Keywords
- password_hash(), 72 bytes
- check details of specific funtions
- print it out
Given info
<?php
$password = exec("openssl rand -hex 64");
$stretched_password = "";
for($a = 0; $a < strlen($password); $a++) {
for($b = 0; $b < 64; $b++)
$stretched_password .= $password[$a];
}
echo "Fear my 4096 byte password!\n> ";
$h = password_hash($stretched_password, PASSWORD_DEFAULT);
while (FALSE !== ($line = fgets(STDIN))) {
if(password_verify(trim($line), $h)) die(file_get_contents("flag"));
echo "> ";
}
die("No!");
?>
- We should make true of
password_verify()
Ideas
- find REAL $h value
- bypass password_verify()
- $h made by very strange codes
$password = exec("openssl rand -hex 64");
$stretched_password = "";
for($a = 0; $a < strlen($password); $a++) {
for($b = 0; $b < 64; $b++)
$stretched_password .= $password[$a];
}
$h = password_hash($stretched_password, PASSWORD_DEFAULT);
get result of chal.php file
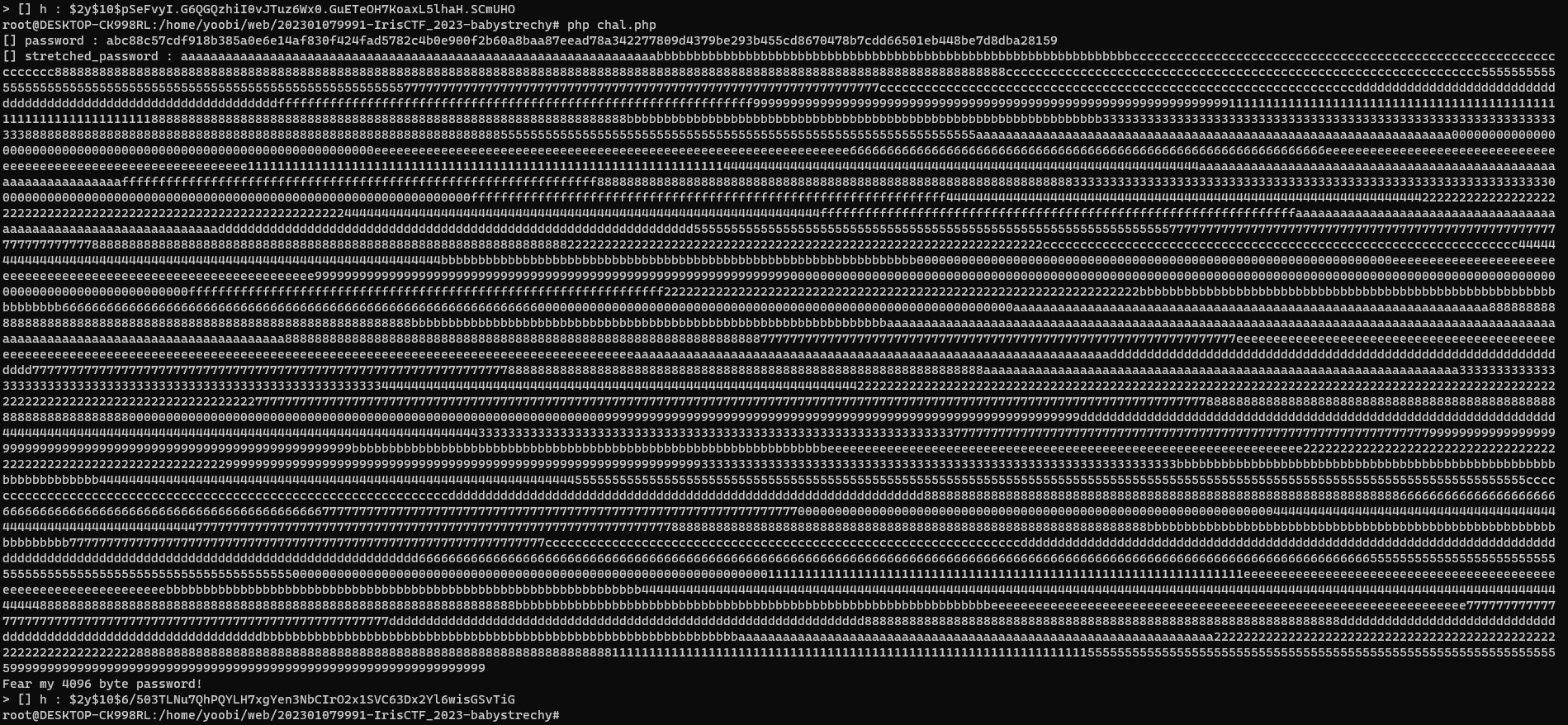
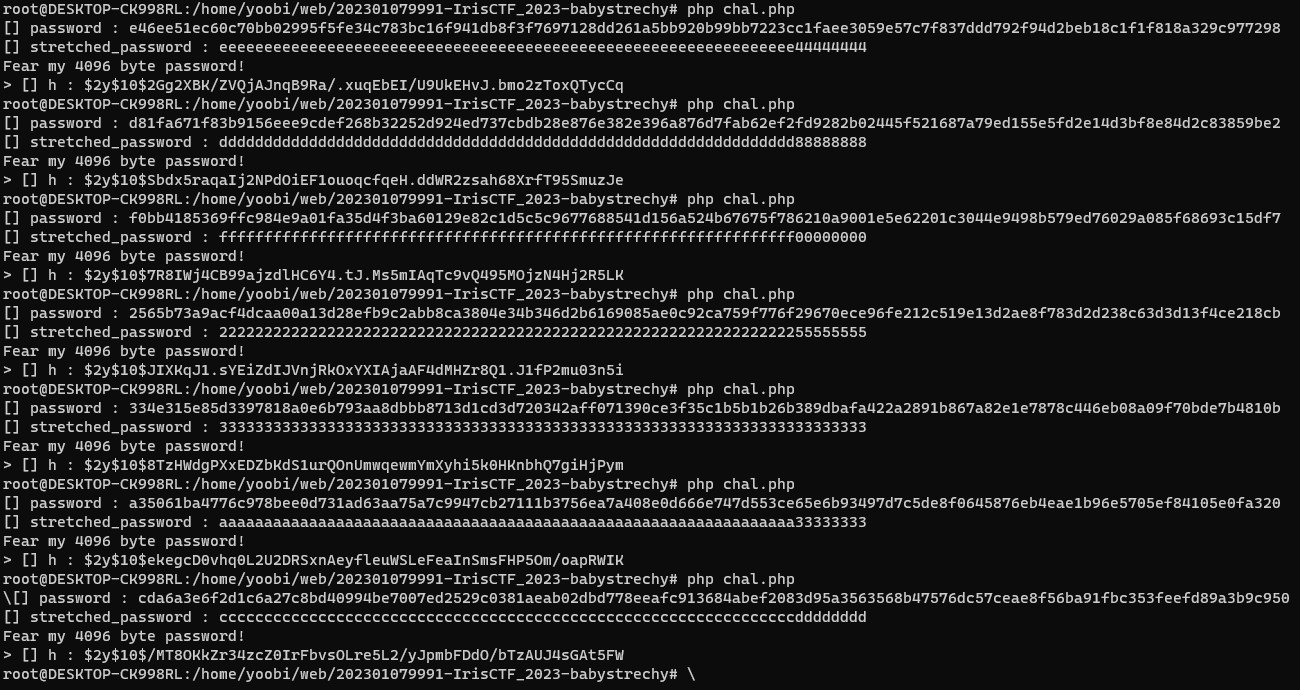
- We can see that streched_password have very long data
- But, password_hash() function only allowed maximum 72 bytes
- It means we can bruteforce the 72 bytes value. because same 64 bytes and same 8 bytes values
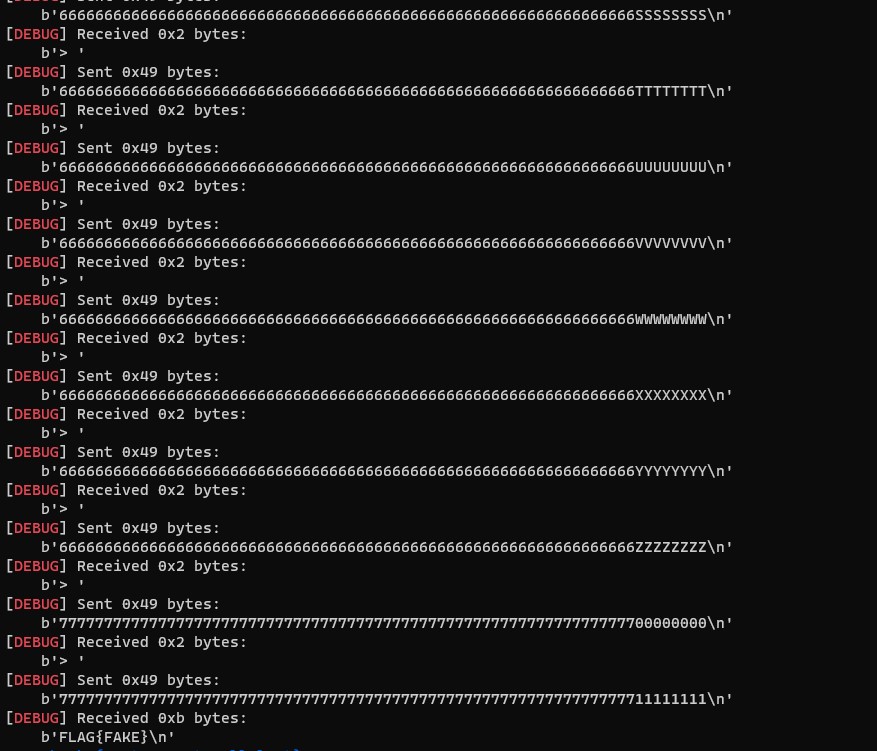
brute forcing
- make ex.py to brute forcing 72 bytes (64 + 8 bytes)
import subprocess
import pwn
import string
pwn.context.log_level = "debug"
r = pwn.process(["php", "chal.php"])
wordlist = string.digits + string.ascii_letters
for vector1 in wordlist:
for vector2 in wordlist:
payload = vector1 * 64 + vector2 * 8
r.recvuntil("> ")
r.sendline(payload)