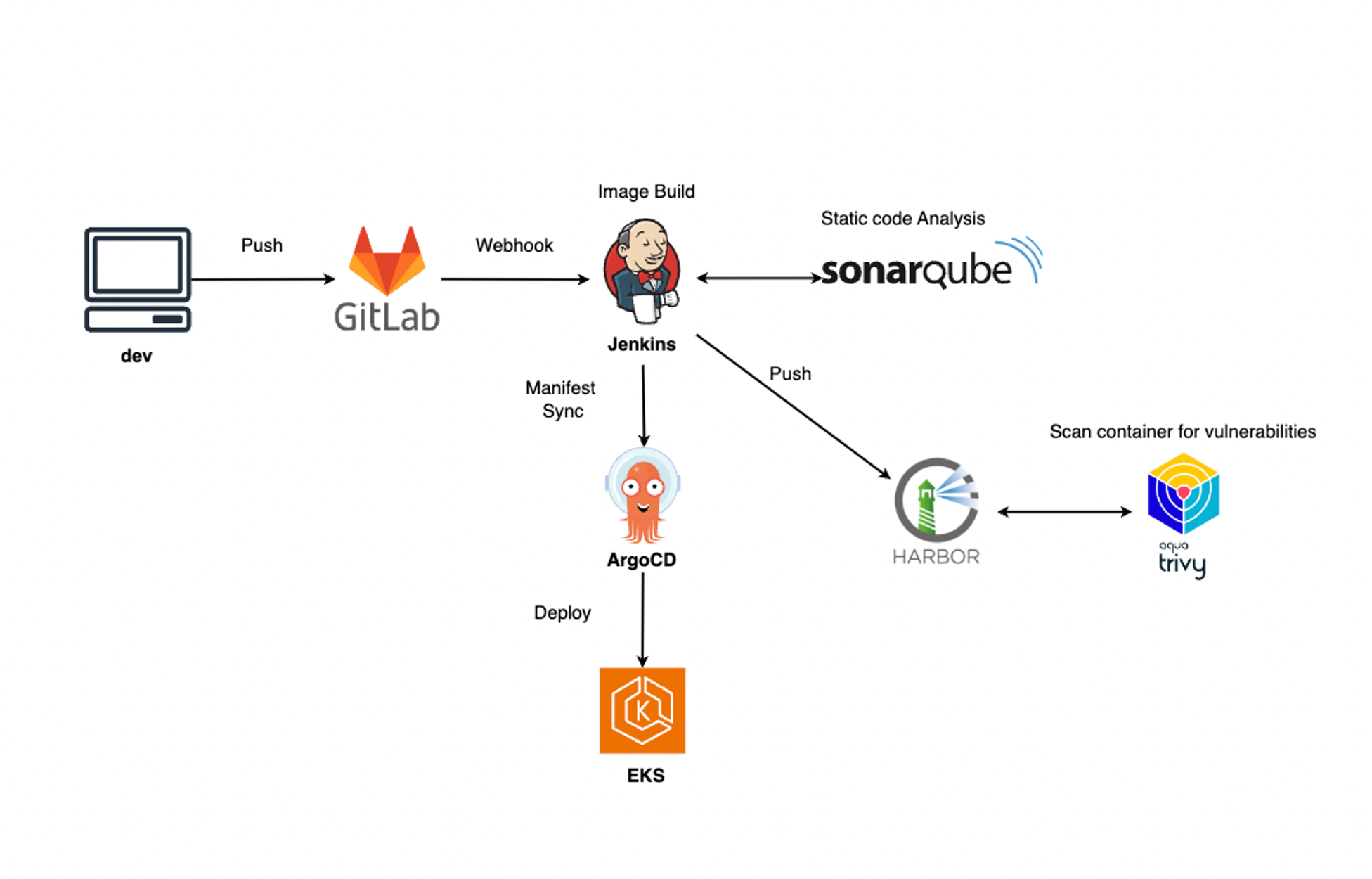
Harbor
하버는 ssl 인증서를 필요로 하기 때문에 자체 인증서를 발급 받아 설치하겠습니다.
