Introduction
This section briefly covers the way in which to investigate threat cases such as Spear Phishing, User Execution.
Spear Phishing
Let's follow the below questions.
What data sources (sourcetypes) should we look for mail traffic in?
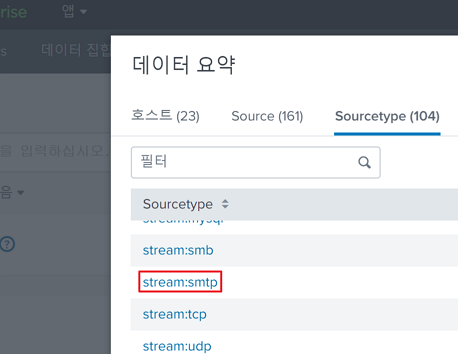
The first question is asking about the sourcetypes in which we can look for email traffic.
The summary of the provided sourcetypes can be found in the "Data Summary" tab under "Search & Reporting":
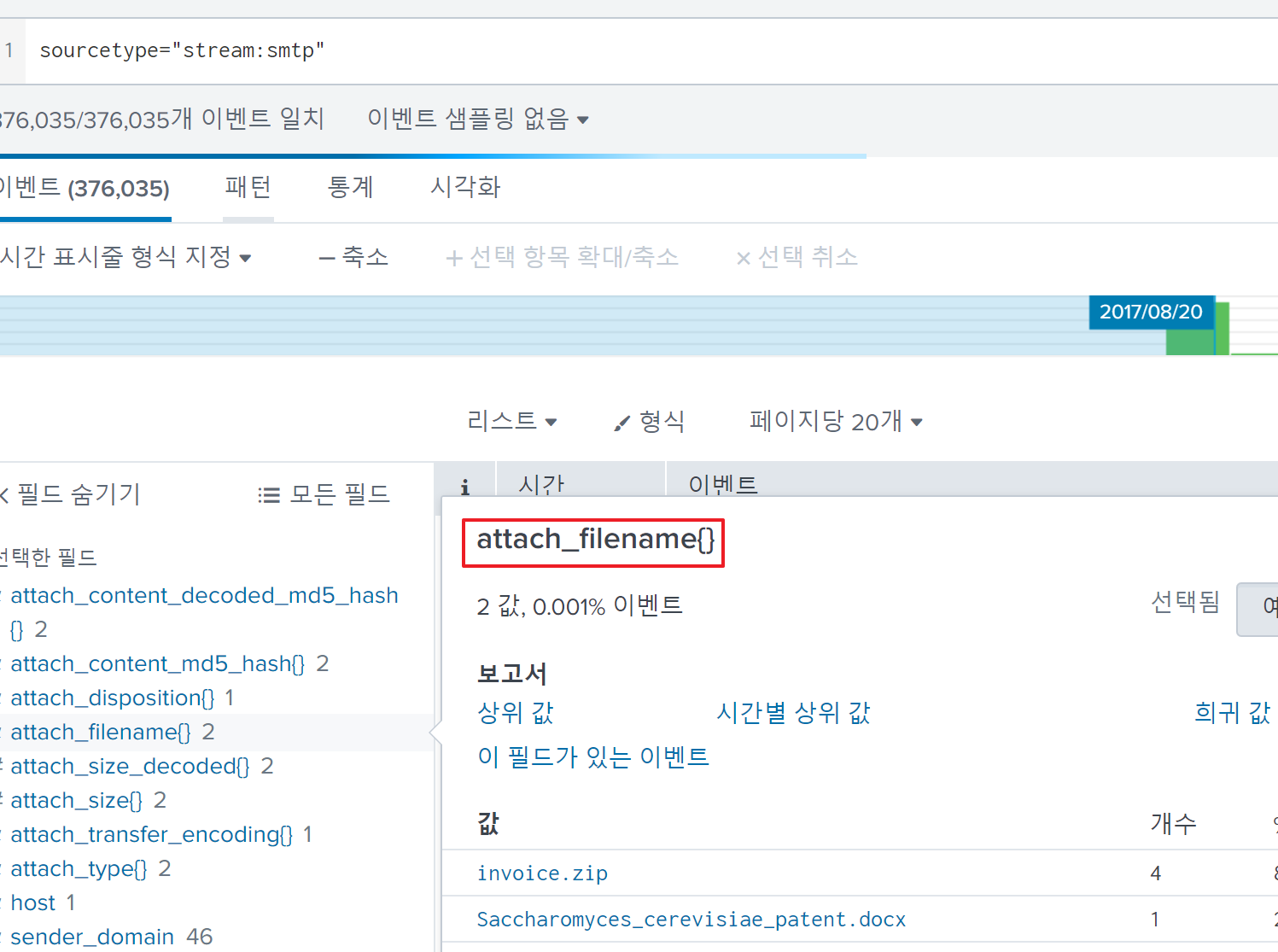
If we are hypothesizing about email attachments, do we have visibility into what email attachments are being received?
