📌 VPC 구축하기
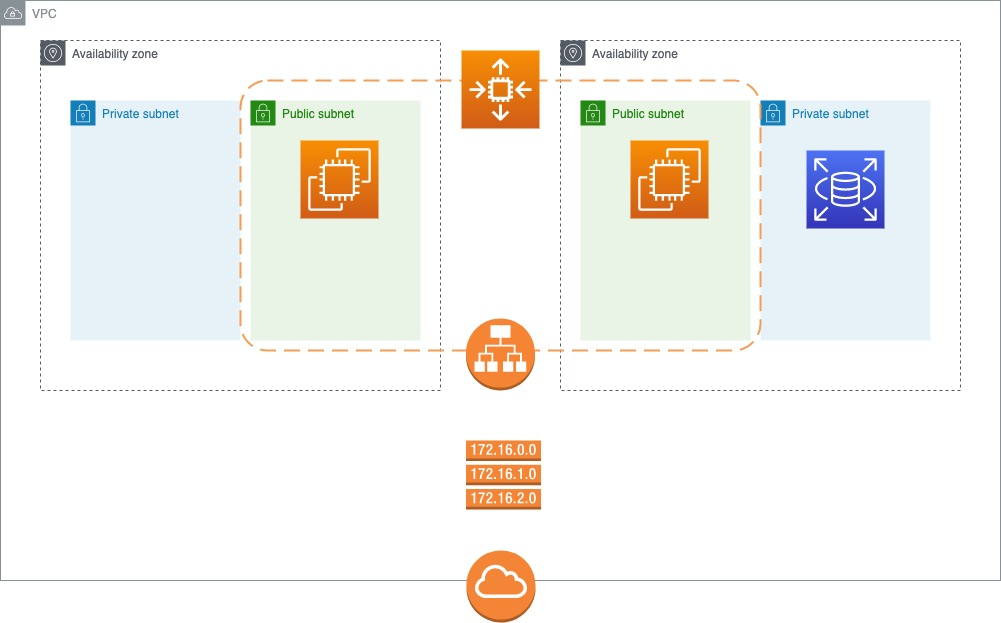
아키텍처에 부합하는 인스턴스를 구축하기전 가상의 프라이빗 네트워크 망을 구축한다.
👉 Provider Version
사용할 프로바이더의 버전을 명시한다.
~> 4.16 :: 4.16 버전보다 높은 버전을 사용할 것을 명시함.
# version.tf
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.16"
}
}
}
provider "aws" {
region = "ap-northeast-2"
}👉 VPC
