Step1: Information gathering
Information gathering이란?
We already know that information gathering is the first step in penetration testing and it is an act of gathering data about our target.
It can be any type of data that we might find useful for the future attack.
And if you remember, there are two types of information gathering.
We got active information gathering and passive information gathering.
Active
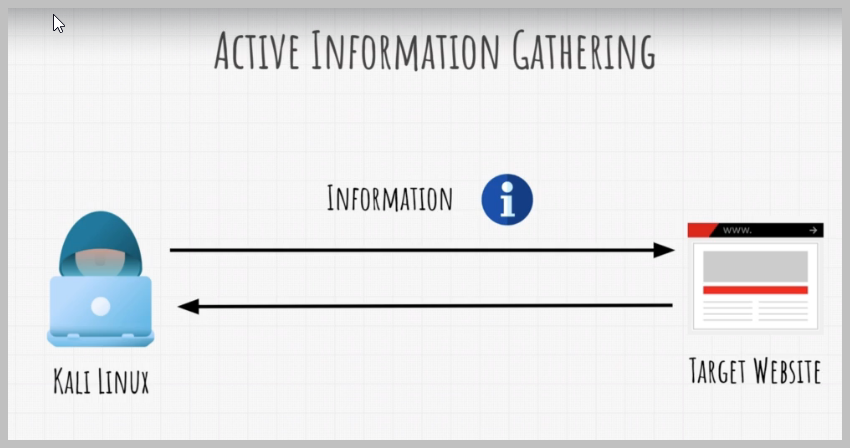
We use our Kleenex machine and we try to get as much data or as much information about our target while Or it could also be a network that we're testing, or perhaps an entire company.
The main point is that with active information gathering, we directly get that data from the target. This could mean directly exchanging packets with the target by visiting and enumerating their website Or it could also mean talking to an employee that works there. We could maybe call them over mobile phone to try to get them to tell us something important.
Nonetheless, any action where we exchange something with the target is active information gathering.
And it is important to mention that usually active information gathering will provide us with much more important data than passive information gathering, since we are directly interacting with the target.
Passive

On the other hand, we got passive information gathering and it is similar.
We got our Linux machine and our target.
But we also have an intermediate system or what I like to call a middle source and what this metal source
Well, basically, it could be anything from a search engine to a website.
But what matters is that information we get is going through that middle source.
For example, if we want to find out something about a certain target and we Google that target to find
some pages that contain information about it.
This is considered passive information gathering.
Information gathering 목적이 무엇인가?
But what are the goals of this?
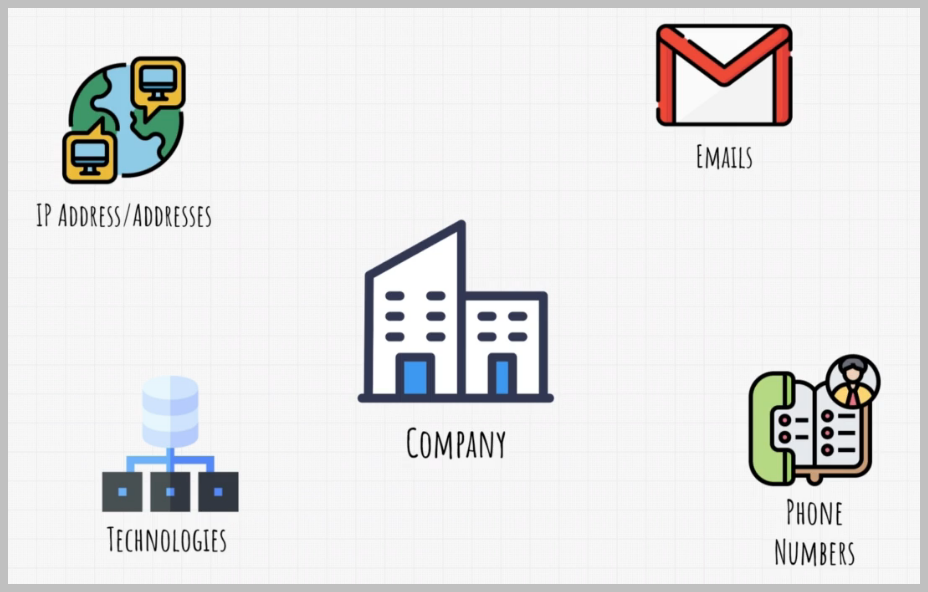
Usually the first thing we search to identify a target is their IP address or IP addresses if the target has multiple addresses that belong to them.
This could be, for example, a company that has servers and buildings all around the world.
And if we were to test this company, we would also be interested in their employees to.
For example, we would want to gather their emails, which could be useful for a future attack to gain Or we could possibly want to gather their phone numbers, which could also be useful.
But most importantly, and what we're mainly interested in are technologies that the target has.
Obtaining IP Address, Physical Address Using Whois Tool
whois 도메인명
Whatweb Stealthy Scan
whatweb
whatweb -help
whatweb 도메인명 -v