In the sourcetype stream:smtp, you can see the attach_filename{} field.
Are there specific kinds of attachments that we should be hunting for?
Definitely, theMalware Alert Text.txt which blatantly includes the word Malware makes me suspicious.
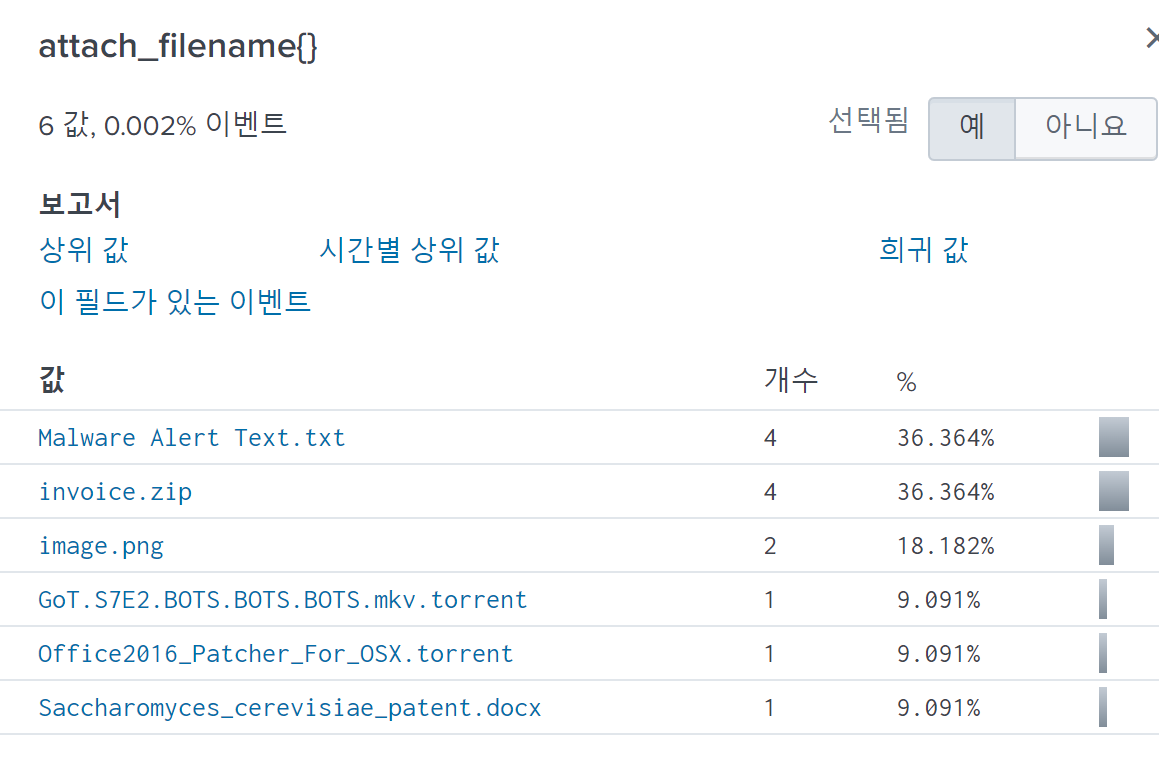
Also, both the invoice.zip, which might contain a malicious file and the Saccharomyces_cerevisiae_patent.docx that might be mimicking a benign document are notable for me.