create_cert.sh
#!/bin/bash
mkdir /auth
openssl \
req -newkey rsa:4096 -nodes -sha256 -x509 \
-days 365 -keyout /auth/myregistry.com.key -out /auth/myregistry.com.crt \
-subj '/CN=myregistry.com' \
-addext "subjectAltName = DNS:myregistry.com"
mkdir -p /etc/docker/certs.d/myregistry.com
cp /auth/myregistry.com.crt /etc/docker/certs.d/myregistry.com/ca.crt- myregistry.com은 실제 도메인을 넣어야 함
install_harbor.sh
#!/bin/bash
cp -r /auth /data
dnf install -y wget
wget https://github.com/goharbor/harbor/releases/download/v2.10.0/harbor-offline-installer-v2.10.0.tgz
tar xzvf harbor-offline-installer-v2.10.0.tgzharbor.yml 수정
harbor 다운로드시 생성되는 기본 설정 파일인 harbor.yml.tmpl의 이름을 harbor.yml로 변경하고 수정
# Configuration file of Harbor
# The IP address or hostname to access admin UI and registry service.
# DO NOT use localhost or 127.0.0.1, because Harbor needs to be accessed by external clients.
hostname: myregistry.com
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 8888
# https related config
https:
# https port for harbor, default is 443
port: 8443
# The path of cert and key files for nginx
certificate: /data/myregistry.com.crt
private_key: /data/myregistry.com.key- 실제 도메인명과 사용할 포트 번호로 변경
- 하버 계정 password와 Harbor DB password도 변경할 수 있습니다
Trivy 설치
cp harbor.yml harbor/
cd harbor/
./install.sh --with-trivy새로운 프로젝트 추가
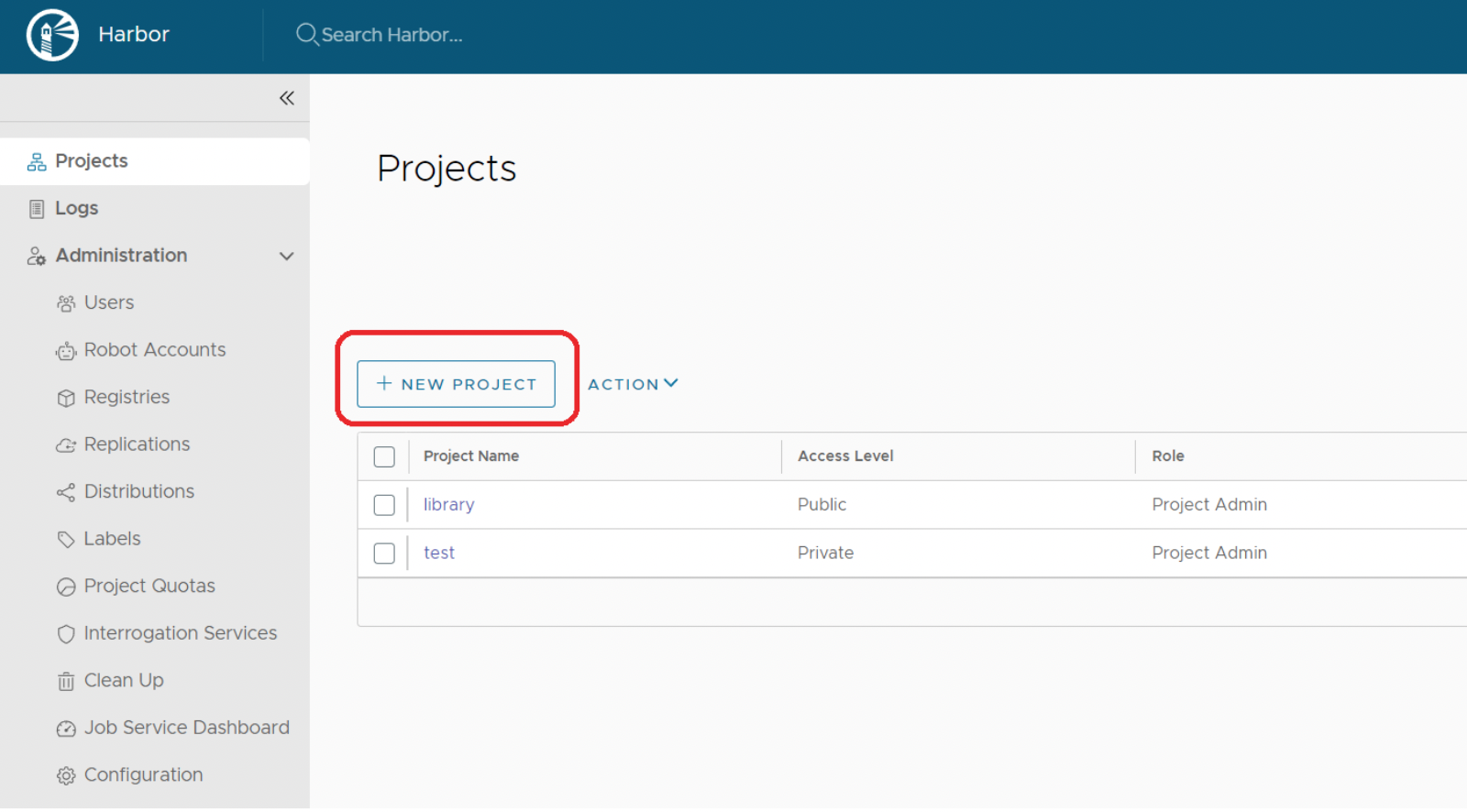
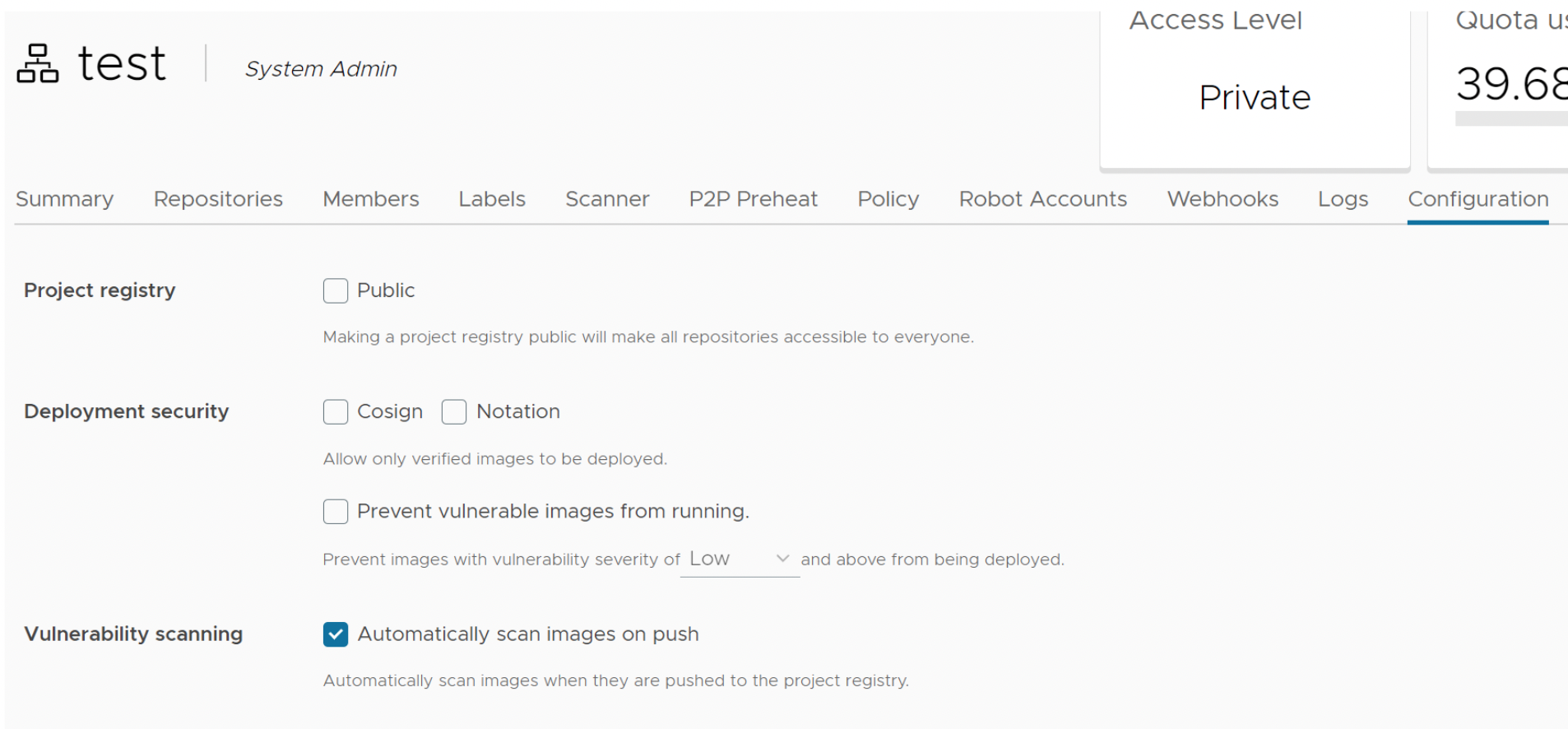
자동 스캔
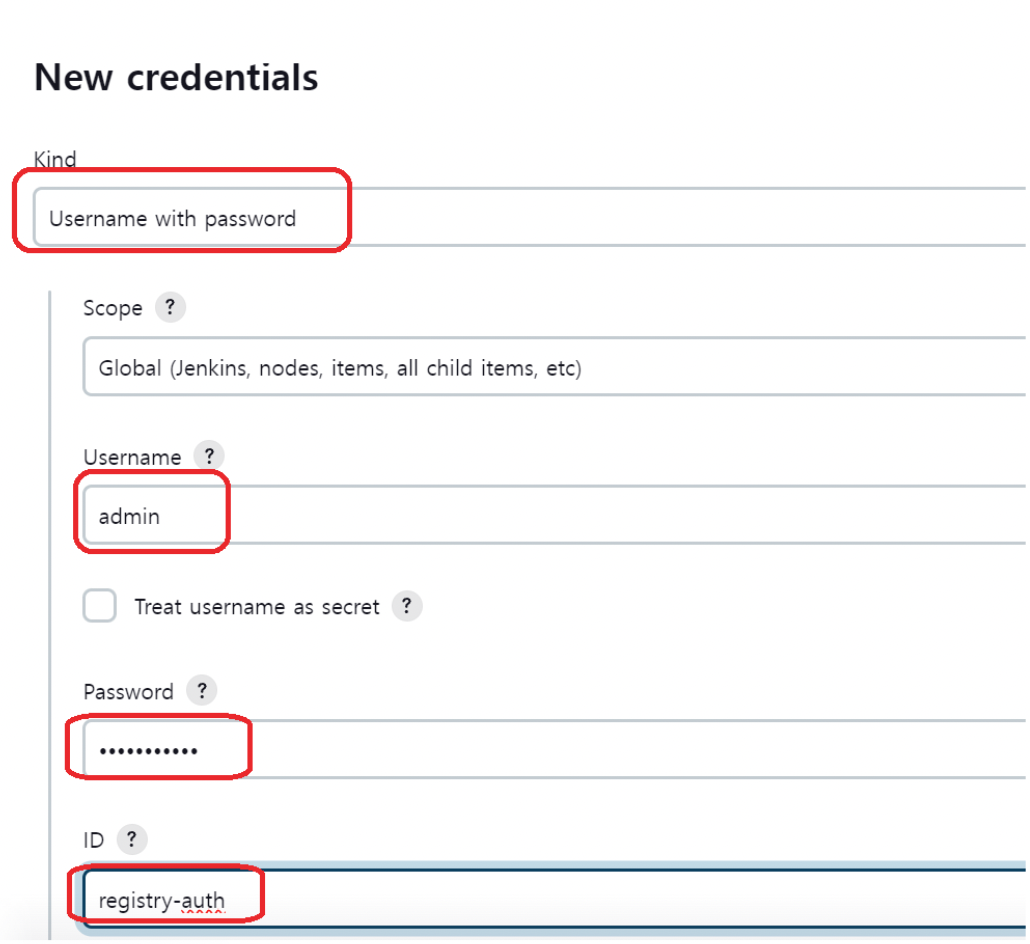
credential 추가
ArgoCD
ArgoCD 설치
//가용성 없는 버전
$ kubectl create namespace argocd
$ kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/v2.12.0/manifests/install.yaml
//가용성 있는 버전
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/v2.12.0/manifests/ha/install.yaml
ArgoCD 접속
//외부접속 위해서 lb로 변환
$ kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "LoadBalancer"}}'
// 생성된 address로 argoCD 접속
$ kubectl get svc
argocd-server LoadBalancer 172.20.90.177 a647fa3581f724c31b072ed61d5c5206-32621361.ap-northeast-2.elb.amazonaws.com 80:32656/TCP,443:32087/TCP 12h
