내가 해킹을 공부하는 이유
CS 공부를 하는데 운영체제나 네트워크 같은 개념들이 너무 추상적이다. 갈증이 난다. 내가 직접 활용해본 게 아니라 그저 개념이나 이론을 머리에 집어넣으려고 하니까 이걸 왜 배워야 할까? 라는 물음에 대한 갈증이 해소가 안된다. 대부분이 휘발성으로 모두 날아가버린다고 해야하나. 나는 확실히 예제로 배울 때 엄청 오래 기억하고 적용을 잘한다.
- 가상머신과 리눅스 명령어들에 익숙해지기 위해
- 네트워크와 친해지기 위해서
- SQL을 좀 더 재미있게 배우려고.
- 암호학 관련 지식을 좀 더 내 것으로 체화하고 싶어서
화이트 해킹에서 다루는 주제들이 결국은 모두 웹에서 자주 나오는 주제들의 상위호환이라고 해야하나. 서버를 빌드할 때 결국은 보안이라는 것을 염두해서 코드를 짜기 마련이니 반대의 경우인 해킹이라는 상황을 알고 있으면 웹을 공부할 때도 훨씬 쉬울 것이다.
해킹을 공부해두면 확실히 웹코드를 짤 때 "아 이런 맥락에서 그런 코드들이 나온 거였구나?" 하는 상황들이 많이 나올 것 같다.
Ethical Hacking이란?
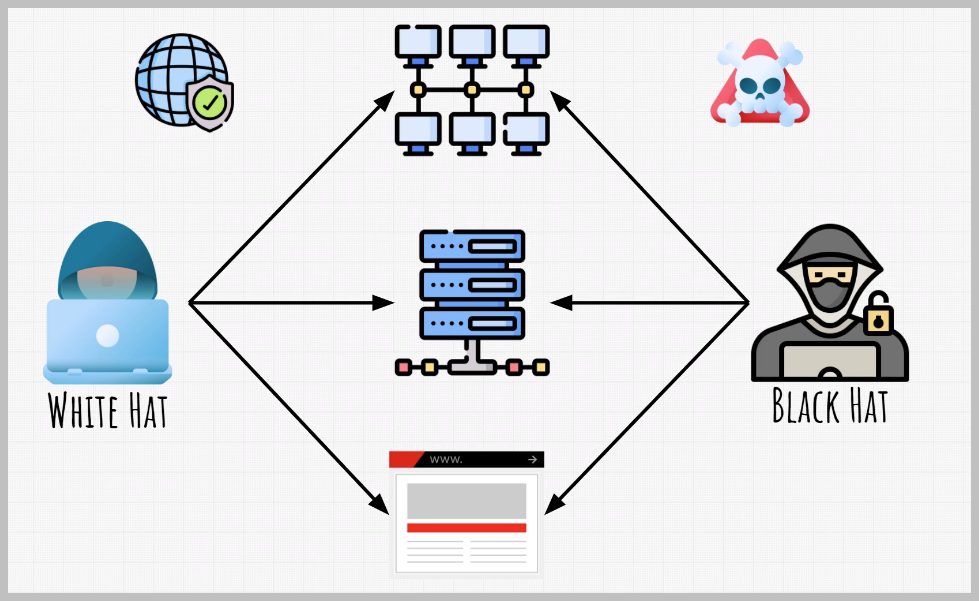
Now, I mentioned a word system quite a few times by now.
What do I mean by finding vulnerabilities in a system?
Well, system can be anything.
It can be a network of multiple computers, or it could be just one single computer.
It could also be some company server that they keep their important data on.
A vulnerability, on the other hand, is anything that could allow someone to have an unauthorized access to that system.
The methods white hat and black hat hackers use can be quite similar.
Virtual Machine이란?
