Task 1 What is an SSRF?
SSRF (Server-Side Request Forgery) It’s a vulnerability that allows a malicious user to cause the webserver to make an additional or edited HTTP request to the resource of the attacker’s choosing.
1. regular SSRF: data is returned to the attacker’s screen.
2. Blind SSRF: SSRF occurs, but no information is returned to the attacker’s screen.
Result
- Access to unauthorized areas
- Access to customer/organizational data
- Ability to Scale to internal networks.
- Reveal authentication tokens/credentials
Task 2 SSRF Examples
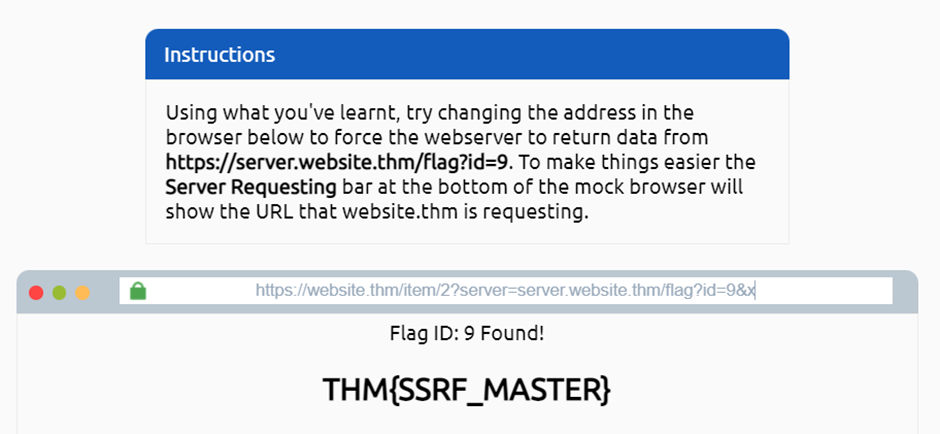
Task 3 Finding an SSRF
Potential SSRF vulnerabilities can be spotted in web applications in many different ways.
- When a full URL is used in a parameter in the address bar
- A hidden field in a form
- A partial URL such as just the hostname
- Only the path of the URL
If working with a blind SSRF where no output is reflected back to you, you’ll need to use an external HTTP logging tool to monitor requests such as requestbin.com, your own HTTP server or Burp Suite’s Collaborator client.
Task 4 Defeating Common SSRF Defenses
Deny List: where all requests are accepted apart from resources specified in a list or matching a particular pattern. A Web Application may employ a deny list to protect sensitive endpoints, IP addresses or domains from being accessed by the public while still allowing access to other locations.
allow list: where all requests get denied unless they appear on a list or match a particular pattern
open redirect is an endpoint on the server where the website visitor gets automatically redirected to another website address.
Task 5 SSRF Practical
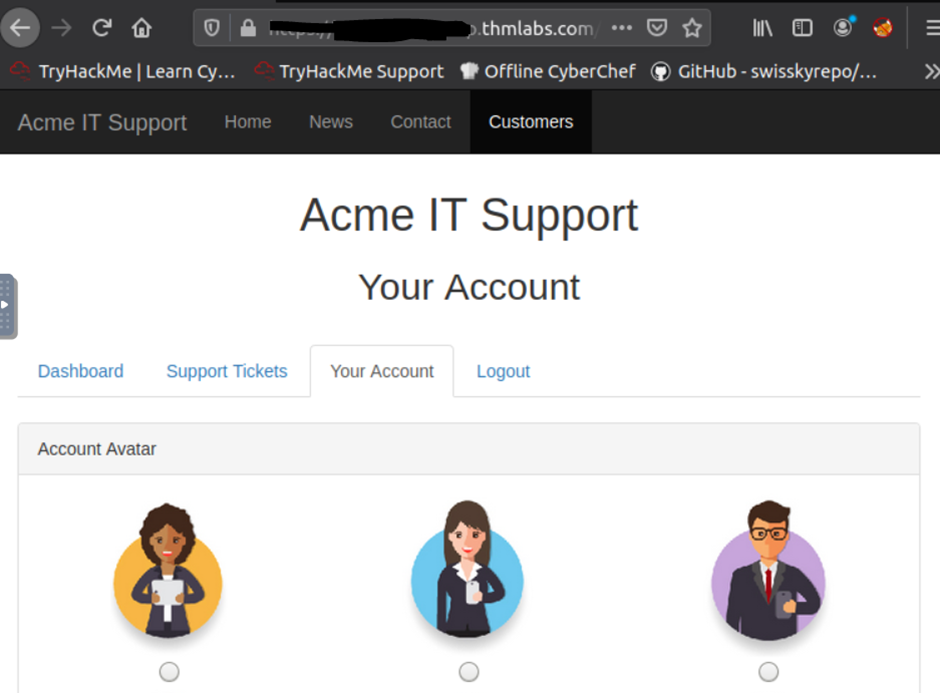
Sing in and go to the customers/new-account-page to view the new avatar selection feature.

I can see the avatar form field value contains the path to the image.
After choosing one of the avatars and the click the update avatar button, I can see the from change and above it, display my currently selected avatar.
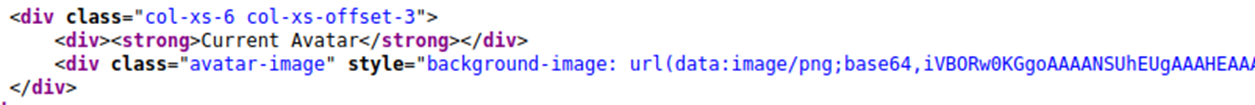
My current avatar is displayed using the data URI scheme, and the image content is base64 encoded as per the screenshot above.
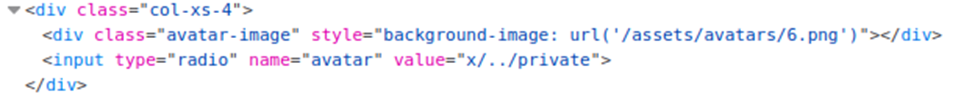
Change the value to x/../private. Then update the avatar.
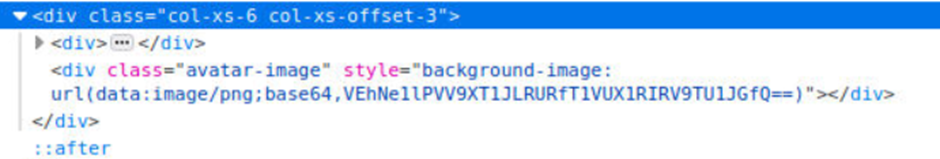
I can see the contents form the /private directory in base64 encoding.
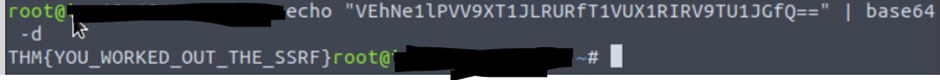
Decode with base64 in terminal.

