AES란?
: 대칭키 알고리즘으로 1997년 NIST(미국 국립기술표준원)에서 DES를 대체하기 위해 Advanced Encryption Standard(AES)로 불리는 암호 알고리즘을 공모하였다. 이후 레인달이 개발한 알고리즘이 AES로 채택되었고 높은 안전성과 효율성, 속도 등으로 인해 DES 대신 전 세계적으로 많이 사용되고 있다.
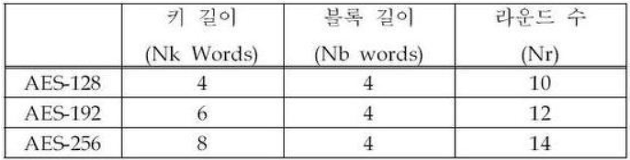
AES에는 3가지 종류가 있으며 각각 AES-128, AES-192, AES-256으로 불리며 이름 그대로 키 크기가 128, 192, 256 bit이다.
DES는 Feistel 네트워크라는 기본 구조를 사용하지만 AES에서는 SPN 이라는 구조를 사용하고 있다.
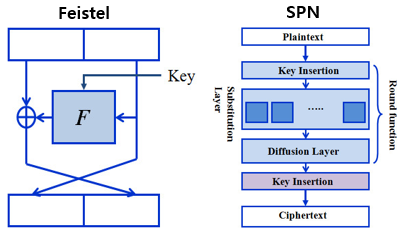
spn: Subsititution Layer과 Pernutation을 이용하여 Confusion과 Diffusion을 만족시켜주는 구조이다. 이 구조의 장점은 Feistal 구조와 반대로 병렬연산이 가능하여 속도가 빠르고 단점은 복호화시 별도의 복호화 모듈을 구현해줘야 한다는 것이다.
AES 알고리즘의 동작과정
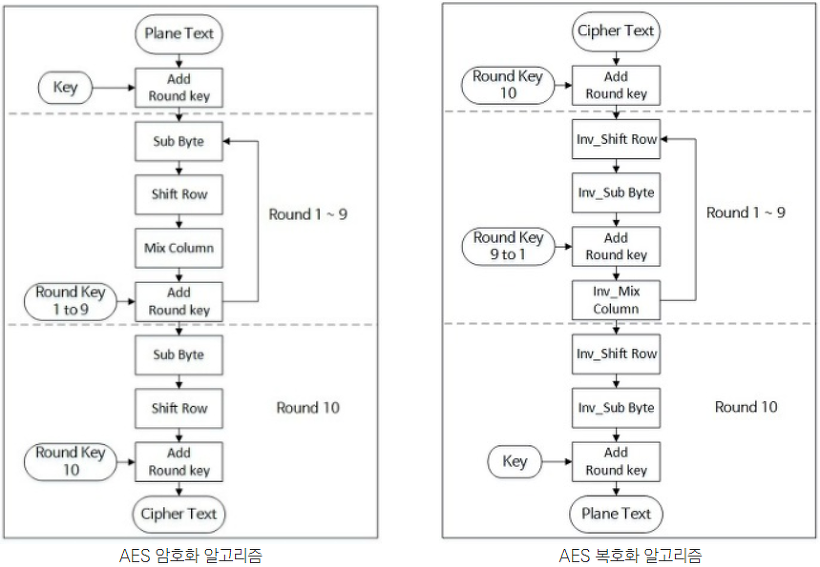
1. SubBytes 과정 (바이트 대체)
: 암호문이 비 선형성을 갖도록 하기 위해 바이트 단위로 역 변환이 가능한 S-box라는 표를 이용하여 블록을 교환한다.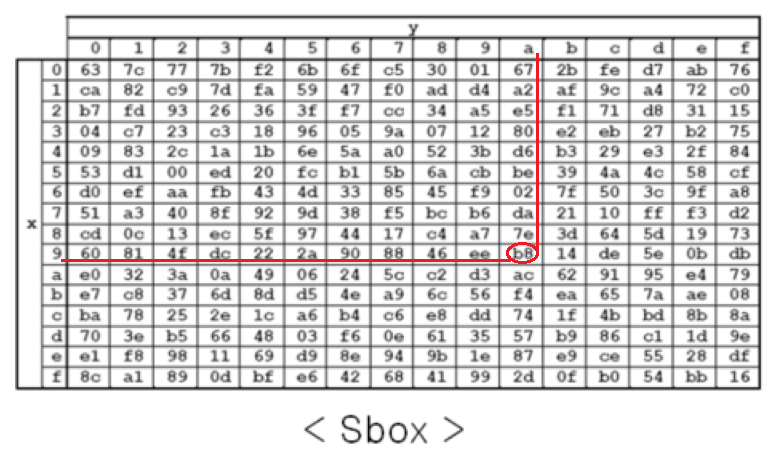
2. ShiftRows 과정 (행 이동)
: Shift 연산을 하여 단순히 행과 행을 치환하는데 4개의 행은 각각 왼쪽으로 Shift되지만 첫번째 행은 그 행의 맨 오른쪽 값으로 이동한다.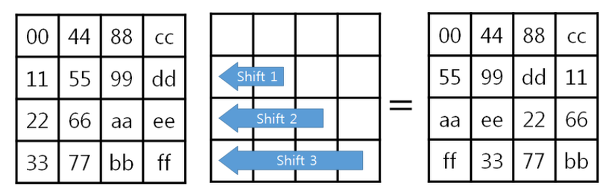
void ShiftRows()
{
unsigned char temp;
// Rotate first row 1 columns to left
temp = state[1][0];
state[1][0] = state[1][1];
state[1][1] = state[1][2];
state[1][2] = state[1][3];
state[1][3] = temp;
// Rotate second row 2 columns to left
temp = state[2][0];
state[2][0] = state[2][2];
state[2][2] = temp;
temp = state[2][1];
state[2][1] = state[2][3];
state[2][3] = temp;
// Rotate third row 3 columns to left
temp = state[3][0];
state[3][0] = state[3][3];
state[3][3] = state[3][2];
state[3][2] = state[3][1];
state[3][1] = temp;
}
3. Mixcolumn 과정 (열 섞기)
: 열 단위 연산을 수행한다. 열에 속한 모든 바이트를 순환 행렬을 사용해 함수로 열에 있는 각 바이트를 대체하여 변화시킨다. 참고로 마지막 라운드는 MixColumn을 하지 않는다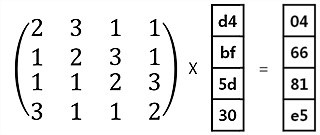