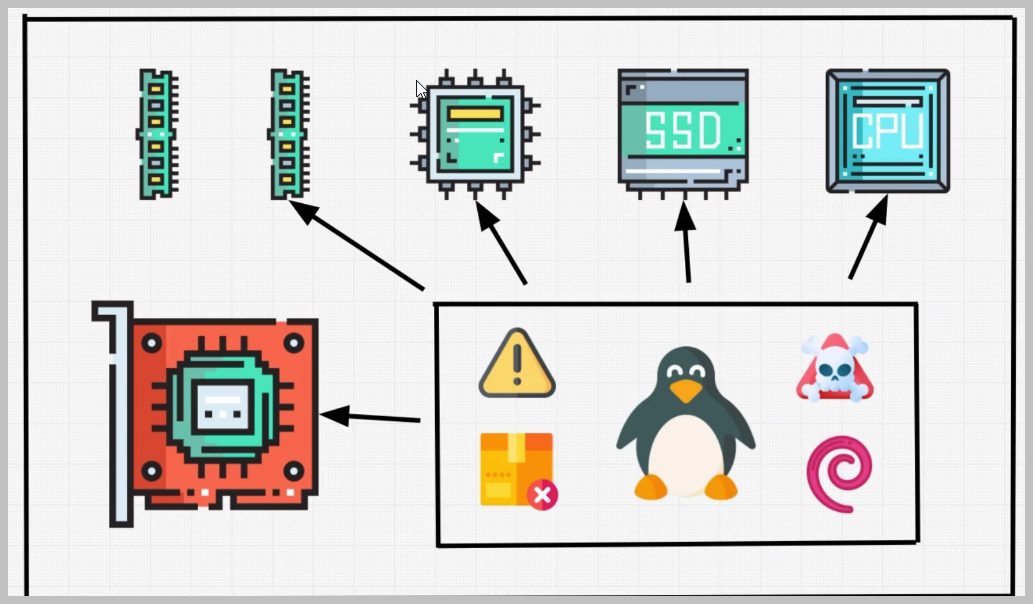
I can just give you a definition and say virtual machine is a machine within our physical computer that is using its hardware resources.
Imagine these four lines representing our computer, and we already know that any computer will have one of the three main operating systems Windows, Mac, OS or Linux.
operating system is not the only thing defining our machine.
Our machine also has its computer parts.
We have hard disk processor, RAM Memory motherboard and many more computer parts that with the operating system make our machine work. These computer parts are also known as hardware.We will install Linux as a virtual machine, and for this machine to work, it will need to have access to our hardware components.
And what we will do is we're going to borrow our physical machines, CPU power, ram memory, harvest memory to our virtual machine so it can run just like our physical machine.
In other words, we're splitting the power of our physical machine into two different machines or more if we decide that we want to create multiple virtual machines.
Virtual Machine의 이점
But what are other benefits that we have?
The good thing about virtual machines is that if, for example, our machine starts getting some annoying error or we get locked out of our files, or simply we delete a file that we shouldn't have deleted and it crashes our virtual machine.What if we, for example, get infected by a malware or virus by accident?
Don't worry, with two clicks we can delete the entire virtual machine with all of its files and it will have no effect on our physical machine.
We can also create something called a snapshot, which will allow us to save the current state of a
And with it we can revert back to that state whenever we want.
리눅스를 쓰는 이유?

So what are the benefits of using Linux?
First thing that's great about Linux is that it is an open source operating system.
This means that we can inspect the code of it and see how it is made and what programs or functionsAnd another great thing about it is that most of the Linux distros are free of cost.
Maybe some of you have heard about Ubuntu Linux Mint or Debian.
Well, to use an updated Windows operating system, you must pay for a license.
And not only that, but it also due to it being an open source, it allows the users of Linux to edit, copy or distribute various aspects of Linux based operating system without violating any copyright law or terms and conditions.There are Linux distros called Linux Pirate Backtrack(=retrace) and others that are especially made for penetration(=invasion) testing and checking for security loopholes.