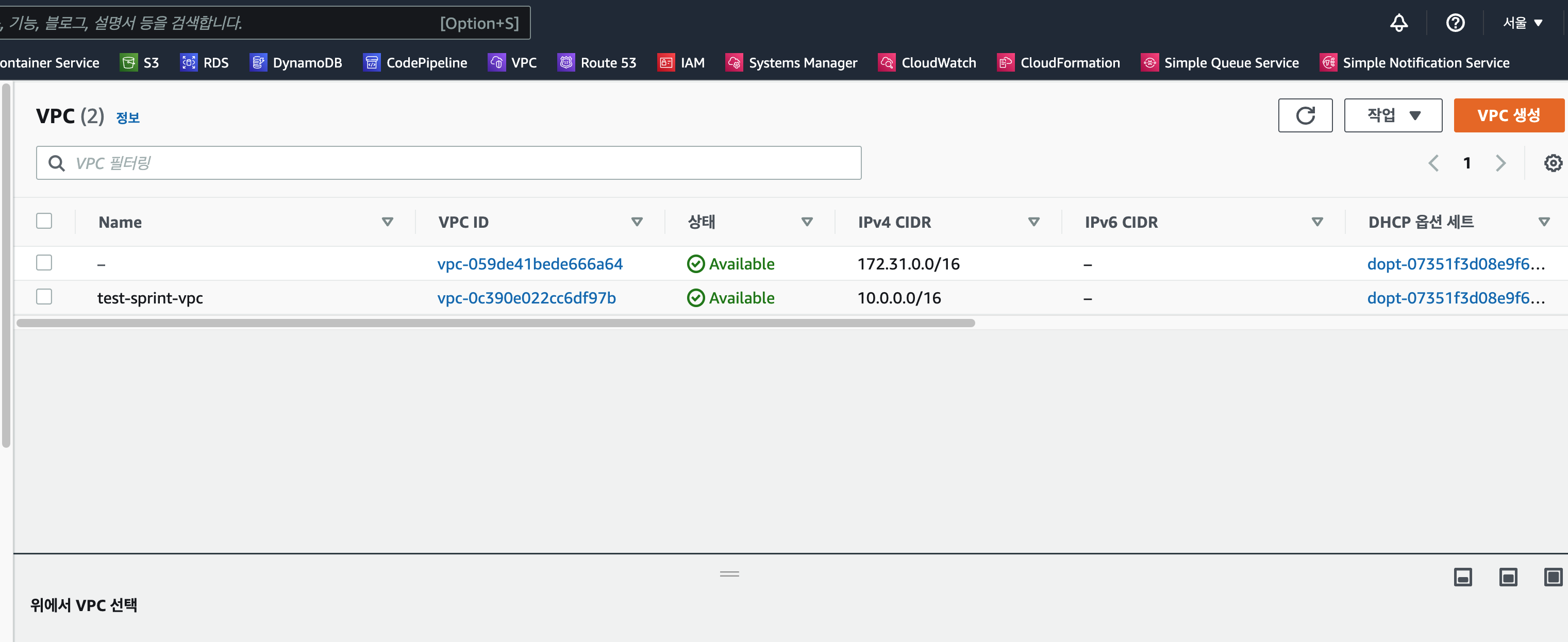
VPC를 생성한다.
CIDR 블록 - 10.0.0.0/16
# vpc.tf
resource "aws_vpc" "vpc" {
cidr_block = "10.0.0.0/16"
tags = {
Name = "test-sprint-vpc"
}
}- 결과
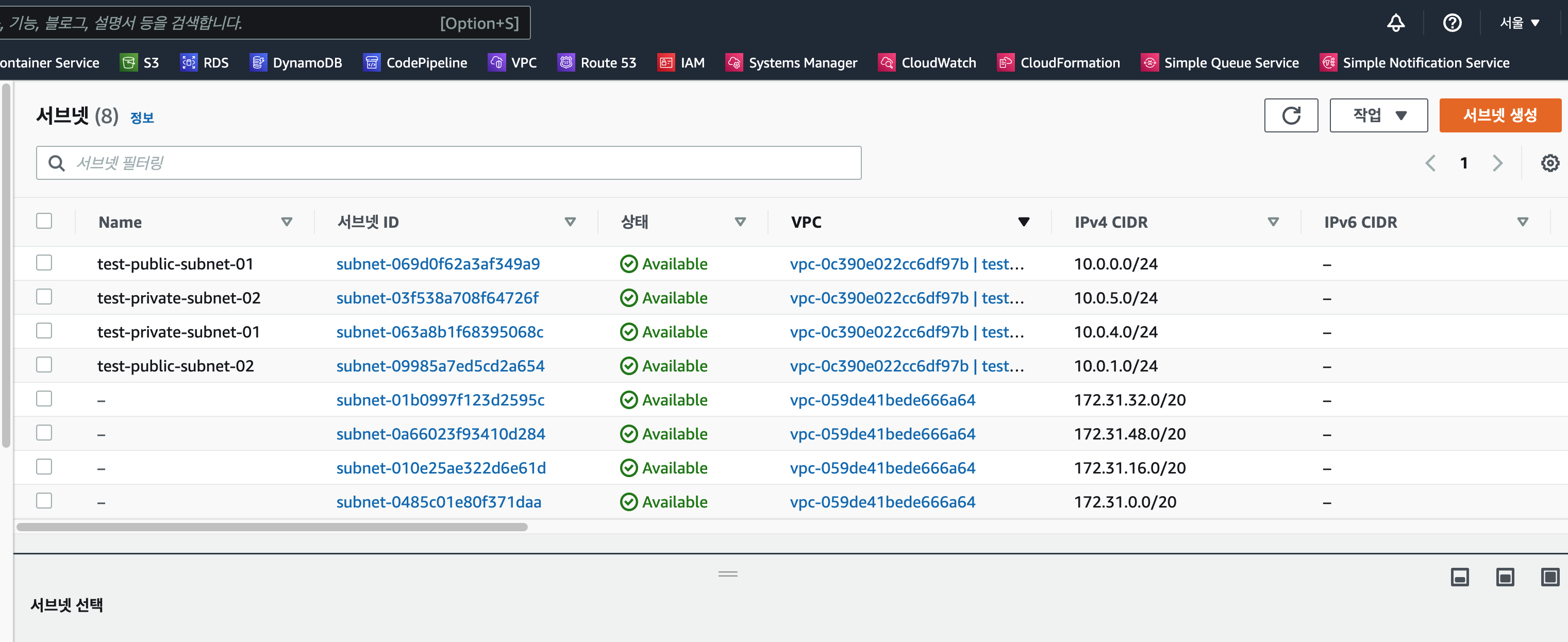
👉 Subnet
- PublicSubnet - 2a, 2c
- PrivateSubnet - 2a, 2c
를 각각 생성하고, 해당되는 CIDR 블록을 명시한다.