//비번 확인
$ kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echo최종 Jenkinsfile
pipeline {
agent {
label 'gradle' // Docker 에이전트
}
environment {
// GitLab 저장소에서 소스 가져오기 위한 자격 증명
GITLAB_CREDENTIALS_ID = 'gitlab'
// Harbor 레지스트리 관련 변수
HARBOR_URL = 'harbor.myregistry.com'
HARBOR_REPOSITORY_NAME = 'olivesafety'
HARBOR_REPOSITORY_URI = "${HARBOR_URL}/${HARBOR_REPOSITORY_NAME}/olivesafety"
IMAGE_TAG = 'latest'
// Argo CD 관련 변수
ARGOCD_SERVER = 'argocd.myregistry.com' // 실제 Argo CD 서버 주소로 교체
}
stages {
stage('Checkout') {
steps {
// GitLab 저장소에서 소스 가져오기
checkout([$class: 'GitSCM',
userRemoteConfigs: [[url: 'https://gitlab.myregistry.com/olivesafety/project.git', credentialsId: "${GITLAB_CREDENTIALS_ID}"]],
branches: [[name: '*/main']]
])
}
}
stage('Gradle Jar Build') {
steps {
sh 'chmod +x gradlew'
sh './gradlew clean bootJar'
}
}
stage('SonarQube analysis') {
steps {
// mysonar = jenkins - System - SonarQube servers 이름
withSonarQubeEnv('mysonar') {
sh './gradlew sonar'
}
}
}