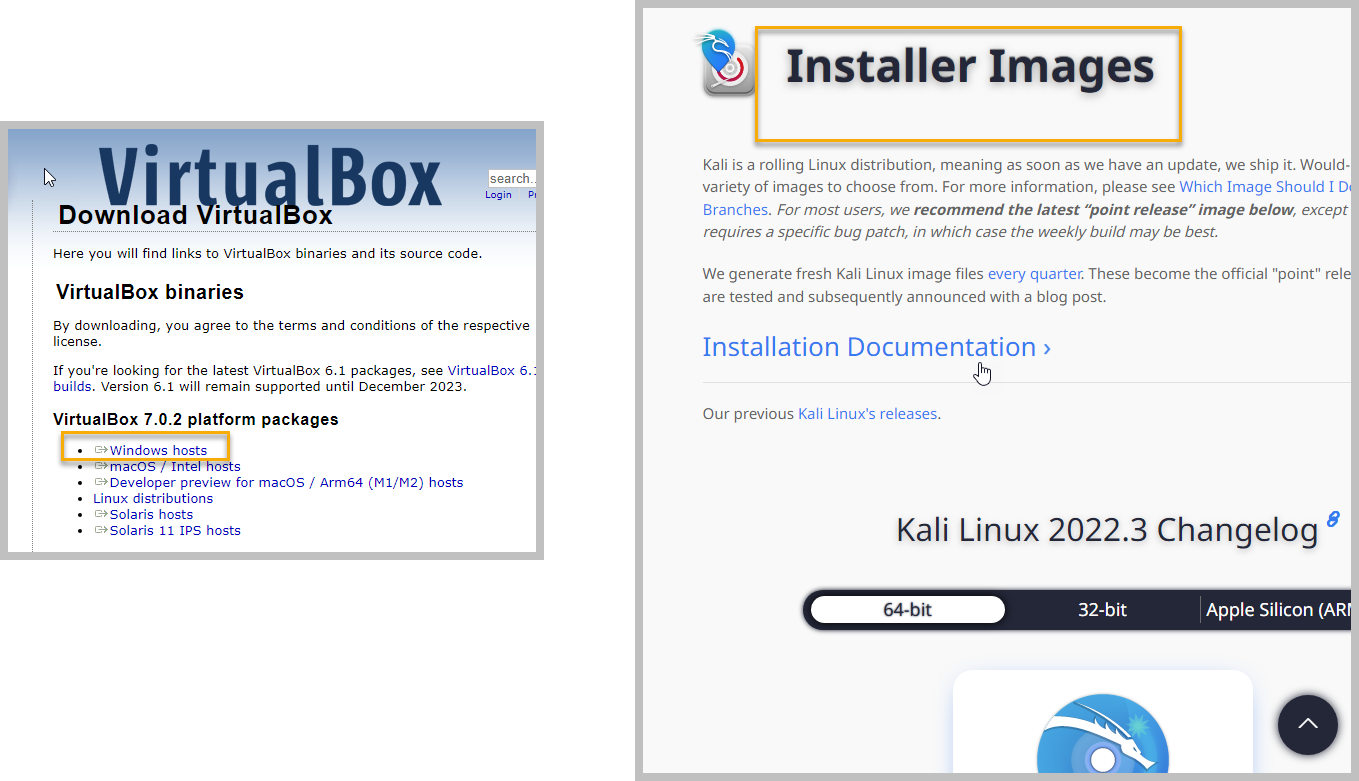
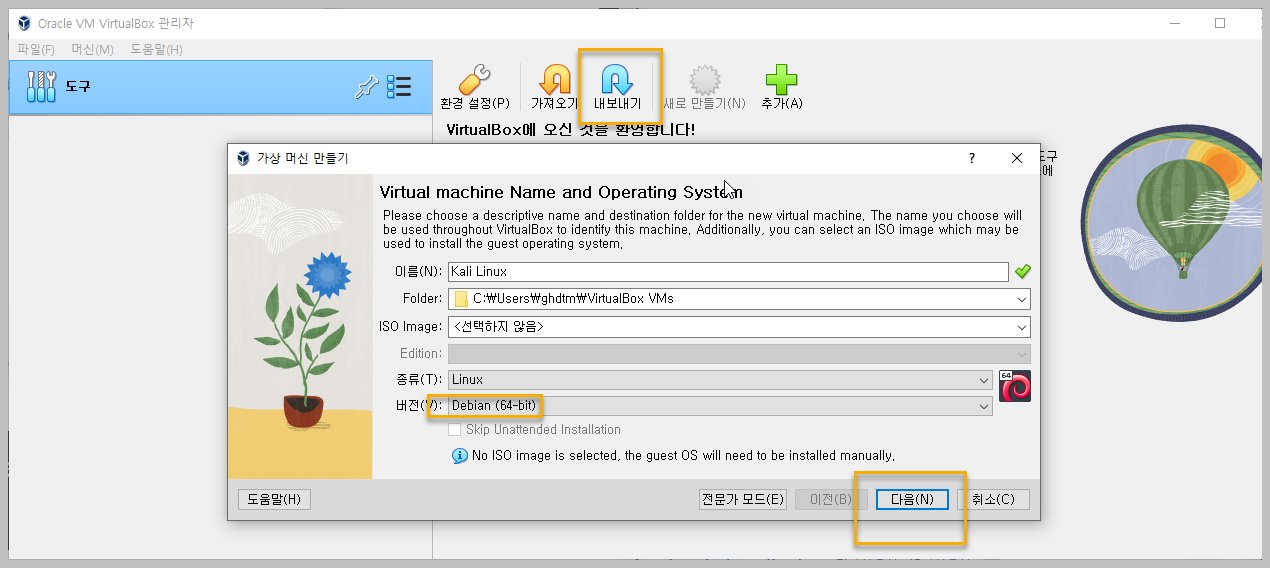
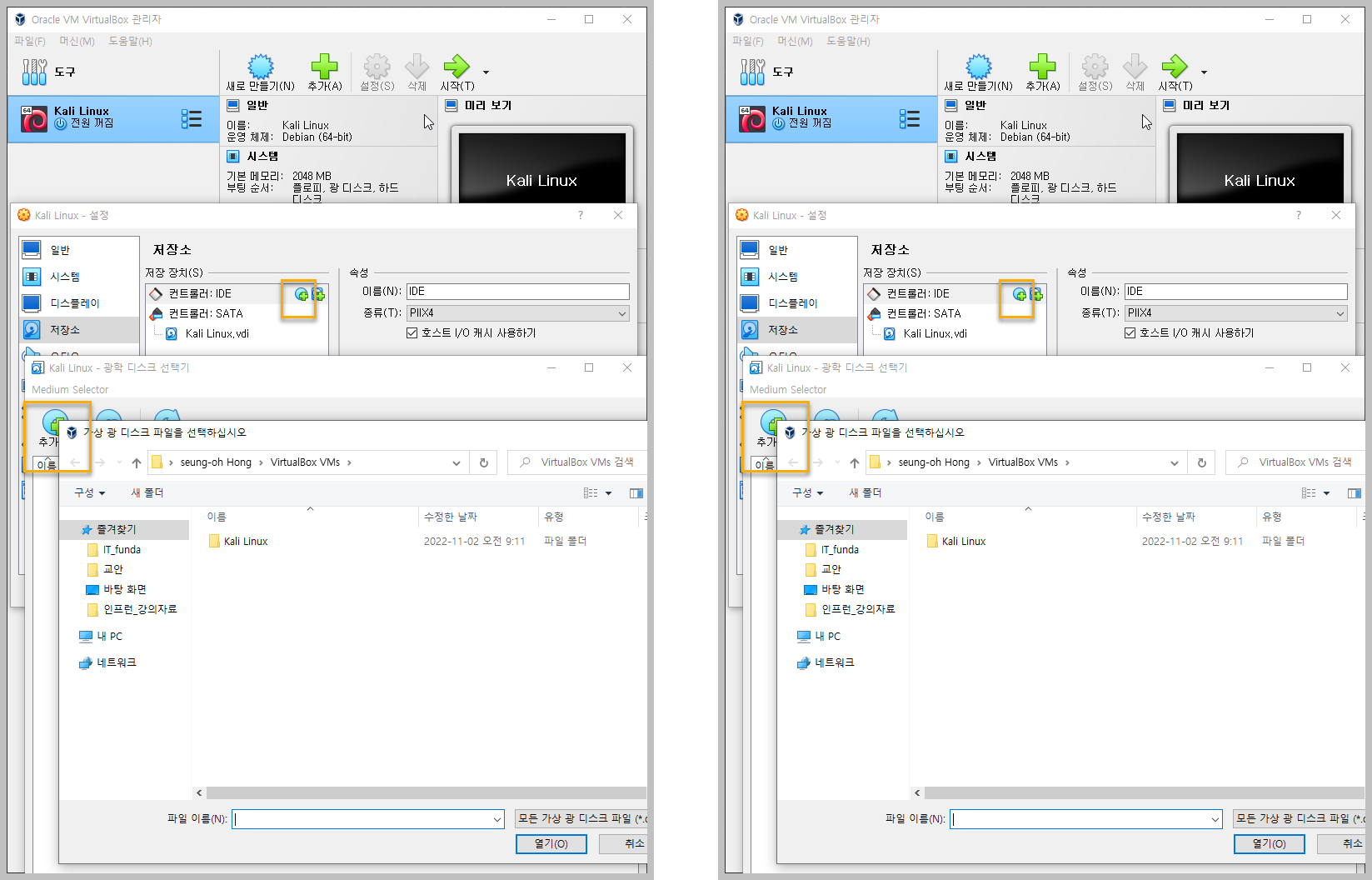
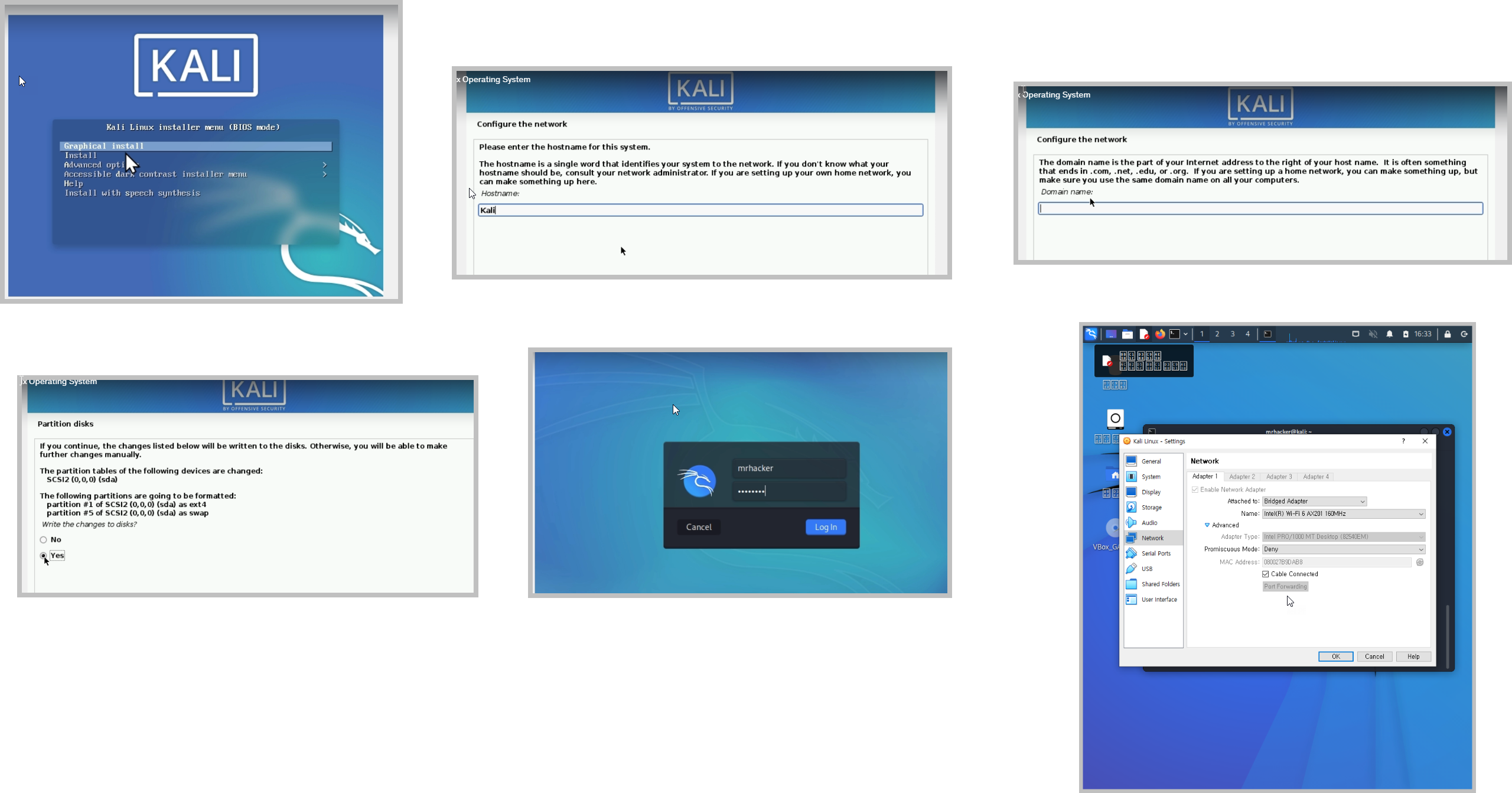
리눅스 & VirtualBox 설치
https://www.kali.org/get-kali/#kali-installer-images