# subnet.tf
resource "aws_subnet" "publicSubnet1" {
vpc_id = aws_vpc.vpc.id
cidr_block = "10.0.0.0/24"
availability_zone = "ap-northeast-2a"
tags = {
"Name" = "test-public-subnet-01"
}
}
resource "aws_subnet" "publicSubnet2" {
vpc_id = aws_vpc.vpc.id
cidr_block = "10.0.1.0/24"
availability_zone = "ap-northeast-2c"
tags = {
"Name" = "test-public-subnet-02"
}
}
## private rds subnet
resource "aws_subnet" "privateSubnet1" {
vpc_id = aws_vpc.vpc.id
cidr_block = "10.0.4.0/24"
availability_zone = "ap-northeast-2a"
tags = {
"Name" = "test-private-subnet-01"
}
}
resource "aws_subnet" "privateSubnet2" {
vpc_id = aws_vpc.vpc.id
cidr_block = "10.0.5.0/24"
availability_zone = "ap-northeast-2c"
tags = {
"Name" = "test-private-subnet-02"
}
}
👉 Internet Gateway
Default로 생성 되지만, 별도의 Name을 부여해서 관리하고자 설정함.
# igw.tf
resource "aws_internet_gateway" "testIGW" {
vpc_id = aws_vpc.vpc.id
tags = {
"Name" = "testIGW"
}
}- 결과
👉 Route table
- Public 외부로 통신하기 위해서 위에서 생성한 IGW와 연결해준다. Public Subnet과 연결한다.
- Private 내부 통신을 위한 라우팅이므로 별도로 설정하지 않는다. Private Subnet과 연결한다.
# route.tf
resource "aws_route_table" "testPublicRTb" {
vpc_id = aws_vpc.vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.testIGW.id
}
tags = {
"Name" = "test-public-rtb"
}
}
resource "aws_route_table" "testPrivateRTb" {
vpc_id = aws_vpc.vpc.id
tags = {
"Name" = "test-private-rtb"
}
}
## route
### subnet associate
resource "aws_route_table_association" "publicRTbAssociation01" {
subnet_id = aws_subnet.publicSubnet1.id
route_table_id = aws_route_table.testPublicRTb.id
}
resource "aws_route_table_association" "publicRTbAssociation02" {