If we find attachments of interest, what attributes are associated with it?
First, when I set the condition to include the string Malware Alert Text.txt in the results, the result log showed the base64-encoded content of the Malware Alert Text.txt file, which was stored in the content field.
Additionally, its decoded value is as follows:
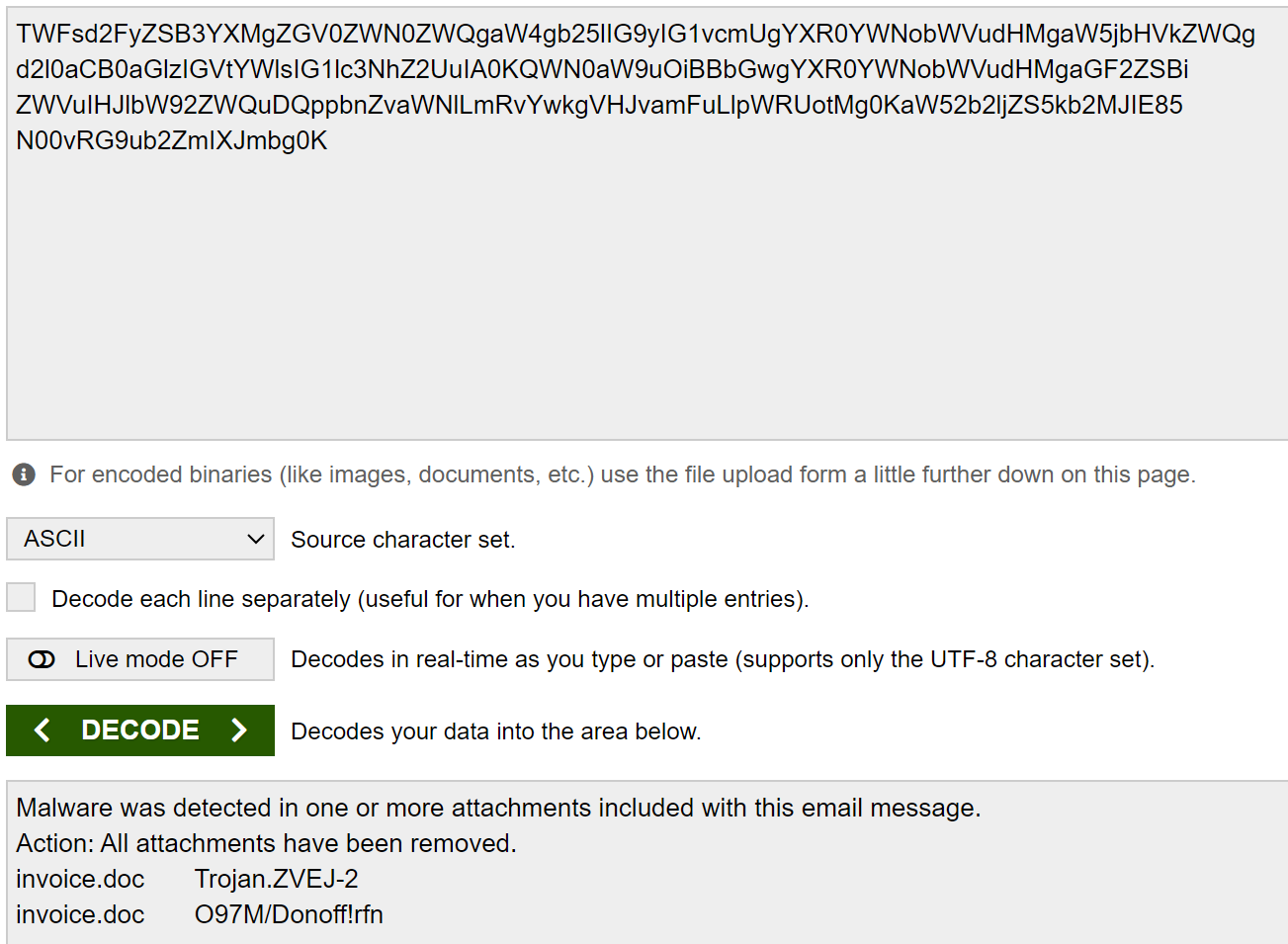
It clearly indicates that the attached file is malware and that it, in and of itself, is an email for alerting the receiver.