https://www.virtualbox.org/
Kali Linux한글 설정
Penetration test(침투테스트) 의 다섯가지 전략
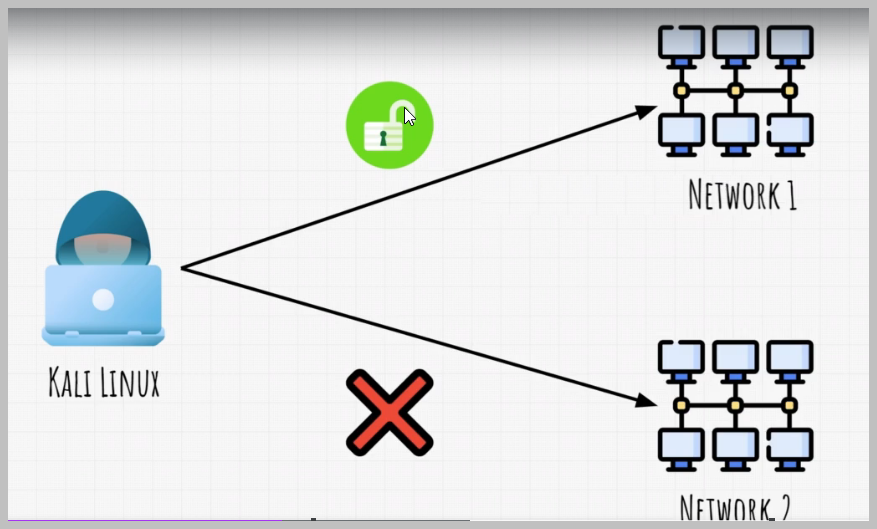
From now, the basic steps that we are going to do is we will use our Linux machine to scan and attack different machines, networks, websites and accounts.
But how are we going to do that?
Do we just magically attack it and do we just install virus on their machine somehow?
And if so, how do we do that?
Well, that is just a small portion of a penetration test.
First thing and most important thing before we even start the penetration test on a target is to figure out do we have permission to attack this target?