subnet_id = aws_subnet.publicSubnet2.id
route_table_id = aws_route_table.testPublicRTb.id
}
resource "aws_route_table_association" "privateRTbAssociation01" {
subnet_id = aws_subnet.privateSubnet1.id
route_table_id = aws_route_table.testPrivateRTb.id
}
resource "aws_route_table_association" "privateRTbAssociation02" {
subnet_id = aws_subnet.privateSubnet2.id
route_table_id = aws_route_table.testPrivateRTb.id
}- 결과
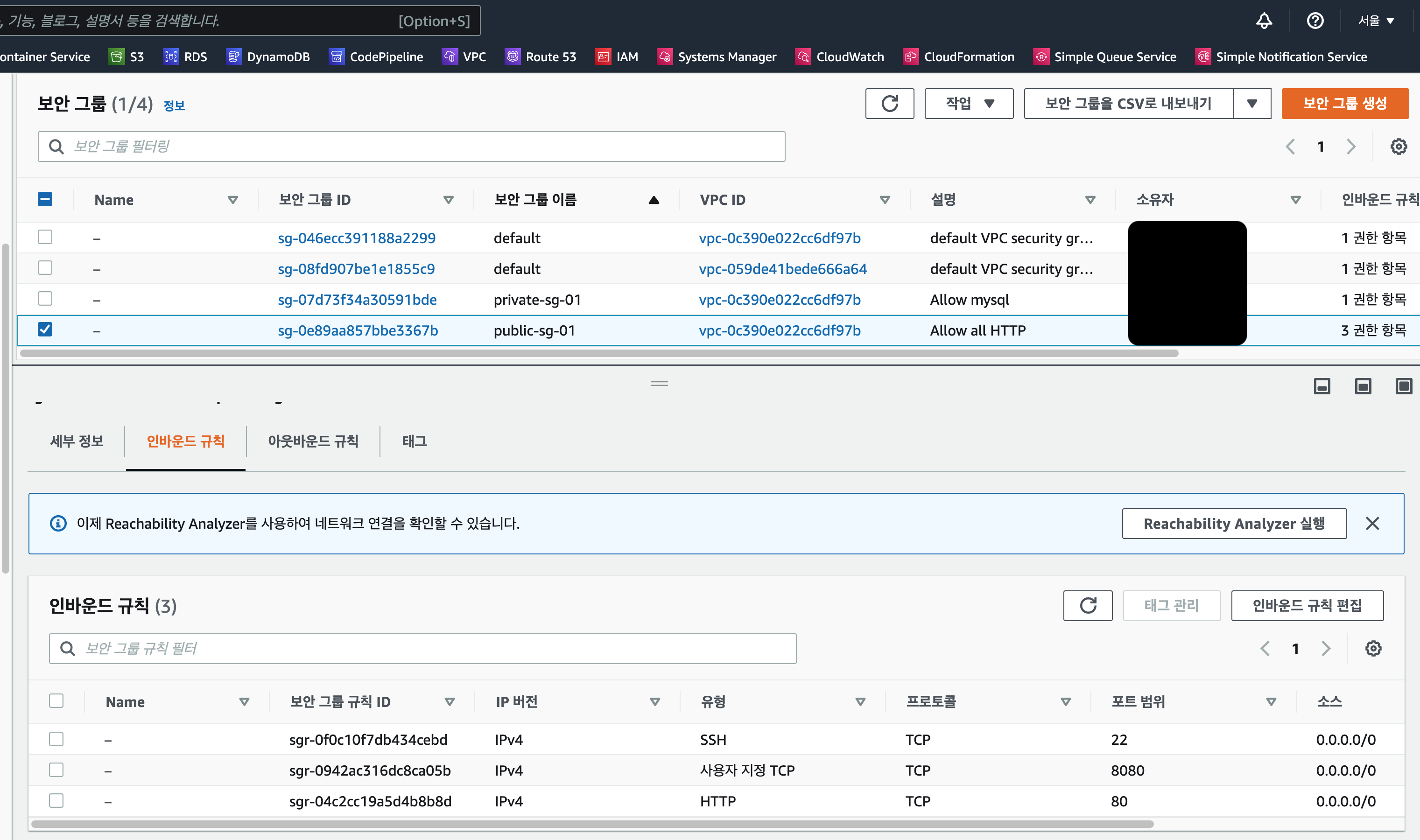
👉 Security groups
EC2 통신을 위한 인바운드 규칙적용된 sg를 생성한다.
이번 과정에서는 80포트가 아닌, 8080 포트로 웹서버 구축함.
RDS 통신을 위해서 인바운드 3306을 오픈한 프라이빗 sg를 별도로 생성한다.
# sg.tf
## public Seucurity Group
resource "aws_security_group" "publicSG01" {
name = "public-sg-01"
description = "Allow all HTTP"
vpc_id = aws_vpc.vpc.id
ingress {
description = "For http port"
protocol = "tcp"
from_port = 80
to_port = 80
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "For http port"
protocol = "tcp"
from_port = 8080
to_port = 8080
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
description = "For ssh port"
protocol = "tcp"
from_port = 22
to_port = 22
cidr_blocks = ["0.0.0.0/0"]
}
egress {
cidr_blocks = ["0.0.0.0/0"]
from_port = 0
protocol = "-1"
to_port = 0
}
}
## private Security Group
resource "aws_security_group" "privateSG01" {
name = "private-sg-01"
description = "Allow mysql"
vpc_id = aws_vpc.vpc.id
ingress {
description = "For mysql port"
protocol = "tcp"
from_port = 3306
to_port = 3306
cidr_blocks = ["0.0.0.0/0"]
}
egress {
cidr_blocks = ["0.0.0.0/0"]
from_port = 0
protocol = "-1"
to_port = 0
}
}- 결과