-----------------
--- azure_set ---
-----------------
# git clone https://github.com/hali-linux/azure_set.git
# vi variables.tf
variable "resource_group_name_prefix" {
default = "rg"
description = "Prefix of the resource group name that's combined with a random ID so name is unique in your Azure subscription."
}
variable "resource_group_location" {
default = "koreacentral"
description = "Location of the resource group."
}
# vi main.tf
provider "azurerm" {
features {}
}
resource "random_pet" "rg-name" {
prefix = var.resource_group_name_prefix
}
resource "azurerm_resource_group" "rg" {
name = random_pet.rg-name.id
location = var.resource_group_location
}
# Create virtual network
resource "azurerm_virtual_network" "myterraformnetwork" {
name = "myVnet"
address_space = ["10.219.0.0/16"]
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
}
# Create subnet
resource "azurerm_subnet" "myterraformsubnet" {
name = "mySubnet"
resource_group_name = azurerm_resource_group.rg.name
virtual_network_name = azurerm_virtual_network.myterraformnetwork.name
address_prefixes = ["10.219.0.0/24"]
}
# Create public IPs
resource "azurerm_public_ip" "myterraformpublicip" {
name = "myPublicIP"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
allocation_method = "Dynamic"
}
# Create Network Security Group and rule
resource "azurerm_network_security_group" "myterraformnsg" {
name = "myNetworkSecurityGroup"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
security_rule {
name = "SSH"
priority = 1001
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "22"
source_address_prefix = "112.221.225.165/32"
destination_address_prefix = "*"
}
security_rule {
name = "HTTP"
priority = 1002
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "80"
source_address_prefix = "*"
destination_address_prefix = "*"
}
}
# Create network interface
resource "azurerm_network_interface" "myterraformnic" {
name = "myNIC"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
ip_configuration {
name = "myNicConfiguration"
subnet_id = azurerm_subnet.myterraformsubnet.id
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.myterraformpublicip.id
}
}
# Connect the security group to the network interface
resource "azurerm_network_interface_security_group_association" "example" {
network_interface_id = azurerm_network_interface.myterraformnic.id
network_security_group_id = azurerm_network_security_group.myterraformnsg.id
}
# Create (and display) an SSH key
resource "tls_private_key" "example_ssh" {
algorithm = "RSA"
rsa_bits = 4096
}
# Create virtual machine
resource "azurerm_linux_virtual_machine" "myterraformvm" {
name = "myVM"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
network_interface_ids = [azurerm_network_interface.myterraformnic.id]
size = "Standard_B1s"
os_disk {
name = "myOsDisk"
caching = "ReadWrite"
storage_account_type = "Premium_LRS"
}
source_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "18.04-LTS"
version = "latest"
}
computer_name = "myvm"
admin_username = "azureuser"
custom_data = filebase64("httpd-azure.txt")
disable_password_authentication = true
admin_ssh_key {
username = "azureuser"