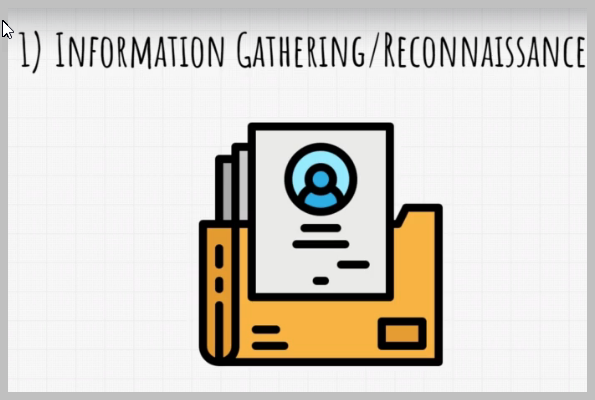
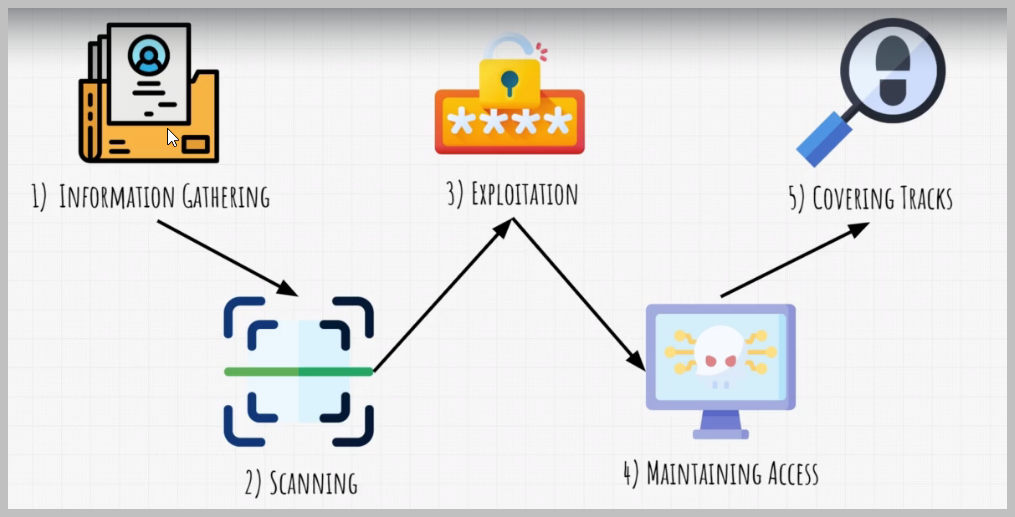
We already know that there are five of them, and the first one is reconnaissance or information gathering.
Reconnaissance is the act of gathering information about your target to better plan out your attack.
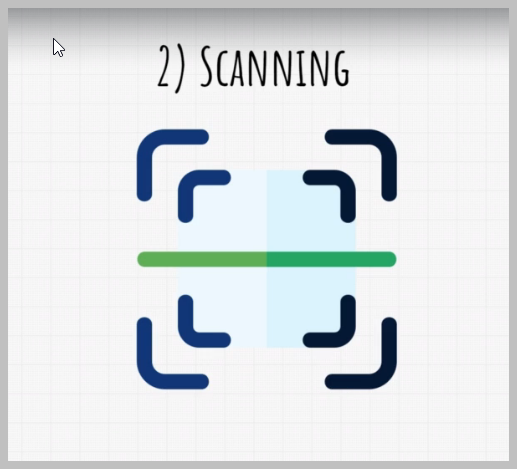
After the step comes scanning.
Here is where you can start getting in trouble if you do it without permission.
Scanning is a deeper form of information gathering, using technical tools to find openings in the target and in the systems that you are attacking.These openings can be gateways, open ports, operating systems that target runs and so on and so on.
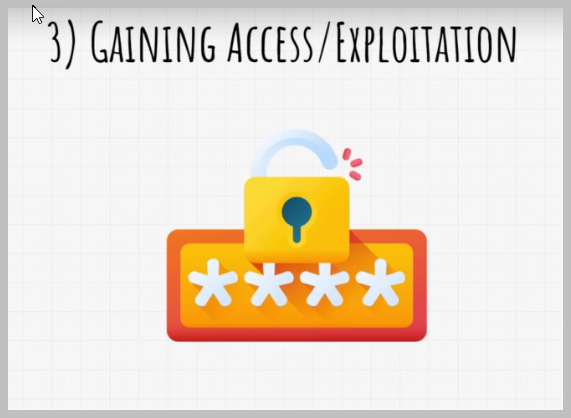
After information gathering and scanning comes third step, which is gaining access or so called exploitation. And this is the step where we actually hack the target.
Gaining access of target devices allows us to steal data from their system or to use those devices to attack other devices on the same network.

After exploitation comes maintaining access.
This step with the fifth step is sometimes optional.
However, maintaining access is also important step and it is commonly done by installing back doors and planting rootkits.
What a backdoor and rootkits are simply programs that will allow us to gain access to that target whenever we want without the need to exploit it again.

And last step of penetration test is covering tracks. Covering tracks is simply removing all evidence that an attack ever took place.
This can involve deleting or hiding files, editing logs, or basically reverting any changes that you did to the system while the attack took place.