. Refer below doc
Refer https://docs.vmware.com/en/VMware-vSphere/7.0/vmware-vsphere-with-tanzu/GUID-6DE4016E-D51C-4E9B-9F8B-F6577A18F296.htmlsays yes we can. ref
all that was needed was a simple rolebinding.
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: rolebinding-cluster-user-joe
namespace: default
roleRef:
kind: ClusterRole
name: edit #Default ClusterRole
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: User
name: sso:joe@vsphere.local #sso:<username>@<domain>
apiGroup: rbac.authorization.k8s.ioabove yaml code is a clusterrolebinding which have higher access level. to restrict access to each namespace, use rolebinding.
Takeaway
Tanzu was a k8s tool afterall. stick to the basics.