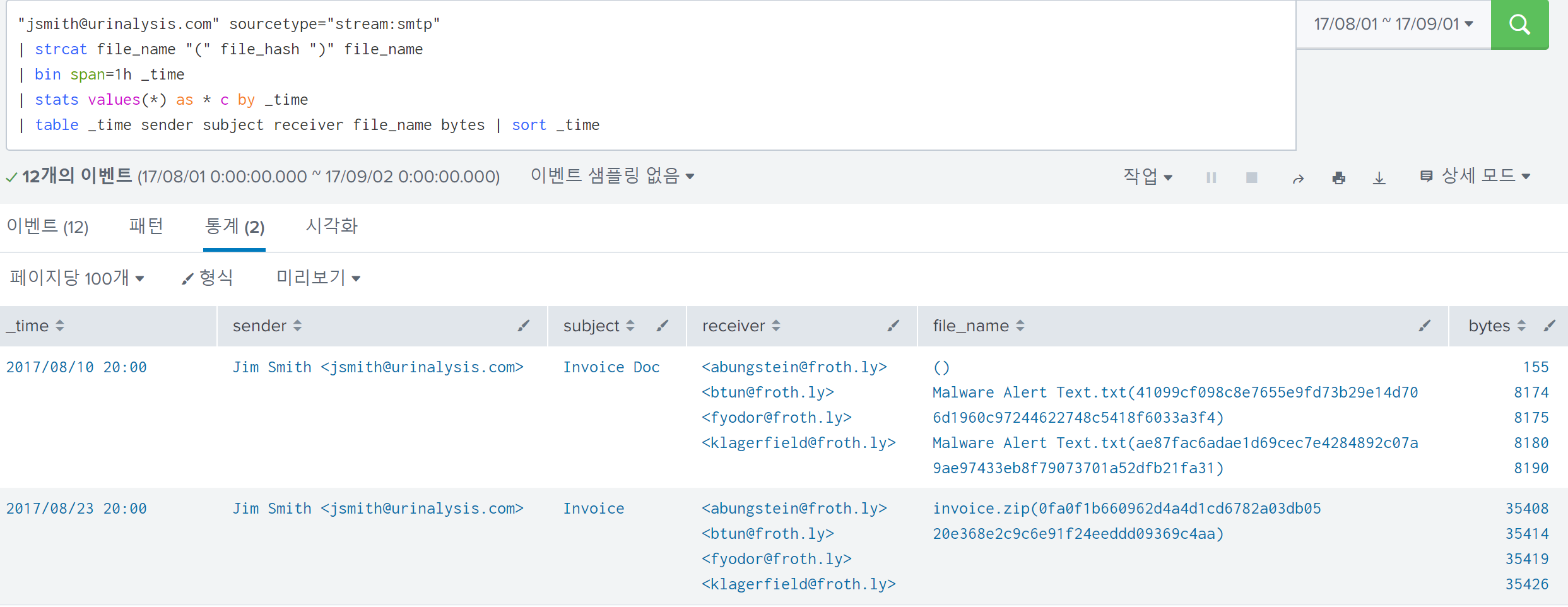
Additionally, taking a look at the sender field, you can see that the aforementioned emails all were sent from jsmith@urinalysis.com to each unique receiver.
Do we see those attributes in other emails?
Naturally, the attach_filename{} field can be found when a file was attached in an email.
In some cases, I could see that the sender field might not be contained in stream:smtp logs.