public_key = tls_private_key.example_ssh.public_key_openssh
}
}
# vi outputs.tf
output "resource_group_name" {
value = azurerm_resource_group.rg.name
}
output "public_ip_address" {
value = azurerm_linux_virtual_machine.myterraformvm.public_ip_address
}
output "tls_private_key" {
value = tls_private_key.example_ssh.private_key_pem
sensitive = true
}
# terraform init
# terraform plan
# terraform apply
# terraform output -raw tls_private_key > azure-key.pem // 프라이빗 키를 PEM키로 만들겠다.
# terraform output public_ip_address
# ssh -i azure-key.pem azureuser@<public_ip_address>
gcp cli
--- GCP CLI
# mkdir gcp_cli && cd $_
# tee -a /etc/yum.repos.d/google-cloud-sdk.repo << EOM
[google-cloud-cli]
name=Google Cloud CLI
baseurl=https://packages.cloud.google.com/yum/repos/cloud-sdk-el8-x86_64
enabled=1
gpgcheck=1
repo_gpgcheck=0
gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg
https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg
EOM
# yum install -y google-cloud-cli
# gcloud --version
# gcloud init --console-only
asia-northeast3-a
# gcloud compute networks create new-vpc --subnet-mode=custom
+# gcloud compute networks subnets create new-subnet --network=new-vpc --range=192.168.0.0/16 --region=asia-northeast3
# gcloud compute firewall-rules list
# gcloud compute firewall-rules create new-vpc-allow-ssh --allow=tcp:22 --description="Allow incoming traffic on TCP port 22" --direction=INGRESS --network=new-vpc --source-ranges 0.0.0.0/0
# gcloud compute firewall-rules create new-vpc-allow-http --allow=tcp:80 --description="Allow incoming traffic on TCP port 80" --direction=INGRESS --network=new-vpc --source-ranges 0.0.0.0/0
# gcloud compute images list
# gcloud compute images describe centos-7-v20220621 \
--project=centos-cloud
# gcloud compute machine-types list --filter="zone:( asia-northeast3-a )"
# vi httpd-gcp.txt
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello GCP CLI" > /var/www/html/index.html