stage('Build and Push Docker Image') {
steps {
script {
// Docker 이미지 빌드
sh "docker build -t ${HARBOR_REPOSITORY_NAME}:${IMAGE_TAG} ."
// Docker 이미지 태그 추가
sh "docker tag ${HARBOR_REPOSITORY_NAME}:${IMAGE_TAG} ${HARBOR_REPOSITORY_URI}:${IMAGE_TAG}"
// Harbor 레지스트리에 로그인 및 Docker 이미지 푸시
withCredentials([usernamePassword(credentialsId: 'harbor', usernameVariable: 'HARBOR_USERNAME', passwordVariable: 'HARBOR_PASSWORD')]) {
sh "echo ${HARBOR_PASSWORD} | docker login ${HARBOR_URL} --username ${HARBOR_USERNAME} --password-stdin"
sh "docker push ${HARBOR_REPOSITORY_URI}:${IMAGE_TAG}"
}
}
}
}
stage('Login to Argo CD') {
steps {
script {
// Argo CD에 로그인하고 sync
withCredentials([usernamePassword(credentialsId: 'argocd', usernameVariable: 'ARGOCD_USERNAME', passwordVariable: 'ARGOCD_PASSWORD')]) {
sh "argocd login ${ARGOCD_SERVER} --username ${ARGOCD_USERNAME} --password ${ARGOCD_PASSWORD} --insecure"
sh "argocd app sync app"
}
}
}
}
}
post {
success {
echo 'Pipeline succeeded!'
}
failure {
echo 'Pipeline failed!'
}
}
}