To verify the difference between when the sender field is included and when it is not, I extracted all fields of the two cases and compared them:
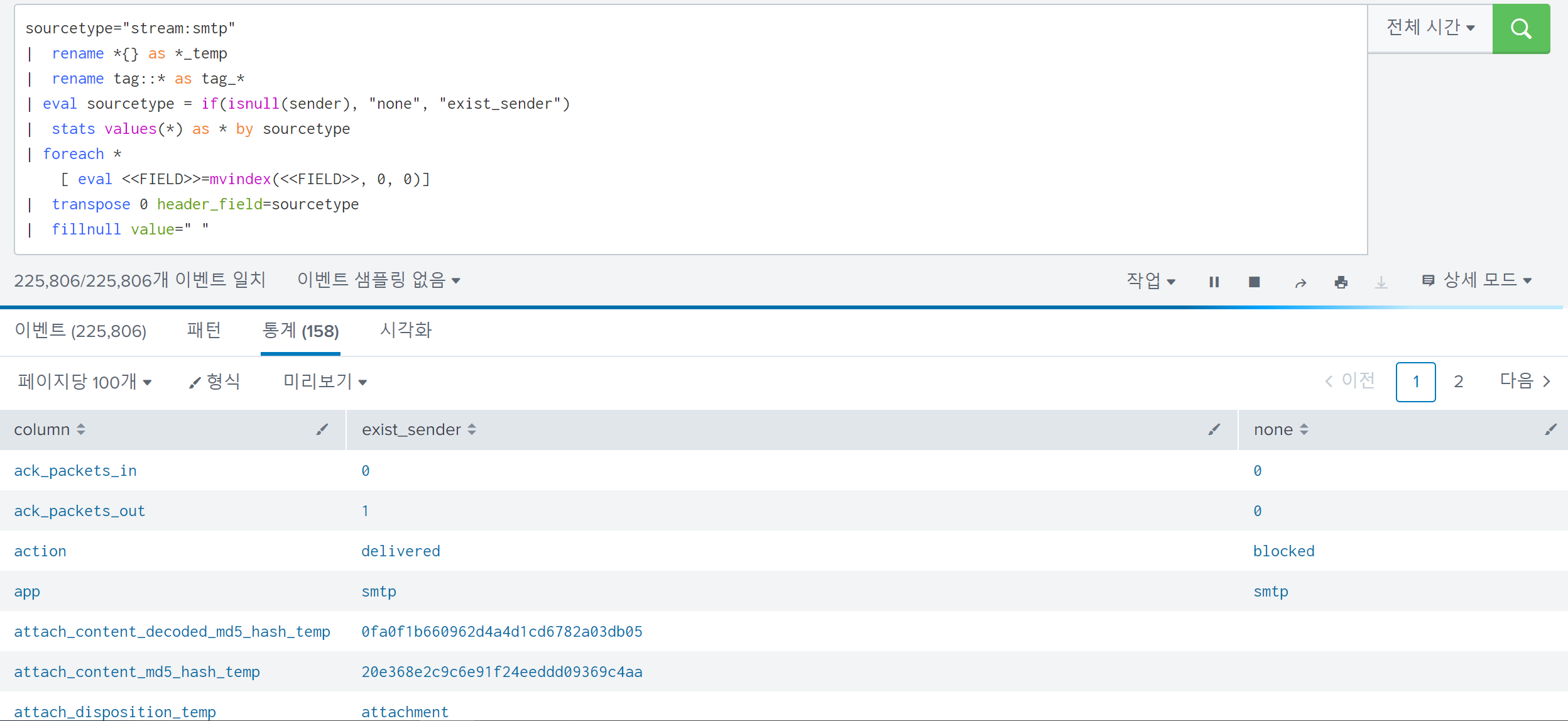
Unfortunately, there is no explicit difference between them.
Are there prior spearphishing attempts that were unsuccessful that can be leveraged?
The answer to this question is the smtp traffic sent by jsmith@urinalysis.com along withMalware Alert Text.txt file.
It is more clear by sorting smtp traffics sent by jsmith@urinalysis.com in chronological order: