EBS (Elastic Block Store)
Primary offering to create and manage file systems and disc space, it is thick provisioned
Basics
- It is accessed through EC2 endpoint
- OS will view it as a local block device
Volume Types
SSD
SSD is designed for primarily smaller bits of data that are accessed randomly.
gp2
Operates on a creadit and burst system.
gp3
Allows to provision the number of IOPS and the amount of throughput for the storage.
Has a lower ceiling for the overall performance.
HDD
Designed for larger transfer of data that are on contiguous space on the volume itself.
ST1
Throughput optimized, better performance than sc1 but also cost a bit more
SC1
Cold storage
Setup EBS with Console
- Go to EC2 console
- Go to EBS Volumes
- Click on Create volume
- Leave the default, enable encryption
- Create
S3
Region scoped object storage that is designed for durability
Object storage means that you cannot edit any files, you can only overwrite. So if you edit one word in a text file, it's going to overwrite the entire file.
It's optimized for WORM (write once, read many) workloads.
Basics
When you place an object in an S3 bucket, you are actually creating multiple replicas of that object.
Storage Classes
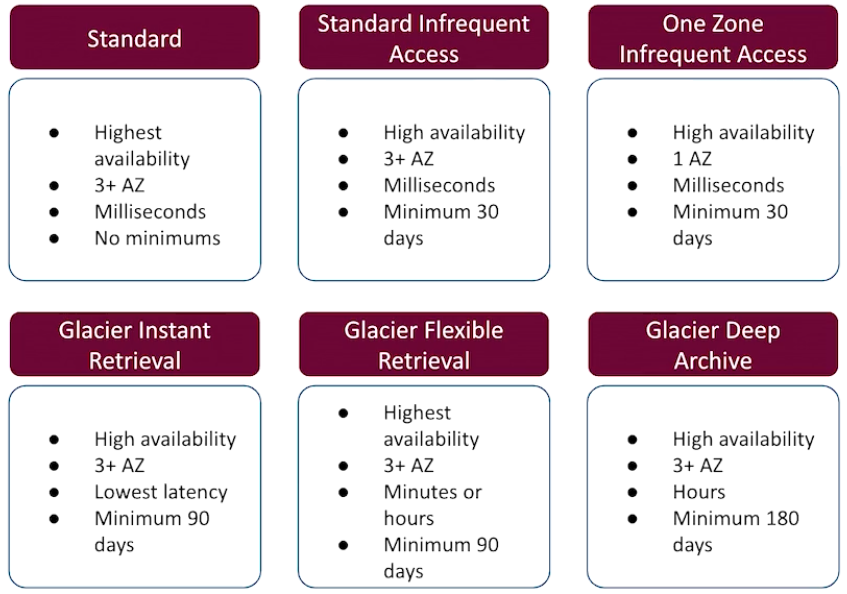
S3 Intelligent Tiering actually moves objects within each class to fit the appropriate use cases.
Features
Bucket policy
Acts similar to an IAM policy to grant or restrict access to the bucket
Bucket/object ACLs (Access Control Lists)
If you create a pre-signed URL for an objects in an S3 bueckt, it uses an ACL to provide that permission
Object encryption
Lifecycle rules
Move data through different classes of buckets as they age
S3 Versioning
Turns the bucket into a version contro system
Glacier Vault Lock
Guarantee that the data will not be deleted under any circumstances
Vault Log
A resource based policy you only get 24 hours to verify, and after the verification, that policy is locked forever.
Objects in S3
Every single object has its own URL that ou can use to access.
However, the data is private by default.
You can also create a pre-signed URL for the client to use without specific authentication and permissions to do so.
If you turn the bucket into a static web, you CANNOT use HTTPS.
Creating S3 Bucket in Console
- Click Create bucket
- For most use cases, ACLs can be disabled
- Leave the default setting
- Enable Deafult encryption, Amazon managed
- Create bucket
Bucket Access from EC2 CLI
Copy a local file to S3
- Copy to S3, if error occurs, you might have to add a region setting
$ aws s3 cp ./FILE_NAME s3://END_POINT- Copy dir is almost the same
$ aws s3 cp ./YOUR_DIR/ s3://END_POINT --recursive- Copy data from one bucket to another
$ aws s3 cp s3://FIRST_BUCKET/object_name s3://SECOND_BUCKETPublic Access in Console
The first two are for ACLs
Latter two are for bucket policies
Good practice would be to make public connections that are required AND THEN block public access for NEW connections.
Lifecycle Operations in Console
- Go to bucket, click on Management
- Create lifecycle rule
- If there are overlapping logic, AWS will give a warning but it won't stop the action
- So having an extensive rule is better than having multiple modular rules
Disclaimer
This summary is made possible by Oreilly's AWS, 3rd Edition - Chad Smith.
If the above post violates any copyright permissions, please let me know!