// xtime is a macro that finds the product of {02} and the argument to xtime modulo {1b}
#define xtime(x) ((x<<1) ^ (((x>>7) & 1) * 0x1b))
// MixColumns function mixes the columns of the state matrix
// The method used may look complicated, but it is easy if you know the underlying theory.
// Refer the documents specified above.
void MixColumns()
{
int i;
unsigned char Tmp, Tm, t;
for (i = 0; i<4; i++)
{
t = state[0][i];
Tmp = state[0][i] ^ state[1][i] ^ state[2][i] ^ state[3][i];
Tm = state[0][i] ^ state[1][i]; Tm = xtime(Tm); state[0][i] ^= Tm ^ Tmp;
Tm = state[1][i] ^ state[2][i]; Tm = xtime(Tm); state[1][i] ^= Tm ^ Tmp;
Tm = state[2][i] ^ state[3][i]; Tm = xtime(Tm); state[2][i] ^= Tm ^ Tmp;
Tm = state[3][i] ^ t; Tm = xtime(Tm); state[3][i] ^= Tm ^ Tmp;
}
}
4. AddRoundKey 과정 (라운드 키 더하기)
: 라운드 키와 현재 state 블록을 비트별로 XOR 한다.RoundKey는 key expansion schedule에 따라 key로부터 유도되어진다.
// This function adds the round key to state.
// The round key is added to the state by an XOR function.
void AddRoundKey(int round)
{
int i, j;
for (i = 0; i<4; i++)
for (j = 0; j<4; j++)
state[j][i] ^= RoundKey[round * Nb * 4 + i * Nb + j];
}5. AES 암호화, 복호화 알고리즘
참고) 대칭형 알고리즘
:암호화 할 때의 key와 복호화 할 때의 key 값이 같으면 대칭키라고 한다. 대칭키를 사용하는 암호화를 '대칭형 암호 알고리즘'이라고 하고 대표적인 예로는 SEED, DES, DES3, AES 등이 있다.
대칭 암호화 방식
자신의 키로 메세지를 암호화라고 키를 수신자에게 보내면 키를 이용해 복호화하는 방식이다. 키를 공유해야하기 때문에 키가 공격자에게 노출되면 보안에 취약해지지만 비대칭 암호화 방식에 비해 키 사이즈가 작고 알고리즘 구조가 간단해서 속도가 빨라 효율적이다.
Reference
https://developer-mac.tistory.com/59
https://www.crocus.co.kr/1230
https://gaeko-security-hack.tistory.com/106