# gcloud compute instances create web01 \
--image=centos-7-v20220621 \
--image-project=centos-cloud \
--machine-type=e2-micro \
--network=new-vpc \
--subnet=new-subnet \
--tags http-server,https-server \
--zone=asia-northeast3-a \
--metadata-from-file=startup-script=httpd-gcp.txt
# ssh-keygen -t rsa -f /root/.ssh/wony -C wony -b 2048 // 키 생성. wony 는 키이름
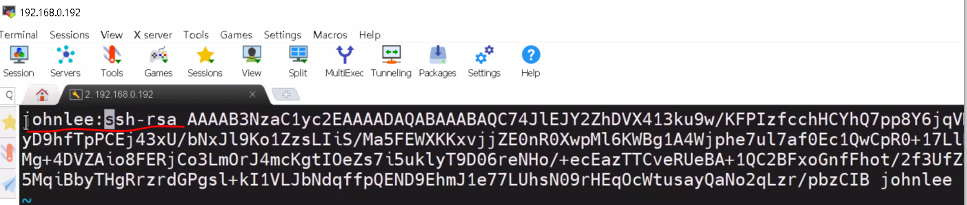
# vi /root/.ssh/wony.pub
wony:ssh-rsa
# gcloud compute os-login ssh-keys add \
--key-file=/root/.ssh/wony.pub \
--project=gcp-wony2022 \
--ttl=365d
# gcloud compute instances add-metadata web01 --metadata-from-file ssh-keys=/root/.ssh/wony.pub
# gcloud compute instances describe web01
# curl 34.64.150.44
# ssh -i /root/.ssh/wony wony@34.64.150.44
# gcloud compute instances delete web01
# gcloud compute firewall-rules list
# gcloud compute firewall-rules delete new-vpc-allow-http
# gcloud compute firewall-rules delete new-vpc-allow-ssh
# gcloud compute networks subnets delete new-subnet
# gcloud compute networks delete new-vpc
# vi /root/.ssh/wony.pub 넣어주어야한다.
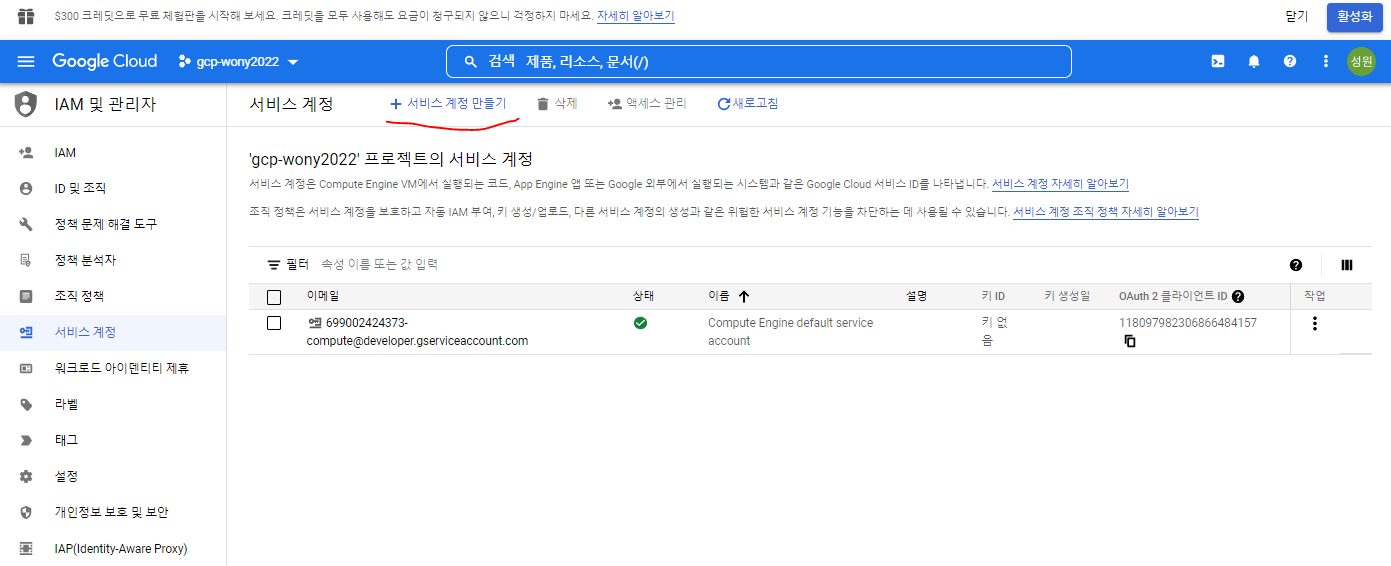
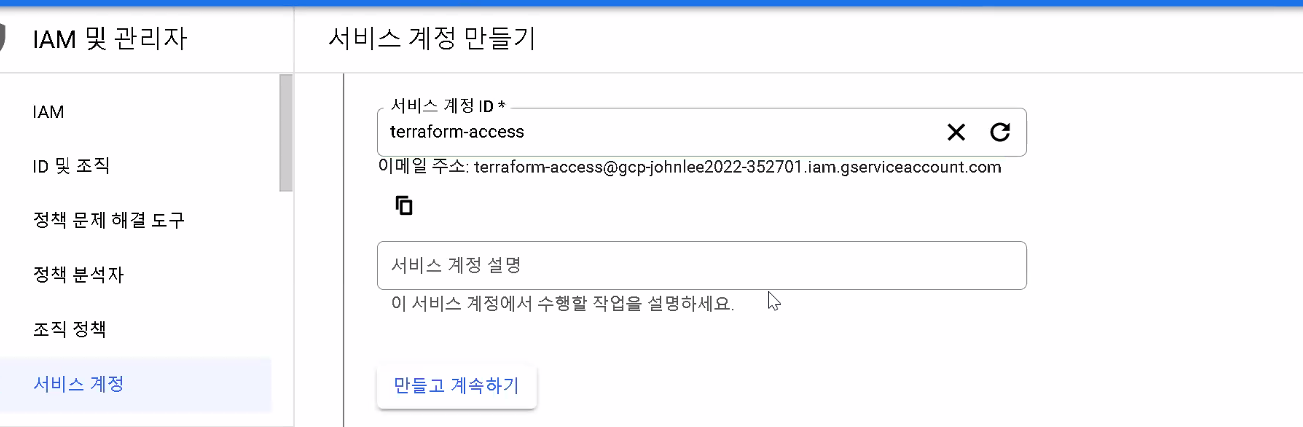
gcp Terraform 사용자 만들기
---------------
--- gcp_set ---
---------------
# git clone https://github.com/hali-linux/gcp_set.git
# vi provider.tf
provider "google" {
credentials = file("credentials.json")
project = "gcp-wony2022"
region = "asia-northeast3"
zone = "asia-northeast3-a"
}
# vi main.tf
resource "google_compute_network" "custom-test" {
name = "new-vpc"
auto_create_subnetworks = false
}
resource "google_compute_subnetwork" "network-with-private-ip-ranges" {
name = "new-subnet"
ip_cidr_range = "192.168.0.0/16"
region = "asia-northeast3"
network = google_compute_network.custom-test.id
}
resource "google_compute_instance" "default" {
name = "vm-from-terraform"
machine_type = "e2-micro"
zone = "asia-northeast3-a"
boot_disk {
initialize_params {
image = "debian-cloud/debian-9"
}
}
network_interface {
network = "new-vpc"
subnetwork = "new-subnet"
access_config {
// Include this section to give the VM an external ip address
}
}
metadata_startup_script = file("/root/gcp_set/script.txt")
// Apply the firewall rule to allow external IPs to access this instance
tags = ["http-server","ssh-server"]
}
resource "google_compute_firewall" "http-server" {
name = "default-allow-http-terraform"
network = "new-vpc"
allow {
protocol = "tcp"
ports = ["80"]
}
// Allow traffic from everywhere to instances with an http-server tag
source_ranges = ["0.0.0.0/0"]
target_tags = ["http-server"]
}
resource "google_compute_firewall" "ssh-server" {
name = "default-allow-http-terraform"
network = "new-vpc"
allow {
protocol = "tcp"
ports = ["22"]
}
source_ranges = ["0.0.0.0/0"]
target_tags = ["ssh-server"]
}
# vi output.tf
output "ip" {
value = "${google_compute_instance.default.network_interface.0.access_config.0.nat_ip}"
}
# terraform init
# terraform plan
# terraform apply
# terraform output ip
# gcloud compute instances add-metadata vm-from-terraform --metadata-from-file ssh-keys=/root/.ssh/wony.pub
[root@localhost gcp_set]# ssh -i /root/.ssh/wony wony@34.64.171.4
ssh 오류뜨면 .ssh/knownhost 날려준다
Ansible
우분투 설치
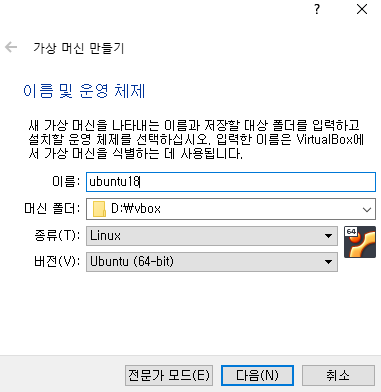
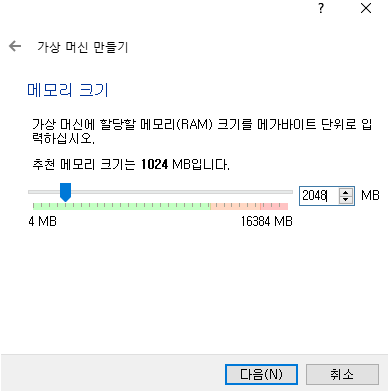
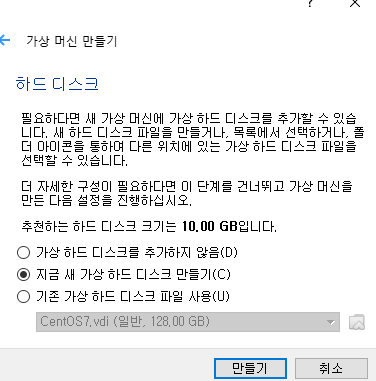

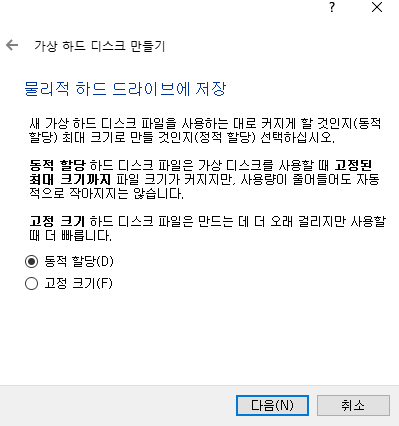
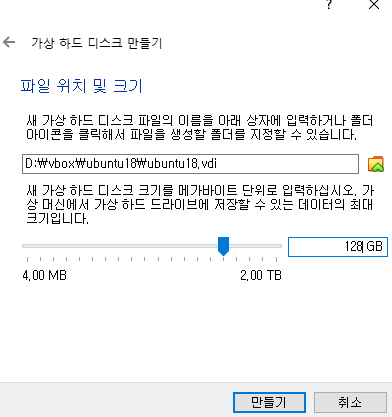
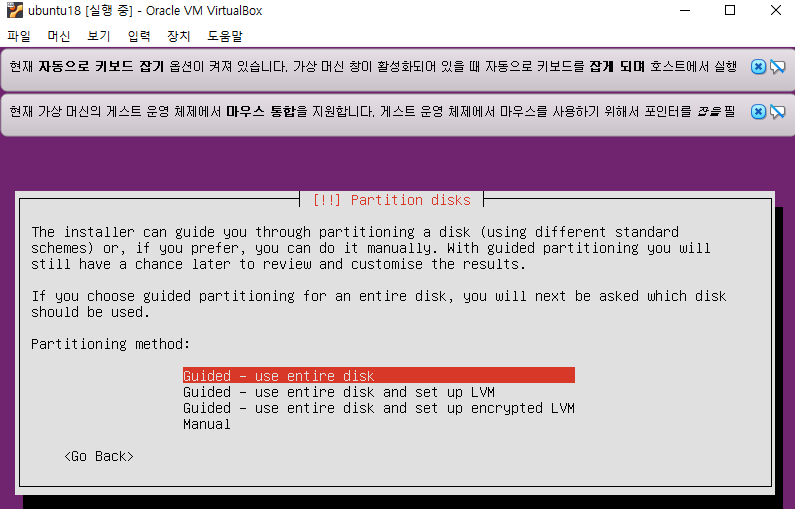
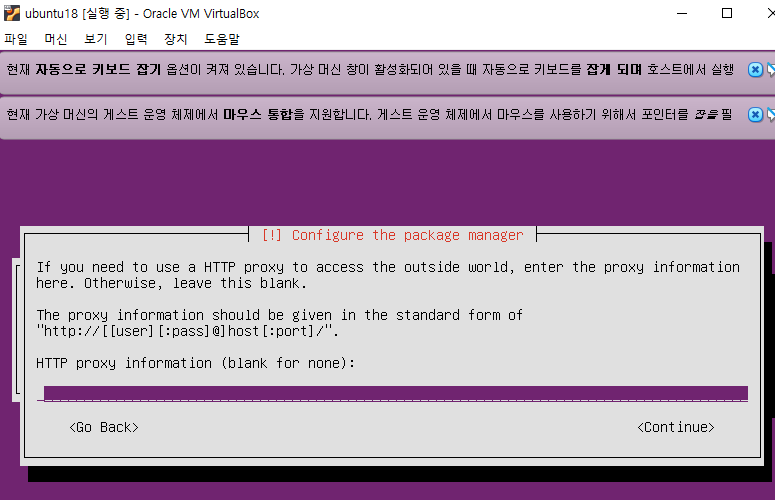
빈칸 엔터
root 계정 접근 후 (ssh/sshd_config) permit 어쩌구 변경
sudo -su ?
systemctl restart sshd
